Protect your users from threats including:
Account compromise
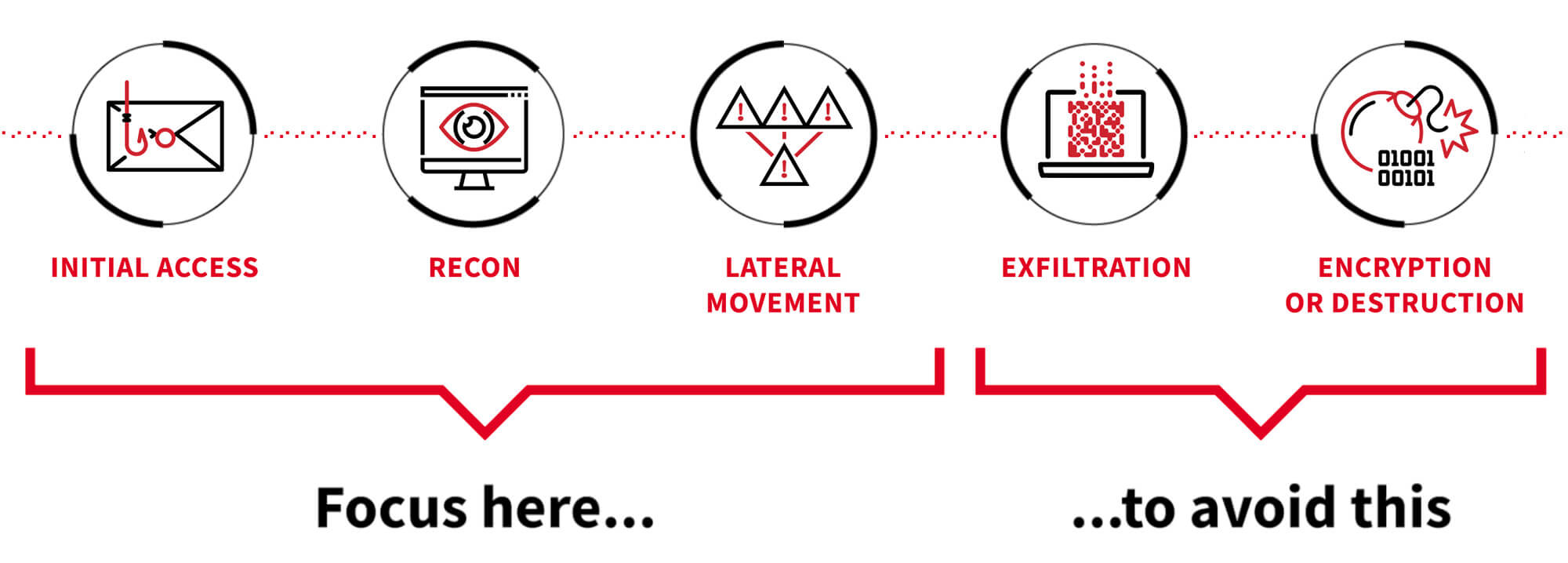
Prevent attackers from gaining initial access and compromising workloadsMisconfigurations and misuse
Remediate cloud security misconfigurations such as exposed systems or codeData exfiltration
Identify potential exfiltration pathsWe find and stop threats, no matter where adversaries choose to attack
Red Canary Managed Detection and Response (MDR) combines trailblazing security technology and human expertise to detect cloud threats earlier, and stop them faster.
Red Canary protects customers’ infrastructure running atop the world’s leading cloud providers, including Amazon Web Services (AWS), Microsoft Azure, and Google Cloud. We unify data from those platforms with critical insights from leading cloud security tools like Wiz to detect and stop cloud threats before impact. Our comprehensive integrations and 24×7 cloud security expertise help you manage your entire cloud attack surface—from control plane to workload—proactively addressing both active threats and risks like vulnerable software, misconfigurations, and toxic combinations.
Key benefits
Secure multicloud environments
Gain 24×7 detection and response to suspicious activity and patterns in AWS, Azure and GCP through advanced analytics on log data as well as investigation of Wiz alerts and issues.
Augment your SOC with cloud expertise
Add multicloud threat intelligence, threat hunting, and a rapidly expanding library of cloud detectors to your SOC in days, not months or years.
Extend protection of critical production Linux
Detect cloud runtime threats across your workloads and containerized environments with the most lightweight and performant Linux EDR in the market.
“We’ve worked with many of the members of the Red Canary team for years now, and we know that when it’s 'go time' they’re going to execute in a very disciplined manner.”

- Red Canary ingests comprehensive security data from cloud providers, cloud control plane tools and leading CSPM platforms like Wiz.
- The Red Canary platform applies thousands of behavior-based detections and proprietary threat intelligence to hunt for suspicious activity.
- Experts investigate activity 24×7, eliminate noise, and correlate events from disparate sources to confirm threats.
- Access clear, contextualized investigations, making it easy to understand our experts’ decisions as well as each threat’s root cause and scope.
- Act swiftly with automated and guided response capabilities.