We are proud to announce the latest release of our automation product, Automate. Initially released in September to help security teams automate their remediation processes in a safe, easy, and meaningful way, we’ve updated Automate with support for forensics package collection, audit logging, human approval of automated actions, and more.
In this latest release, we have introduced new features that give you:
- Greater control around automation: Support for ad-hoc execution of playbooks and human approval workflows (partial automation)
- Greater detail into threats identified: Support for forensics package collection and collection of malicious files (IOCs)
- Broader containment and remediation capabilities: Support for securing user identities for providers like Okta, extending beyond endpoint and network containment and remediation
- Audit and reporting controls: Support for viewing all automated actions taken and all changes made in addition to a unified view that can be shared with auditors for review
- Flexible endpoint management capabilities: Support for taking action when an endpoint’s status changes (ex: offline -> online), in addition to automated decommissioning of endpoints that are no longer in service
Read on to learn more about these features and the use-cases they support.
Greater Control Around Automation
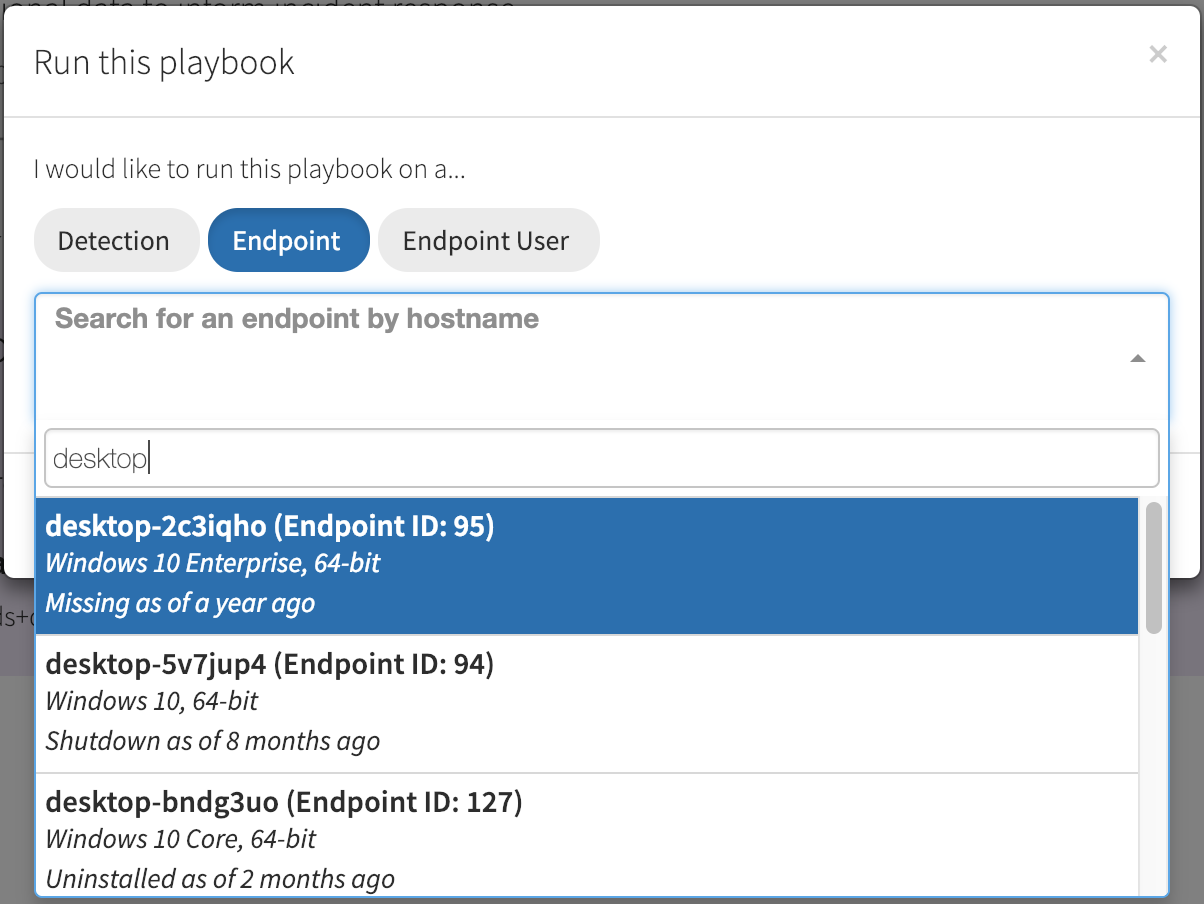
Execute playbooks as needed against specific users and endpoints
The initial release of Automate was focused on end-to-end automation. However, not all incidents or investigations stem from an alert or detection. To best support your point-in-time investigations, Automate playbooks can now be manually run against an endpoint or endpoint user.
