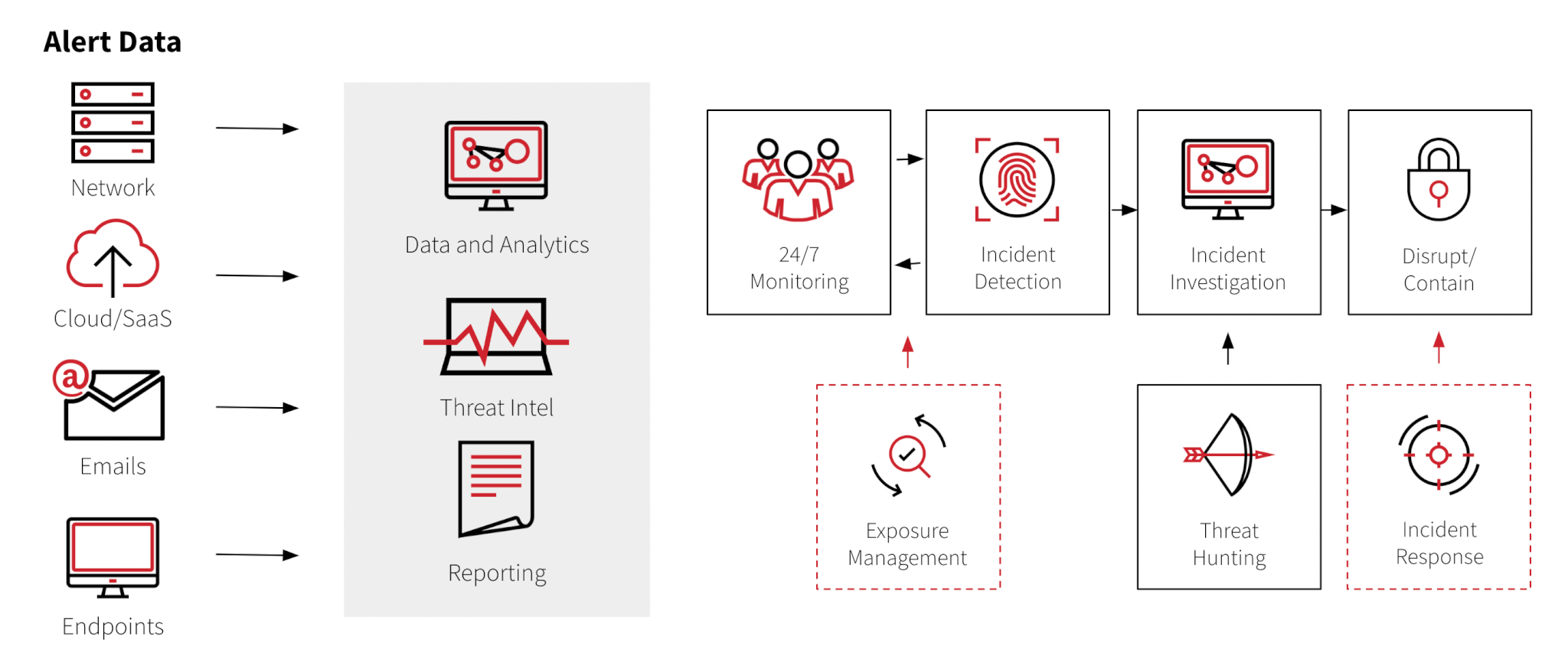
According to S&P Global Market intelligence, more than three-quarters or 77 percent of surveyed security professionals stated that threat detection and response is more difficult than it’s ever been. This is because there is an increasing amount of data coming in from network, cloud or SaaS applications, emails, and endpoints. Security teams are tasked with making sense of this data to quickly uncover threats.
Endpoint detection and response (EDR) and Security Information and Event Management (SIEM) are examples of traditional tools used for threat detection and response. EDR technologies monitor endpoints, such as workstations or laptops, for suspicious behavior, while SIEM technologies collect, analyze, and log data from a variety of security tools from across the organization. However, both tools lack an effective way to make use of the overwhelming amount of incoming data.
Here are 6 ways your organization can reduce risk with MDR:
1. Coverage and skills gap
Aside from round-the-clock monitoring, a good cybersecurity environment requires orchestration across multiple security platforms, integration of alert case management and automation, and a wide variety of specific security skills. With 3.5 million jobs available, the shortage of security professionals is making this increasingly difficult. Companies struggle to find, hire, train, and retain top talent.
With MDR, you can shift the burden of hiring a team of 24/7 security experts to a third party. You have a full security team on your side advising you along your security journey, leaving your team to focus on the organization specific tasks that are difficult to outsource.
