From the tactical security implications of Europe’s General Data Protection Regulation (GDPR) to an examination of old cyberattacks with new intel tooling, the seventh annual SANS Cyber Threat Intelligence Summit wrapped up last week in Arlington, Virginia, and it featured a handful of interesting talks.
Without further introduction, here are our favorite talks (in order of appearance):
5. Privacy vs. Security: It’s a Log Story
The event started with a really strong and tactical examination of logging complications brought on by GDPR. Whitney Merrill (an attorney at Electronic Arts who also happens to have a masters degree in computer science) discussed the delicate balance of collecting robust logs for security while also limiting the amount of personally identifiable information (PII) you retain in those logs. To provide just a little bit of context, GDPR vastly broadened the definition of PII and governs how it is handled.
An exploration of GDPR is not exactly what you’d expect as the opening keynote at a threat intelligence summit—let alone a practical discussion from a lawyer about carefully considering what data you actually need to retain in your logs.
Kudos to Merrill on a great keynote. Unfortunately, her slides didn’t make it up on SANS’s site, so we can’t share them with you.
4. ATT&CK™ Your CTI with Lessons Learned from Four Years in the Trenches
Our very own Brian Beyer and MITRE’s threat intel lead, Katie Nickels, discussed how security teams can use the ATT&CK framework as a mechanism for discussing threat intelligence and adversary behaviors across teams and organizations. Perhaps more importantly, ATT&CK offers security teams a structure they can follow to help them transition away from tracking adversaries based on indicators and toward tracking them based on behavior.
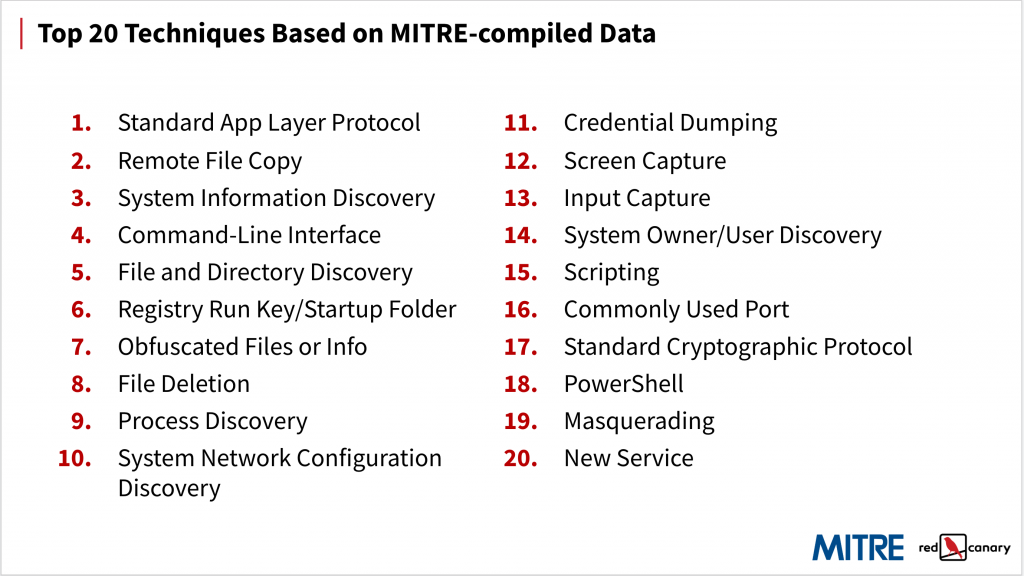
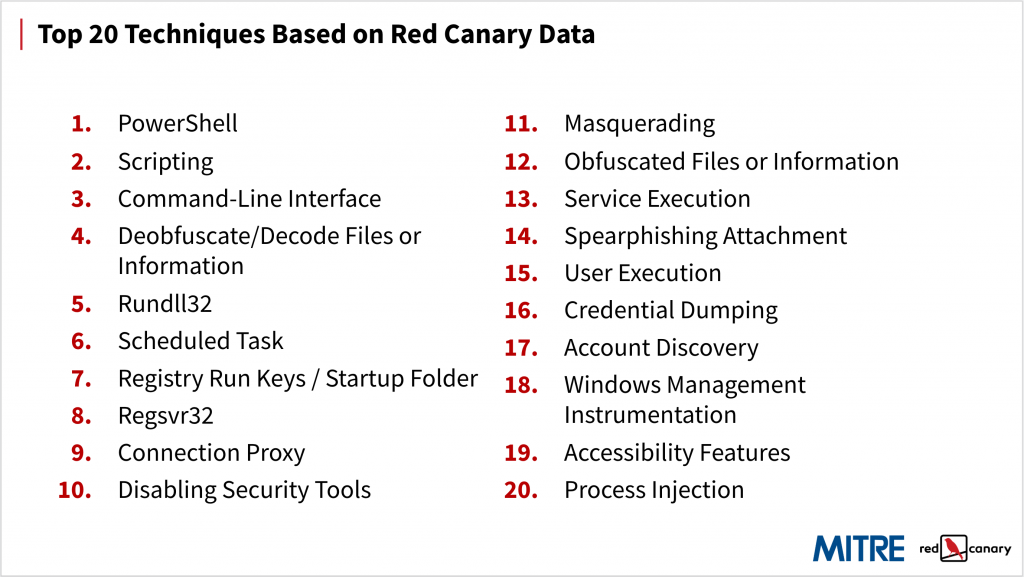
The meat of the talk (and the part that prompted nearly everyone in attendance to pull out their phones and start taking pictures of the slide deck), was the ATT&CK top twenty technique lists.