Greater Detail Into Threats Identified
Collect forensics packages for added visibility when responding to threats
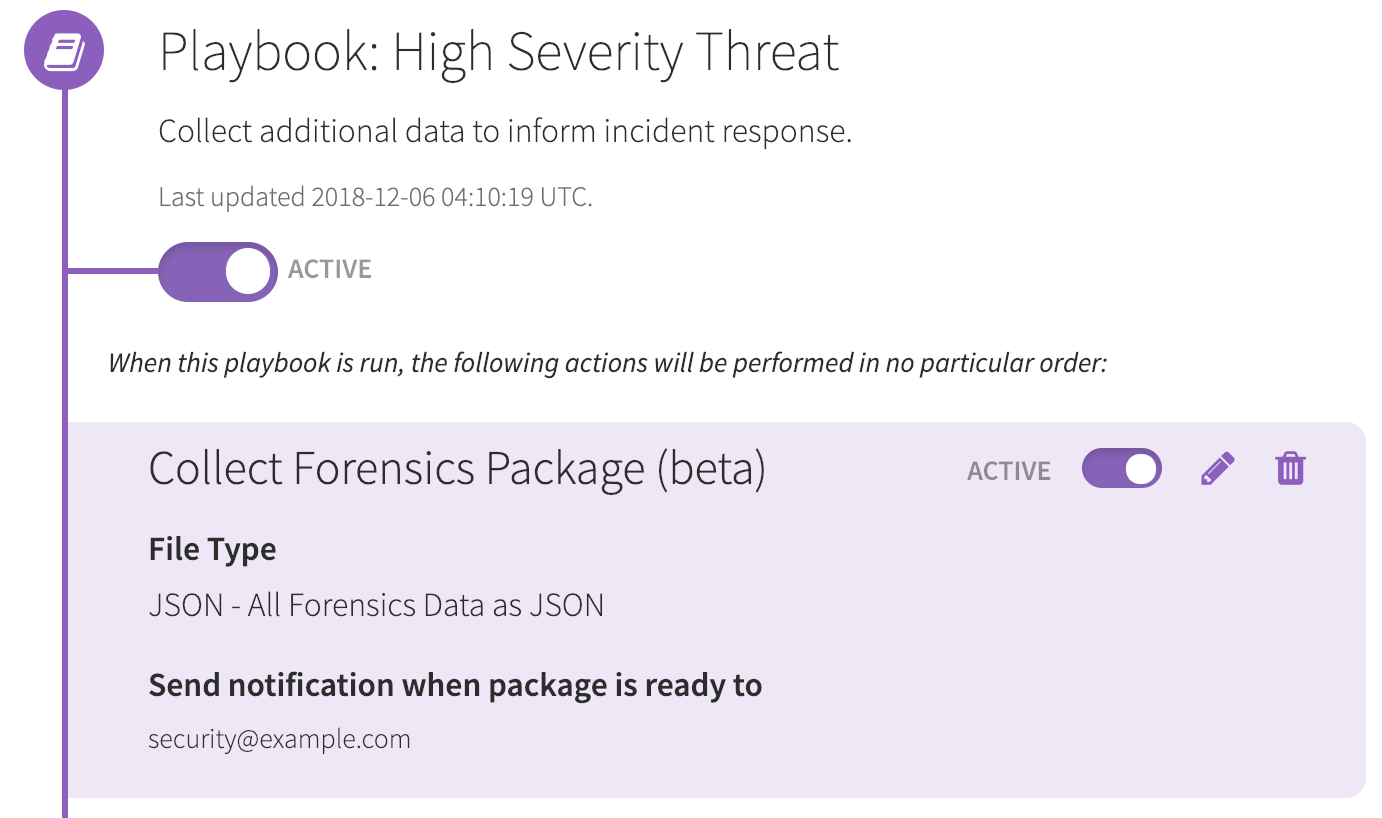
With this release you can collect a forensics package from your Windows, macOS, and Linux endpoints. The forensics package captures artifacts that augment endpoint telemetry, giving you the detailed visibility you need to effectively scope, contain, and eradicate threats.
This action, like all other Automate actions, can be automated for any of your endpoints when a threat is identified or it can be manually invoked on an endpoint for an ad-hoc investigation.
