With many students starting or continuing remote learning, arming schools to stop cyber attacks is more important than ever. As a former security leader at a K-12 school district—and most importantly, a parent—this topic is especially top of mind for me. I remember the difficulty that school and technology department leaders faced when balancing efforts focused on student engagement and safety. Do you cut a security line item or increase class size? These decisions were incredibly tough for school districts, even before the pandemic hit. Now K-12 schools struggle with advancing technology and structuring security around a flexible, shifting distributed model of learning and technology management. All the while, budgets and access to train personnel continue to shrink.
This article highlights some resources schools can use to continue to protect their environments, data, and students. Knowing that budget restrictions are top of mind, most of these resources are free or very low cost. Whether your organization is conducting virtual learning, in-person classes, or some combination thereof, I hope this collection can help relieve the burden on your IT and security staff.
Cybersecurity resources for schools
Want Better Security? Start With These 5 Proven IT Fundamentals
by Adam Mathis, Red Canary
This article focuses on implementing fundamental controls that lay the groundwork for a great security program over time. Increasing your overall awareness of what you are protecting is key, and trying to minimize access, rights, gaps, and vulnerabilities is all part of a larger cybersecurity game for defenders.
The amazing thing about this article is that these fundamentals could be implemented in your organization without a huge investment.
Good IT hygiene will create an awesome platform for you to continue to build a strong, yet flexible security program for the future. This will not be an easy task, however, and will require some great communication with your team, and possibly some adjustments to meet the new post-pandemic challenges we are seeing in the remote learning environments. If your school’s SCCM/JAMF platform is behind a firewall, you may want to explore modifications like:
- Leverage curated application stores over providing local admin rights to facilitate necessary software installation
- Set up remote patch management options or solutions to allow remote systems to maintain the latest patches
- Streamline your software approval process so you can continue to remain flexible as new tools are discovered and requested
The 20 CIS Controls & Resources
by the Center for Internet Security
Maintaining multiple aspects of a security program can quickly become overwhelming. Leveraging a cybersecurity control framework can give your program the structure and strength you need. I love the CIS Critical Security Controls for this purpose.
CIS breaks down their controls into Basic, Foundational, and Organizational controls. By pursuing the Basic controls, you can buy down a significant amount of risk for your organization.
These controls include:
- Inventory what you have (hardware and software)
- Continuously look to see what vulnerabilities and gaps those technologies bring into your organization
- Restrict rights, access, and ways systems communicate
- Capture logs that could indicate if evil is afoot
The great thing about the CIS Critical Controls that they suggest additional control areas, allowing your program to grow and scale, while keeping what is important at the heart of the matter.
Critical Concerns for the Education Industry
by Susan Morrow, Infosec
When building your security program, it’s important to get a good grasp of the regulations and compliance concerns for your industry. This article does a great job reviewing critical security concerns in the education industry and highlighting how organizations can stay compliant.
Education is in the unique position of having its own federal regulation—The Family Educational Rights and Privacy Act (FERPA)—and also needing to comply with regulations from other industries, depending on what courses and services the institution offers. This may include state-specific legislation, such as California’s Student Online Personal Information Protection Act (SOPIPA), as well. Once you have a good idea of all your compliance requirements, you can shape parts of your program around them.