MITRE and Red Canary each presented a list of the top 20 ATT&CK techniques that are most popular among adversaries. MITRE generated their top 20 by analyzing more than 400 publicly available threat intelligence reports and mapping them back to the framework. Our list is based on the techniques we’ve observed in customer environments on a daily basis over the past few years.
There is a ton that could be said of these two lists, and we intend to say quite a lot (shameless plug) in an upcoming report. However, the differences between these two lists is largely the result of our differing datasets. MITRE’s list includes a lot of discovery and other techniques because their data is based on holistic and retrospective threat intelligence reporting. Ours is heavy on execution and other post-exploit techniques because our data is based on the detections we use to stop attacks in customers’ environments, including some in which a security incident has already occurred.
3. Meet Me in the Middle: Threat Indications and Warning in Principle and Practice
Joe Slowik—the principle adversary hunter at Dragos—talked about indicators and warning in principle and practice and how threat intel teams can better provide timely value. Problematically, he explained, raw indicators, while readily sharable and conducive to alerting, lack context and have short shelf-lives. On the other hand, finished intel reporting provides context but is generally received in retrospect, long after an attack campaign is completed.
Instead of focusing on unreliable indicators of compromise (IoC) and untimely finished intel reporting, Slowik advocated that threat intel teams focus on providing indications and warning of malicious activity in real time. Such information would not focus on attribution or intent, but would instead attempt to categorize and differentiate threats while providing information that informs defenders and enables incident response efforts. The most useful intel, he argued, is that which can be shared almost immediately without requiring enrichment or vetting, clearly describes what was observed to whatever degree is possible, and offers guidance on mitigation and detection.
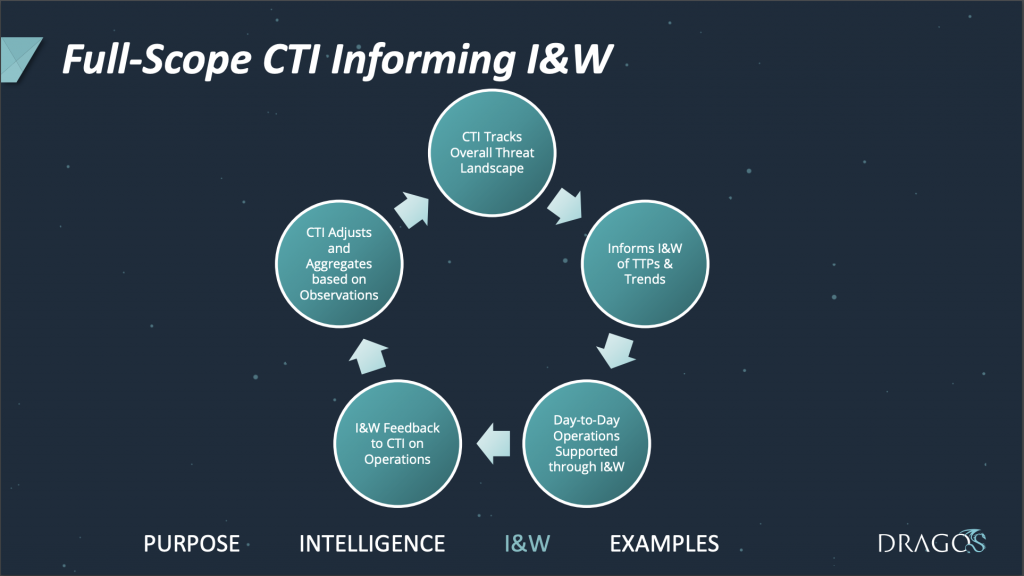
Slowik’s slides stand alone nicely if you’re interested in giving them a read.
