We are very excited to announce that Endgame and Red Canary have partnered to integrate Endgame’s endpoint telemetry into the Red Canary platform. Our teams have worked together for years on research, mapping adversary techniques to ATT&CK™, and most recently on designing Endgame’s streaming APIs for this integration. Endgame now supports the collection of not only process-level telemetry, but a number of low-level endpoint data types invaluable for detection of modern threats.
Here are a few of the elements that make this partnership unique:
1: Advanced sensor capabilities
The Endgame sensor has several features that can be very powerful when plugged into the Red Canary platform. First, the sensor has a unique level of visibility into endpoint activity that is beneficial for detection as well as investigation. A good example of this is the sensor’s extraction of Office macros and shellcode fragments. These are what I would call “meta” data types that are often used as intermediaries or payloads for adversaries.
The sensor also has scriptable rules for configuring behavioral block of system activity. While most NGAV platforms come with a set of rules, algorithms, or models that determine whether blocking should take place, the Endgame sensor allows advanced users to push new blocking rules directly to the sensor. This is very powerful when the Red Canary Cyber Incident Response Team (CIRT) identifies new adversary techniques that are certain to be malicious and should be prevented outright.
2: Similar detection engineering philosophies
The Red Canary and Endgame detection engineering teams have run into a lot of “great minds think alike” moments. Last year, our teams collaborated with Microsoft on design principles for a common schema for endpoint telemetry.
During this exercise we discovered that Red Canary’s Detection Domain Specific Language (DSL) for streaming detection and Endgame’s Event Query Language (EQL) share very similar design philosophies. Take a look at the examples below to see the commonalities.
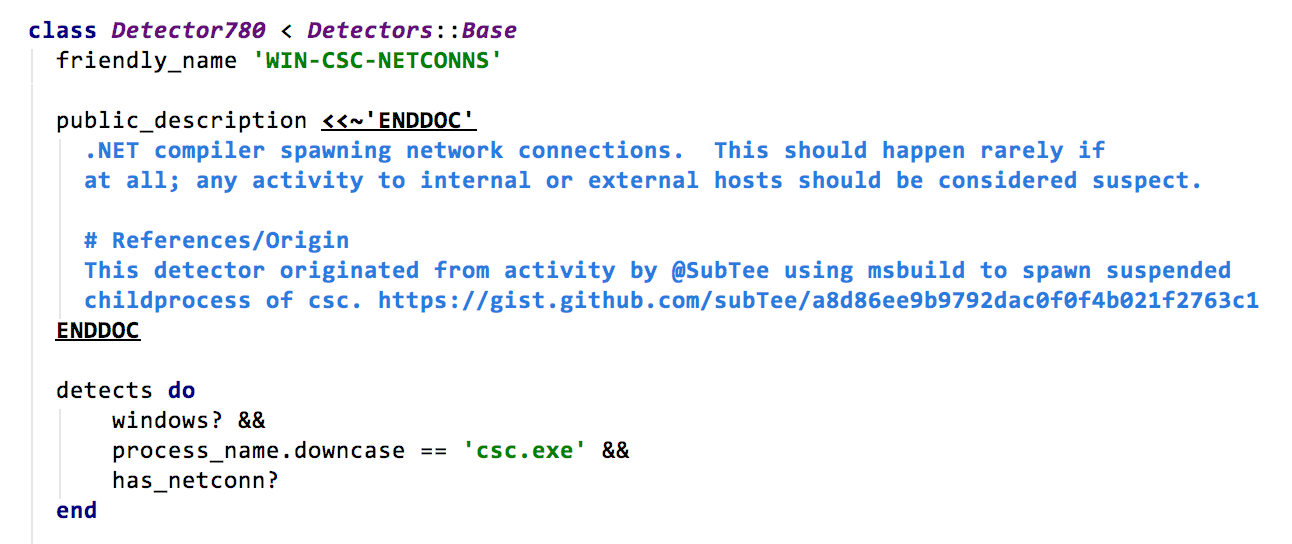
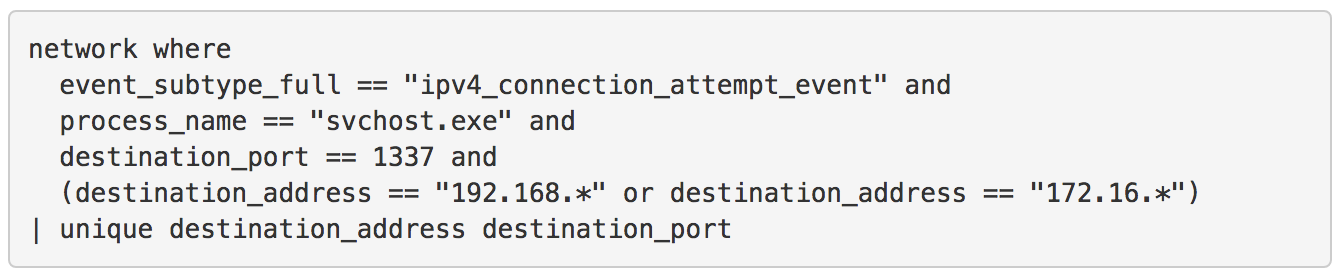
When you build the deep technical integrations that we expect with all our partners, sharing core philosophies like this are a huge advantage in making our joint customers’ security better.
