Cloud adoption has drastically altered traditional network architectures and ushered in the need for greater visibility into the perimeters of the network. Advancements in detective and preventive security technologies have forced attackers to shift their strategies from relying on malware and overt payloads to focusing on compromising user identities.
This is evident by the year-over-year increase in identity-based attacks such as phishing campaigns and credential theft reported in the 2021 Verizon Data Breach Investigation Report. Detection and prevention of these attacks is a key defense strategy to safeguard organizational data from unauthorized access. To attenuate this risk, Microsoft has developed several powerful solutions for businesses to protect identities from suspicious or fraudulent activity.
In this blog, we’re going to compare Microsoft Defender for Identity with Azure Active Directory (AD) Identity Protection. We’ll explore the functional differences, review some of the common threats that are mitigated by both, and provide high-level guidance on selecting the optimal product to reduce businesses identity risks.
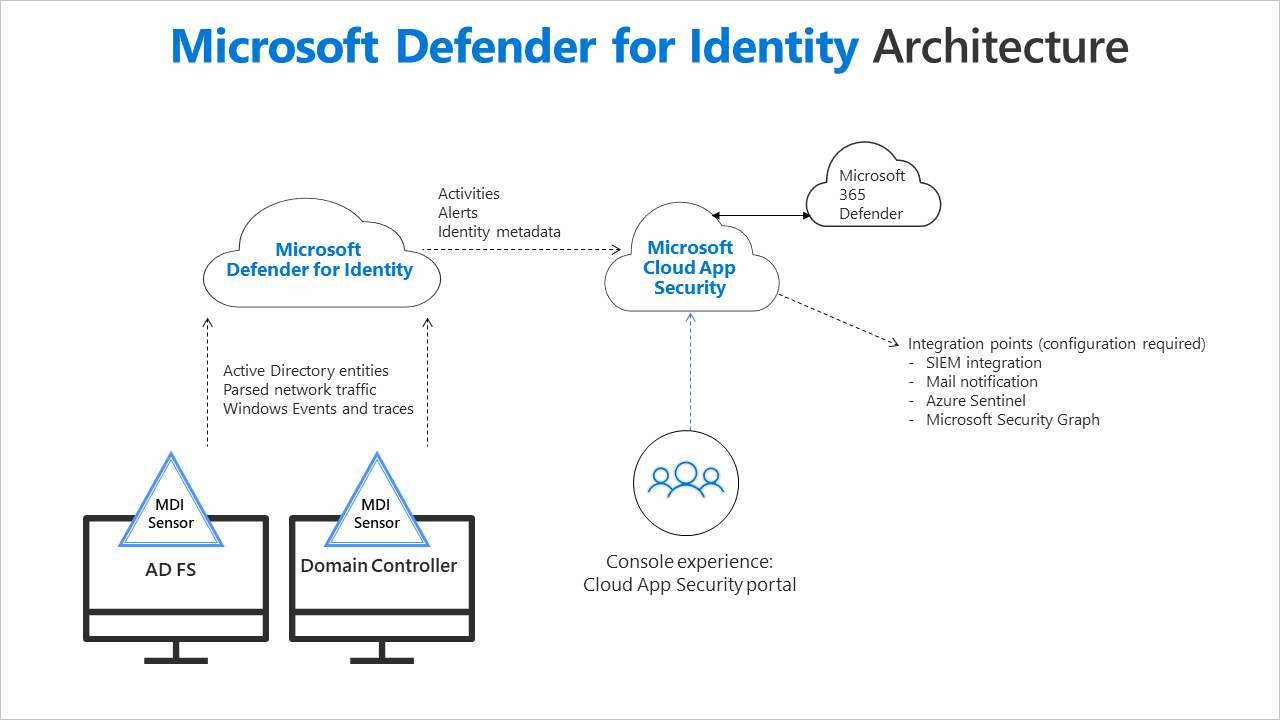
Microsoft Identity Protection architecture
Both Microsoft Defender for Identity and Azure AD Identity Protection work to defend Microsoft-based domain accounts. However, there are noteworthy architectural differences between the two services, which necessitate deployment configurations in the Microsoft domain environment and licensing. Additionally, supported product capabilities and available integrations are also different.
Defender for Identity is more flexible for on-premise deployments and examines a broader variety of information—including the ability to monitor network traffic. Defender for Identity supports detection for on-premise attacks in AD Federated Services (ADFS) hybrid deployments. Defender for Identity also supports integration into the broader Microsoft XDR environment, including Microsoft 365 Defender and Cloud App Security.
Image courtesy of Microsoft documentation
Azure Active Directory Identity Protection, on the other hand, lives solely in the Azure cloud and combats threats against Azure Active Directory instances. Azure Activity Directory (AAD) Identity Protection product design displays a tight integration with Azure Active Directory, working to enforce policies and automate detection and remediation of identity-based risks.
Defender for Identity
Defender for Identity contains three major components:
- The Defender for Identity portal is hosted in the Azure cloud and presents a unique instance to the customer, enabling them to monitor and manage Defender for Identity.
