Tabletop simulations provide a great vehicle for organizational awareness and training for inevitable security incidents. They allow a team to come together in a low-stress environment and assess their procedures and plans. Yet for most organizations these exercises are conducted once a year as a compliance requirement or to spend unused retainer hours from an incident response services provider. So how do we better design and deliver a simulation that drives our security program toward a state of continuous improvement?
First, Assign a Gamemaster
Successful tabletop exercises for security incidents start with assigning a Gamemaster. Their role is to architect and facilitate the exercise. The following sections will break down the flow and process a Gamemaster should be aware of when preparing to deliver a tabletop simulation.
 Set the Stage
Set the Stage
The majority of successful tabletop simulations are a direct result of preparation. This is where the Gamemaster and associated stakeholders determine key details regarding the upcoming simulation. Some of the items I like to set before undertaking development of a scenario and exercise material include:
- Number of scenarios – Determine early on how many scenarios will be exercised.
- Timing – Set a date and stick to it.
- Location/resources – Identify a location and any supporting resources for the exercise (EX: monitor, whiteboard, projector, large conference room, etc.)
- Participants – Coinciding with timing, determine who needs to participate and work the schedule to facilitate attendance. For some organizations this may require participants to travel to a single office location.
- Onsite vs Remote Participation: Onsite participation in exercises tends to produce the best results even for globally dispersed IR teams. I do not recommend remote tabletops, as the value of the exercise and means to facilitate participation drastically decrease when members are attending via web conferencing. If multiple teams from remote offices are participating, have participants join from single conference rooms at a minimum.
- Key Roles to Include: Determining who should participate is primarily dependent upon the scenario and target audience. Consider the following roles for technically focused scenarios: operations, development teams, IT/ITsec management, and members from IR teams. For the less technically focused scenarios invite members from Legal, HR, C-levels (if applicable), senior management, and risk/compliance. In some scenarios all roles may be present, which can result in interesting findings.
- Set goals – Before embarking on the exciting journey of concocting an evil incident for your tabletop, consider what your organization is hoping to achieve. Some questions I always ask stakeholders of the simulation include:
- What types of gaps in our response process are we aiming to shed light on?
- Communication failures
- Process and procedure inefficiencies
- Knowledge
- Are we trying to drive the response team to failure during our test or just observe overall?
- Do we plan to take our findings to the next level and conduct targeted testing? (More on this later!)
- What types of gaps in our response process are we aiming to shed light on?
Designing an Effective Tabletop Scenario
Let’s take a break from general logistics and discuss architecting a tabletop scenario that will achieve intended results. As a Gamemaster and facilitator, this is where you implement creative ways to tell your story. The incident you will present must be a multi-branching story strict enough to test your organization but loose enough to handle any action from the participants.
The following three elements make up a solid foundation for any security incident tabletop:
- Format/Structure – Does the presented tabletop incident progress through the incident handling stages or attack lifecycle?
- Scenario(s) – The tabletop exercise should present participants with one or more security incidents to work through as a team.
- Props/Tools – Don’t be boring and use plain slide decks. Get creative and present team members with specific pieces of information. Test your team’s ability to share information and provide status updates. For example, on one scenario I presented network analysts with sample logfile information that, if pivoted off, would lead the forensics team to the next clue. In another scenario, I presented the executive team with a fake news video about leaked information appearing on forums like WikiLeaks. (The intended effect was achieved!) As a facilitator your role is to guide but not hand-hold and drive team members to work together and solve a complex problem.
