Managed Detection and Response Services
Detect and stop threats 24×7 across your endpoints, identities, cloud and beyond.
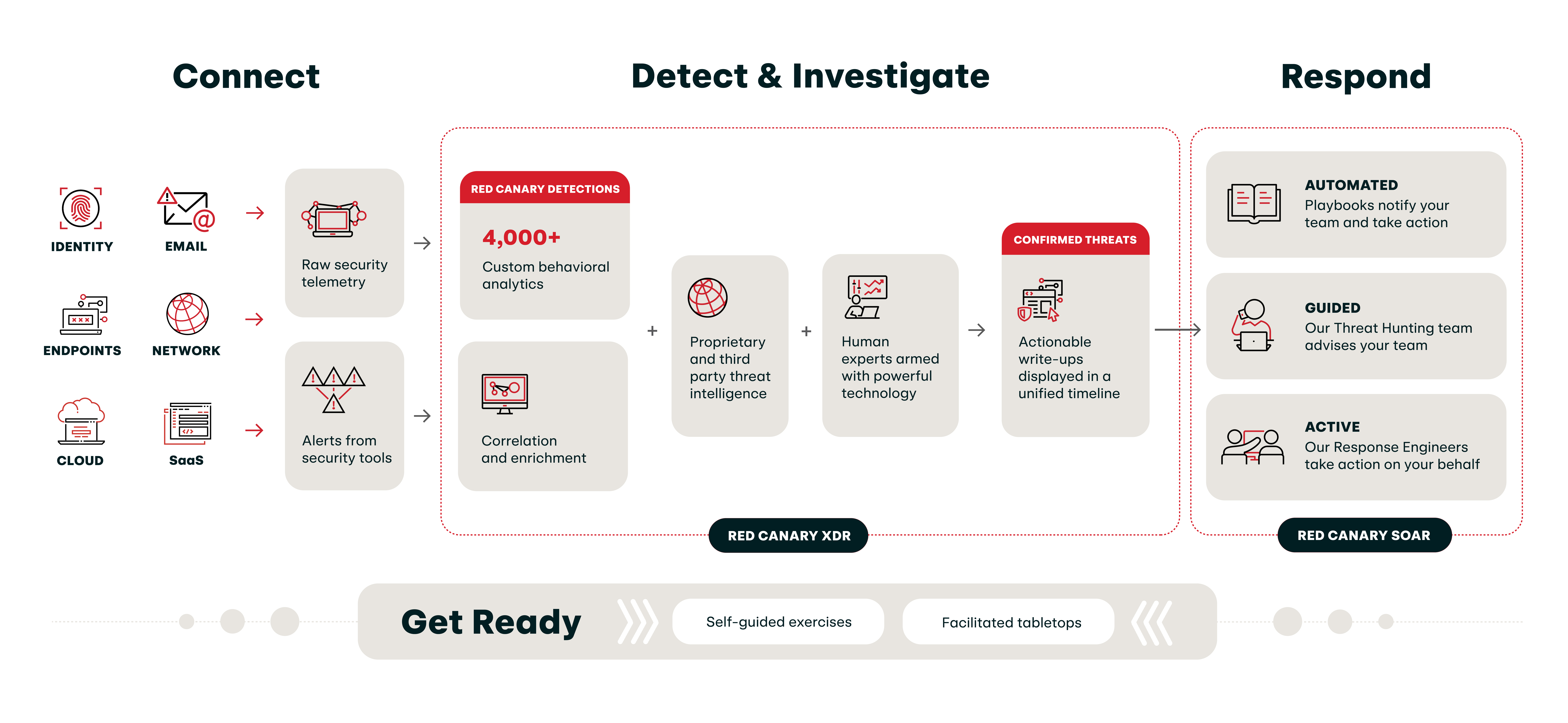
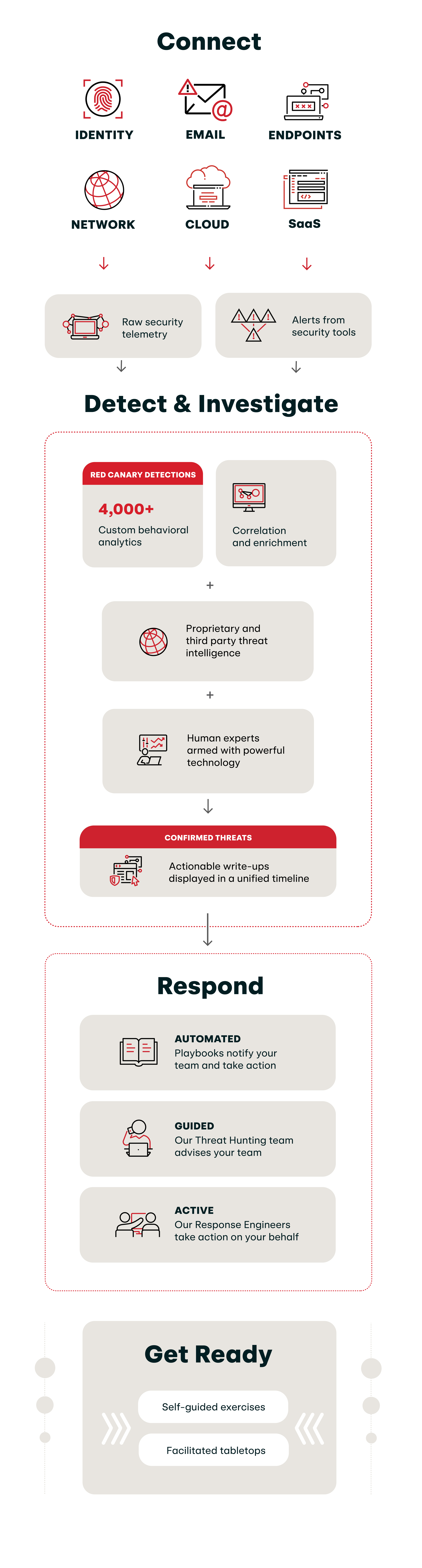
Intelligence-led security across your environment
Connect your security alerts and telemetry. We will pinpoint threats and help you respond 24×7.
-
Unmatched threat detection: 99+% true positive rate keeps your focus on signal, not noise
-
Actionable threat intelligence: On-demand adversary insights and expert collaboration
-
24x7 expert response: Guided, automated, and human-led capabilities so you can sleep
Stop prevalent threats across critical domains
Endpoints
- Credential theft
- Malware
- Ransomware
- Reconnaissance & espionage
- Unmanaged devices (IoT)
Identities
- Account compromise
- Unauthorized access
- Business email compromise
- Brute force attacks
- MFA attacks
Cloud
- Compromised user credentials
- Misconfigured environments
- Runtime threats
- IAM role abuse
- Data exfiltration
“Red Canary takes the intelligence they see across their customers’ environments and applies it immediately to us. That visibility and context fuels our own threat hunting and speeds up our reaction.”

Integrations
Get more value from your tools
Red Canary analyzes alerts and telemetry across multiple products to stop threats before impact.

What it means for you
No more wondering. As soon as it happens, you’ll know.
We only notify you of cyber threats that matter. Our notifications are accurate, complete, and timely so that you can quickly go from awareness to action. Multiple Red Canary experts validate threats before we alert you, ensuring you focus on real threats and not false positives.