- The Defender for Identity sensor is the software component that administrators can install on a target server or local installation to collect telemetry from Active Directory Domain Services (ADDS) enabled, on-premise servers. The sensor captures data in several ways, including network traffic capture and local domain event data monitoring. Microsoft identifies suspicious and malicious activity—and generates alerts and warnings in the Defender for Identity portal accordingly—by applying machine learning, baselining, and behavioral algorithms to this traffic and these events.
- Defender for Identity cloud service is a backend component of Defender for Identity, hosted by Microsoft in the Azure cloud. This service is transparent to the end user, and connects Defender for Identity to the Microsoft Intelligent Security Graph API and other services that enable Defender for Identity to integrate into the larger Microsoft security ecosystem.
Microsoft 365 Defender
Defender for Identity and Azure AD Identity Protection currently contribute identity-related alerts and information into the incidents and alerts present in Microsoft 365 Defender. To learn more about Microsoft 365 Defender, you can check out our Crash Course on Microsoft 365 Defender, a three-part video series in which we provide an overview of the XDR platform and walk you through a simulated threat in both the Microsoft console and Red Canary.
Cloud App Security
In addition to the Defender for Identity portal, Microsoft displays Defender for Identity alerts within the Cloud App Security Alerts queue. Alert queues are independent to each service, so security teams should be careful to avoid duplicate alert entries if they’ve enabled SIEM forwarding.
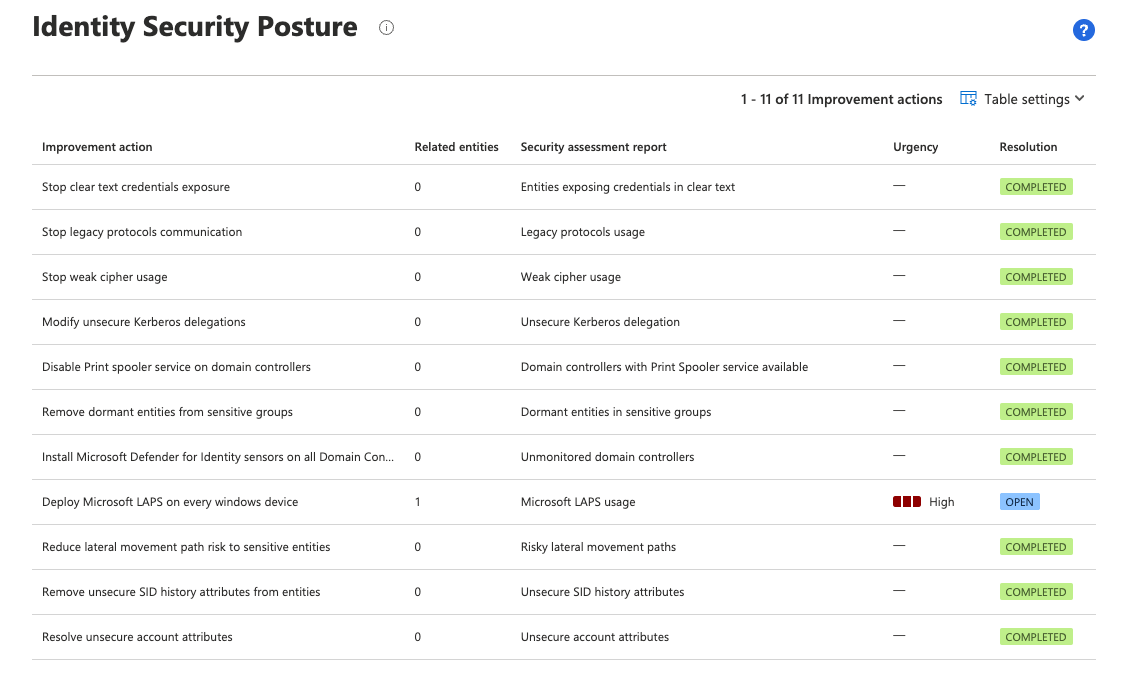
Cloud App Security and Defender for Identity are tightly integrated in other ways as well, with Defender for Identity’s security posture assessments feature located in Cloud App Security.
Security posture assessments powered by Defender for Identity and hosted in Cloud App Security provide an easy way to identify common misconfigurations, legacy components, and other identity risks within the Microsoft security ecosystem. Focusing particularly on identity, these risks include (but aren’t limited to):
- dormant entities
- legacy protocol usage
- weak cipher usage
- insecure Kerberos delegation
You can quickly gather a variety of useful reporting metrics from the Cloud App Security portal:
Azure AD Identity Protection
Azure AD Identity Protection is a collection of identity controls built into Azure AD that provide policy management, enforcement, and notifications.
As a sub-component of Azure AD, Azure AD Identity Protection is only compatible with organizations that leverage the Azure AD service for their Microsoft domain environments.
