Add an ally. Strengthen your defenses.
You don’t need time, expertise, or an army of security hires to build a 24/7 detection and response capability—you simply need Red Canary.
As VMware Carbon Black specialists, we ensure you get immediate return on your product investments, along with the added peace of mind of knowing an industry-respected detection and response team is watching your environment at all times.
10x
your detection coverage
24/7
detection and response
99.9%
fewer false positives
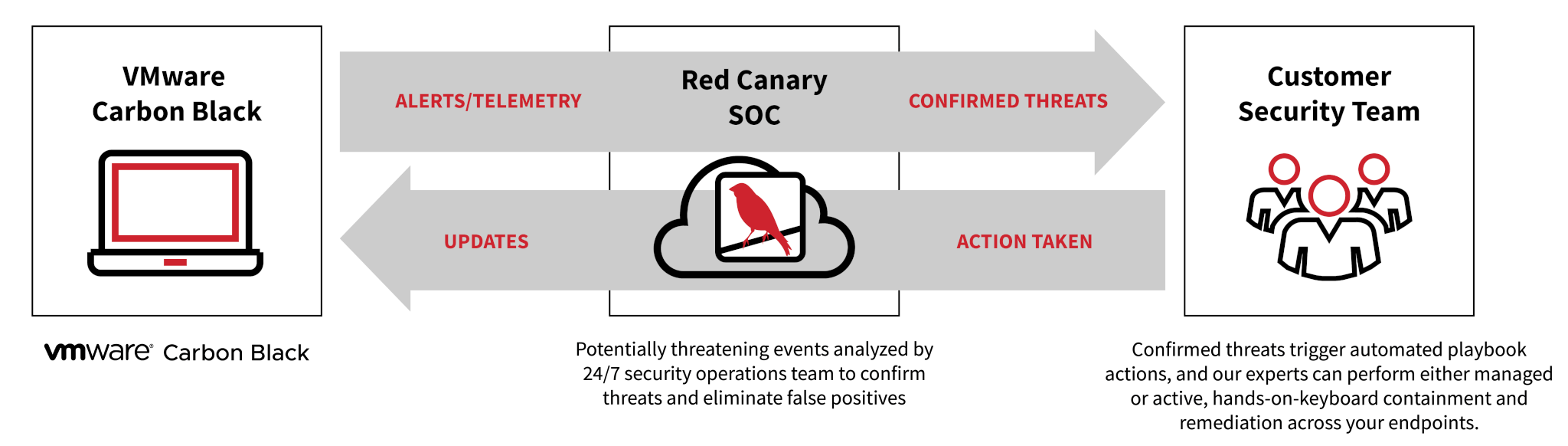
How it works
Turnkey detection and response
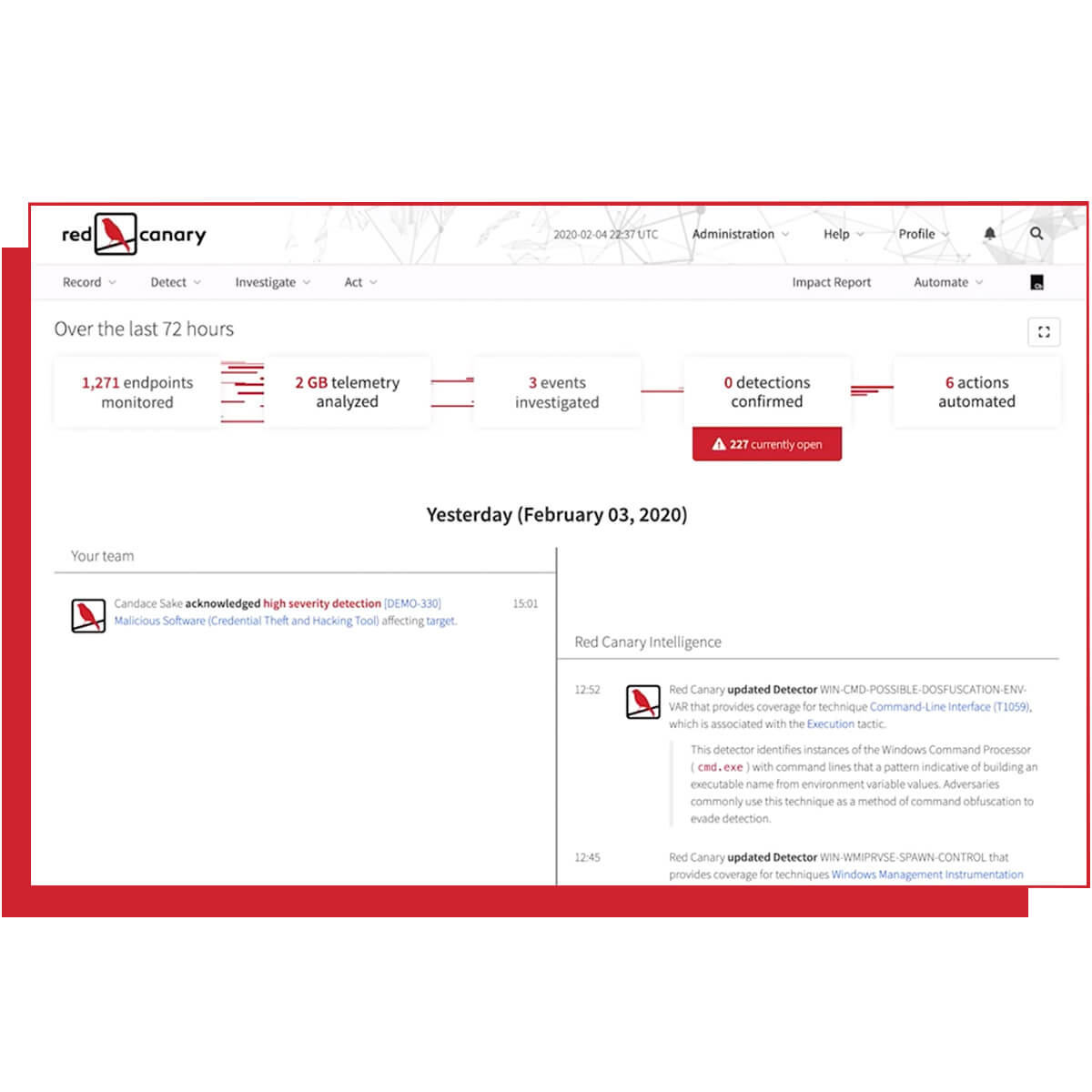
