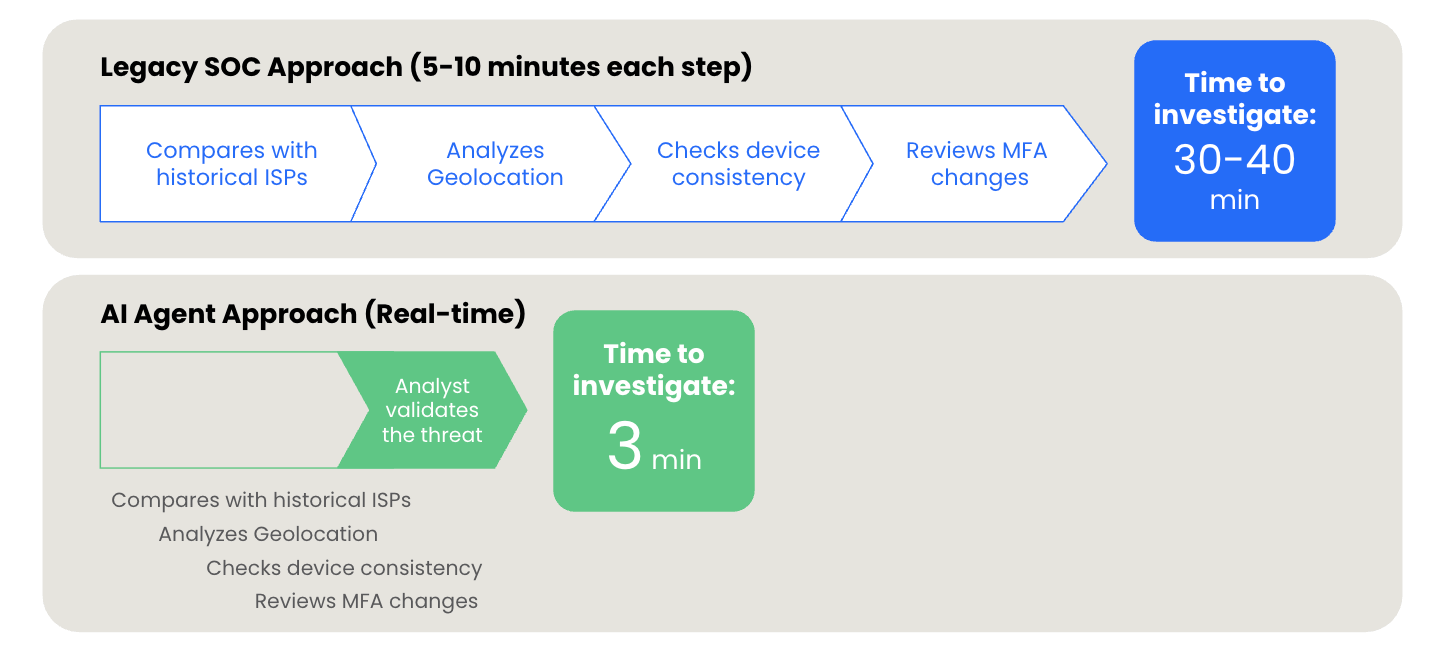
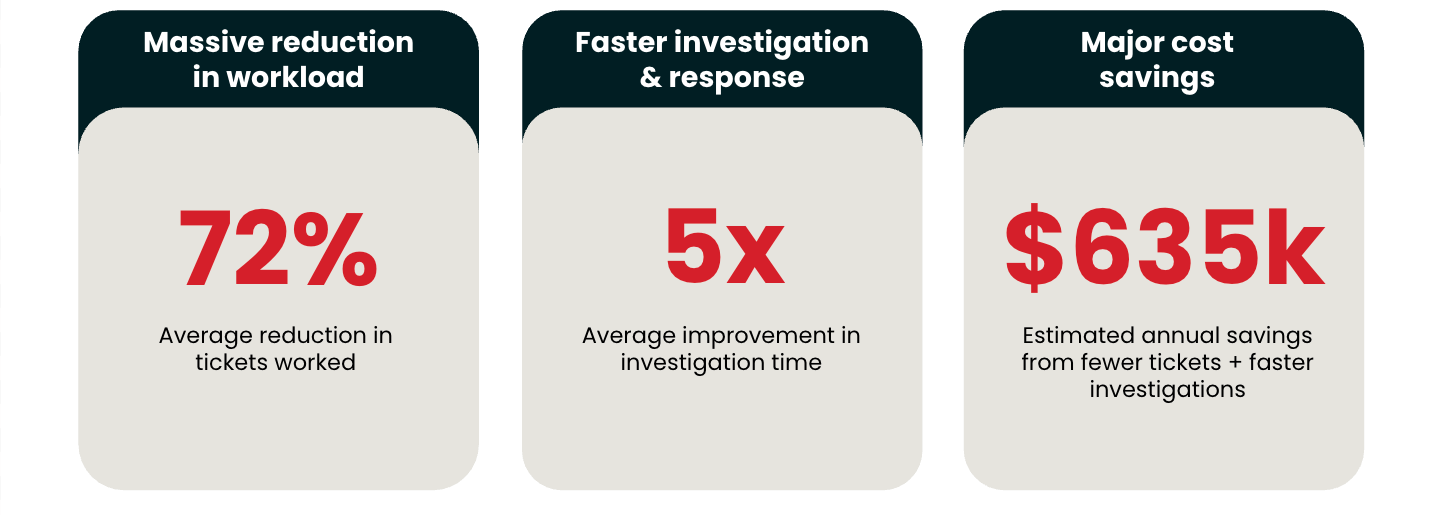
When integrated into a security operations center (SOC), AI agents promise real leverage for defense: faster triage, better context, and improved workflows. They can also introduce new risks and operational questions.
Organizations looking to bring AI into their SOC need practical guidance: That’s why we’re excited to share a new resource, “How to build AI agents into your SOC,” a hands-on guide for building reliable AI agents for security operations—along with open source code and actionable tips to help get your team started.
The way we see it, effective AI systems aren’t the ones with the flashiest autonomy, they’re the ones wrapped in strong workflows, governed by clear constraints, and measured relentlessly.
Building on Red Canary Director of Machine Learning Jimmy Astle’s talk from SecTor 2025, this guide offers a pragmatic, reliable blueprint to integrate AI agents and structure your workflows so your team can transform its security posture and empower your SOC to operate with efficiency.
Read this guide to learn more about:
- Intelligent model selection: Strategically matching the right AI model to the right task, leveraging cost-effective models for routine operations and escalating to more powerful models for complex reasoning.
- Security by design: Implementing stringent guardrails against prompt injection, isolating tools, and meticulously logging all actions to ensure auditability and data governance, treating AI agents as critical infrastructure.
- Iterative implementation: Adopting a phased roadmap that begins with foundational constraints and measurable goals, progresses through quick wins with schema validation and simple routing, and matures with refined routing and expanded test coverage.
