Trend
Ransomware
Despite some promising disruptions to the ransomware ecosystem in 2023, defenders should stay vigilant in detecting common precursor behavior.
Pairs With This SongThreat Sounds
What you need is a good defense–against ransomware precursors that is.
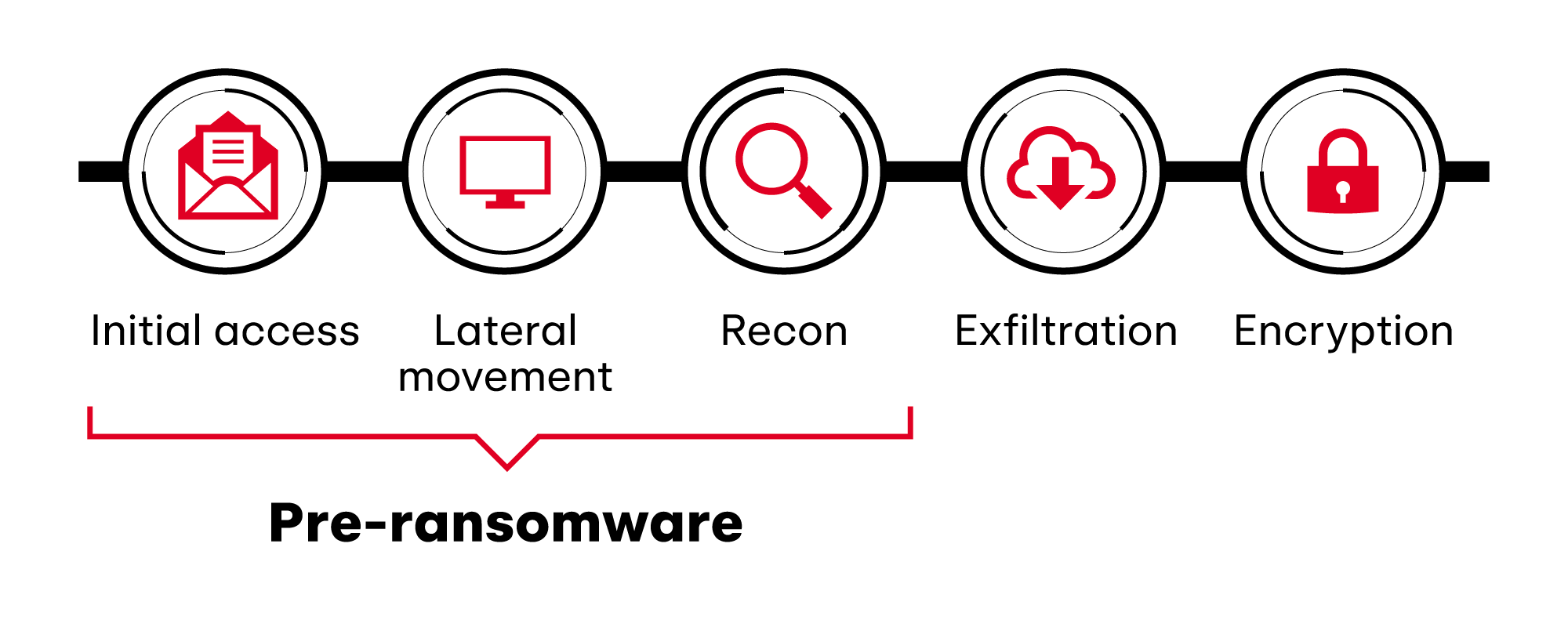
Even if we as a community are tired of talking about it, 2023 showed us that ransomware isn’t done with us yet. As with 2022, Red Canary’s visibility into the ransomware landscape focused on the early stages of the ransomware intrusion chain—the initial access, reconnaissance, and lateral movement occurring before exfiltration or encryption, which we refer to as “ransomware precursors.” Focusing on detecting these precursors continued to be a solid approach to stopping ransomware in 2023, so we’ll focus on sharing what has worked for us.
