Red Canary Automate empowers security teams to define and automate threat remediation processes in a safe, easy, and meaningful way. Customers use Automate to trigger notification workflows and to initiate containment actions against a threat to instantly mitigate risk. Since adversaries don’t always keep a 9-5 schedule, you can be confident that initial remediation actions are ready and waiting to fire, even when your team is away from keys.
We are excited to add Ban IP and Ban Domain playbook actions to our list of available remediation actions available with the Red Canary + Microsoft platform.
Why ban an IP or a domain with Defender?
Ideally, your endpoints all connect to the internet through centrally administered firewalls or proxies, whether on a local corporate network or via VPN from elsewhere. Those tools are a necessary control plane for network traffic from your endpoints and modern firewalls often block traffic to known bad destinations automatically or by configuration. However, you can’t always count on your endpoints to connect online via primary security infrastructure like your firewall. When your team is on the road or working “from home” at a beach resort in Maui, how can you ensure that those endpoints aren’t connecting to malicious destinations beyond your network?
Red Canary’s Ban IP and Ban Domain playbook actions use the Defender for Endpoint Network Protection feature to block traffic to and from domains and IP addresses that you mark as indicators of compromise (IOC).
Let’s set one up to see it in action:
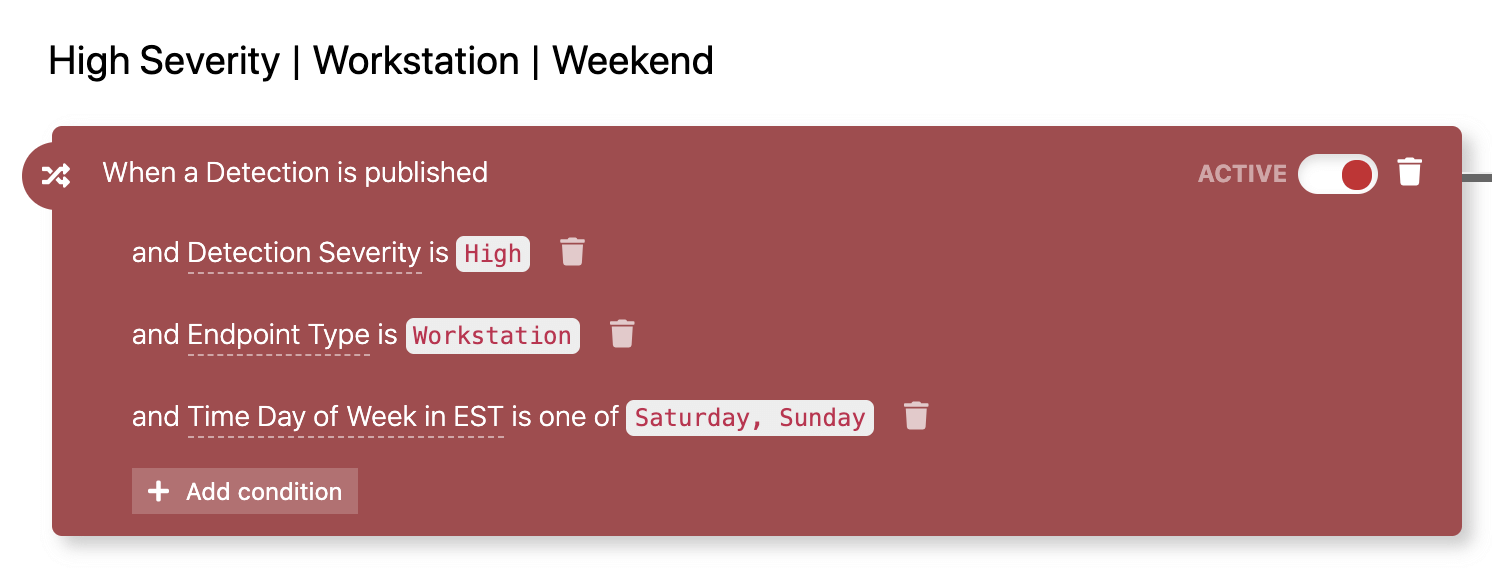
This Automate trigger is set up to run on the weekends, when most security teams are away from their work (don’t forget that Red Canary’s team monitors for threats 24/7):
Now, you can add new actions to block connections to IPs and to domains that are identified as IOCs:
After adding these to your Playbook, you are done with configuration in the Red Canary platform. However, there are still some Defender prerequisites to double check.
From Microsoft Documentation:
- URL/IP allow and block relies on the Defender for Endpoint component Network Protection to be enabled in block mode.
- The Antimalware client version must be 4.18.1906.x or later.
- Supported on machines on Windows 10, version 1709 or later.
- Ensure that Custom network indicators is enabled in Microsoft Defender Security Center > Settings > Advanced features.
Red Canary will set each individual IOC as an “Indicator” within the Defender portal in “Alert and Block” mode. Any machine set up with Microsoft Defender for Endpoint will subsequently block connections to those IOCs at the endpoint level, whether or not that traffic is going through your firewall.