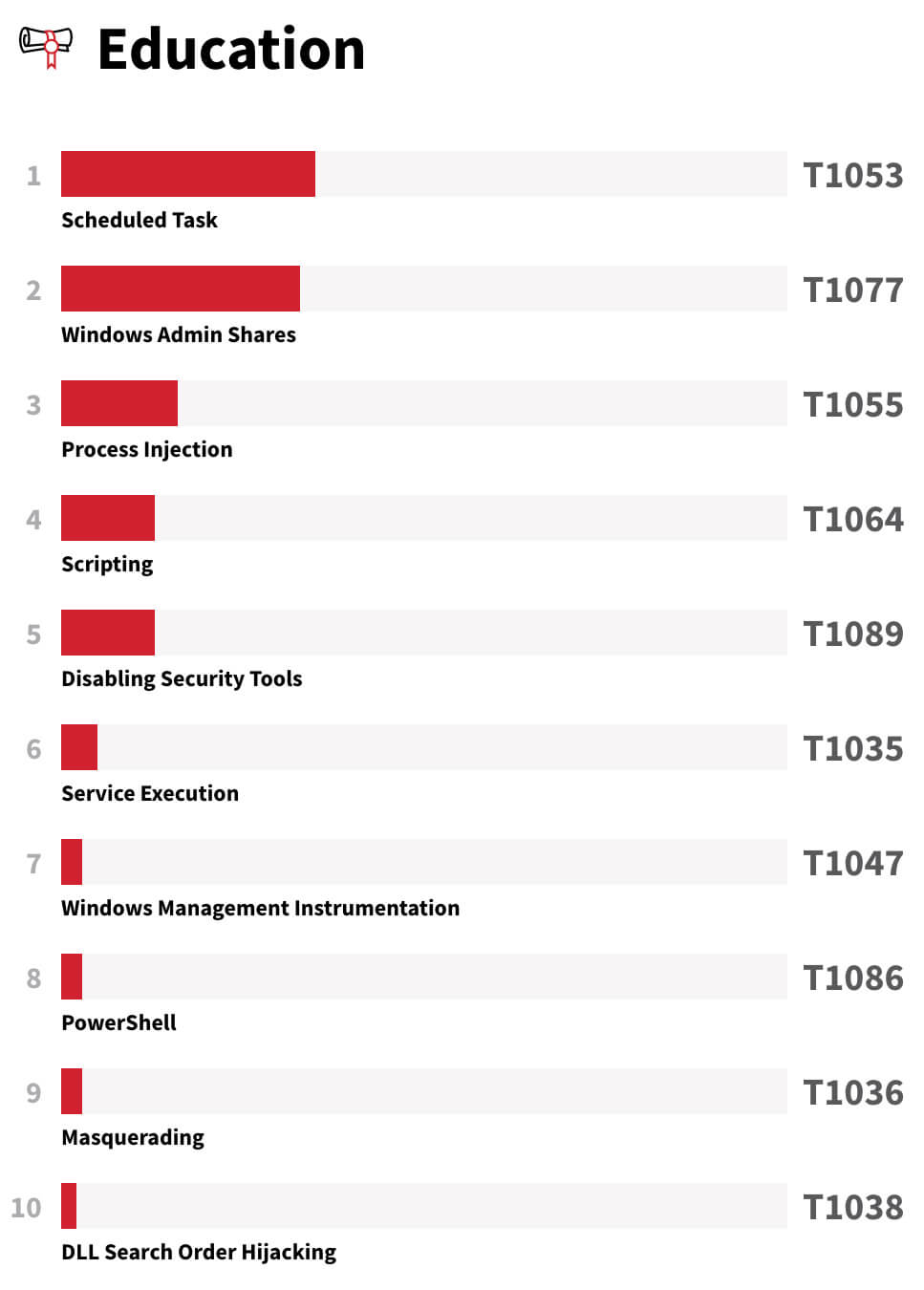
2020 Threat Detection Report
by Red Canary
You’ve probably heard the phrase “know thy enemy.” At Red Canary, we believe that understanding the tactics and techniques an adversary is most likely to use against you is a critical step in defending against them.
Each year, our research, threat intelligence, and content teams come together to produce an in-depth analysis of our observations over the course of a year. The report shares the most prevalent MITRE ATT&CK® techniques across different industries. Armed with this information, organizations can look holistically at their security programs to assess whether or not they have the correct processes, technology, and governance in place.
While we recommend reading the full report, below is a list of the top threats in education, which you can use to help guide your detection efforts where reasonable. Read the full Threat Detection Report for detection strategies and open source tests to evaluate your coverage.
Navigating remote and distance learning
None of the articles or frameworks above directly address what many schools realized very quickly when moving to a decentralized model of IT. As devices left our traditional network, security and IT staff needed to scramble to look for Software as a Service (SaaS) offerings that provided the flexibility needed for a remote working environment. Often, this meant taking devices that may have never left the network’s “circle of trust” (firewall, routers, content filters) and shipping them out to teachers and students. This was (and is) a whole new world for some organizations, as many of the core IT services are not available externally.
Below are a few resources that address this important shift.
Cloud offerings
Because virtual private networks (VPN) come with limited licenses and adds overhead, some schools may have migrated to O365 or Google Apps offerings. Here are some resources and checklists your IT staff can follow when configuring either environment to reduce the risk of compromise, data leakage, and other attacks.
Video conferencing
Attacks targeting disruption of remote classwork (like “zoombombing”) continue to plague digital classrooms. Ensure both your enterprise team and remote users are aware of ways to improve the safety and security of their remote sessions.