The goal here is to provide faster time to signal (think: reducing human investigation time from 30+ minutes to under 2 minutes) to yield repeatable, accurate investigations while providing cost-aware scalability. Doing this enables your security analysts to move beyond reactive firefighting to proactive, intelligent threat detection and response.
Consider this guide your manual to building a resilient system, not just an isolated AI model. By implementing the workflow design, guardrails, and workload routing we lay out here, you can help your organization deliver predictable and trustworthy outcomes that can be used for security investigations and incident response for years to come.
Why take it from us?
At Red Canary, these principles aren’t theoretical; they’re fundamental to how we operate our human-led, AI-powered managed detection and response (MDR) services. We’ve been putting the concepts outlined in this guide to use for the last two years to detect threats faster with more accuracy—across a wide range of data sources.
We deploy scoped agents with a narrow focus, ensuring each is dedicated to a specific task and specific data source to help keep them accurate, fast, and cost-effective. We bound them with deterministic orchestration and rigorous review—we’re continually improving our agents with feedback and tuning—to make sure they’re always evolving.
By integrating AI agents into established SOC processes, Red Canary helps translate repeatable standard operating procedures into precise prompts to achieve faster investigations and triage times without compromising reliability or scope.
Our detection engineers, who identify threats day-in and day out, have seen the impact of AI agents on the SOC firsthand:
Doing this ensures customers benefit from highly efficient security operations across a diverse array of data sources, resulting in faster threat detection and freeing up more time for human analysts to focus on higher value, strategic initiatives.