Learn how adversaries level up to access sensitive systems and information.
Experts from Red Canary, Carbon Black, and MITRE ATT&CK weigh in on how privilege escalation looks on various operating systems and what you should collect to detect it.
Why you’ll want to watch the webcast:
- Get a better understanding of privilege escalation and how it’s being used across operating systems
- Find out if you have the right tools in place to provide detection coverage
- Learn useful analytics for observing privilege escalation in your environment
- Discover additional ways to test and implement actionable detection strategies
00:35 Presenter Introduction
01:11 What is Privilege Escalation?
01:17 “When an adversary tries to gain higher level permissions than they start with. Compared to a normal user, a system or root level user can be used to leverage additional adversary goals like credential dumping or lateral movement” -Sarah
01:37 Webinar Agenda
02:21 Privilege Escalation: Windows
03:12 “In the case of Access Token Manipulation, the adversary’s main goal is to trick the system into believing that the running process belongs to someone other than themselves. It is like stealing someone’s work badge to get into a building you can’t.” -Sarah
03:43 “Bypass User Access Control or UAC is a Windows feature that prevents harmful programs from making changes to a user’s computer by prompting the user for confirmation.” -Sarah
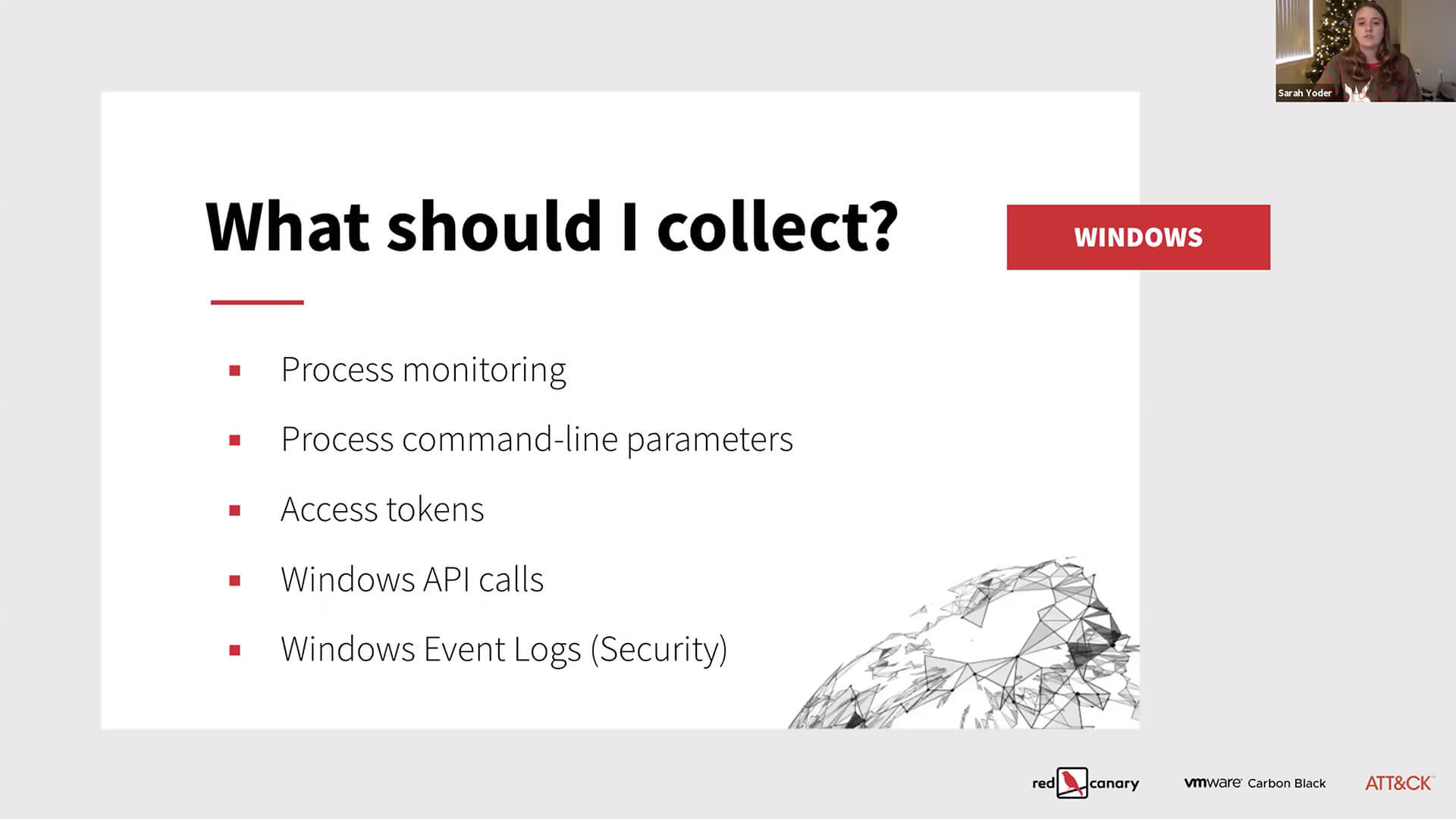
04:40 Collecting Data: Windows
04:56 “What you specifically collect in these instances is really going to depend on what tooling and systems you have in your environment.” -Sarah
05:14 Detecting Behaviors: Windows
05:38 “If a process starts, and a child process with a higher integrity level than the parent is found, then that is probably an indication of privilege escalation.” -Sarah
06:57 Real-World Examples
08:08 “Neither FODHELPER or EVENTVWR normally spawn children, they are usually running under an administrator account. Those are really good indicators for threat hunting and detection in your environment for UAC bypass.” -Cathy
09:07 Privilege Escalation: macOS
09:45 “With macOS, most of the techniques require user interaction. Most of the things you will see in the wild actually require the user to enter a password. The problem is that most of the prompts for escalation pretty much look the same. Attackers are able to make these look however they want.” -Erika
12:32 “The user gets so used to putting their password in for everything that they start not caring or not looking into what it is asking: ‘Do I really want to authorize this application?’ It is very easy to masquerade as a different application.” -Erika
18:13 “On macOS and Linux, you have a larger set of tools—command line tools—that are very powerful.” -Erika
21:34 Collecting Data: macOS
21:45 “Your typical malicious program is going to have to establish some sort of persistence so that when you reboot, it’s going to start up automatically. There are a lot of ways to do that.” -Erika
22:00 “There is a system utility called Log that will collect and filter all of these events. It is very powerful, but also very robust so you need to know what you are looking for.” -Erika
24:20 Detecting Behaviors: macOS