We saw so few intrusions making it to the final stages that no ransomware group made it into our top 20 threats. That said, throughout the year, we observed Lockbit, Crysis, Akira, and Snatch, as well as an attempt to deploy Cerber ransomware. Since our visibility centers on ransomware precursors, we also recommend checking out ransomware reporting from others across the community, including Malwarebytes, Emsisoft, and Recorded Future.
Common ransomware precursors
As in previous years, multiple threats in our top 10 play a role in ransomware intrusions as common precursors:
Check out each of those pages for ideas on how to take action to detect those threats. We’ve previously shared this simplified ransomware intrusion chain as a way to think about detecting across the entire intrusion, and in 2023, this chain continued to hold up as a high-level approach to breaking down ransomware.
Here are some of the common techniques, tools, and procedures we observed across “pre-ransomware” intrusion stages:
Initial access
Red Canary has observed ransomware intrusions beginning with adversaries exploiting vulnerabilities in internet-facing devices such as Confluence or Veritas. While some vulnerabilities were more recent, in 2023 we also observed adversaries exploiting years-old vulnerabilities as well. These internet-facing devices were often unmonitored, resulting in detection of the intrusion only when adversaries moved off the initial device. We weren’t the only ones to observe adversaries exploiting vulnerabilities to start ransomware intrusions; cyber insurance company Corvus noted that in the first half of 2023, they observed exploitation of external vulnerabilities as the leading method of initial entry for ransomware.
Additionally, we observed intrusions starting with common malware families like SocGholish and Qbot that were followed by reconnaissance commands, suggesting they might have turned into a full-fledged ransomware intrusion had they not been remediated. For more on common initial access techniques, see the Trends page.
Lateral movement
Adversaries moving from unmonitored parts of the network is often the first hint at a ransomware intrusion in progress. For this stage, adversaries commonly use compromised accounts obtained from credential dumping wherever they gained initial access, often using tools like Mimikatz. Once they had credentials, we observed adversaries moving via SMB, RDP and WMI, often assisted by tools like Impacket.
As adversaries achieved necessary execution during lateral movement, we observed tried-but-true LOLbins like Rundll32. We also observed adversaries downloading and using remote monitoring and management (RMM) tools like AnyDesk, FleetDeck, and others to facilitate lateral movement as well as persist in the environment.
Reconnaissance
As adversaries landed on new systems, we regularly observed them conducting reconnaissance with the usual built-in commands: ipconfig, whoami, net, and nltest. Additionally, we observed adversaries using tools like SoftPerfect Network Scanner (netscan.exe) and ADrecon to assist.
Exfiltration and extortion continue
A trend that continued in 2023 is the shift toward exfiltration and extortion, often without encryption at all. It’s clear that adversaries aren’t just encrypting data anymore, they’re stealing it as well, then demanding payment or threatening to leak the data. As reporting by Recorded Future shows, posting stolen data has become the de facto standard for leading ransomware/extortionware actors. Some defenders track exfiltration and extortion activities under the umbrella of ransomware, which can be helpful since some adversaries exfiltrate and encrypt data. However, we encourage defenders to be clear about which operators commonly achieve which objectives, since these outcomes require different types of responses.
Affiliates make for increased attribution challenges
The “ransomware-as-a-service” (RaaS) ecosystem continued to present challenges to defenders in 2023. As in previous years, adversaries teamed up during ransomware intrusions, with one actor (often called an “initial access broker”) gaining initial access to a network and then passing off access to other actors. SocGholish, Qbot, and Raspberry Robin are examples of our top 10 threats that are often delivered via initial access brokers that later pass off access to separate ransomware or extortionware operators.
In 2023, we observed multiple brokers using similar patterns and TTPs, which made the already-difficult question of attribution even more difficult. For example, we analyzed an intrusion that spawned from Veritas backup software and compared TTPs to our own observed intrusions as well as community reporting. While some TTPs overlapped with what Mandiant observed from ALPHV, the exploitation of Veritas as well as the use of BITSAdmin were not sufficient evidence to give us confidence in associating the intrusion to ALPHV.
