UPDATE: On November 16, 2022, we updated this blog to include information about a relevant Windows security update that emerged after publication and to include more details about mitigation, prevention, and detection.
Editor’s note: This blog was written by a Red Canary detection engineer who uses the pseudonym “Han Shan.”
Red Canary’s Detection Engineering team has observed an increase in adversaries using malicious disk images (specifically, .iso files) as a form of initial access. Rather than luring targets with the more commonly known .zip file, adversaries across the threat spectrum from ChromeLoader to Cozy Bear have started using a file format that many typical users might not recognize or consider a threat.
There are two big reasons an attacker might use an .iso file (also called ISO images) for their initial compromise. First, security practitioners are used to seeing threats arriving in the form of .zip files. Subsequently, many modern security controls readily detect these files. It’s become a commonplace technique. On the other hand, utilizing ISO images can help an adversary evade any security checks designed to look for zipped files.
Second, ISOs let an adversary bypass a Windows security control called Mark-of-the-Web (MOTW) more effectively than ZIPs. MOTW plays a key role in how Windows tries to protect users from downloaded threats. Fully understanding how MOTW works can help security teams build better protections that fill the control’s shortcomings (and if your security posture includes rules that detect on ZIP files but not ISOs, this blog will hopefully explain why you should be looking for both).
Wait, what’s an ISO file?
Great question. For many of us nerds tech and security professionals, our first interaction with .iso files might have occurred when we downloaded our first Linux distribution or some other operating system to run in a virtual machine. These files are commonly called ISO images, borrowing their name from the ISO 9660 file system used with CD-ROM media.
In a nutshell, an ISO image is an entire optical disk (DVD, CD, Blu-ray) stored in a single file. They are similar to .rar and .zip files in that ISOs are a single file that can hold many files within it, however, ISOs do not use any compression. They are exact copies of optical disks, sector by sector, to include the disk’s file system (remember this fact, it will be important later).
Common uses for ISO images include storage and backup for optical disks and anything from video games to fully configured operating systems. “Executing” an ISO image usually involves mounting it like you would with external media. From there, the system will treat the file like any other removable drive. However, you can also use third-party tools like 7Zip to extract and view the contents of the file without having to mount it. This latter option again makes ISO images functionally similar to compressed files like ZIPs.