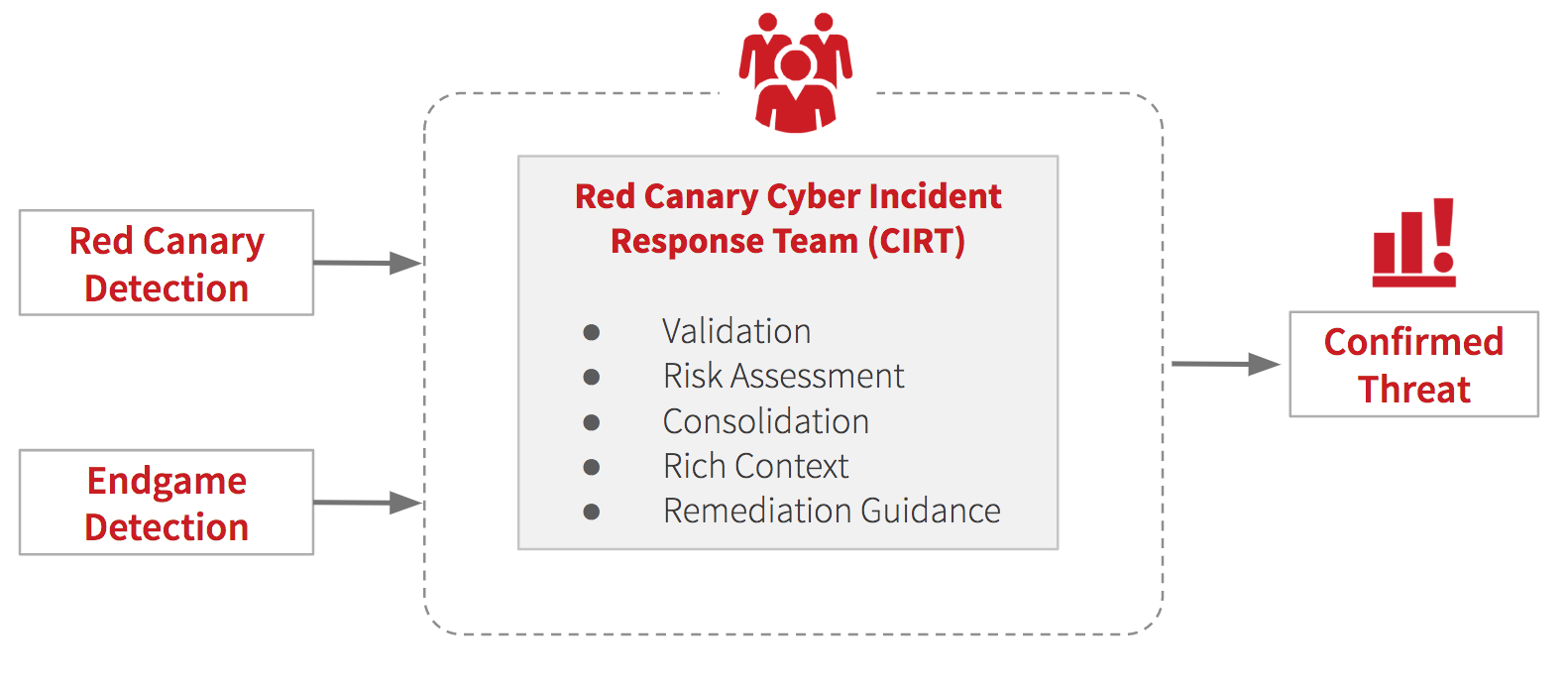
How It Works
Red Canary customers and fans are well aware that we don’t deliver a “managed service” by looking at the alerts created by EDR products. We require complete access to the telemetry collected by the sensor so we can feed it into our detection and analytics pipeline. The Endgame platform now supports raw event streaming into Red Canary’s platform.
This is how it works:
- Endgame ships all the endpoint telemetry it collects to Red Canary.
- Red Canary standardizes the telemetry into its internal format.
- The Red Canary Engine analyzes the data and surfaces potential threats.
- The Red Canary CIRT investigates and confirms threats and publishes full-context detections to your incident response team.
The Red Canary CIRT will validate and add additional context to alerts generated by the Endgame platform as well.
Learn More About Red Canary and Endgame
If you’re attending Blackhat, stop by Endgame Booth #1328 to see a live demo of the solution. Or schedule a demo to have our team walk you through the solution at your convenience.