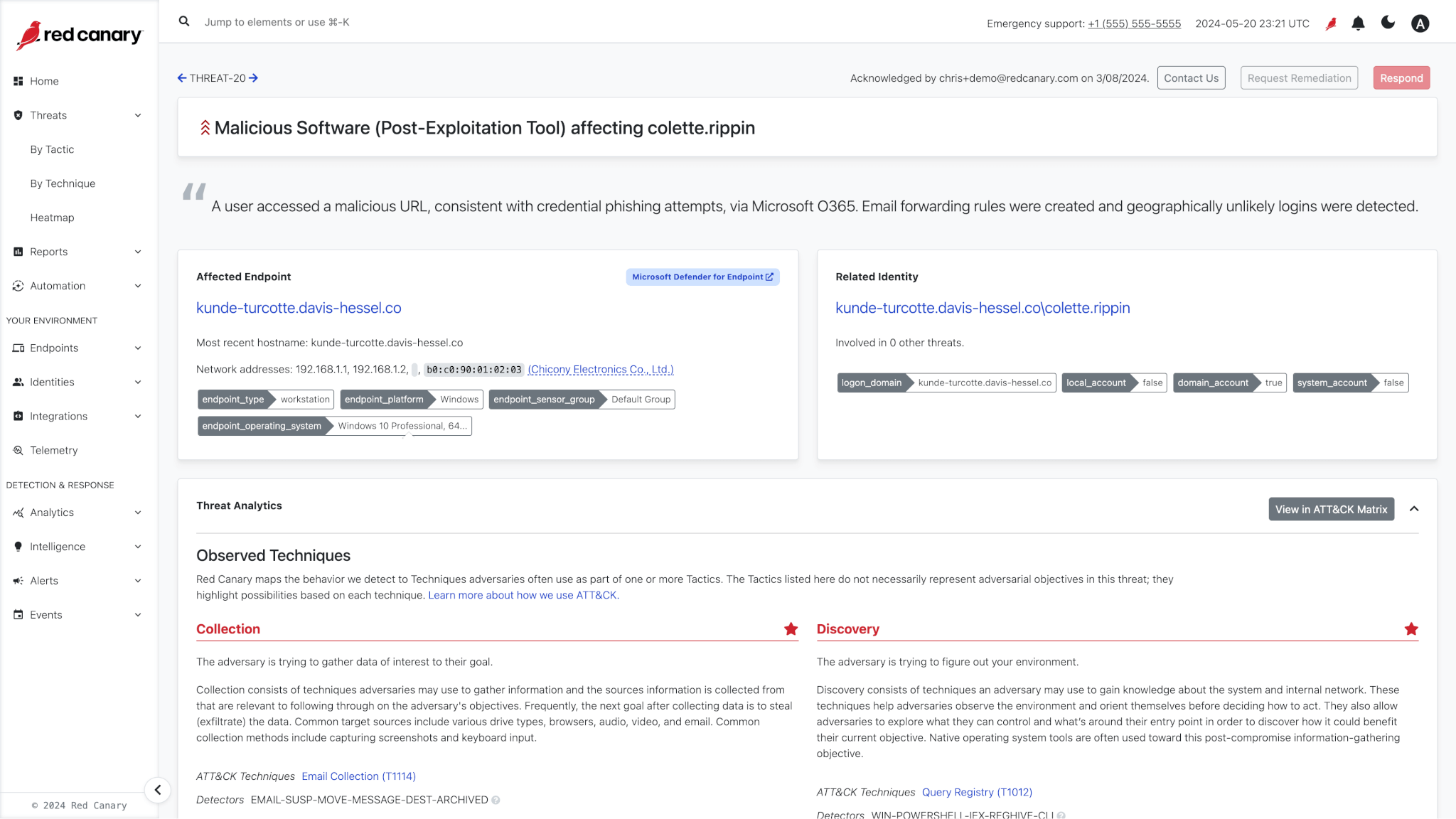

Find the needles in the haystack.
Red Canary identifies threats that you’d otherwise miss, and we show you the data to prove it. 4,000+ behavioral analytics alongside automated and ad-hoc threat hunts uncover elusive adversary activity.
