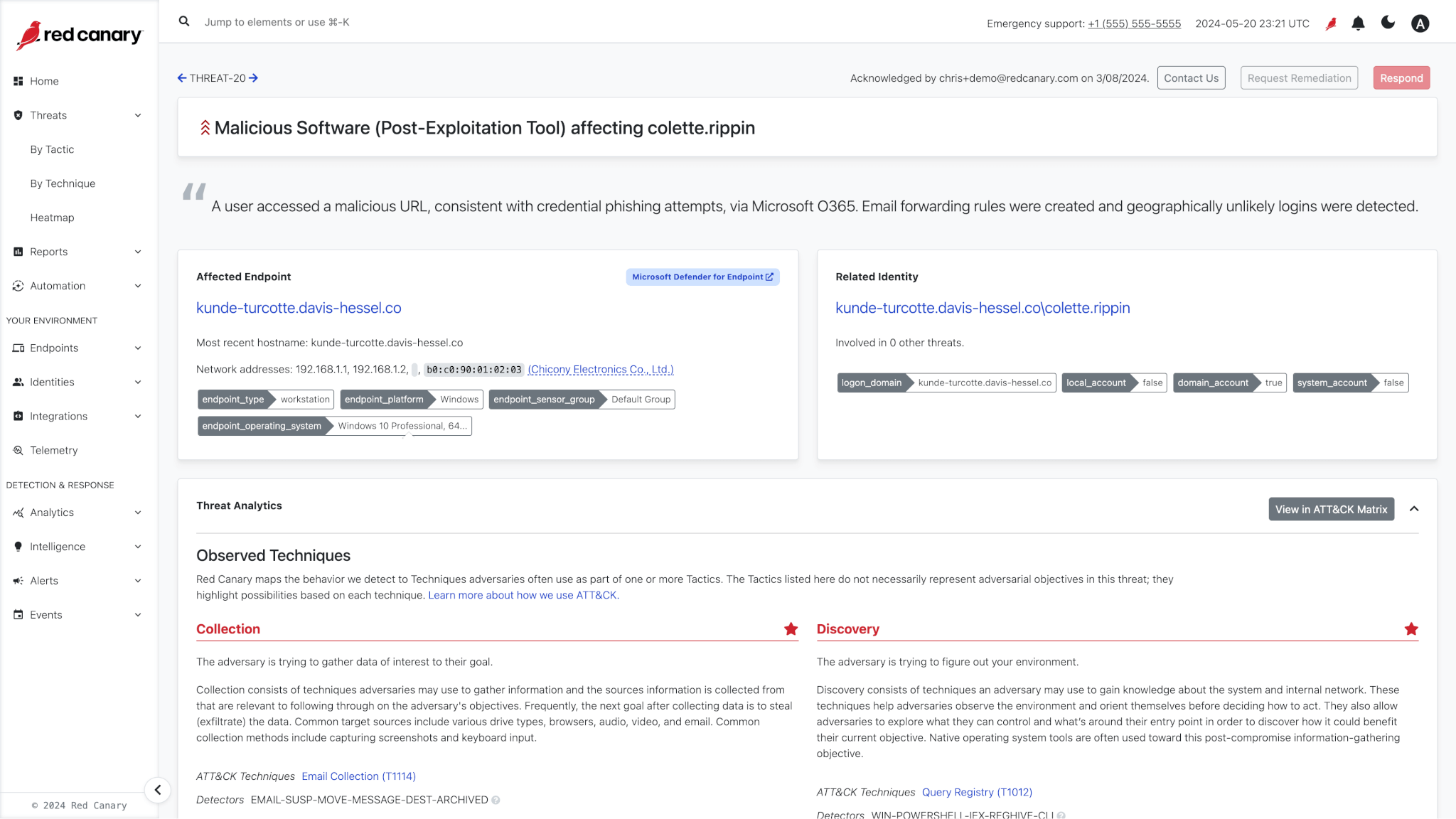
SQL search and analytics
Use SQL to search based on specific attributes–IPs, hostnames, URLs, date/time ranges–and run basic statistical analyses to support internal investigations.
