Worms—threats that leverage automated lateral movement to infect as many systems as possible—dominated the landscape in 2019, according to an analysis of confirmed threats in Red Canary’s 2020 Threat Detection Report. Specifically, behaviors tied to the information-stealing trojan TrickBot led to thousands of detections across our customer base—predominantly organizations that came to us through incident response partners—and shaped the findings in this year’s report.
About the report
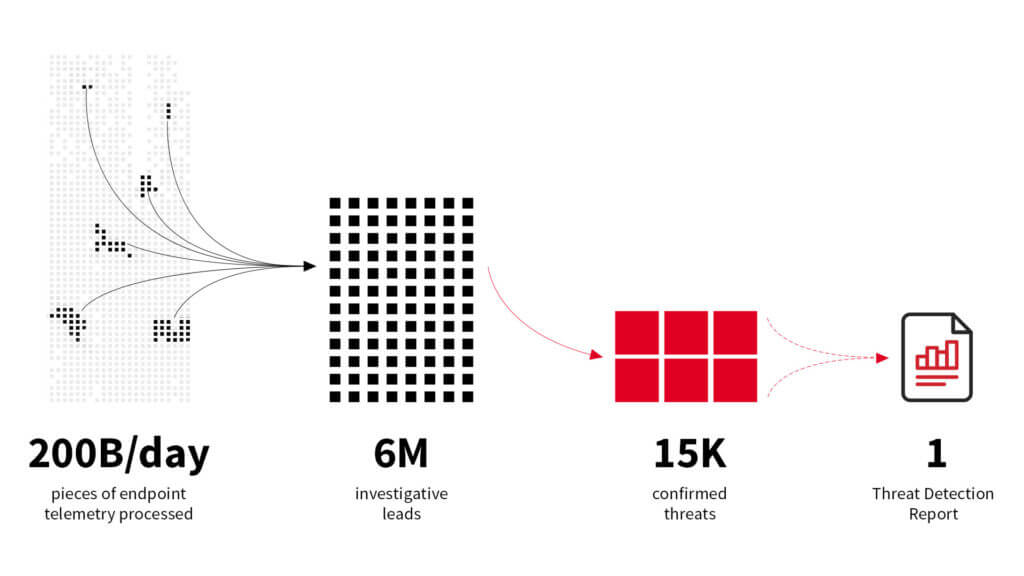
The report analyzed approximately 15,000 confirmed threats that Red Canary detected in customers’ environments in 2019, using the corresponding MITRE ATT&CK® data to determine what threats are most prevalent. The analysis focuses on threats that are known to be malicious or suspicious and excludes detections associated with adware and potentially unwanted programs.
Threat trends
An abundance of threats exhibiting worm-like behavior (i.e., those that move laterally within an environment in an automated fashion) is perhaps the clearest trend from the 2020 Threat Detection Report, and TrickBot is the main driver of this activity. Another trend that stands out is the use of remote administration and network management tools for lateral movement and execution. The table below shows the top 10 ATT&CK techniques observed across Red Canary’s customer set and marks which of these trends they exemplify.
The Top 10 Techniques Detected in 2019
| ATT&CK® Technique | Worm | TrickBot | Remote/network admin tools |
|---|---|---|---|
| ATT&CK® Technique : 1. Process Injection (T1055) | Worm: √ | TrickBot : √ | Remote/network admin tools: |
| ATT&CK® Technique : 2. Scheduled Task (T1053) | Worm: √ | TrickBot : √ | Remote/network admin tools: |
| ATT&CK® Technique : 3. Windows Admin Shares (T1077) | Worm: √ | TrickBot : | Remote/network admin tools: √ |
| ATT&CK® Technique : 4. PowerShell (T1086) | Worm: √ | TrickBot : √ | Remote/network admin tools: |
| ATT&CK® Technique : 5. Remote File Copy (T1105) | Worm: √ | TrickBot : | Remote/network admin tools: √ |
| ATT&CK® Technique : 6. Masquerading (T1036) | Worm: | TrickBot : | Remote/network admin tools: |
| ATT&CK® Technique : 7. Scripting (T1064) | Worm: | TrickBot : | Remote/network admin tools: |
| ATT&CK® Technique : 8. DLL Search Order Hijacking (T1038) | Worm: | TrickBot : | Remote/network admin tools: |
| ATT&CK® Technique : 9. Domain Trust Discovery (T1482) | Worm: √ | TrickBot : √ | Remote/network admin tools: |
| ATT&CK® Technique : 10. Disabling Security Tools (T1089) | Worm: √ | TrickBot : √ | Remote/network admin tools: |
The use of worms, TrickBot and/or remote admin tools doesn’t account for the prevalence of these techniques entirely, but they play a major role.