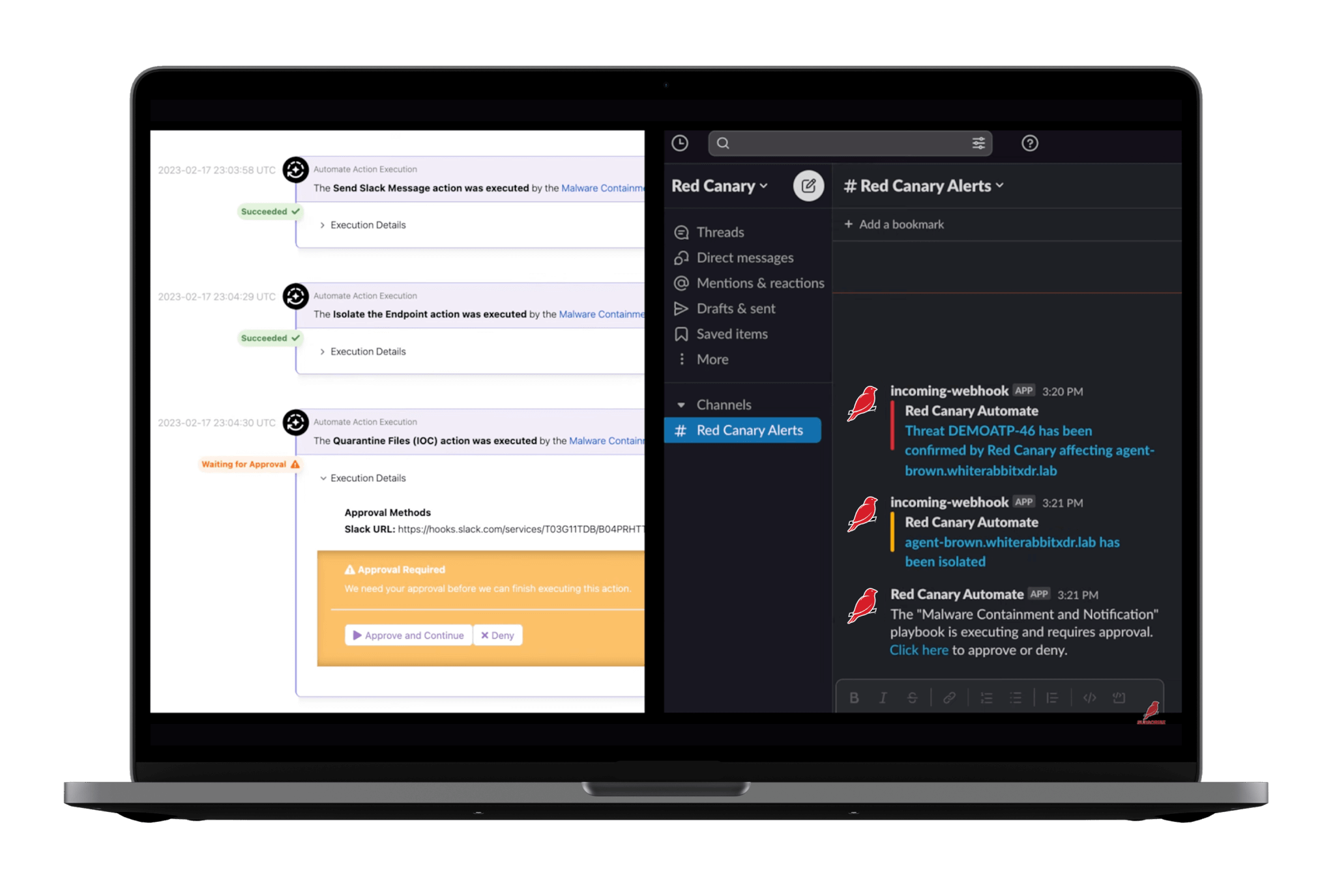
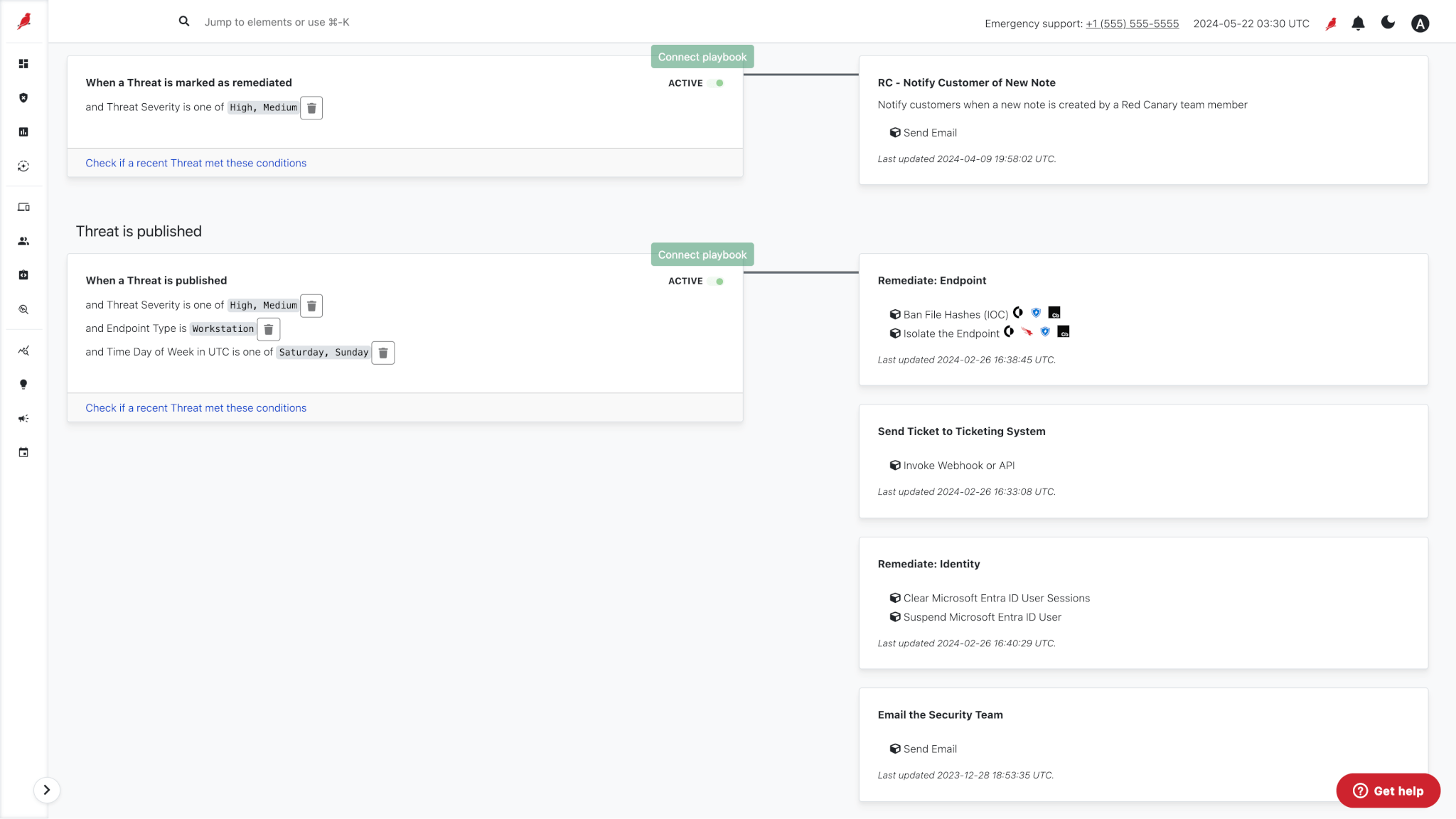
Respond, recover, and improve.
Automate response through playbooks that integrate with your collaboration tools, incident management, and security products. Would you rather have Red Canary’s experts handle the remediation? No problem. We got you.
