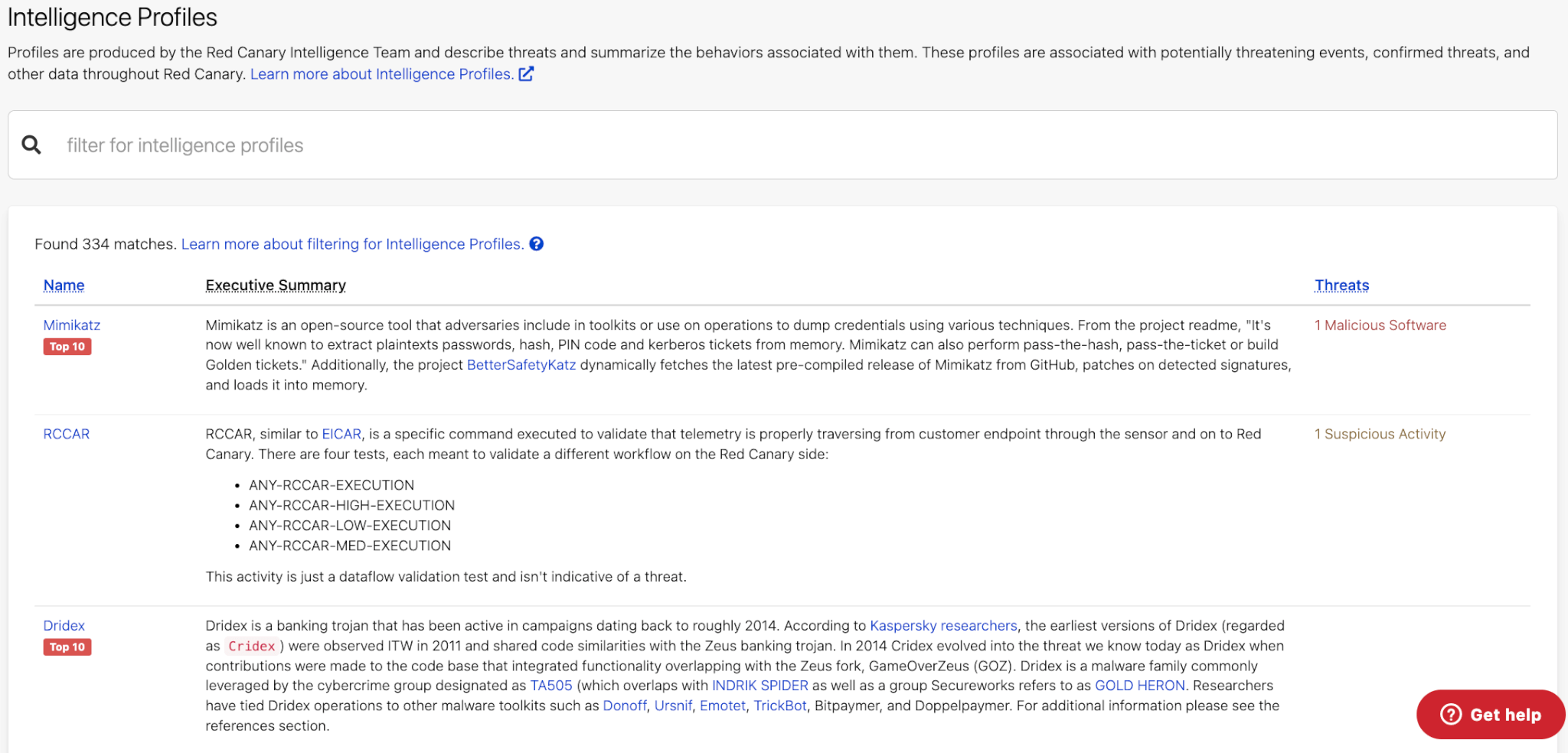
As a leading MDR provider servicing a large number of customers across a variety of industries, we have the benefit of taking in all of that threat information to build out better threat intelligence. Not only do our customers benefit from this level of threat intelligence and research passively through our improved detection abilities, but Red Canary also uniquely provides this information to all customers—for free—within the portal through Intelligence Profiles.