What is Mark-of-the-Web (MOTW)?
It’s not what happens when an internet wizard curses a file and puts a lightning birthmark on its forehead. Though, that’s not the worst metaphor we’ve heard for MOTW.
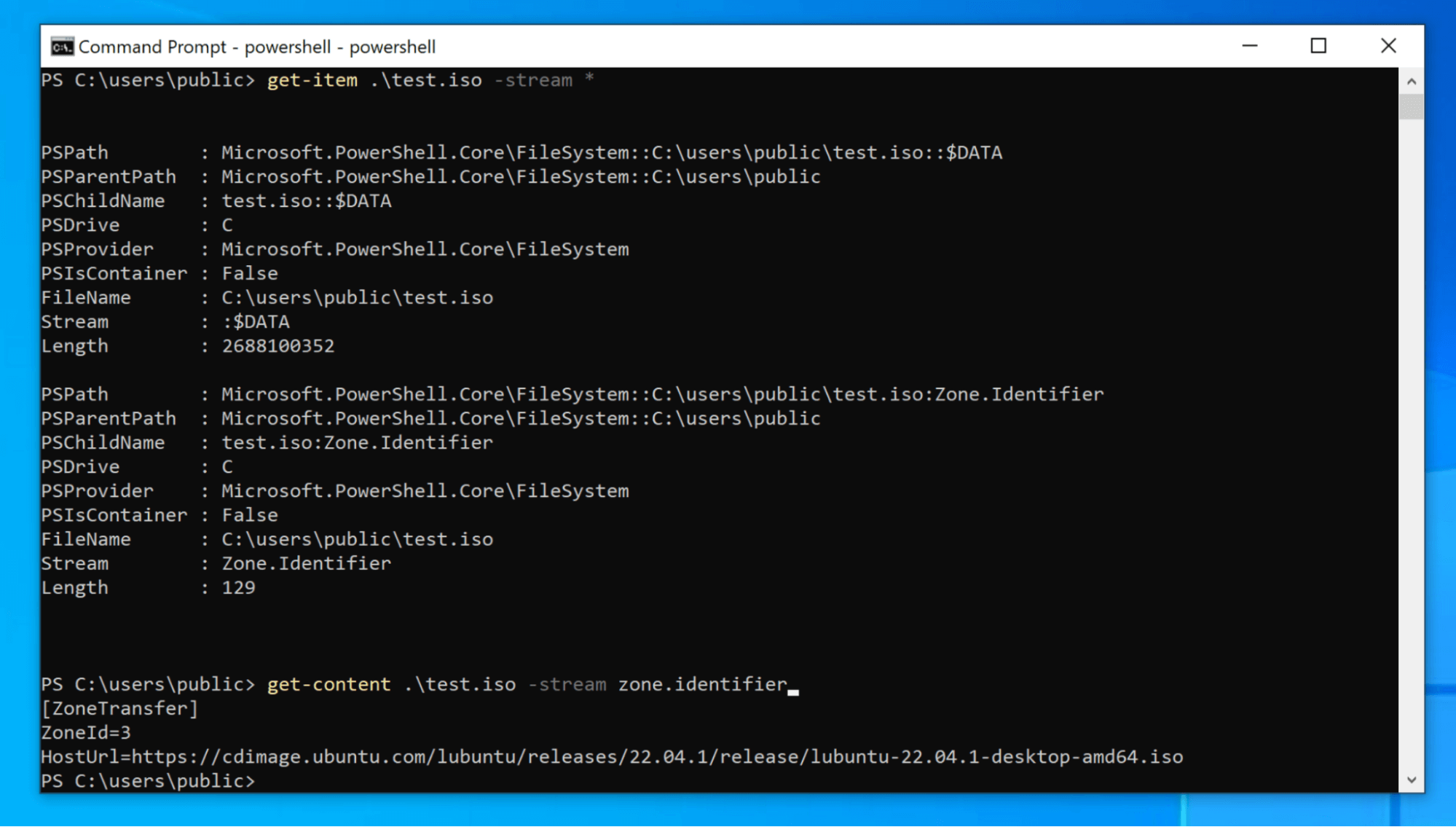
In Windows, files downloaded from the internet receive a special hidden value that gets assigned to the Zone.Identifier Alternate Data Stream (ADS). This value is commonly known as the MOTW. In reality, it is simply a ZoneID value of 3, which is the ZoneID number for the internet (a ZoneID of 0 means a file from the local computer, 1 is from the local intranet, 2 is trusted sites, and 4 is restricted sites). In the below image, we used some basic PowerShell commands to view the ZoneID of a downloaded file and you can see the ZoneId=3 at the bottom of the window.
If a file has this value, Windows prevents it from performing certain actions. When you download a Microsoft Office document and it opens in “Protected View,” that’s MOTW at work.
Any executable files tagged with MOTW get processed by Windows Defender SmartScreen. Defender then checks to see if the binary is on an allowlist of well-known executables. If the file is not on the list, it gets blocked from executing and a warning is passed to the user.
Mark-of-the-Web bypasses
That’s all MOTW really is, a value assigned to an Alternate Data Stream (ADS) that Windows is on the lookout for. Sort of like an internet wizard cursing a file by branding the number 3 on its forehead. And the number 3 could be made to look like a lightning bolt, so the metaphor works:
More importantly, due to how this security feature is implemented, there are some limitations and MOTW is not a catch-all solution. For example, some software does not assign Zone Identifiers to downloaded files. Git is a known example. If Git assigned the MOTW to every file you downloaded when pulling a repository, it would be a hassle to identify which files need special permissions and reassign their ZoneIDs.
7Zip sometimes assigns the MOTW to extracted files and sometimes doesn’t. It depends on how the user opened the file. If the user double clicks a file from the 7Zip GUI so that the file is extracted to the temp directory and then opened, MOTW is assigned. However, if the user clicks on the extract button in 7Zip rather than just double clicking, MOTW is not assigned. Git and 7Zip are just two well known examples of software that allows downloads without MOTW.