As an example, we collect anonymous and named pipes on Windows endpoints. Pipes are an interprocess communication mechanism that have been utilized by malware families like NotPetya and Ramnit—in addition to tools like CobaltStrike and PsExec (see our earlier blog on named pipes and lateral movement):
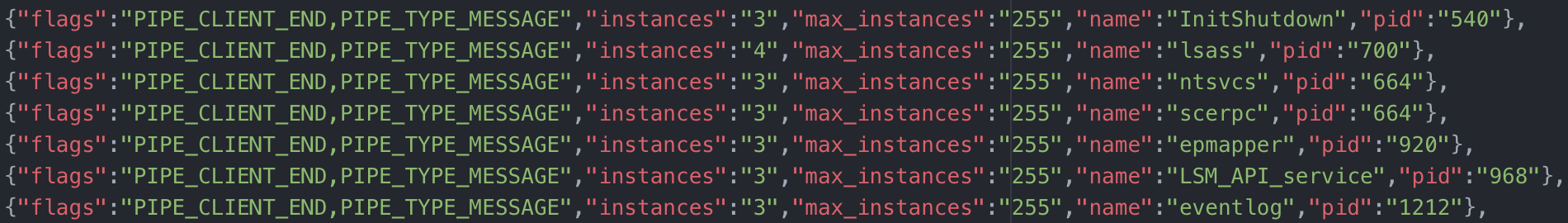
Data is delivered in CSV or JSON format, allowing you to easily view the data locally or import the data into a spreadsheet, SIEM, or a tool of your choice.
To give you a sense of the breadth and depth of the data collected across Windows, macOS, and Linux endpoints, here is a subset of the forensic artifacts collected:
- Networking: ARP cache, processes with open network connections, processes with listening ports, interfaces, etc-hosts, firewall profiles and rules, routes, mounts, shares
- Software: execution history (prefetch, shell history, …), pipes, browser plugins, drivers, patches, programs/applications, services, startup items, WMI filters and consumers
- Users: users, groups, logged-in users, login history, shell history
- System: local time, uptime, operating system and version, drives
Broader Containment and Remediation Capabilities
Require human approval of certain automated actions
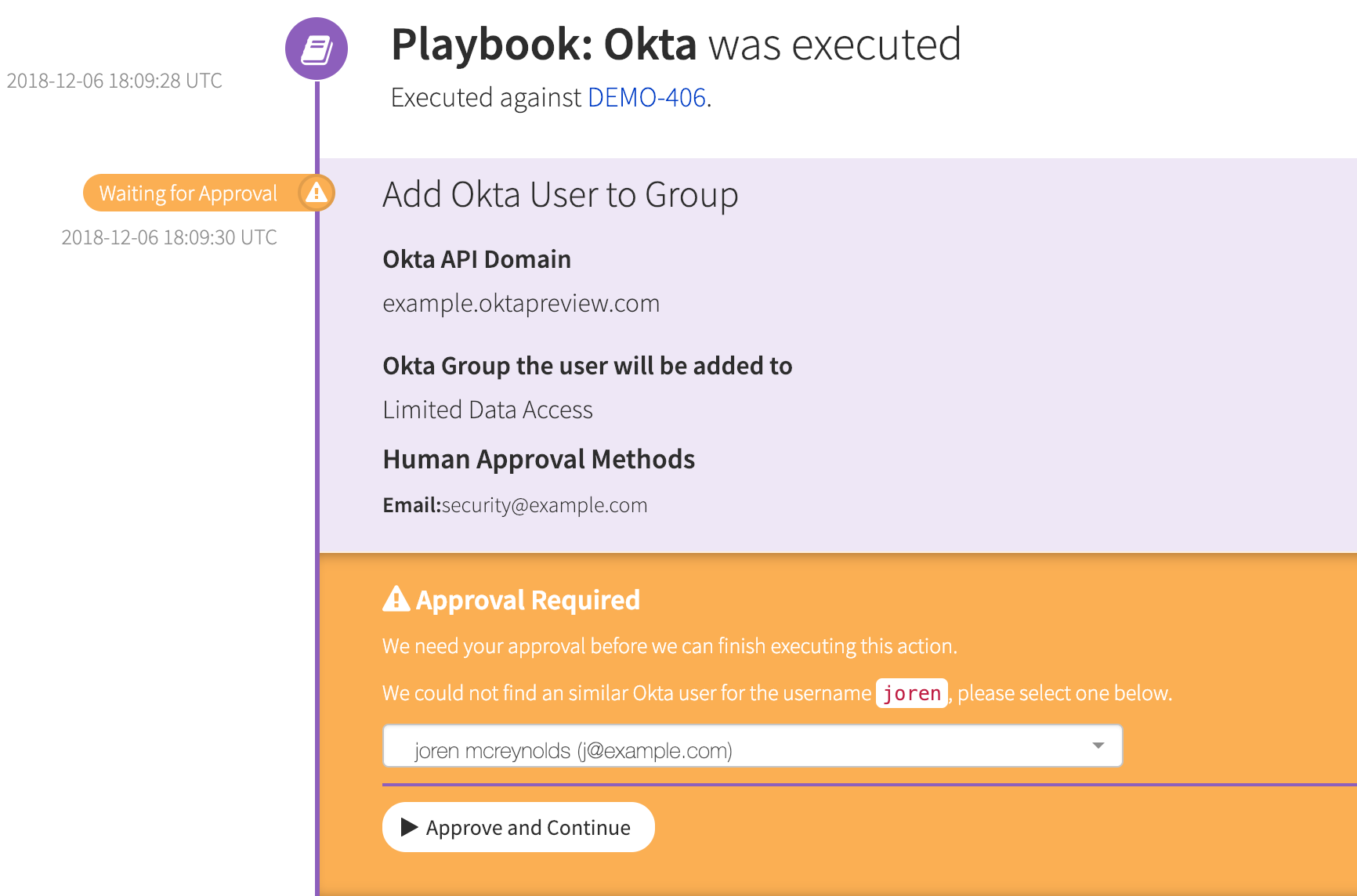
In some instances, end-to-end automation isn’t possible (safely) without some form of human review or approval. Take the example of securing an identity for a service like Okta, in the event of a compromised endpoint. The endpoint has an associated user identity, but that user identity (AD_DOMAIN\joren) may not exactly match that user’s associated Okta identity (joren.m@example.com).