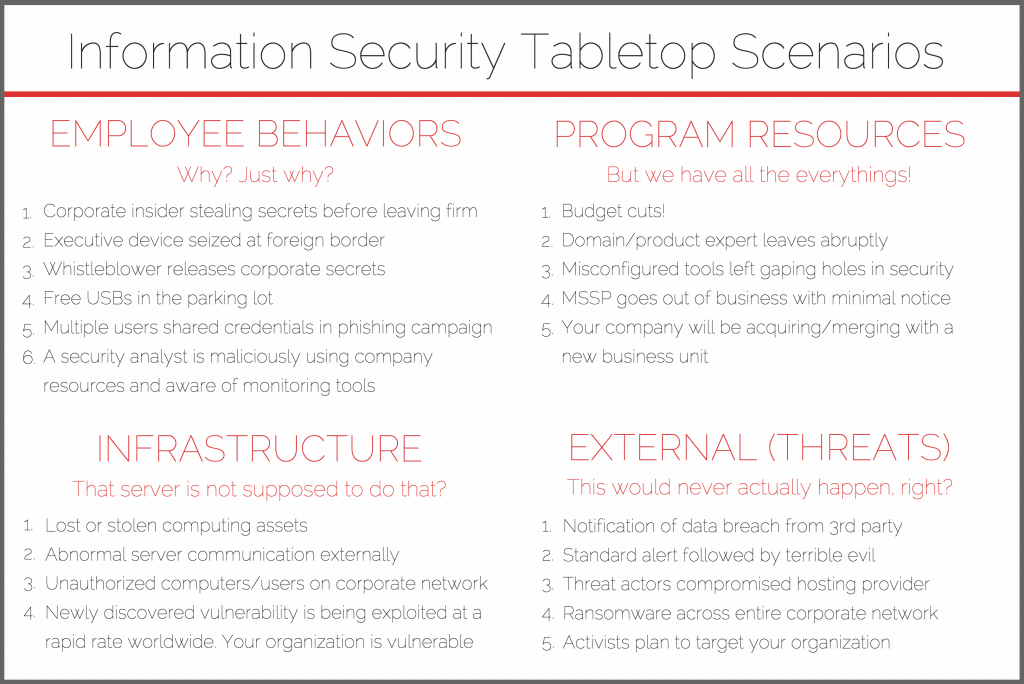
Example Scenarios and Frameworks for Building Your Simulation
There are surprisingly few idea boards for information security tabletop scenarios. While the best tabletop exercises will incorporate information about your organization, it always helps to have a starting point. The below scenarios are suggestions and potential frameworks for you to build your simulation. It is the responsibility of the gamemaster and facilitator to come up with the full story and the questions that will be asked of participants (many times dozens to hundreds are needed). Just remember to design your scenario in a way that lets your team discover gaps and issues during the engagement. The best scenarios present enough information and clues that the team is able to drive the story forward. And don’t feel you must limit your exercise to one topic; some of the most interesting exercises might chain together a number of these topics.
Example: A standard alert leads to the discovery of a widespread phishing campaign. In a later session with executives you reveal a data breach notification from the FBI. It is up to you to separate or connect your scenario’s story.
You can use this to drive technical responses and great discussion within the information security team. But don’t overlook post-breach response activities. What about calls from your customer base, how to handle public relations, data breach notification laws, etc.? Incorporating all of these elements in the scenario will help the security team and key business units improve.
The Day of Delivery
You’ve assembled your team, it’s the day the of the exercise and the scenario is ready. It is time to begin! This is where your teams will discover communications gaps, identify needed capabilities, and learn about what various teams and team members bring to an incident.
One rule to rule them all:
My mentors taught me the only rule that matters when delivering simulations: DO NOT POKE HOLES. What this means is participants should not aim to find fault in parts of the scenario. As a facilitator, you are the puppeteer to combat the participants that attempt this strategy. Cause mayhem in your scenario and make the response efforts that much more difficult. Simulate delayed responses from MSSPs. Attack weak points such as tribal knowledge by informing your team that the tribal expert is on vacation and unreachable. Remember, the point is to drive the team to identify strengths and weaknesses.
Stay confident in the delivery and be energetic. Make sure to engage all of the participants by leading them with questions and guiding the scenario forward. Balance that by letting discussion take place between the participants, only interrupting to drive the scenario forward for the sake of time.
Key Takeaways
Simulations are a great opportunity for organizational units to discover more about their ability to handle a security incident of any shape, size, and type. Use this opportunity as a stress-free environment designed to make security better throughout the organization. Following the scenario, get together as a team to review the failures identified, discuss action items to improve upon those weaknesses over time, and—most importantly—highlight the strengths of your team.
As your teams become accustomed to handling incidents and working through tabletop simulations, level-up your game by executing targeted simulations that focus on testing specific skills and processes.
In closing, here are five key takeaways to guide your tabletop simulation:
- Have a plan.
- Design an engaging scenario. Not every simulation needs to be a data breach.
- Be engaging and have fun.
- Learn about your team.
- Make security better!
Editor’s Note: This post was originally published in May 2017, but it remains just as relevant now as it was back then. We’re reposting it today because an apocalyptic snowstorm—aptly called a “Bomb Cyclone”—is wreaking havoc on the Denver metropolitan area and hindering editorial coordination. Worry not, though—our CIRT is operating at full capacity.
 Set the Stage
Set the Stage