An additional limitation of MOTW is that ADSs are specific to the New Technology File System (NTFS). Other file systems can’t have MOTW assigned because they don’t have ADS. Remember how ISO files are exact copies of optical disks to include the disk’s file system? This means that, while the .iso itself is marked (see the above screenshot), the files inside the .iso cannot have MOTW assigned to them because the file system doesn’t support ADS. Furthermore, MOTW does not prevent a user from mounting the disk image. Thus, when a user mounts an ISO image or extracts its contents, anything inside is treated the same as local files rather than dangerous files from the internet. This is what makes ISO images an ideal file format for adversaries to bypass this Windows security feature.
Building defenses around MOTW’s gaps
Now that we understand MOTW’s limitations and why .iso files are so useful for adversaries, we can build both defenses and awareness.
Mitigation
On November 8 2022, Microsoft patched a vulnerability that enabled adversaries to bypass certain MOTW security features. Installing the update that closed this bug is a good starting point. The patch reportedly mitigates the technique described earlier in this blog, whereby an adversary can bypass MOTW protections by hiding malicious payloads in an ISO file.
Prevention
MITRE ATT&CK recommends disabling the ability for users to auto-mount disk image files (this includes files like .vhd). Users can still manually mount these files, but the extra, deliberate steps involved should reduce the number of accidental compromises.
Group policy objects offer one way of doing this, and many organizations implement some variation of the following:
Regedit -> HKEY_CLASSES_ROOT -> Windows.ISO.File -> shell -> delete 'mount' and Regedit -> HKEY_CLASSES_ROOT -> Windows.VHD.File -> shell -> delete 'mount'
This prevents users from double-clicking and auto-mounting an ISO file. They can still mount an ISO file via the command line or other means, but clicking on a malicious ISO file in an email message, for example, will display a simple error message rather than executing the file.
If your organization allows, you can also fully block disk images at the web gateway, but this could hamper legitimate use of ISO files. A better option might be to block these files for certain categories of uses, as disk images are likely not common files needed for every department. Blocking downloads of disk images specifically from email clients may help as well because there are very few legitimate use cases for these files to be emailed. Remember, unlike ZIP files, disk images are not compressed, so most authentic disk images are too large to email anyway.
Detection
If you can’t block them outright and a disk image comes through to your inbox or you download a file from the web and it turns out to be an ISO, think about what the file is purporting to be and whether or not that file format makes sense. For example, a common email phishing attack includes attaching an “invoice” to the email. We have observed adversaries sending fake invoices formatted as ISO images. This raises eyebrows for our detection engineers analyzing telemetry because there is no legitimate reason for an invoice document to be formatted as a disk image. In fact, Red Canary has detection analytics that specifically look for files with an .iso extension where the name matches common phishing themes:
filemod_includes [.iso]
&&
file_path_includes ['Users' & 'Downloads'] || [‘AppData’}In certain smaller environments, you may be able to get away with watching for any ISO and similar file modifications, but that could have the unintended consequence of overwhelming your team with false positives. However, it’s worth considering something like this:
filemod == ISO || VHD || IMG
Security teams may be able to develop detection around a relatively obscure Windows Event log: Microsoft-Windows-VHDMP-Operational. Event ID 1 will populate whenever anyone mounts a virtual hard disk. Event ID 2 lets you know if the drive remains active. And event ID 12 populates with specific information about the mounted device.
Emulation
Whether or not these detection ideas are prohibitively noisy will be self-evident, but you’ll still want to safely test whether or not the preventive and detective controls actually work. Luckily, we’ve Atomic Red Team tests that emulate varieties of malicious ISO usage. Tests number 1 and 2 for T1553.005: Subvert Trust Controls: Mark-of-the-Web Bypass are a great starting point to test your mitigatory, preventive, and detective controls.
Know your mark
We hope this blog helps you better understand why adversaries use ISO images as initial delivery vehicles. While Mark-of-the-Web is effective in blocking some threats, knowing its limitations around certain file formats like ISOs can help you defend accordingly and make the right analysis decisions.