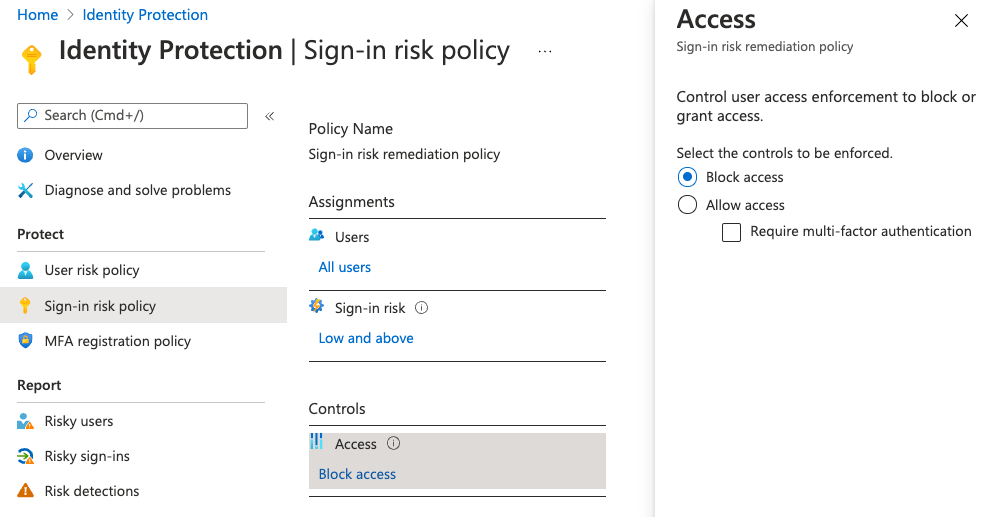
One of the key differentiators for Azure AD Identity Protection is the ability to enforce policy. Administrators are able to do this by setting conditions, which include scoring elements such as “User Risk” and “Sign In Risk” that are calculated based on the probability of a compromised identity or sign in. Whether triggered by an Azure AD Identity Protection alert or telemetry from one of your other security products, Red Canary allows you to create playbooks in our platform that allow you to respond automatically in Azure AD, e.g. by clearing a user’s sessions or suspending them.
Reporting on risky users or risky sign ins provides detailed insights on the metadata that Azure AD Identity Protection used to make determinations about a particular user or sign-in attempt:
Similar to Defender for Identity, Azure AD Identity Protection supports integration with Microsoft Sentinel (Microsoft’s Security Information Event Manager), and makes data—including risky users, risky sign-ins, and detections—available via the Microsoft Graph API.
Identity risks and coverage
Both Azure Active Directory Identity Protection and Defender for Identity work to provide protection against similar threats. For example, there’s some policy overlap that includes coverage for password spray attacks, where adversaries attempt to brute-force compromise multiple accounts using common passwords. Additionally, both services will detect logins from suspicious or unusual IP addresses, brute-force attacks, or other types of account enumeration activity.
Despite the overlap, there’s still a lot of disparity between the two products. Differences include the ability of Defender for Identity to detect high severity on-premise attacks against Windows domain environments such as Kerberoasting attacks, DCShadow attacks, Suspected Golden Ticket usage, and more. Microsoft documentation includes a policy list for Defender for Identity covering all of its various features.
Takeaways for risk management
When you’re making a strategic risk management decision, it’s important to consider an organization’s total attack surface—and the possibilities for managing that attack surface. Applying practical and appropriate mitigations or preventive controls is often more important and effective than simply analyzing or ingesting more data. Both of these solutions will help you mitigate identity threats, but in different ways. As such, it’s important to understand the respective security outcomes you can expect to achieve by using Defender for Identity, Azure AD Identity Protection, or both.
The offline calculation capabilities of Azure AD Identity Protection—and its integration with Microsoft threat intelligence—make it a powerful tool for administrators to easily verify user risk based on user-linked detection capabilities. The integrated nature of Azure AD Identity Protection with the Azure AD provides an enhanced and immediate response capability that is not present in Defender for Identity.
Conversely, even if Azure AD Identity Protection is able to alert on identity issues in a Hybrid Azure Active Directory environment, it will not have the capability to protect or alert on major on-premise attacks that present a serious risk to many organizations. The unparalleled optics of Defender for Identity to expose attackers’ attempts for domain dominance or lateral movement within a network are some of the most powerful ways an organization can limit the potential impact of a major breach scenario.
Based on your organization’s footprint, technology usage patterns, and habits, choosing the right solution or combinations thereof will prove tremendously helpful in detecting and preventing identity-based attacks. Both Microsoft and Red Canary work together to provide end-to-end Identity protection for customers, including the Red Canary MDR support for integration of Defender for Identity and Azure AD Identity Protection alerts into the Red Canary platform. To learn more about Red Canary’s integrations with Microsoft 365 Defender, Microsoft Sentinel, and Microsoft Defender for Cloud, you can check out our MDR for Microsoft page or request a custom demo of our Microsoft capabilities.