A high-profile incident demonstrating the attribution challenges of the ransomware affiliate model occurred in September 2023 when MGM Resorts experienced a ransomware intrusion. While some reporting attributed the incident to ALPHV/BlackCat actors, other reporting later attributed the incident to the group SCATTERED SPIDER, an affiliate of ALPHV. This incident serves as just one example of the challenges of clustering loosely affiliated adversaries; ransomware/extortionware actors will likely continue to strain the traditional CTI notion of a tracked group under a single name.
Takedowns and disruptions
Ransomware trends were not all doom and gloom in 2023, as law enforcement entities took action to disrupt multiple actors. A prominent example was the FBI’s deployment of a decryption tool to decrypt data from ALPHV/BlackCat intrusions. Another example included the international law enforcement and judicial partnership to arrest actors and take down Ragnar Locker infrastructure.
A notable ransomware-adjacent disruption occurred as Microsoft, Fortra, Health-ISAC, and law enforcement partners took action to disrupt the use of Cobalt Strike by adversaries such as ransomware operators. While we at Red Canary observed Cobalt Strike being used in some intrusions (including those that looked like they might lead to ransomware), notably, we did not observe it as commonly as we did the prior year. Last year, Cobalt Strike was our eighth most prevalent threat, and this year it dropped to #19. While it’s impossible to establish causation with absolute certainty, it’s possible that the community’s collective disruption efforts resulted in this reduction.
Take action
The good news for defenders is that even though new techniques and tools have emerged, many ransomware techniques have remained the same for the past several years. Continuing to focus on detection across the entire ransomware intrusion chain—particularly ransomware precursors—remains an effective strategy to ensure ransomware incidents have minimal impact. The tried-and-true guidance of patching known vulnerabilities remains a solid approach to preventing initial access, as many ransomware intrusions start this way. If an organization can’t keep up with patching all vulnerabilities, we recommend prioritizing based on vulnerabilities in internet-facing devices that are also in CISA’s Known Exploited Vulnerabilities catalog.
Detection opportunities
When it comes to detecting ransomware, the earlier you detect it, the better. While you may not be able to prevent initial access, having detection in depth along multiple intrusion phases will increase the likelihood of identifying ransomware precursors before the intrusion gets to exfiltration or encryption. We encourage you to check out the following other TDR pages for detection opportunities along multiple precursor phases prior to exfiltration or encryption:
- Initial Access: Qbot, SocGholish, Raspberry Robin
- Reconnaissance: BloodHound
- Credential Dumping: Mimikatz, LSASS Memory
- Lateral Movement: Cobalt Strike, Impacket, Ingress Tool Transfer
As adversaries conduct discovery about the environment, we’ve found they regularly perform similar commands. The following detection analytic can help identify nltest behavior that helps an adversary learn more about domain trusts. Of course, if this is a command that is commonly run in your environment, you’ll need to tune it, but in our experience nltest is fairly uncommon.
command == ('nltest /domain_trusts')If the activity makes it all the way to ransomware, the following detection analytic reliably identifies adversaries deleting volume shadow copies. This is something we see the majority of ransomware groups do if they encrypt data and cause impact. While this is a detection of “last resort,” if you detect at this point and act quickly, you may be able to prevent further lateral movement and encryption.
command == ('vssadmin.exe delete shadows')Testing
Start testing your defenses against Ransomware using Atomic Red Team—an open source testing framework of small, highly portable detection tests mapped to MITRE ATT&CK.
Getting started
The best strategy for testing your defenses against ransomware is actually to emulate and test your ability to detect the precursors that commonly deliver ransomware as a later stage payload. Likewise, consider exploring the testing sections in this report for:
In addition to that, T1490: Inhibit System Recovery includes relevant tests for deletion of volume shadow copies and T1482: Domain Trust Discovery includes tests that leverage the nltest command to discover information about domain trust relationships.
Review and repeat
Now that you have executed one or several common tests and checked for the expected results, it’s useful to answer some immediate questions:
- Were any of your actions detected?
- Were any of your actions blocked or prevented?
- Were your actions visible in logs or other defensive telemetry?
Repeat this process, performing additional tests related to this technique. You can also create and contribute tests of your own.