Key benefits
24x7 detection and response
Backed by our team of Linux and Kubernetes security experts who help monitor your environment to identify threats and provide support and proactive security guidance.Custom built by Linux experts exclusively for Linux
Protect against Linux-specific threats with comprehensive coverage across a wide array of Linux distributionsFlexible and lightweight deployment
Our agent is lightweight so you can monitor production Linux deployments with minimal performance impact or downtimeWhat we detect
Runtime security threats
Our runtime code analysis validates authenticity, identifies suspicious dynamic code execution, and detects malicious code.
Container activity
Orchestration-ready with support for Kubernetes, AWS ECS, AWS EKS, Azure AKS, and Google GKE deployments. Our continuous threat monitoring captures container visibility for the lifetime of the container, whether it’s ephemeral or long lived.
Cloud workload behavior
Identify and monitor workloads across cloud platforms enriched with instance and container metadata, including details about the cloud provider, account ID, region, machine image, platform, and more.
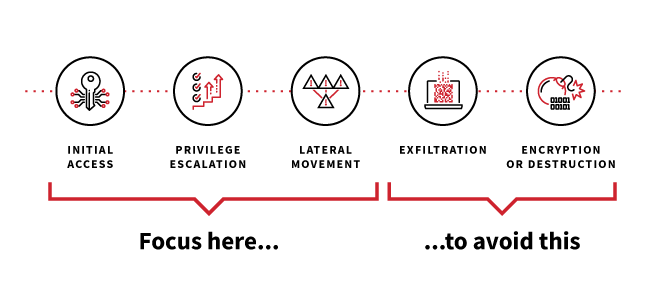
Red Canary optimizes for detecting and responding rapidly to early-stage adversary activity
"I've not been thrilled with other Linux agents, but the Red Canary option has been great. You made what we wished every other Linux agent would do and made it lightweight and effective.”

We find and stop threats, no matter where adversaries choose to attack
Red Canary Managed Detection and Response (MDR) combines trailblazing security technology and human expertise to detect threats earlier and stop them faster.
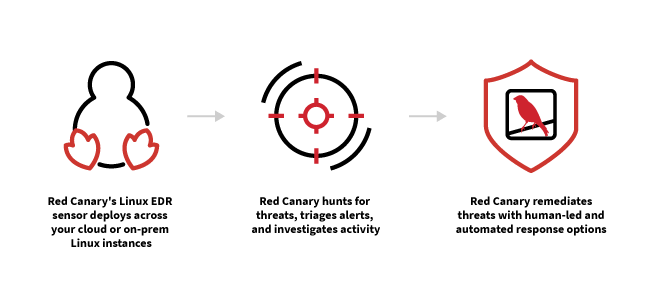
- Data is ingested from production Linux environments, containers, Kubernetes, and cloud workloads.
- Thousands of behavior-based detections and proprietary threat intelligence are applied to hunt for suspicious activity.
- Our team of experts investigates activity, eliminates noise, and correlates events from disparate sources.
- View investigations in a unified timeline, written in clear language with all the necessary context, making it easy to understand the root cause and scope of a threat.
- Take action with our combination of automated and human-led response capabilities.
learn about Linux EDR