In security, gaps are opportunities, but not just for adversaries. The defining edge for blue teams lies in identifying detection gaps before they can be exploited.
At Red Canary, this philosophy drives our approach, and the following anecdote is the latest to highlight just how well it works.
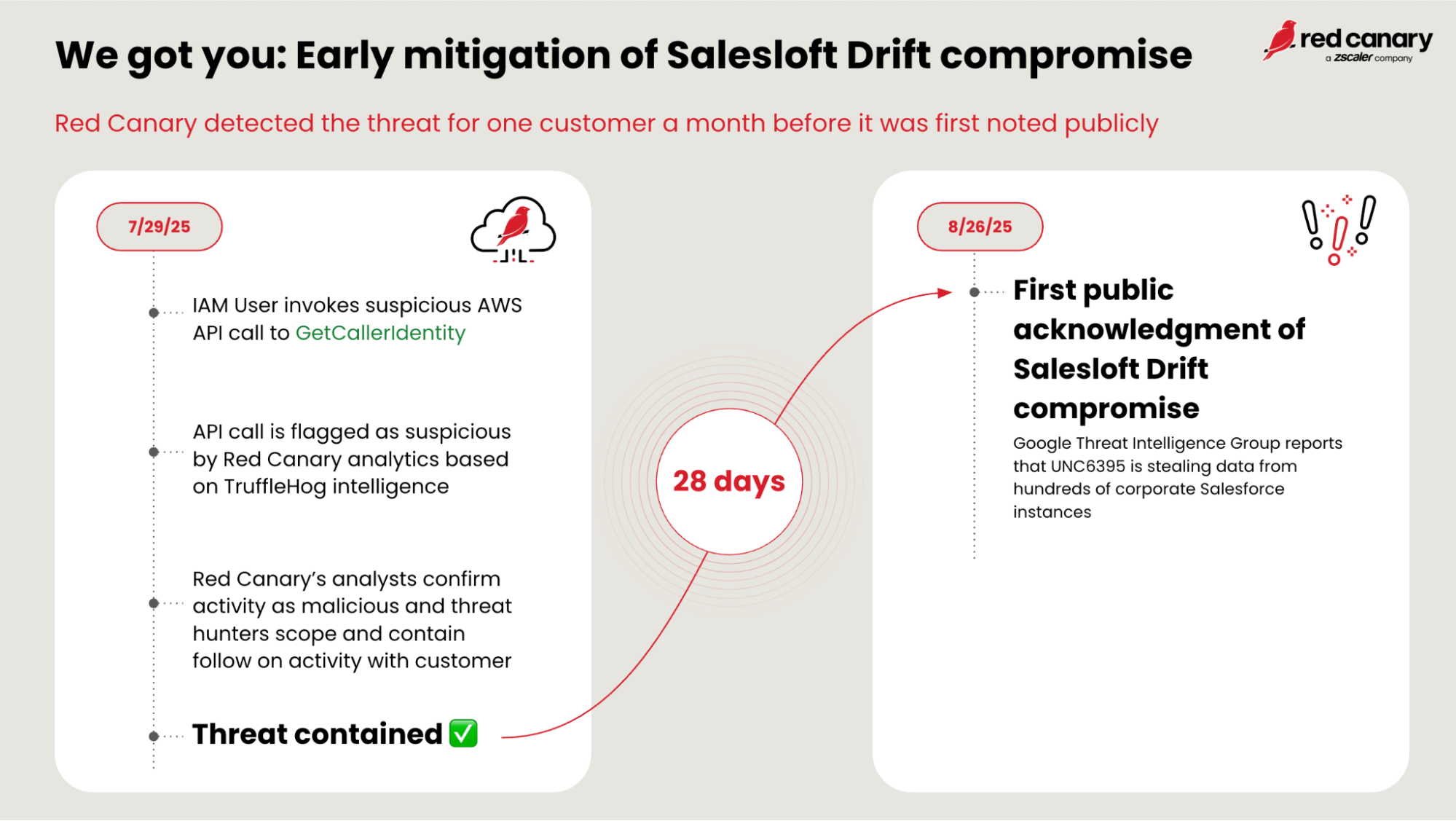
28 days before the attack became public knowledge, we detected and contained a threat tied to the now infamous Salesloft Drift compromise.