In this case, we need to suggest possible matches and have your team make the final call before taking the automated action. In the case of Okta, automated action options include clearing the user’s Okta sessions, suspending the account, or adding the account to a group with data access restrictions.
An example of the human approvals flow with our new Okta integration:
The new “human approvals” capability—coupled with the new Okta integration—ensures that your containment and remediation strategy doesn’t prematurely stop at the endpoint or your network.
By securing the Okta identity of the user of a compromised endpoint, you’re securing access to the cloud services that power your business, including email, file-sharing, and infrastructure services like Gmail, Dropbox, AWS, and others.
The “human approvals” capability will be included in future Automate actions when additional context and knowledge is needed from your team.
Audit and Reporting Controls
Satisfy compliance and auditing needs by documenting automated actions
Automate builds an audit log that documents all of the automated actions performed, and any changes made, in an easy-to-understand timeline for your team:
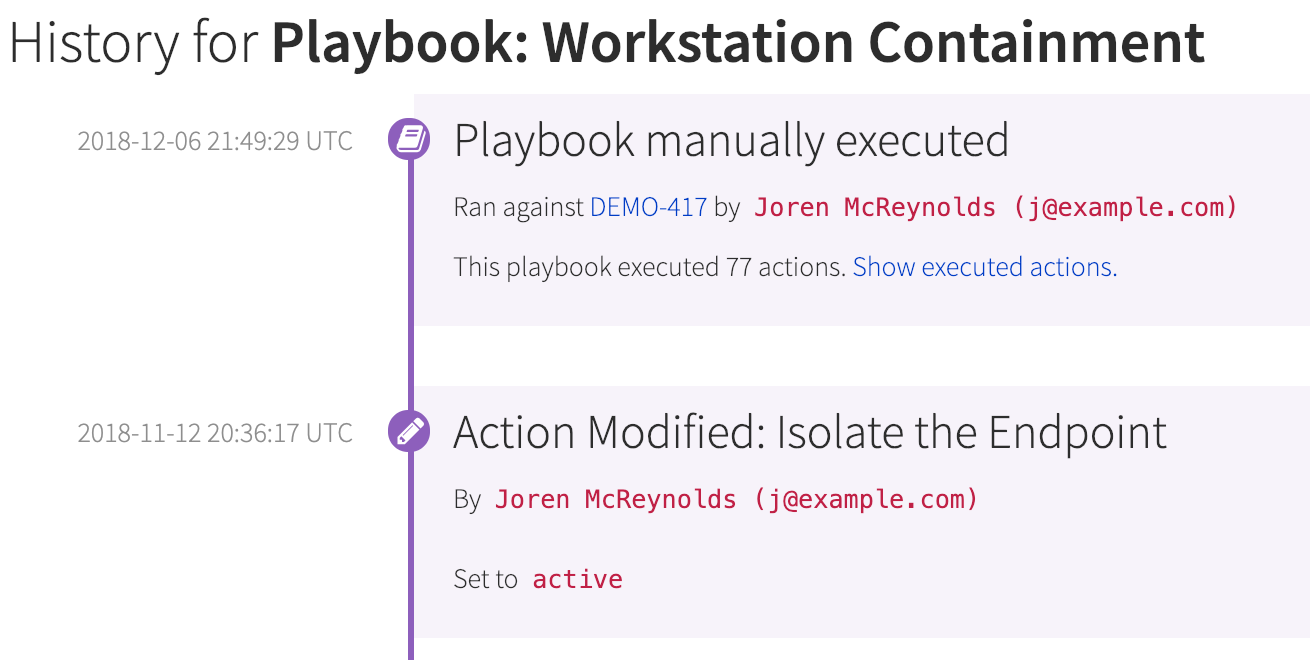
Many of our customers wanted us to take this a step further for auditing and compliance needs. As a result, you can now print or create a PDF detailing all playbook configurations and changes in a single view.
