Expert AI agents: the future of SecOps is here
Benefit from agentic AI in your security program today
99.6% threat accuracy
3 min AI agent investigations
↓60% triage + notification time
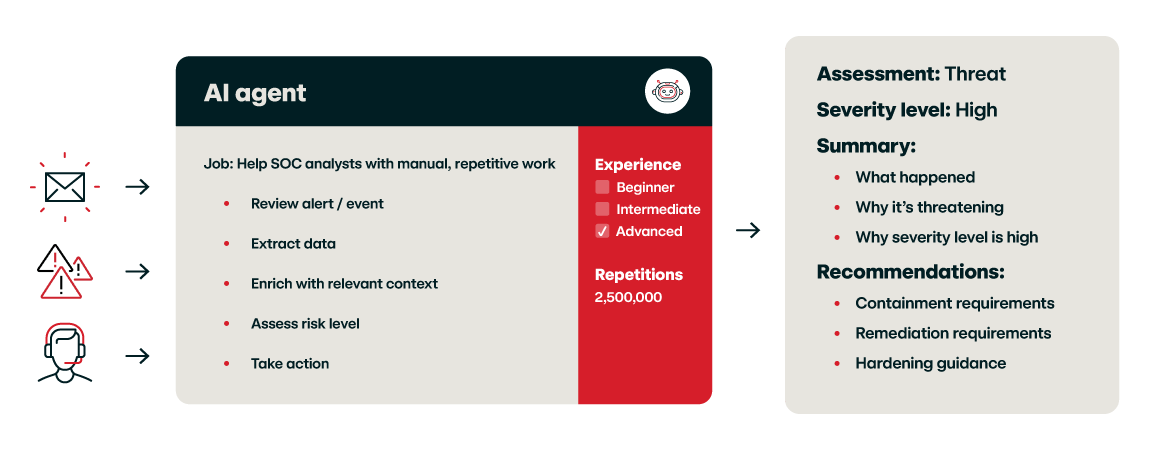
What is an AI agent?
An AI agent is a program that dynamically interacts with data and systems to execute a job based on real-time inputs and context.
Powered by AI models like LLM, these agents adapt their behavior based on tasking – a massive upgrade from rigid automated workflows.
Our Approach
Red Canary’s AI agents and experts deliver SecOps excellence at machine speed
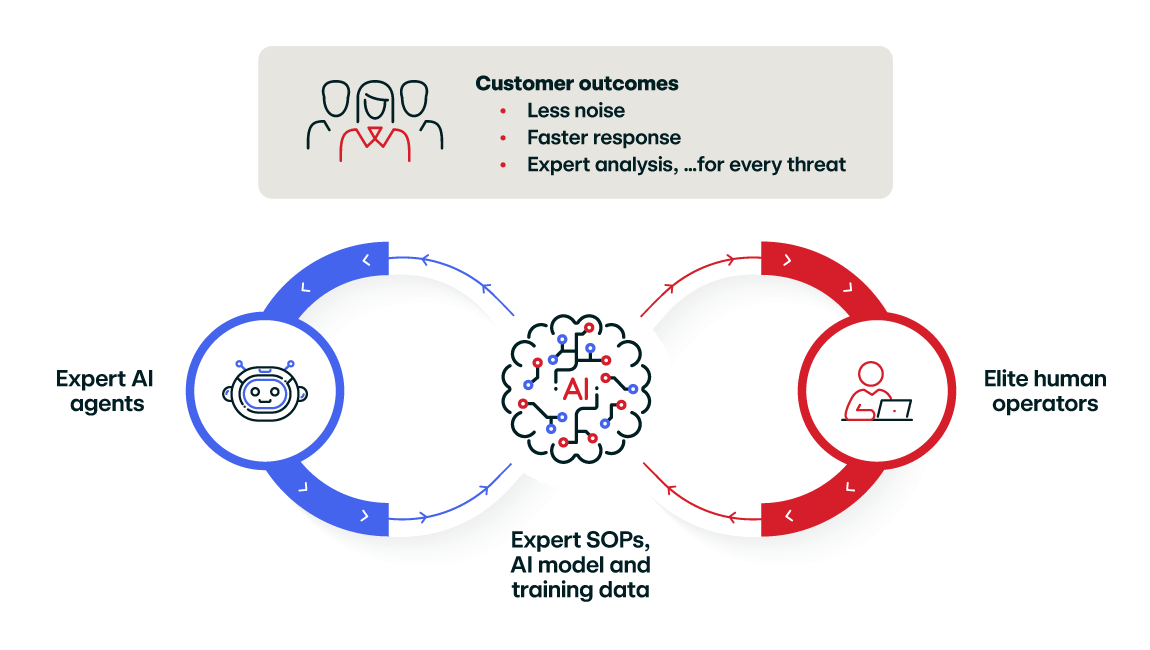
Red Canary AI agents are different:
Most AI agents chase autonomy at the expense of reliability. Red Canary’s expert AI agents are built from a strong foundation and continuously improved to ensure quality and predictability.