What made this case unique wasn’t just the detection itself, but how it began as part of a deliberate focus on areas where attackers often thrive: cloud and identity. Here’s how it all unfolded.
The starting point: A focused hunt on tools that cross the line
Every good detection starts with a question: What are we missing, and how could attackers exploit it? For our threat hunters, the rise of identity-based compromises in cloud environments has been a growing concern. With attackers favoring dual-purpose tools for credential hunting and other reconnaissance activities, it was one of our keen-eyed threat hunters who identified a potential detection gap for TruffleHog after observing an adversary abusing the legitimate tool.
Not fundamentally harmful
TruffleHog is often used by security and development teams to search for secrets or credentials exposed in places like Git repositories. While not inherently malicious, it can just as easily be used by attackers. With that in mind, the threat hunter recognized the risk of leaving such activity unnoticed: potential credential exposure, lateral movement, and subsequent data exfiltration.
He wasted no time in collaborating with our detection engineering team to create a bespoke detector that would sniff out TruffleHog activity in customer environments. Initially, there was radio silence, but not for long…
The alert: Seeing what others miss
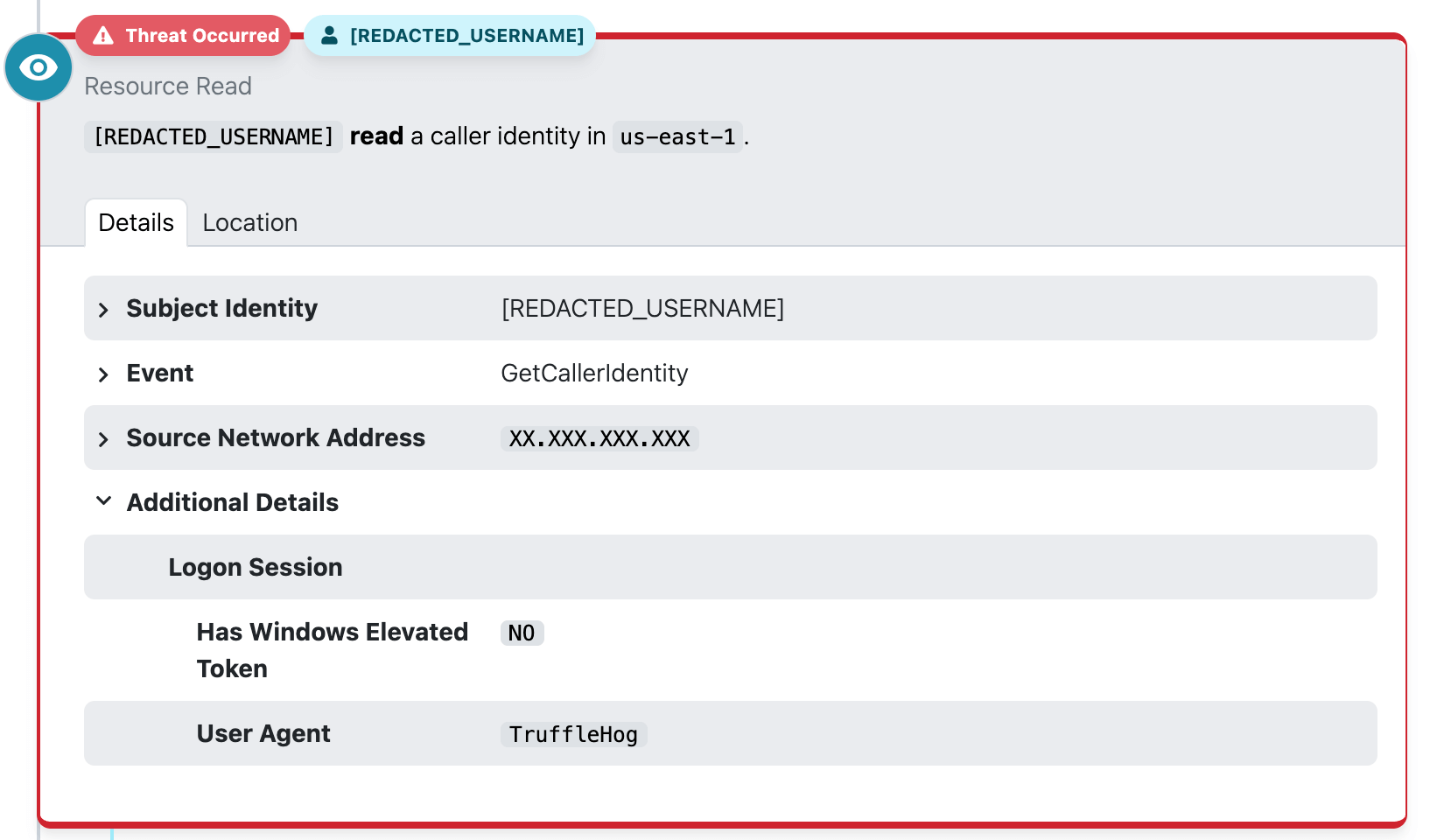
Less than a month after the detector’s deployment, it triggered an alert in one of our customer’s AWS environments. TruffleHog had surfaced, this time conducting reconnaissance API calls that warranted immediate attention.
Initial investigation
Our analysis showed the adversary leveraged a compromised IAM user identity associated with a TruffleHog user agent to execute the GetCallerIdentity AWS API call. What the threat hunter had hypothesized above was playing out in real life.
Customer collaboration
We quickly made contact with the customer and worked together to put a name to the identity and its business purpose. Beyond that, the concerns from the customer, understandably, were: Is data exposed? Are there more accounts compromised? What’s the impact? We set out to help answer those questions.
Scoping the incident
After containing the threat, follow-on digging revealed that the TruffleHog activity may have been tied to attempts to expose credentials or secrets within the environment. Using API logs and artifacts gathered from the event’s telemetry, we were able to determine that no further accounts had been compromised, a sigh of relief for us and our customer. We then passed the investigation off to the customer’s dedicated incident response firm, who continued with additional scoping needs and mitigation efforts.
