Highlights from October
Making its debut at number 1 on our top 10 most prevalent threat list this month is JustAskJacky, a family of malicious NodeJS applications that masquerade as a helpful AI or utility tool while conducting reconnaissance and executing arbitrary commands in memory in the background. At Red Canary, we’re tracking the whole family of tools under the name JustAskJacky, but we’ve seen more than a dozen different lure names including:
- AllManualsReader
- AskBettyHow
- ManualReaderPro
- pdfblitz
You can learn more about JustAskJacky below.
Rhadamanthys jumped into 2nd place this month, after debuting in 10th last month. Rhadamanthys is an information stealer written in C++ that is used to steal credentials, cryptocurrency wallets, and browser data, as well as download and execute additional payloads. This range of capabilities has made it a popular follow-on payload since it first appeared in 2022. The recent wave of activity we’ve seen is fueled by adversaries using Rhadamanthys as a paste-and-run payload.
Like LummaC2, another popular stealer delivered through paste and run, Rhadamanthys is offered as a service. Pricing plans start from USD $299 per month for individuals and small groups, with options for enterprise-level payment tiers as well. It’s been delivered in a variety of ways, including various email phishing campaigns, Google ads, and even a prior paste-and-run campaign last year that used fake Google Meet video conference links.
The latest version was reportedly released in October 2025. On November 11, 2025, Rhadamanthys “customers” reported they could no longer access their servers. On November 13, 2025, Europol confirmed that the latest phase of Operation Endgame, a multi-national effort to disrupt malware infrastructure, targeted Rhadamanthys servers. It remains to be seen how this will affect Rhadamanthys activity in the long term; at the time of publication, Red Canary has not observed Rhadamanthys activity since October 31, 2025.
It’s worth noting that CypherIT, one of the threats tied for 6th this month, is related to the increased Rhadamanthys activity. CypherIT is a malicious commodity packer used to obfuscate and distribute threats such as information stealers and remote access tools. We see it consistently at Red Canary, but generally at levels too low to crack the top 10. We observed a paste-and-run campaign in October delivering CypherIT-packed Rhadamanthys, landing CypherIT on the list for the first time since March 2022.
Odyssey Stealer debuts on the list this month, as part of the tie for 6th place. Odyssey Stealer is a rebranded version of Poseidon Stealer, with additional defense evasion and persistence features, that targets credentials on macOS. Both Poseidon and Odyssey Stealers target sensitive data from browsers, extensions, and other applications using AppleScript code. Poseidon and Odyssey have code-sharing roots in Atomic Stealer, another threat in a tie for 6th place this month. If you are curious about the distinctions between Odyssey, Poseidon, and Atomic Stealer, we have a blog post with more details on the topic.
This month’s top 10 threats
To track pervasiveness over time, we identify the number of unique customer environments in which we observed a given threat and compare it to what we’ve seen in previous months.
Here’s how the numbers shook out for October 2025:
| Month's rank | Threat name | Threat description |
|---|---|---|
| Month's rank: ⬆ 1 | Threat name: JustAskJacky | Threat description : Family of malicious NodeJS applications that masquerade as a helpful AI or utility tool while conducting reconnaissance and executing arbitrary commands in memory in the background |
| Month's rank: ⮕ 2* | Threat name: | Threat description : Traffic distribution system, first observed in 2024, that uses compromised WordPress sites to deploy malicious code that may lead to malware families such as Rhysida and Interlock ransomware, D3F@ck Loader, Mocha Manakin, Mintsloader, and WARMCOOKIE |
| Month's rank: ⬆ 2* | Threat name: Rhadamanthys | Threat description : Information stealer written in C++ that is used to steal credentials, cryptocurrency wallets, and browser data, as well as download and execute additional payloads |
| Month's rank: ⮕ 4* | Threat name: | Threat description : Legitimate remote access tool (RAT) that can be used as a trojan by adversaries to remotely control victim endpoints for unauthorized access |
| Month's rank: ⬇ 4* | Threat name: | Threat description : Electron Node.JS-based threat designed to process steganographic content with arbitrary JavaScript code delivered alongside recipes for meals |
| Month's rank: ⬆ 6* | Threat name: | Threat description : macOS malware that attempts to hijack and redirect user web browsing traffic |
| Month's rank: ⬇ 6* | Threat name: | Threat description : Red Canary's name for a cluster of activity, delivered via installers masquerading as legitimate free software, that progresses through several stages to a PyInstaller EXE with stealer capabilities |
| Month's rank: ⬆ 6* | Threat name: | Threat description : Information stealer designed to target data within web browsers and locally stored files on macOS systems, with the goal of accessing sensitive information including credentials, payment card data, keychain details, and cryptocurrency wallets |
| Month's rank: ⬆ 6* | Threat name: | Threat description : Malicious commodity packer used to obfuscate and distribute threats such as information stealers and remote access tools. |
| Month's rank: ⬆ 6* | Threat name: | Threat description : Malware family used as part of a botnet. Some variants are worms and frequently spread via infected USB drives |
| Month's rank: ⬆ 6* | Threat name: Maya "vaccine" virus | Threat description : Worm-like virus that infects the Maya graphic design software created by Autodesk |
| Month's rank: ⬆ 6* | Threat name: | Threat description : Rebranded version of Poseidon Stealer with additional features, targeting credentials on macOS |
| Month's rank: ⮕ 6* | Threat name: | Threat description : Activity cluster that uses a distribution scheme similar to SocGholish and uses JScript files to drop NetSupport Manager onto victim systems |
⬆ = trending up from previous month
⬇= trending down from previous month
➡ = no change in rank from previous month
*Denotes a tie
Just(Don’t)AskJacky
Images from https://www.gdatasoftware.com/blog/2025/08/38247-justaskjacky-ai-trojan-horse-comeback
JustAskJacky is typically introduced as a seemingly legitimate application online. Users download an installer masquerading as a helpful AI tool or utility. Like a true trojan horse, JustAskJacky is deceptive in the sense it actually has the functionality it claims to have; users can interact with the downloaded AI tool/utility, and it will return results. The combination of an ostensibly useful tool—with additional undisclosed malicious capabilities—is what makes it a trojan horse. The installer name will match the name of the application lure, like JustAskJacky.exe or GoAskBobby.exe, etc. Regardless of the lure name, this code family has the same behavior.