- Imbued with a decade+ of real-world security operations experiences
- Guided by expert-crafted standard operating procedures
- Deployed at scale knowing what great output looks like
- Managed and tuned by elite human operators
- Continuously optimized with feedback and new intelligence
Meet Red Canary's AI Agents
Detection Engineering / SOC Analyst agents
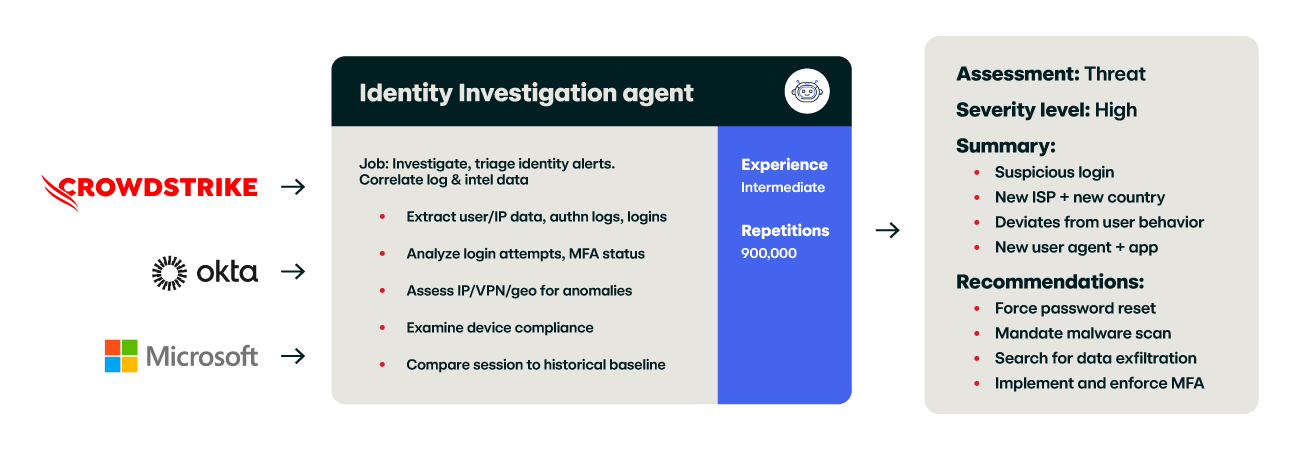
- Identity Investigation agent, Crowdstrike Falcon Identity
Investigate and triage identity-based security alerts from the Falcon Identity Protection platform. - Identity Investigation agent, Microsoft Entra Identity Protection
Investigate and triage alerts from Microsoft Entra Identity Protection. - Identity Investigation agent, Microsoft Cloud App Security
Investigate and triage identity security alerts from Microsoft Cloud App Security. - Identity Investigation agent, Okta Workforce Identity
Investigate and triage security alerts from Okta Workforce Identity. - Identity Investigation agent, User Baselining & Analysis
Analyze login patterns over a 30-day period, identifies anomalies, and generates concise reports - Identity Investigation agent, Cisco Duo
Investigate and triage security alerts from Cisco Duo Trust Monitor. - Cloud Security Investigation agent, AWS GuardDuty
Investigate and triage security alerts from AWS GuardDuty - Endpoint Investigation agent, Microsoft Defender for Endpoint
Investigate and triage security alerts from Microsoft Defender for Endpoint. - Endpoint Investigation agent, SentinelOne
Investigate and triage security alerts from SentinelOne Singularity Platform - Endpoint Investigation agent, Red Canary MDR for Endpoints
Investigate and triage EDR events from Red Canary’s detection engine - SIEM Investigation agent, Microsoft Sentinel
Investigate and triage security alerts from Microsoft Sentinel. - SOC Event Investigator agent, Threat Analysis
Provide summaries, recommendations, and narratives about a threat to aid understanding and response. - SOC Event Investigator agent, Notes & Annotations
Add context to threat timelines related to user activity vs typical baseline behavior. - SOC Event Investigator agent, Intelligence Insights
Provide detailed threat intelligence context for ongoing security investigations, including profiles. - SOC Event Investigator agent, Platform & Tool Assistance
Provide knowledge to SOC personnel regarding Red Canary products and Copilot features - Email Investigation agent
Assess likelihood of email being a phish or not a phish, and provide a reason why.
Incident Response agent
- SOC Event Investigator agent, Response & Remediation
Provide actionable plans for containment, eradication, hardening, and escalation risks.
Intelligence agent
- SOC Event Investigator agent, Intelligence Insights
Provide detailed threat intelligence context for ongoing security investigations, including profiles.
Supported Integrations
The Workflow
Agentic security operations in action
Investigating suspicious logins is one of many use cases where our AI agents & human experts collaborate. Red Canary Identity Investigation agents:
- Extract relevant information from alerts and logs
- Compare sessions to historical baselines and recent login context
- Summarize threat activity and provide clear response and remediation recommendations
FAQs
How can I access these AI agents?
Red Canary MDR customers already have expert AI agents working on their behalf. We are actively exploring pricing and packaging models, alongside MCP server options, for future customers looking to access these AI agents directly.
What data was used to train these AI agents?
Our AI agents are trained on 11+ years and counting of high-fidelity threat detection, investigation, and incident response data and industry-leading security operations workflows. The richness and reliability of the training data is what contributes to a 99.7% threat accuracy rating and rapid responses times when they collaborate with our human experts.
How do you ensure the privacy of my data?
Data utilized by our AI agents never leaves Red Canary controlled infrastructure for processing, storage, training or any other reason. Your data is (1) not available to other customers, (2) not available to third parties, (3) not used to train external AI models, and (4) not used to improve any third-party products or services. The underlying AI models do not interact with other external services, such as ChatGPT.
How does Red Canary get feedback on AI agent performance?
We solicit customer feedback–’thumbs up, thumbs down’ on outputs–in our product and manually review all off-target feedback. We also continuously measure the impact of AI agents on our accuracy, completeness, and timeliness of threat notifications. We only use AI agents to the extent that they benefit our overall performance for our customers.
How do you ensure the outputs of your AI agents can be trusted?
We validate trustworthiness of AI agent performance via extensive functional testing in which all outputs that vary beyond 10% of our ideal output are manually inspected. And as mentioned in the prior question, we continuously measure the impact of AI agents on our accuracy, completeness, and timeliness of threat notifications. We only use AI agents to the extent that they benefit our overall performance for our customers.