2. Unsolved Mysteries–Revisiting the APT Cold Case Files
Juan Andres Guerrero-Saade of Chronicle talked about how we should use new tooling to analyze old threats. He seemed (very intentionally) to avoid naming any specific tooling, but his point was clear: our intel tooling has become stronger, contains more data, and is just generally better at pattern recognition. After all, the security industry is young and the cyber threat intelligence industry is younger still. By that logic, a three- or five-year old intel report about some suspected state-level adversary is relatively ancient and was probably analyzed using similarly archaic tools and techniques. Therefore, he urged the audience to revisit and reanalyze years-old attack campaigns, applying better tools to old attacks to gain new insights.
Making a tangentially related (but nonetheless important) point, Guerrero-Saade criticized the security industry as a whole for focusing its threat intelligence reporting far too much on the interests of journalists and not nearly enough on the needs of network defenders. Unfortunately, his slides did not make it up onto the SANS website.
1. Quality Over Quantity: Determining Your CTI Detection Efficacy
The last talk of the day came from David Bianco, who was tasked with determining what Target’s threat intel team knew about its list of priority adversaries. In essence, he performed a qualitative analysis of the great quantities of threat intelligence data Target had collected over the years. He wanted to learn how volatile Target’s IoCs were, where and how adversaries could operate with impunity in Target’s network, and where the company’s security and IT teams should concentrate their collection efforts to improve security.
He ultimately ended up mapping and heat mapping all of Target’s threat intelligence to Lockheed Martin’s Cyber Kill Chain, the Pyramid of Pain (which Bianco himself invented), and ATT&CK. Maybe even more fascinating, he was able to cross-reference all of this information to visualize intelligence and coverage gaps and to make inferences about the value of his intel.
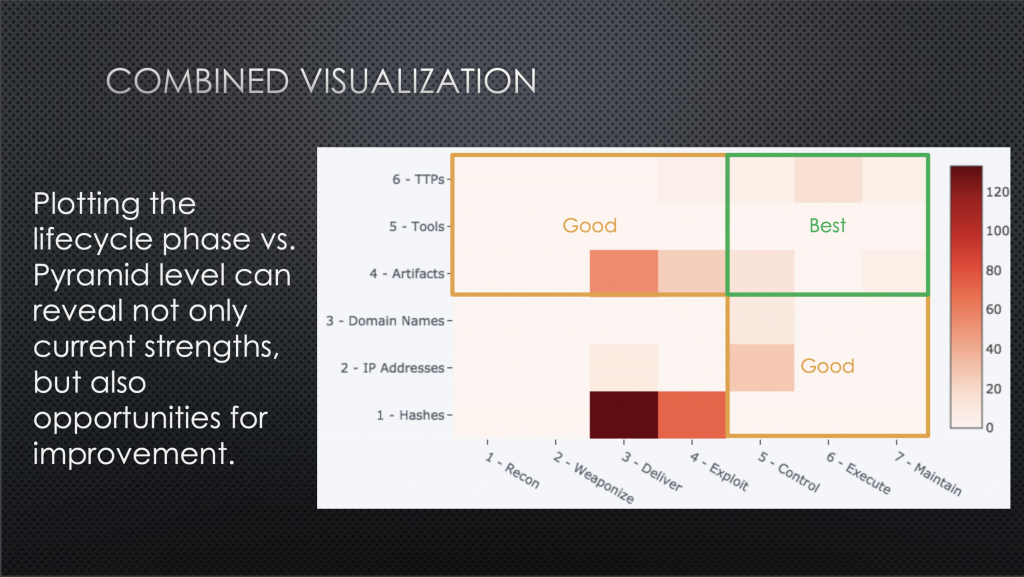
Check out Bianco’s slides here.
Conclusion
As far as security conferences, the SANS CTI Summit was a good one. It certainly followed the less-is-more approach, highlighting a single, narrowly focused topic with just a handful of speakers.
Be sure to check out the slides on the SANS website, and let us know what we missed on Twitter.