Available now
Avoid paying a premium for high volume, low fidelity security data storage. By sending that data to Red Canary, you’ll save money while maintaining accessibility for your team’s and Red Canary’s investigations.
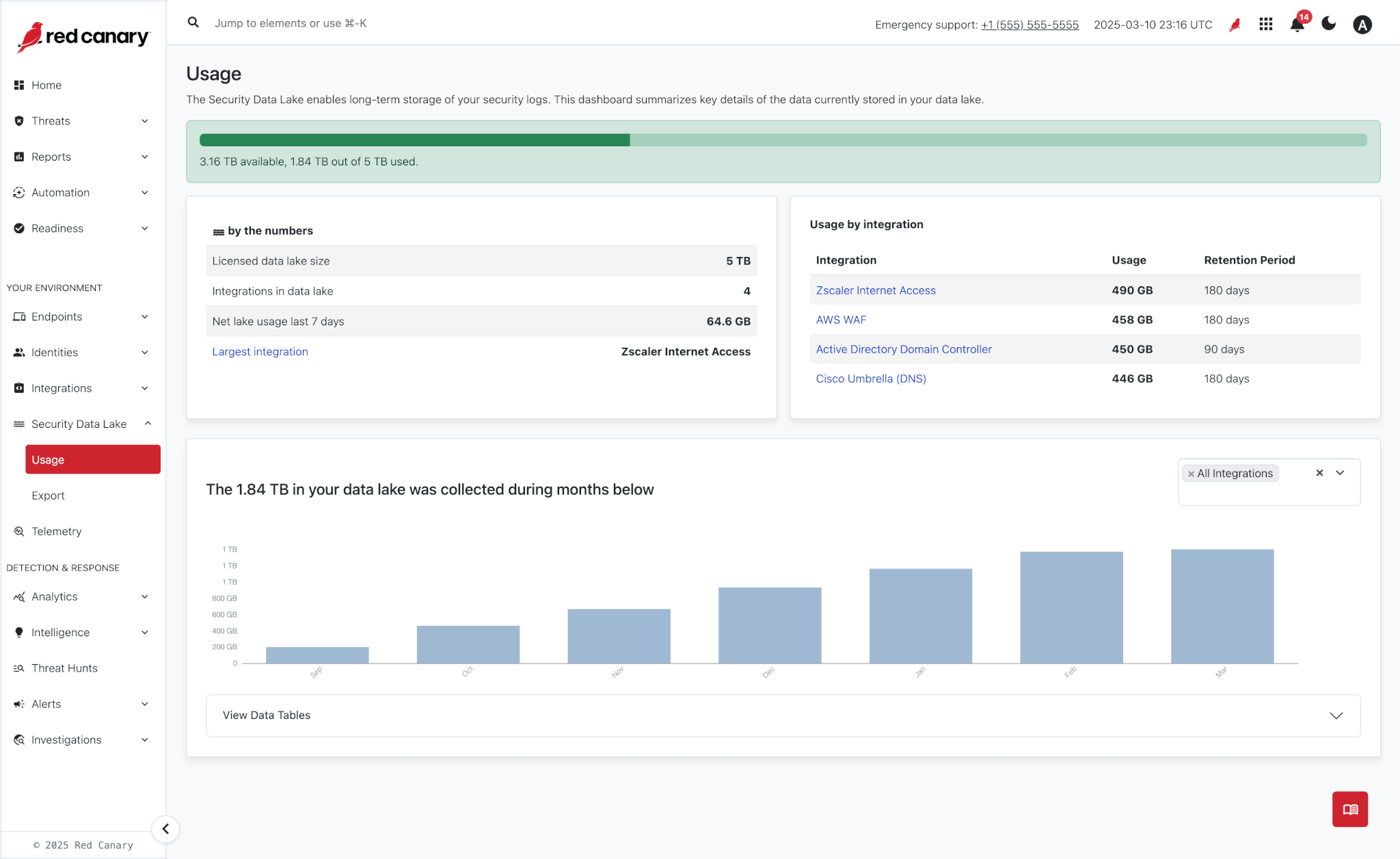
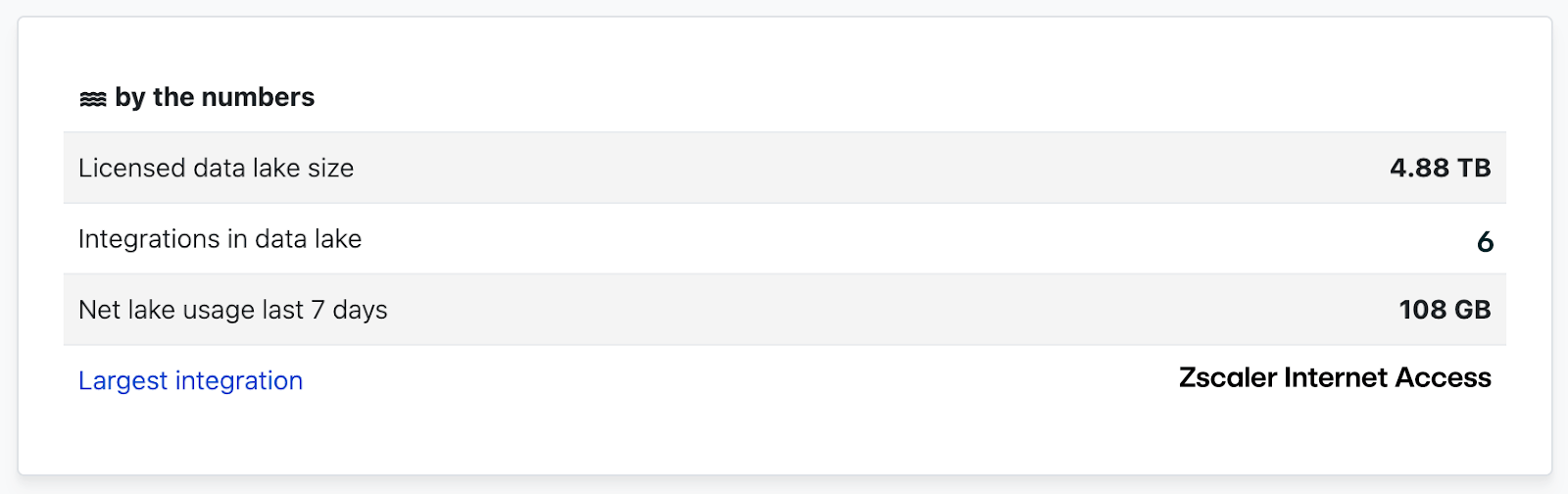
Pay a fraction of SIEM storage costs for high volume, low fidelity data sources like Firewall, DNS, and SASE logs.
Prove to auditors that your data is retained and can be retrieved on-demand. If you need to export specific logs you can do so at any time.
Ensure visibility into your data for your team’s and Red Canary’s investigations, improving your security posture.
Security leaders face tough tradeoffs when managing security data. Storing too much in a SIEM results means you’re overpaying on infrequently searched, low-value data, while managing a data lake adds infrastructure headaches. You need a solution that reduces overhead and keeps data accessible at all times.
Store raw data–JSON strings, syslog messages, anything that’s line delimited that you can write to an S3 bucket–for any length of time specified by you.