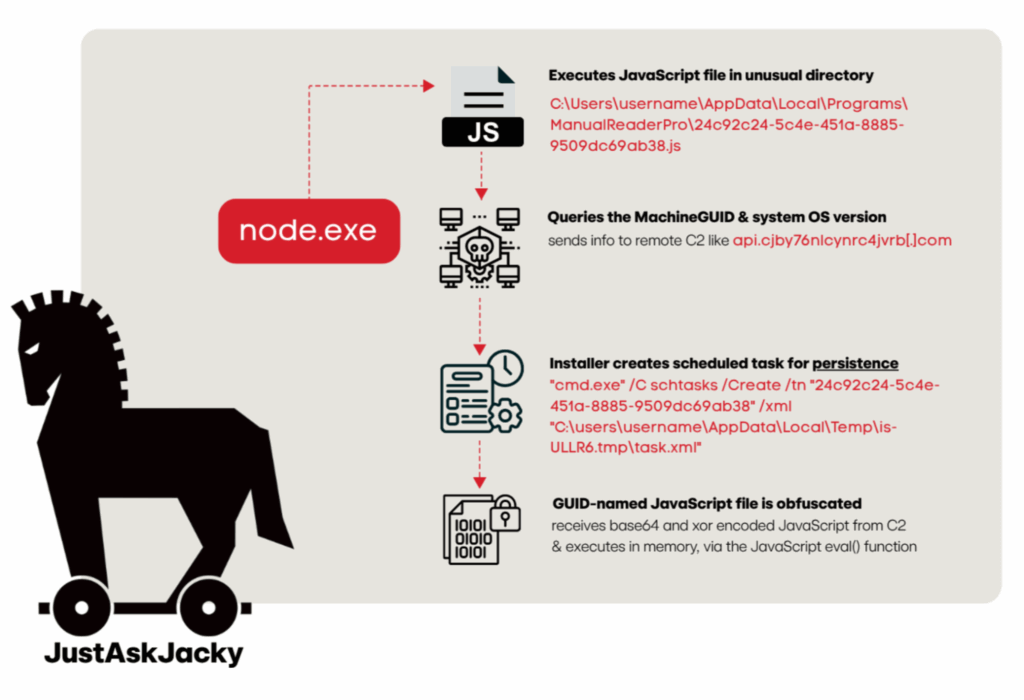
node.exeattempts to execute a JavaScript file in an unusual directory. The directory shares the name of the installer lure, and the JS file will have a GUID-appearing filename.
For example:"cmd.exe" "node.exe C:\Users\username\AppData\Local\Programs\ManualReaderPro\24c92c24-5c4e-451a-8885-9509dc69ab38.js"node.exequeries the MachineGUID and OS version of the system and sends that information to a remote command-and-control (C2) framework via an outbound netconn to a Domain Generation Algorithm (DGA)-like domain, such asapi.cjby76nlcynrc4jvrb[.]com.- The installer creates a scheduled task for persistence that will execute
node.exewith the JavaScript file as a parameter :"cmd.exe" /C schtasks /Create /tn "24c92c24-5c4e-451a-8885-9509dc69ab38" /xml "C:\users\username\AppData\Local\Temp\is-ULLR6.tmp\task.xml" - The GUID-named JS file is obfuscated. After deobfuscation, the code reveals it receives base64 and xor encoded JavaScript from its C2 and executes it in memory, via the JavaScript
eval()function.
Analysis of a JustAskJacky sample identified strings related to cryptomining in memory, suggesting that cryptomining code might be sent back over the C2 in that particular sample, and indicates that cryptomining may be a goal for this threat. If the operators behind JustAskJacky are capable of sending cryptomining strings, they could potentially send arbitrary strings and commands to victim systems as well.
JustAskJacky creates a scheduled task for persistence, and this offers a detection opportunity.
Detection opportunity: Creation of a scheduled task using schtasks.exe in the AppData directory:
The following pseudo-detection analytic identifies creation of a scheduled task using schtasks.exe in the AppData directory. Threats like JustAskJacky use scheduled tasks to create and maintain persistence on victim systems. Some legitimate installers or administrative activity might also do this, so you may have to add exclusions for legitimate task creation strings in your environment.
command_includes ('appdata\local')
&&
process ==(cmd.exe)
&&
child_process_command_includes ('schtasks', '/create', 'appdata\local', '/xml')