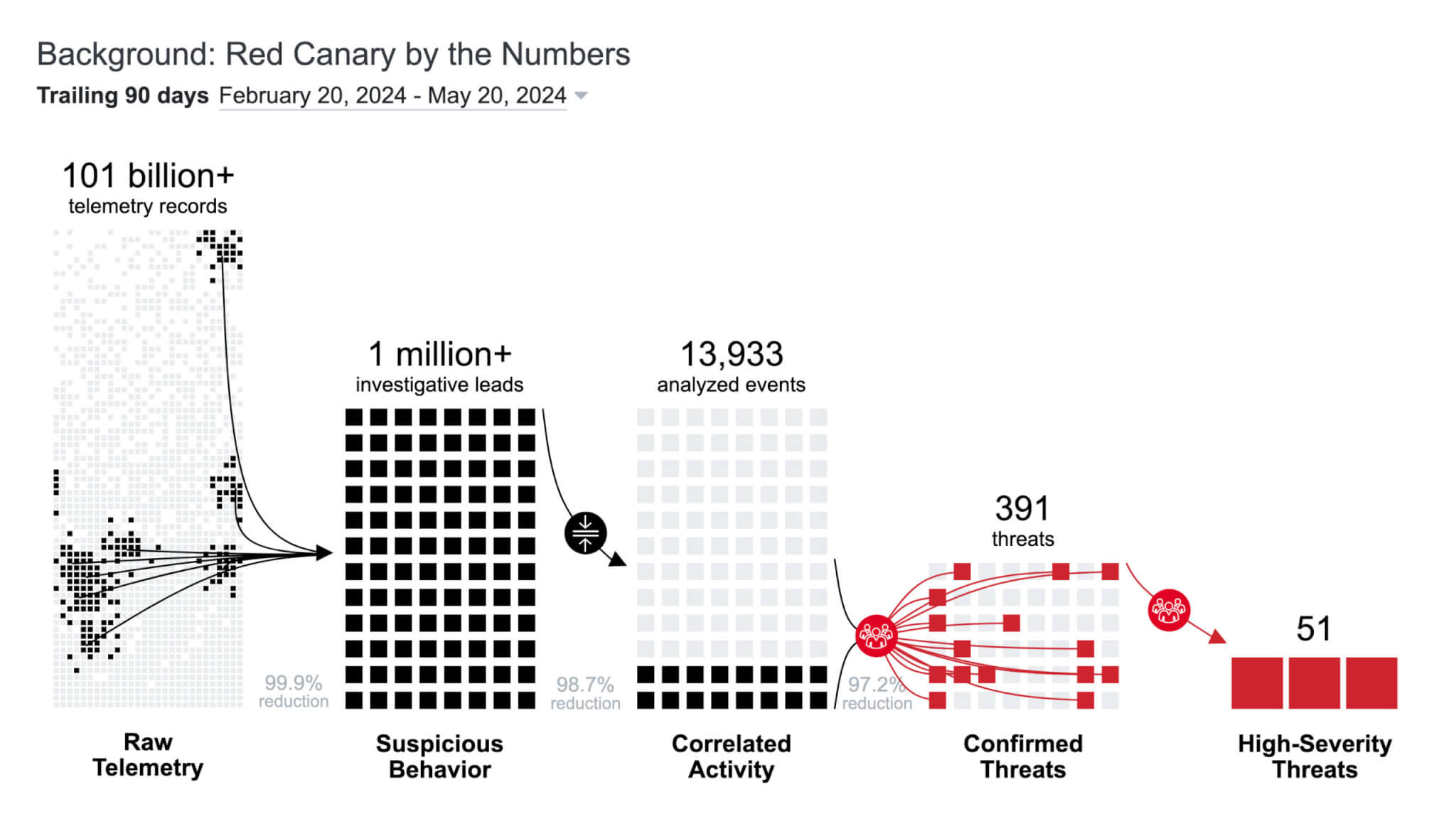
Quantify improvements to your security program
We are fully transparent as to the volume of data we analyze, suspicious events we detect, and threats we stop. With the average cost of a data breach eclipsing $4.4M, it’s easy to measure risk reduction based on the number of threats Red Canary neutralizes.
Why security teams partner with Red Canary
Your organization is unique, and so is our ability to solve your challenges. Explore the use cases below to see how other teams are using Red Canary MDR to improve security outcomes.