threat
Emotet
Emotet is a trojan known for delivering follow-on payloads, including Qbot, and, in some cases, ransomware. Despite an attempted takedown in 2021, adversaries continued to leverage Emotet throughout 2022.
Threat Sounds
After a largely dormant 2021, it had been a while since we’d seen Emotet in customer environments, almost as long as it had been since we thought about the band Staind.
Editor’s note: While the detection opportunities and analysis on this page are still relevant, it has not been updated since 2023.
Analysis
Emotet is an advanced, modular trojan that primarily functions as a downloader or dropper of other malware. It’s disseminated through malicious email links or attachments that use branding familiar to the recipient. Emotet focuses on stealing user data and banking credentials, and opportunistically deploys itself to victims. Emotet is polymorphic, meaning it often evades typical signature-based detection, making it more challenging to detect. Emotet is also virtual machine aware and can generate false indicators if run in a virtual environment, further frustrating defenders. Emotet has been active and evolving since 2014, despite a temporary takedown in 2021.
A year searching its soul
Following the disruption of its operations and infrastructure in January 2021, Emotet operators resumed activity in late 2021, experimenting with AppX bundles to deliver the malware. After that initial divergence, we also witnessed operators use different delivery methods, including Excel 4.0 macros, and shortcut (LNK) files.
Following a weekend of what appeared to be testing activity in April 2022, operators began using LNK files to deliver Emotet, effectively replacing the Excel 4.0 macros observed in previous campaigns. Red Canary observed attempts to deliver these LNK files via phishing emails containing password-protected ZIP files. If executed, the LNK files spawned PowerShell commands that downloaded and executed additional content from an obfuscated URL.
The operators closed out 2022 by reverting back to Excel macros for distribution and going dark after a final flurry of phishing activity in November.
Payload patterns
During the year the larger community noted that Emotet deployed Cobalt Strike beacons during some infections. In addition, there were two distinct groups of Emotet distribution: Epoch 4 and Epoch 5. These two distribution groups often followed different distribution patterns and experimentation. For example, at one point during the year, Epoch 4 distributed Emotet via malicious AppX installers, whereas Epoch 5 distributed the malware via Excel macros during the same time period.
Looking ahead
Despite making a splash of a comeback, Emotet hasn’t quite regained its former glory as one of the most dangerous crimeware families. It’s possible that the 2021 takedown contributed to a diversification of delivery affiliates, leading some adversaries to move on to alternative options. In 2023 we’re on the alert for Emotet to resume phishing and try to regain footing.
take action
We recommend multiple approaches toward mitigating against malicious macro threats like Emotet:
- Block macros from running in Office files from the internet with GPO. Microsoft published a great blog post on how to implement this.
- Validate your email security gateway configuration. Do you normally deal with macro-embedded files such as
.docmor.xlsm? If not, you may want to think about adding those and other macro-embedded files to your blocked attachment policy. Microsoft has a list of Office file formats, and you can use it to help determine what to add to your block policy. - Educate everyone. While you should never expect your non-security coworkers or employees to be security experts, they can serve as a valuable detection signal when trained to identify and report suspicious behavior.
Detection opportunities
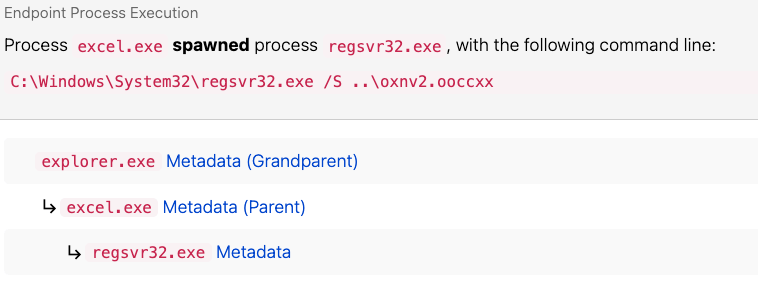
Regsvr32 execution from Microsoft Excel
In the last quarter of 2022, we observed Emotet resume using execution via Microsoft Excel macros spawning regsvr32.exe. We detect this simply by looking for Regsvr32 process execution with a parent process of excel.exe. While this may legitimately happen for some Excel add-ins, it’s fairly rare, and our strategy has proven successful in identifying the early stages of Emotet execution.
parent_process == 'excel.exe'
&&
process == 'regsvr32.exe'
Testing
You can replicate telemetry matching Emotet initial infection activity using a combination of Atomic Red Team tests. Organizations can modify and use these tests: