What we detect
Account takeover
Prevent attackers from gaining initial access and compromising email accountsCompromised email accounts
Detect malicious email collection, unauthorized rule creation, and morePhishing
Assess reported phishing emails and identify compromises from phishingKey benefits
Unmatched depth of detection
By processing massive amounts of streaming data, Red Canary can significantly increase the detection of confirmed email threats
Speed and flexibility of remediation
Our use of AI, automation, and human expertise empower you to quickly respond to phishing emails and contain elusive email threats.
Quality of partnership
Red Canary does the heavy lifting for your team while providing unlimited access to our experts
“Having that extra set of eyes really helps. Now we can confidently discuss the state of our environment and security posture. We aren’t just taking another team’s word for it; we can see it for ourselves. We have a lot of faith in Red Canary.”

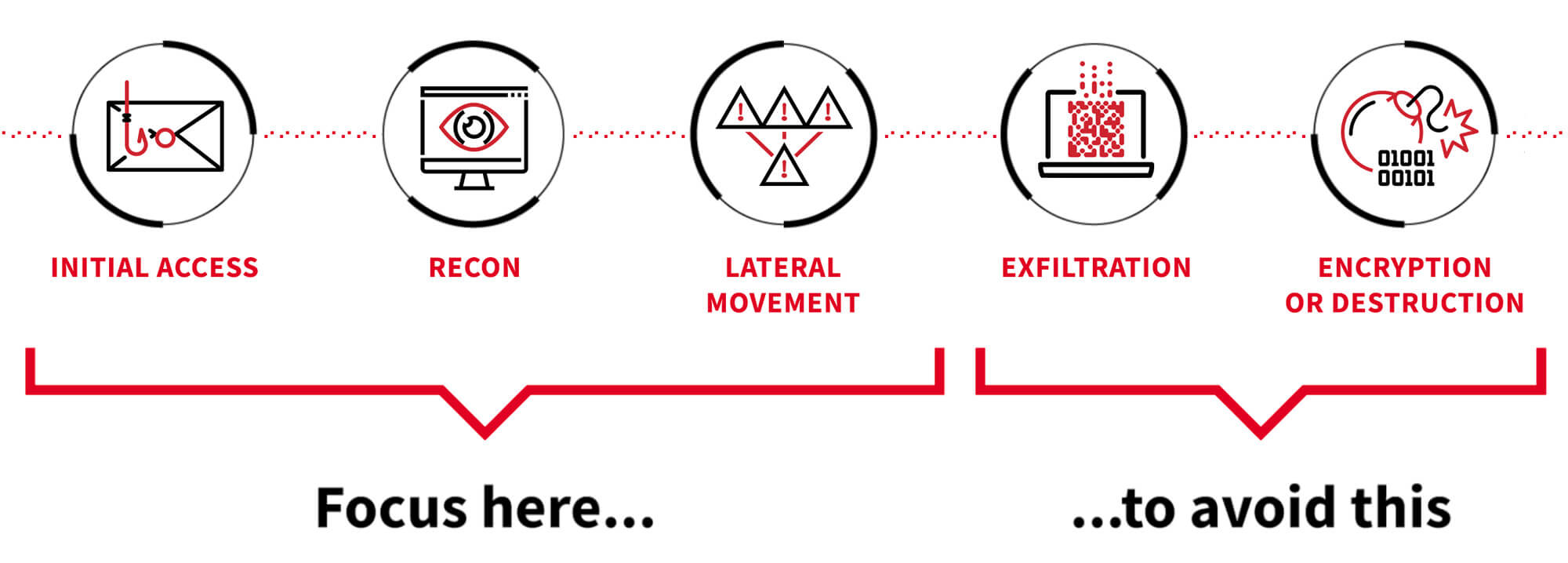
Red Canary optimizes for early-stage adversary detection
AI agents and human experts power rapid phishing response
Red Canary’s AI agents streamline triage and investigation, enabling our human experts to swiftly confirm threats. For example, our Phishing Triage agent enriches user-reported emails and evaluates them before our human experts review.
Explore Managed Phishing ResponseWe find and stop elusive threats
Red Canary Managed Detection and Response (MDR) combines trailblazing security technology and human expertise to detect threats earlier and stop them faster.
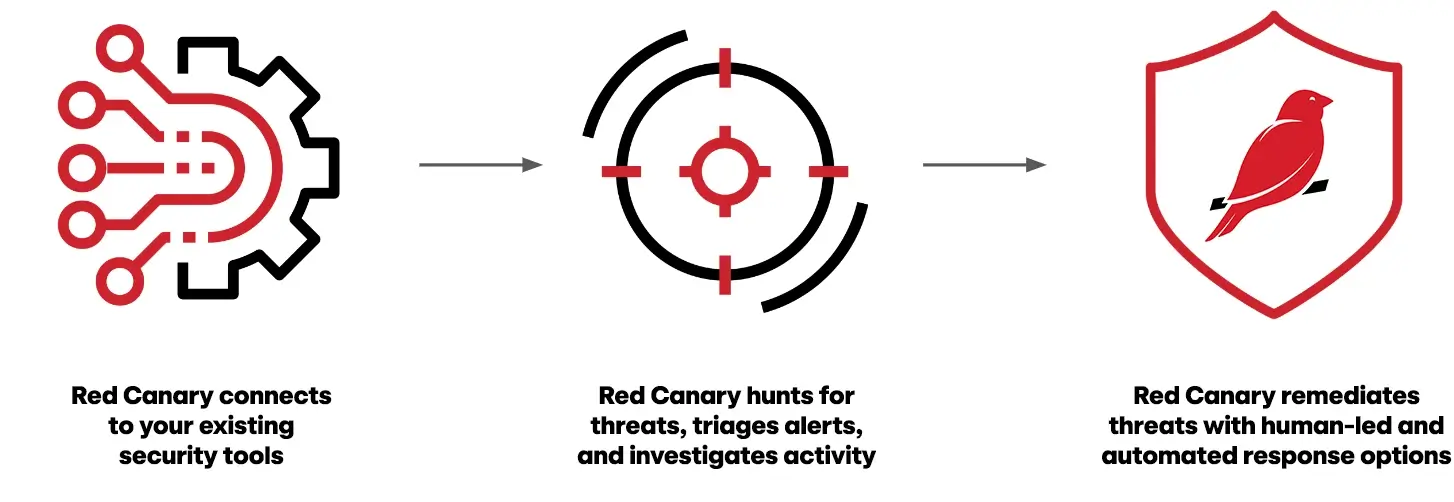
- Data is ingested from your email applications.
- Thousands of behavior-based detections and proprietary threat intelligence are applied to hunt for suspicious activity.
- Our team of experts investigates activity, eliminates noise, and correlates events from disparate sources.
- View investigations in a unified timeline, written in clear language with all the necessary context, making it easy to understand the root cause and scope of a threat.
- Take action with our combination of automated and human-led response capabilities.
learn more about red canary mdr
Red Canary Managed Detection and Response (MDR)
Red Canary Managed Phishing Response
Readiness Exercises
Security Integrations
Red Canary integrates with dozens of endpoint, network, cloud, and SaaS security technology tools to help you detect and stop threats faster.