Available now
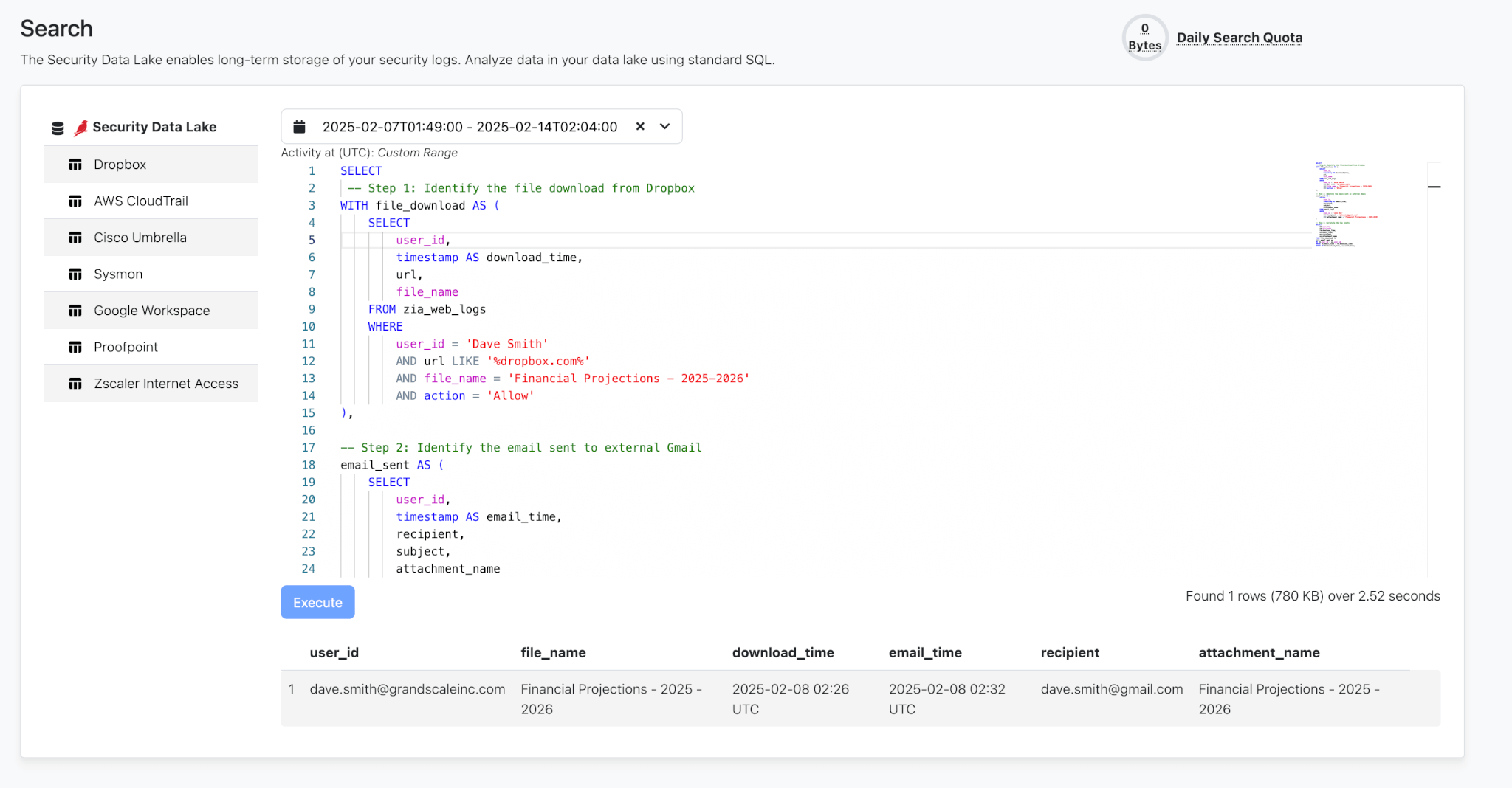
Use SQL to search based on specific attributes–IPs, hostnames, URLs, date/time ranges–and run basic statistical analyses to support internal investigations.
Available now
Red Canary can leverage the Security Data Lake during our investigations, strengthening your detection and response coverage.
Target availability H2 ‘25