2. Early threat detection
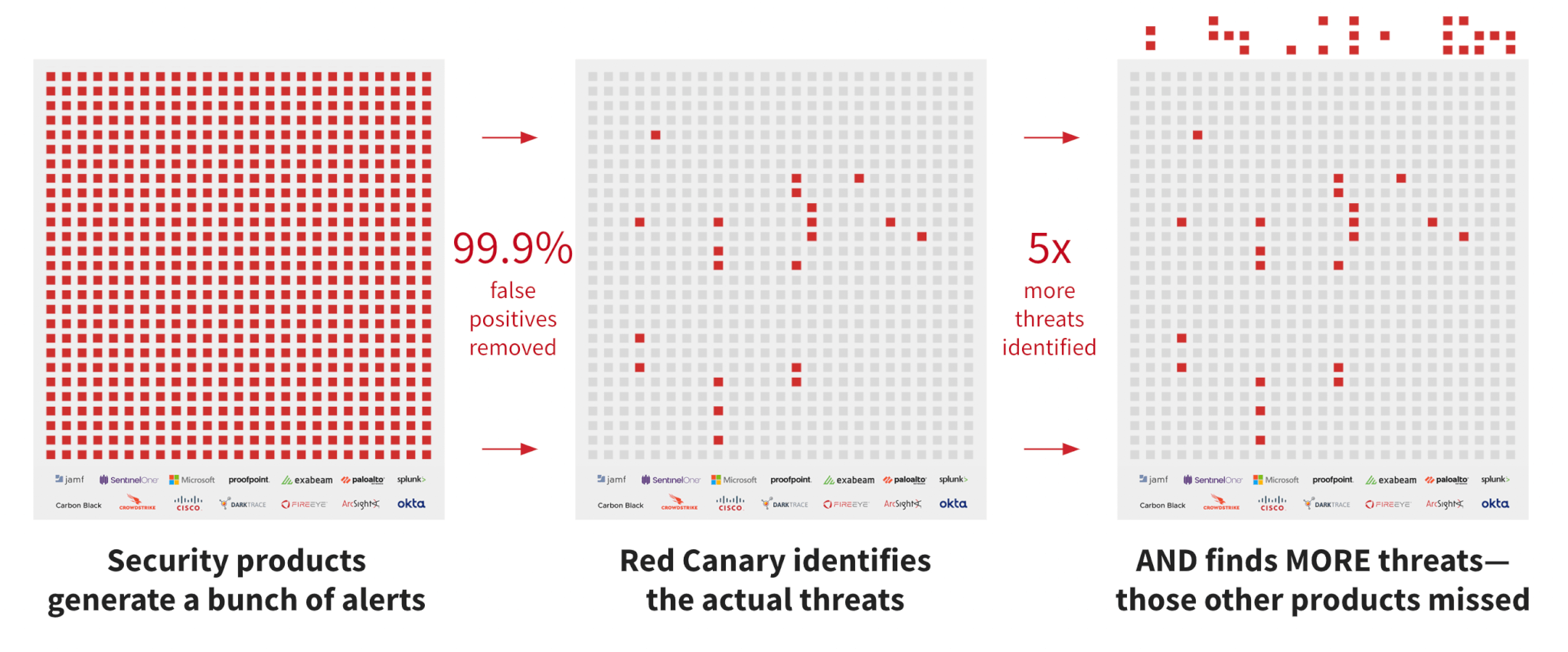
The average enterprise SOC is composed of 75 security tools, creating room for gaps. However, it’s not only about detecting threats that would have been missed; it’s being able to detect threats earlier in the attack chain and with more context so you can remediate when damage occurs.
MDR provides visibility into all traffic flowing through the entire network. MDR continuously searches for suspicious activity across multiple sources, including servers, network devices, cloud applications, log data, and endpoints. Real-time monitoring and correlation help detect known and unknown threats and reduce the lead time needed to identify and react to those potential threats.
3. Threat intelligence
Having intelligence about attacks that have hit other enterprises reduces your risk based on what others have seen.
MDR scans for evidence that attackers are leveraging tools and techniques that could be taking advantage of security vulnerabilities. The advantage here is that we don’t need to know about every vulnerability there is (such as 0-days); we just look for behavior that looks suspicious.
Red Canary gathers intel across our entire customer base which allows us to gather thousands of threats in our yearly Threat Detection Report and monthly Intelligence Insights reports so you can get visibility into threats and adversary techniques and how the landscape is changing.
“We only get to see what happens to Ansys, but Red Canary gets to see what happens to all their customers. With the visibility they provide, they know what bad looks like on a workstation, and that can be replicated across all their customers’ workstations.” – Dave Coughanour, Vice President of Cybersecurity, Ansys
See why Ansys trusts Red Canary and Microsoft Defender for their cyber defense.
4. Context for rapid assessments and faster responses
Detecting a threat earlier in the attack chain helps limit or stop the damage. It is important to understand the root cause so we can stop attacks like it from happening again. Therefore, context is important so we know the most effective way to remediate, not just detect. Context also helps you know the scope and impact of the threat, so you can prioritize and coordinate your response.
5. Breach containment and prevention
When breaches occur, it is important to be able to quickly isolate and contain them. Having a plan that takes into account automated and manual processes—coupled with technology—goes a long way to reducing the potential for a catastrophic impact to the organization.
Red Canary’s advanced detection capabilities make use of known indicators of compromise (IOC) through signature-based detection married with behavior-based detection, presenting the best option for identifying malicious activity. When the adversary executes malware or other malicious activity that matches these detection criteria, an alert is triggered. Thanks to automated response options, the Red Canary platform can immediately move to isolate the endpoint from the rest of the network without the need for any intervention.
Read more about isolating and containing a confirmed threat.
6. Reducing risk of recurrence
Finally, having a strong security posture is more than just a response. It is being able to understand why threats occur and prevent them from occurring in the future. When you are able to understand threats from the root cause on, you are able to make changes to improve your security posture so you will not be vulnerable in the future. This is unique to managed detection and response.
Red Canary not only offers the tools, but also employs detection engineers, detection enablement threat researchers, intelligence and malware specific analysts, and a 24/7 incident handling team available to all of our customers at any time to bolster your security team.
Want to learn more? Schedule a demo with Red Canary today.