Red Canary helps you deploy, configure, and update policies for VMware Carbon Black sensors. We ingest your product alerts and analyze your endpoint telemetry using our cloud-based detection engine composed of thousands of behavioral analytic use cases.
Hunt adversaries and evolve detection
Red Canary researches new attacker behavior and continually combs your environment. We maintain industry-leading detection coverage by updating our library of behavioral analytic use cases hundreds of times per week in response to new attacker behavior.
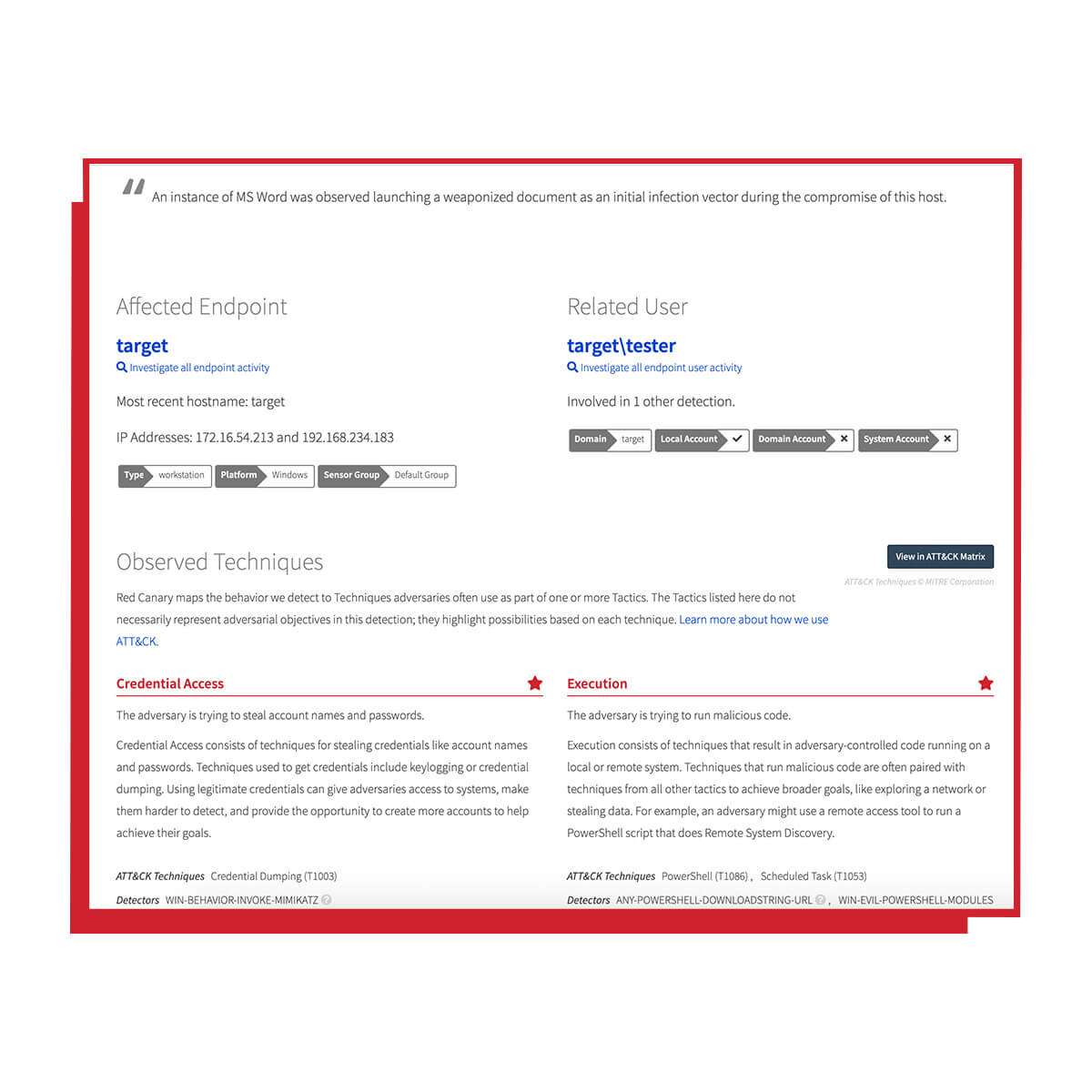
Offload investigations and add automation
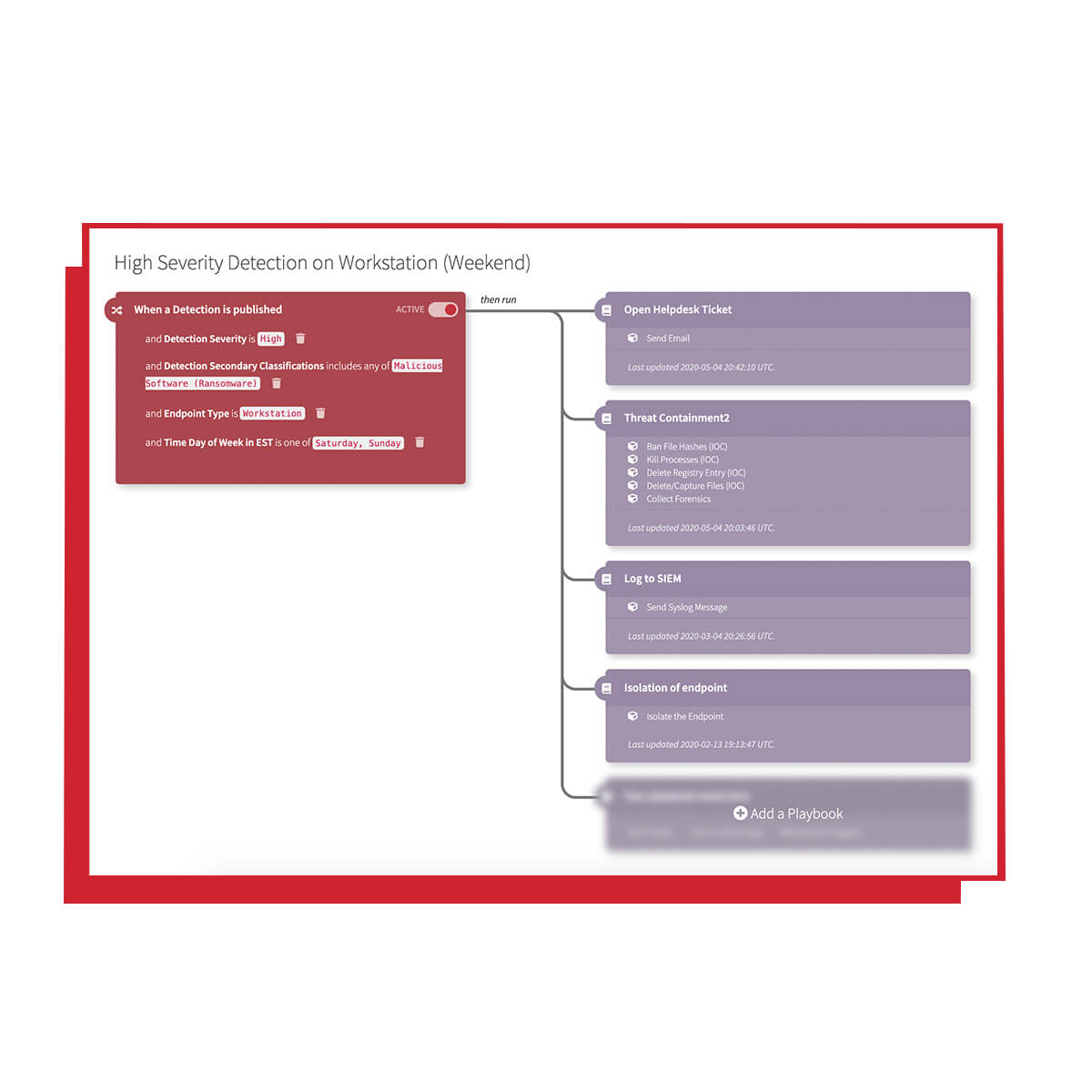
We perform full investigations using our proprietary analyst workbench and only alert you to confirmed threats. A detailed threat report is posted in your Red Canary portal where you can customize automated response actions and playbooks.
Active Remediation and Managed Response
Our incident handlers can perform active or managed remediation and containment in your environment.
learn more
What Customers Are Saying
Benefits
Why Red Canary
Deep expertise rooted in shared lineage
Red Canary and Carbon Black were both innovations started inside Kyrus Tech, a boutique cybersecurity defense contractor. Red Canary’s founders started working with Carbon Black on Day 1 to deliver expert incident response services. When the founding team realized Carbon Black EDR collected all the necessary data for proactive threat detection and response, the idea for Red Canary was born.