This provides a true end-to-end outcome—you can discard document-based playbooks and move to digital playbooks that are consistently followed and easily shared with auditors for review.
Flexible Endpoint Management Capabilities
Initiate automated actions conditionally when an endpoint changes status
Many of our customers have the need to alert and take action when a particular endpoint’s status changes. Some common use-cases and scenarios include:
- A remote employee’s endpoint is under investigation or compromised. You want to investigate the endpoint further, but it’s in a different time zone and offline. You want to know immediately when it comes back online.
- A device has been stolen from one of your employees or offices. You want to know immediately if the device is powered on and obtains internet connectivity.
- You want to know any time an endpoint sensor is uninstalled, as this is a violation of your security policy and may be indicative of an attack or insider threat.
- You’re performing active forensics on an endpoint and want to receive a notification when the endpoint is suspended or shutdown.
With this release, you can now listen to and automatically take action whenever an endpoint’s status changes to online, offline, missing, suspended, or shutdown.
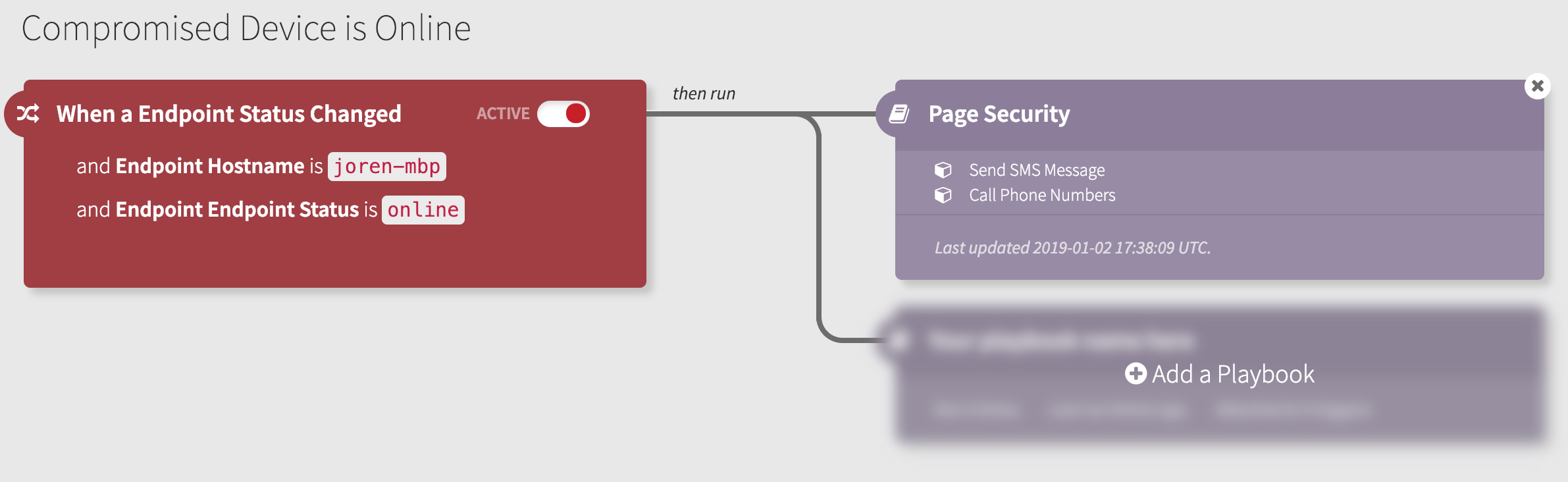
Similarly, you can configure a playbook to decommission an endpoint if it hasn’t checked in for ‘X’ days, keeping your inventory up-to-date.

Interested in learning more?
Read more about Automate or request a demo to see how Automate can help you automate response in a safe, easy, and meaningful way.