Anecdotally, worms became increasingly common throughout the latter half of the 2010s. This trend was underscored first by a rash of ransomware incidents affecting hospitals in 2016, WannaCry and NotPetya outbreaks in 2017, and more recently by large-scale ransomware attacks on municipal government organizations in 2019. The 2020 Threat Detection Report not only backs this trend up with data, it also offers specific examples of how this new paradigm often plays out.
Thanks for all the adventures, TrickBot
TrickBot is frequently part of a trio of infections that starts with the Emotet trojan and ends in a Ryuk ransomware infection. In essence, Emotet infects its hosts and loads TrickBot, which steals credentials from infected machines as it moves laterally around a network. Once TrickBot has run its course, it drops the Ryuk ransomware, which encrypts all of the infected hosts on a network and demands a ransom payment to unlock them.
Given how these attacks play out, one might expect Emotet, the preeminent first stage, to appear with higher prevalence across our detections. So why is Process Injection, a technique leveraged by TrickBot to run arbitrary code through the Windows Service Host, so much more prevalent than Emotet-related behaviors like Spearphishing Attachments or PowerShell?
Red Canary’s findings are a function of our visibility, and an increasing percentage of Red Canary’s visibility comes from incident response engagements. Many of the engagements that came to us via our incident response partners landed us in environments where Emotet had run its course, and where TrickBot subsequently infected large numbers of computers. Irrespective of the later-stage payloads, this phenomena meant that we did not have the opportunity to detect initial access vectors or other early-stage payloads.
The above is in stark contrast to customer environments where we perform ongoing monitoring. In these cases, Red Canary is generally able to detect and automate interdiction of threats like Emotet before they can be used to gain a foothold and spread.
How to use this report
The 2020 Threat Detection Report was produced by and for security practitioners. It doesn’t merely take a high-level view of the trends and forces that shaped detection throughout 2019; each of the 10 ATT&CK techniques listed above has its own analysis section in the report. Those sections attempt to answer questions such as:
- Why and how do adversaries leverage this technique?
- What log sources do you need to collect from to observe this technique?
- What specific behavioral patterns should you look for to detect this technique?
Security leaders can use the report as a resource to understand the merits of a behavioral-based approach to threat detection and a roadmap for setting priorities as their teams attempt to improve detection coverage. Security engineers and analysts can use the report to develop their own detection logic and to help interpret the signals they receive from their security tools respectively.
Get started
Watch a short video to learn how you and your team can get started applying the data uncovered in the report.
Watch VideoWhy does the Threat Detection Report matter?
Many security vendors produce broadly scoped annual threat reports, and many of them are worth reading. However, most of them describe the threat landscape through the lens of threat groups or malicious tooling. Red Canary’s Threat Detection Report, on the other hand, is far more concerned with behaviors than it is with specific threats. We implement and operationalize broad detection coverage designed to catch behaviors that adversaries must leverage to achieve their objectives.
Looking ahead
The 2020 Threat Detection Report is entirely digital. As a result, we plan to add additional technique-specific analyses throughout the year. As of today’s release, we’re already adding three techniques—Credential Dumping, Windows Management Instrumentation, and Spearphishing Attachment. While these techniques are outside of the top 10 in terms of total threat volume, they affected a large number of customers. If there are any techniques that you’d like to see us cover in the report or in a webinar, then please reach out to us on Twitter or here.