The links below offer some suggestions on how to protect popular video conferencing solutions:
- Zoom: Best Practices for Securing Your Virtual Classroom
- Google Meet Security & Privacy for Admins
- Microsoft: Skype in the Classroom Educators Guide Learning from Home with Skype in the Classroom
Content blocking
Layering security controls and maintaining defense-in-depth is always key, and it’s especially critical when devices are leaving the confines of your district’s protected network. Leveraging some sort of proxy or web content blocking on the device will help in blocking malicious and adult content. Layering a secure DNS service with filtering options can also provide you and your students some peace of mind.
The services below offer a variety of content blocking capabilities that may prove helpful. It’s worth noting that they each have their limitations and some have a cost associated.
Stanford’s Information Security Risk Classifications
As you enable a remote workforce and learning environment, you’ll run into some hassles keeping track of all the data for which you’re responsible. Stanford publishes their own standards and guides around how they protect different types of systems and data with approved vendors and checklists. You can use these to help guide your way if you get overwhelmed.
Better together: connecting with others
The importance of community and collaboration in times of crisis cannot be stressed enough. Building, growing, and managing something as complex as a security program is challenging, and the current uncertainty only adds to that. Remember, you are not alone in all of this! Take advantage of the many organizations offering support, information, and services to help you through it.
Here are a few of the groups I’ve found particularly helpful over the years.
Multi-State Information Sharing and Analysis Center (MS-ISAC)
MS-ISAC is a government-funded organization that stresses the importance of cybersecurity among State, Local, Tribal, and Territorial (SLTT) organizations, which includes K-12. They do this through a variety of free and paid programs (usually subsidized through grants) that can help with training, awareness, and vulnerability management, as well as open access to experts throughout the country. Take a look at their website to learn more about their programs and ways to register.
Research and Education Networks Information Sharing and Analysis Center (REN-ISAC)
REN-ISAC has a paid membership for colleges and universities. Member institutions benefit from threat intelligence and peer assessment services to improve security posture. They also facilitate professional training and development with webinars, regional workshops, and an aggregate purchasing program with the SANS Institute.
Peer and government communities
While serving in a K-12 role, I was amazed at the power of reaching out to members in my state and local government communities. Many of their security leaders were dealing with similar challenges, and I was able to build a network I could talk to, ask questions of, and seek insight from. We are all working towards a better, more secure future for the citizens and students we serve, and I found that most people are eager to help if you just ask. Organizations like MS-ISAC helped facilitate some of these conversations, while others required me to be more proactive in reaching out for an individual’s time. (Often with coffee!)
Talking to other educational institutions is also extremely helpful. Taking the time to collaborate and share notes with other schools helped my team continuously structure, tweak, and mature our program. We were able to create a community focused on protecting our organizations, learning from each other, and pooling resources, talent, and training to ensure our collective education objectives were met.
Organizations like Educause, ISTE, and CoSN provide other ways to get involved and speak to other K-12 organizations. Note that many of these groups require memberships, with associated fees.
Here are a few free resources from these organizations that are specific to COVID-19:
- National Cybersecurity Alliance COVID-19 Security Resource Library
- Educause COVID-19 Resource Page
- CIS Resource Guide
Closing thoughts
Recognize the work you just accomplished—and document it!
As the world continues to adapt to the “new normal,” the commitment, resourcefulness, and resilience of our educators, support staff, and faculty deserves to be applauded. The work you’re doing to safeguard our students in virtual settings is critical.
You’ve taken on a monumental task: migrating normal operations to multiple, distributed remote sites, all the while continuing to deliver a safe environment for your staff and students. Don’t let the work go to waste. Leverage planning time to collect what worked and what didn’t. Take time to document the tools, resources, communication plans, and processes established during your move to remote learning, as this serves as a future plan for a Continuity of Operations Plan (COOP) or an Emergency Operation Plan for future disasters and disruption events for your school.
Here is a FEMA Sample Emergency Operations Plan you can use for reference.
Let’s collaborate!
I hope these resources help relieve some of the burden for you and your schools, so that you can continue the important work of empowering, reaching, and educating today’s students. All of us at Red Canary take a lot of pride in being a security ally to organizations, whether or not they are customers.
If you’ve been working to secure your school’s virtual learning environment, I’d love to hear from you and collaborate. Message me on LinkedIn anytime or contact blog@redcanary.com with any observations or questions.