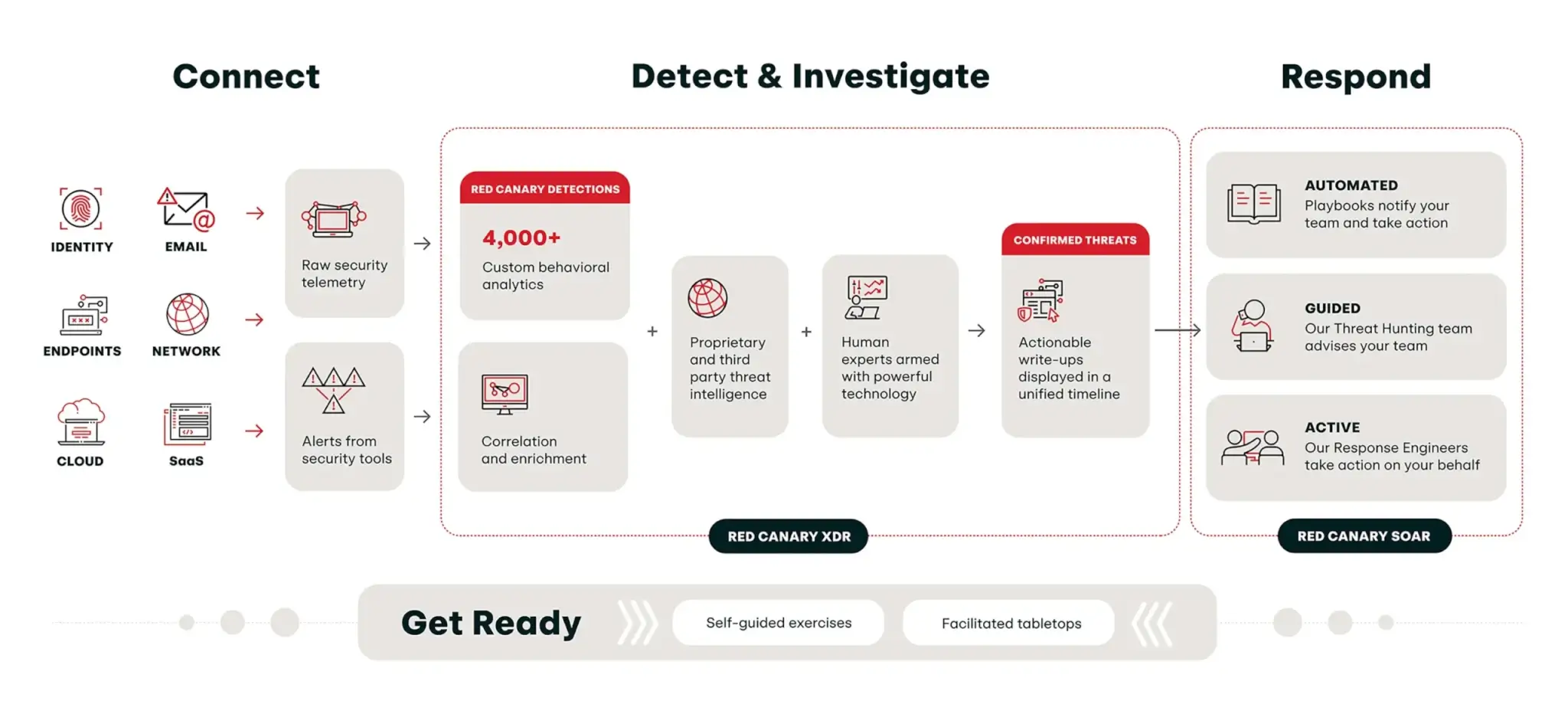
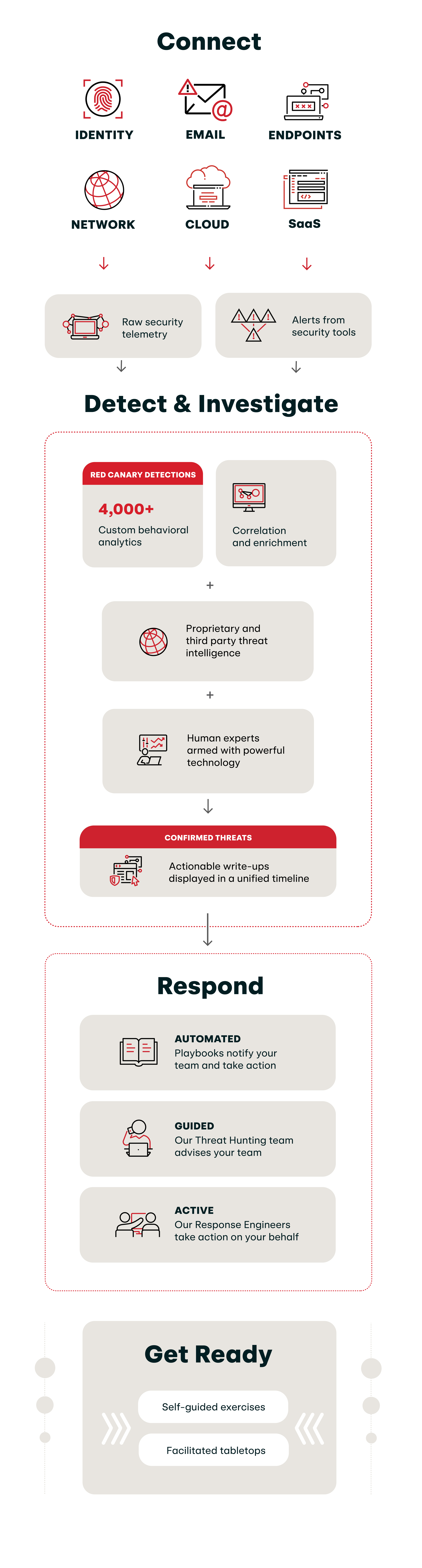
Augment your security team
Cybersecurity for Education Institutions
24×7 managed detection and response to protect sensitive student and institutional data
Bolster your defenses: Prevent unauthorized access, credential theft and ransomware attacks

The problem
The education sector continues to be an attractive target for threat actors. According to Zscaler, ransomware activity against the education sector increased 25% in 2024. If security teams wish to stay ahead of threat actors, security professionals need a proven method to effectively address the ransomware intrusion chain, and phishing attacks.
Detect adversarial activity before it impacts your students and instructors
Defend against ransomware and phishing attacks targeting K-12 and higher education with Red Canary. Our vendor-neutral approach supports our teams ability to focus on ransomware precursors and stop threats before they cause harm.
Discover the top techniques used during ransomware campaigns, and how to deploy open source tools to test your defenses.
Ransomware detection toolkit
The Red Canary difference
Unmatched threat detection, unbeatable accuracy, and quality at scale-so you can focus on what matters most. Learn more
Prioritize specific threats to improve your security posture
To say students safety is important is an understatement. Similarly, protecting educational institutions data is critical to ensuring the ongoing delivery of education for students and teachers alike. Success starts with focusing on the most acute and specific threats impacting your institution. The 2025 Midyear Update to the Threat Detection Report is a great place to start. Learn how actionable intelligence can meaningfully impact your security program.
Related Resources
Business Email Compromise
Learn how to protect your institution from this prevalent, impactful risk
Ransomware Toolkit
Stop ransomware precursors in their tracks with these guides, and open-source tools
User Protection Guide
Navigate the complexities of user identity protection with this insightful resource