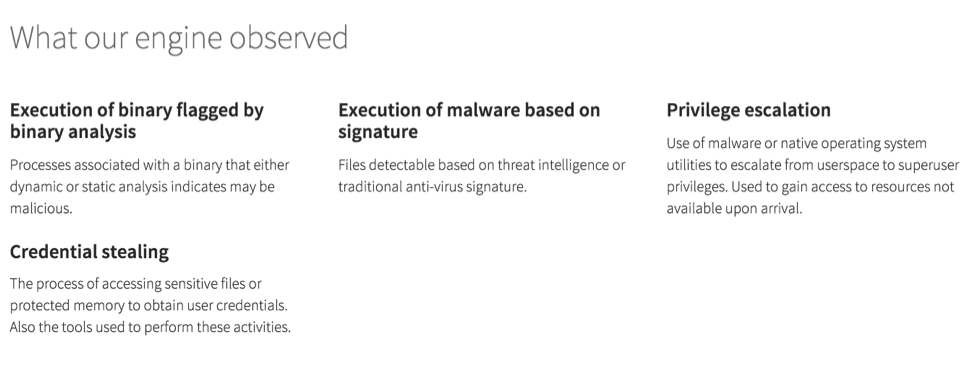
Red Canary’s threat detection leverages the five event types collected by Carbon Black’s endpoint monitoring platform: file modifications, registry modifications, network connections, process tree information, and binary collection. These data points are streamed into our proprietary Threat Detection Engine that was purpose built to perform automated binary, behavioral and threat intelligence analysis to find anomalous events requiring further review at massive scale.
Carbon Black 5.0 now extends the event collection platform to collect a new type of endpoint activity: cross-process events. Cross-process events are triggered when a process modifies another running process—injecting code into the process, duplicating handles, or reading/writing memory in that process. The injection of malicious code into legitimate processes to evade detection and persist on target machines is common in several types of malware. This improved visibility into cross-process events enables Red Canary to detect threats that other security products and services are blind to.
This cross-process activity analysis also allows Red Canary to provide more context around detected threats by tracing threat execution from the original source to actions undertaken under the auspices of other supposedly legitimate processes. Providing that additional context enables you to understand the full scope of the infection and results in additional Indicators of Compromise (IOCs) that you can feed into network defense and prevention devices through our simple platform API.
The ability to migrate code across processes is widely used for legitimate purposes, so simply alerting on any cross-process activity would inundate an analyst with false positives. Red Canary’s Threat Detection Engine correlates that cross-process activity with other behavioral indicators, threat intelligence and binary analysis in order to accurately predict whether unknown code is benign or represents a threat, and our expert analysis team eliminates any remaining false positives so you only receive confirmed detections
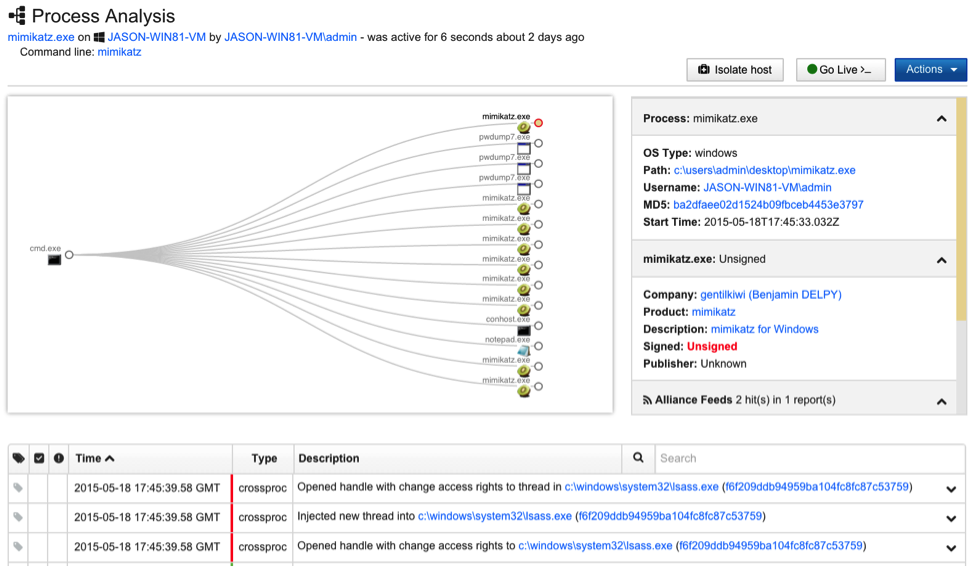
An example of cross-process activity associated with malicious activity is dumping user credentials from the Windows Local Security Authority (LSA) subsystem. The process that hosts the LSA subsystem, LSASS.EXE, is a frequent target for malware because it contains all local credentials and access tokens for users that have logged into a system. Malware that steal credentials from a local system will inject code into the local LSASS.EXE process and send the resulting password hashes back to the attacker. The Red Canary detection of a common credential dumping tool, mimikatz, is shown below and highlights this “Credential Stealing” activity.
Further detail on the detection can be gathered by jumping directly into the associated Carbon Black process from the Red Canary detection:
This visibility into cross-process injection gives Red Canary an ever improving ability to detect malicious software and suspicious activity affecting your organization. That powerful detection is combined with our expert analysts that eliminate false positives and the ability to remotely respond to endpoint threats in a matter of minutes.
Interested in evaluating Red Canary for your organization? Contact one of our security engineers and we could have you started by the end of the day.