Red Canary’s Intelligence Team uses our visibility into many sources to track and identify threats. We then use that knowledge to create Intelligence Profiles that we provide to all customers as part of what you get with Red Canary. These profiles provide summaries and deep-dives into the tactics, techniques, and procedures of malware families, threat groups, activity clusters, and other threats along with Red Canary’s detection coverage as well as remediation advice. We are constantly updating and improving our library of profiles as we discover new threats and information. While most companies charge for this level of threat research and intelligence, Red Canary believes that it is more important to make this information freely available to our customers to arm them with the knowledge they need to respond to threats.
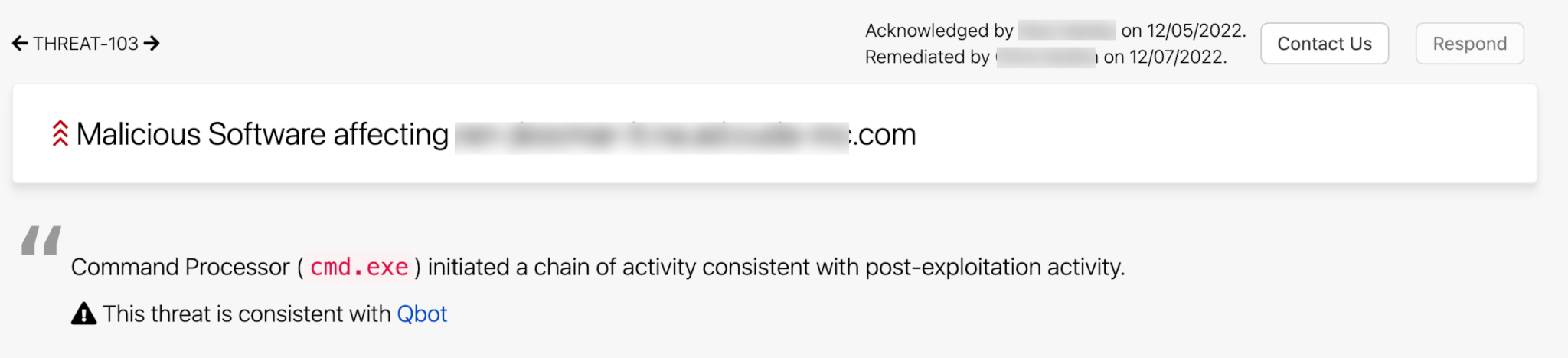
We don’t stop at just providing customers with a library of threat information—we also actively work to identify which of these many threats are in our customers’ environments. Whenever our security teams can identify what named threat is in your environment, we’ll give you that context right in your published threat, allowing you to easily pivot to the Intelligence Profile library to learn about the threat and inform your response.
Now we’re going a step further and allowing customers to take different actions based on what specific threats are in their environment. Red Canary recently released an update allowing customers to use these profiles as triggers in our automated playbooks.
This provides customers an additional layer of granularity and specificity with how they respond to threats as they can now target response actions based on associations to Intelligence Profiles. Actions can be triggered anytime an Intel Profile is associated with a threat, whether it’s during the discovery of the threat or when new information updates a threat that was previously identified but not classified.
Customers may have different risk appetites for various threats. Instead of configuring a “one size fits all” response to threats based on severity or category, they can tune triggers even further based on the specific threat. This can help customers who are hesitant to configure response triggers based solely on threat severity levels—because they worry that a false positive might slip through and impact their operations—since they can further specify when they want to take actions.
For instance, Shlayer is a popular malware found on macOS environments. Because of the potential impact that Shalyer has on an endpoint, Red Canary determines this to be a High Severity threat. Based on other controls they have in place and their risk tolerance, some customers consider Shlayer threats to be Low Severity. With this new capability, customers can differentiate response actions when the threat is associated with the Shlayer profiles versus when it’s a different High Severity threat.
Another use case of how this is impactful is if a customer has endpoints that they cannot isolate when Red Canary sees a general threat but you do want to make sure to isolate threats that are known to move quickly and lead to ransomware. For example Qbot, which was quite active in 2022, is a malware family that has been known to lead to ransomware within minutes or hours. With this new automate feature, you can specify that you want to isolate all endpoints Red Canary observes with Qbot, quickly containing the threat. Using this feature could potentially save you from a ransomware attack.
The possibilities are endless with how you can tailor your automated playbooks based on the association to Intelligence Profiles. What are you going to do with them?