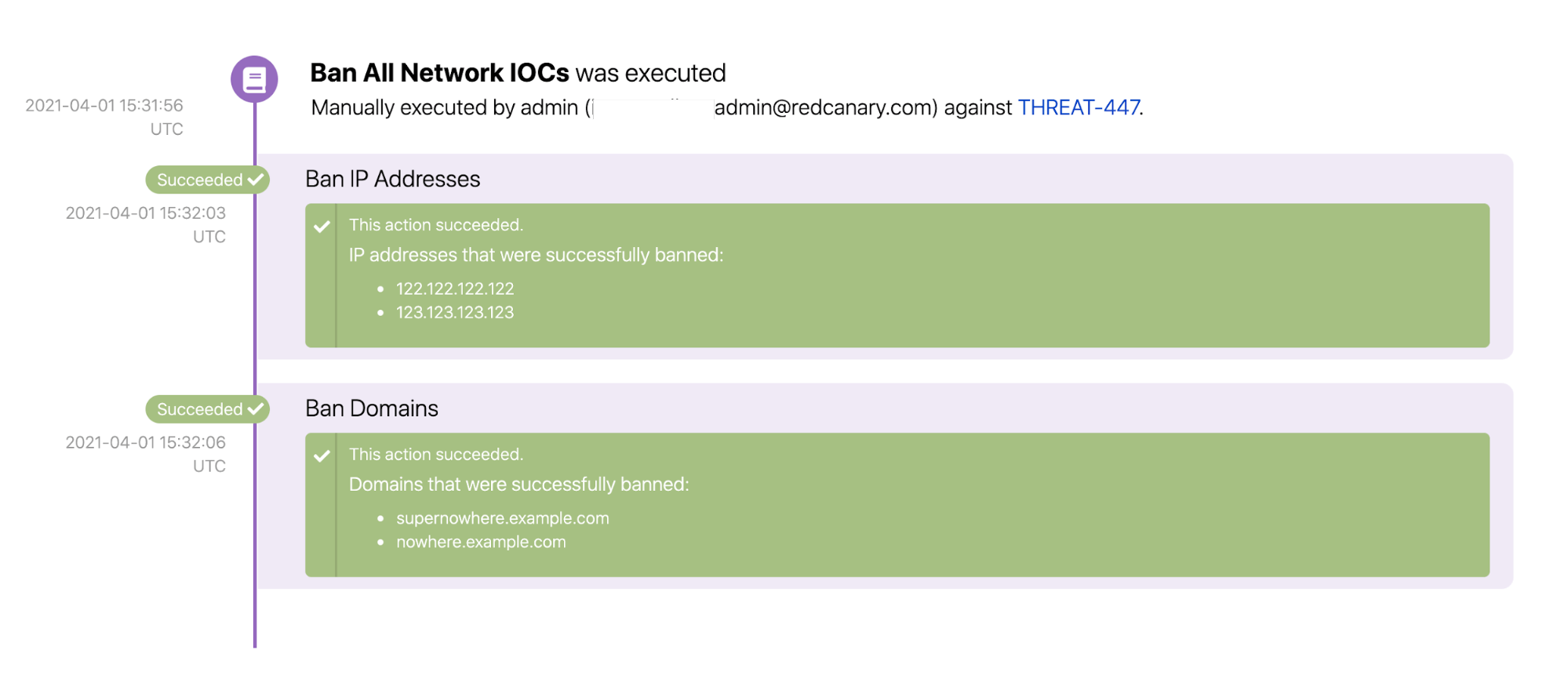
Here’s what it looks like when those actions run successfully:
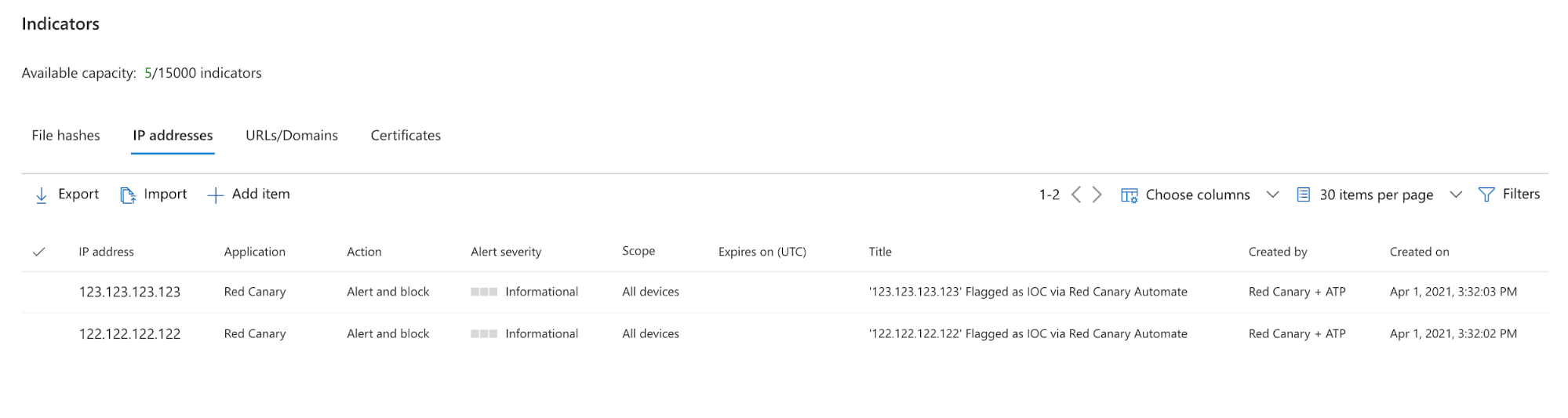
In Defender, you can see where those “Indicators” have been added (only the IP indicators shown here):
While endpoint-based network detection won’t replace your next-gen firewall, you can now take advantage of these Red Canary + Microsoft Automate actions to enhance your network protection procedures.