The connection: From TruffleHog to Salesloft Drift
What made this detection even more significant came later. During a post-incident meeting, the customer confirmed that this activity was related to the Salesloft Drift supply chain attack. This revelation solidified the value of the proactive detector; not only did it give the customer a 28-day head start before the compromise was publicly revealed, but it helped prevent exposed credentials from turning into a larger, more damaging breach.
The attackers had hoped to use a legitimate cloud tool to fly under the radar, but by focusing on behaviors instead of atomic indicators (e.g., known bad IPs or hashes), our team helped the customer uncover and stop the threat before it gained traction.
Why this worked
This case underscores how Red Canary blends proactive threat hunting, automated detection, and collaborative incident response to protect our customers.
Proactive focus on emerging threats
TruffleHog itself isn’t new. What was new was our realization that the uptick in targeting of cloud identities by attackers made tools like TruffleHog a potential weapon. The decision by our threat hunting team to look beyond the obvious and address a detection gap before it could be exploited made all the difference in this case.
Accurate, scalable detection
Proactive hunting is invaluable, but it becomes a force multiplier when paired with automated detection. Turning the team’s observations into a detector meant we didn’t just address a single concern, we protected all Red Canary customers from future incidents involving the combination of this tool and the corresponding ATT&CK techniques (T1552 & T1589.001).
Collaboration with the customer
During the incident, we partnered closely with the customer and its extended team to ensure the terrain we had visibility into was scoped. By working together, we minimized downtime, contained the threat, and ensured they felt confident moving forward.
Looking ahead
The TruffleHog incident isn’t just an example of effective detection, it’s an example of how deliberate, preventative measures can outpace attackers. Detecting threats before they escalate isn’t just about tools; it’s about people who understand the big picture and proactively sniff out opportunities for better defense.