25:23 “You have to look at the events that lead up to the authentication event and the events that happen after.” -Erika
27:52 “One of the most important things for macOS, but also Windows and Linux, is you never should have to re-install Flash Player. If you do, you should go to the Adobe website and download it to verify that it is actually signed by Adobe and is the legitimate copy of it.” -Erika
31:20 “The adversaries almost always have writable access which is the key for temporary directories…being able to write what the adversary wants to then execute.” -Sarah
32:15 Real-World Examples
34:20 “Shlayer would download something then actually decrypt, decode, and then do some other manipulation to a final script. It is a series of scripts that finally downloads the last payload, which is the malicious final payload.” -Erika
36:10 “The Lazarus Group, which is a malicious actor group, has a new implant that is able to do in-memory download and execution of additional software. So it is not even doing something on a command line. That is typically not going to be logged.” -Erika
37:13 “You are more likely to detect the activity that happens after the privilege escalation occurred.” -Cathy
38:02 Privilege Escalation: Linux
38:58 “Normally an attacker is going to try to obtain Shell access in order to get privilege escalation on Linux” -Cathy
41:36 “If less is running as root, then those commands or that Shell that spawned from less will be running with those same privileges.” -Cathy
42:43 Collecting Data: Linux
42:46 “On Linux, you want to collect Network Traffic and Netflow, Authentication Logs, and Process Monitoring via Event Logs. Or you could also use osquery or auditd.” -Cathy
43:02 How You Detect It
43:12 “One specific command line isn’t going to give you a good detection rate. It is going to generate a lot of false positives because a lot of command lines that may be malicious can also look like the same activity an admin would be doing on the system.” -Cathy
44:52 Real-World Examples
56:07 “Take the downtime to patch things. A lot of times there is a long lead time after a patch has been released to when an enterprise is actually going to be able to implement it across an organization because you have to do so much testing.” -Erika
47:20 Why Privilege Escalation Matters
48:03 “If you are seeing Privilege Escalation on your systems, that is probably going to be more indicative of other adversary goals happening.” -Sarah
55:18 Questions & Answers
55:33 Question 1: Making the end user the gatekeeper for security is a sure way to ensure that red actors keep winning. Is there any hope for true process or application isolation or using containers to limit the potential damage these things can do?
56:50 “There is a balance between ‘What do I block?’ versus not making it impossible for application developers to get their applications to run on these systems.” -Erika
58:43 “Users are the weakest points of many security enterprise environments.” -Julie
58:53 Question 2: Have you seen a trend towards actors utilizing more open source tools to gain initial entry into a network and then switching to more custom and more proprietary tools once inside?
01:00:10 “Using something that may fly under the radar to get into the system first is going to be less likely to be detected.” -Erika