As students head back to school, defenders should also get their pencils out. From mid-July continuing into early August 2023, Red Canary has observed multiple email account compromise (EAC) campaigns targeting educational institutions. We assess the timing of these compromises may be related to the upcoming school year, as students and employees are corresponding with new contacts and registering new accounts to prepare. After pivoting on infrastructure used in one campaign we observed, we surmised that this campaign may be targeting many educational institutions.
A crash course on phishing
One notable campaign began with an adversary logging into an initial victim mailbox, likely using compromised credentials. The adversary then created an email rule with repeated characters named ........ to delete all email messages in the mailbox. Red Canary regularly detects the use of multiple consecutive characters in email rules that adversaries create, making this behavior an excellent detection opportunity.
Once the adversary gained access to the initial victim, they used that access to send internal phishing messages (MITRE ATT&CK Technique T1534) to multiple other email addresses at the same educational institution. These emails contained phishing links to a credential phishing page at a victim-specific subdomain of ukit[.]me. While uKit is a legitimate content management system (CMS), this domain is not associated with it, and we assess it is likely malicious.
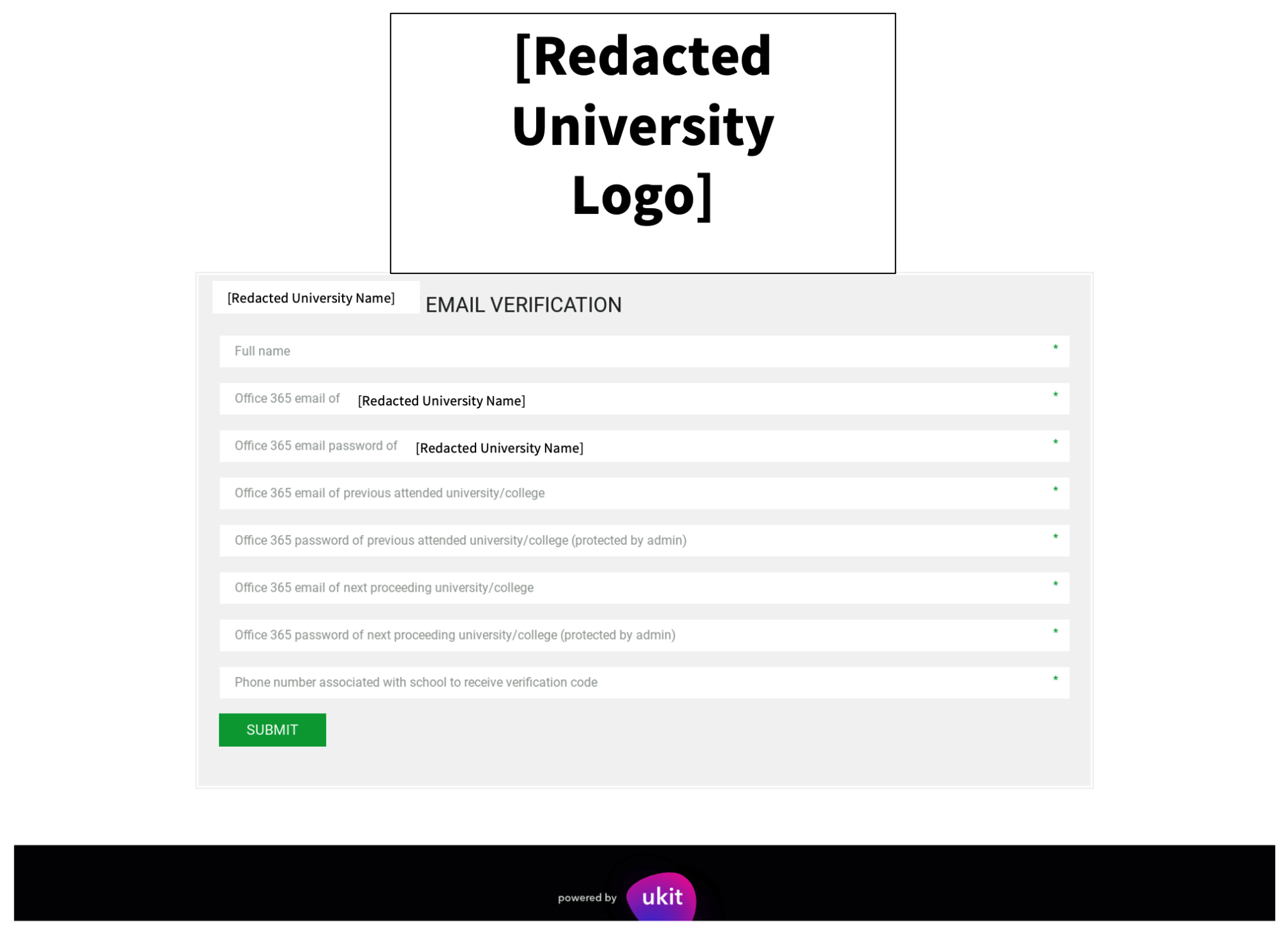
Based on this domain as well as a uKit icon on the credential phishing page, we assess the adversary was attempting to masquerade as the legitimate uKit CMS. As seen in the example below, the credential phishing page requested the victim’s full name, email addresses, passwords, and phone number. (We’ve redacted the university name to respect victim privacy.)
Notably, this phishing page requested not only the email and password for the victim’s current university, but also for a “previous attended university/college” and “next proceeding university/college.” This is particularly concerning because it may allow the adversary to collect credentials for multiple institutions, enabling multiple compromises from a single phishing page. The form also requested the phone number associated with the account. While we have no further information on how this phone number was used, the adversary could be sending additional phishing messages via SMS or, if they had advanced capabilities, intercepting a two-factor authentication code sent to that phone number.
While we initially investigated a single phishing email and phishing page, we then identified multiple phishing pages that appear to target many different educational institutions. Based on open source pivoting using URLscan, we identified that ukit[.]me hosted multiple subdomains with the names of educational institutions that were likely targeted in this campaign. Examples of these subdomains, which we assess are likely credential phishing pages, can be viewed from these URLscan results. (This URLscan query searches for the suspicious domain, ukit[.]me, and a SHA 256 hash of a CSS document that we noticed was consistent across similar pages.)
Study hall: Detection
We recommend searching network logs (such as DNS logs, flow records, and/or proxy logs) for any traffic to ukit[.]me and investigating any findings to determine if a user may have entered credentials. Consider blocking this domain via access controls as well as investigating if any emails contained this domain.
If you are affiliated with an educational institution (or know a cybersecurity friend who works at one), we recommend checking these URLscan results for any registered domain name that contains your institution’s name. If you see a domain name approximating a legitimate university, it may indicate that institution has been or may be targeted in this campaign.
To detect email account compromise in general, we also recommend monitoring email rules for suspicious activity. To detect this specific campaign, we identified an email rule that repeated the same character more than once: ......... Repeated characters in an email rule name may be a useful detection opportunity, as we’ve seen that pattern consistently used by adversaries.
Final exam: Response
If you observe a similar email account compromise, we recommend resetting credentials for affected users and enabling multi-factor authentication to prevent future compromise. Victim organizations should also remove any email rules added by adversaries and investigate additional victims of internal phishing emails. Additionally, we recommend investigating if the adversary accessed additional resources using the compromised accounts, such as accessing OneDrive or SharePoint files.
As the school year starts, we anticipate adversaries will continue to use phishing emails and credential harvesting to gain access into educational institutions. By adding email rule monitoring to your defensive stack, you can increase the likelihood of catching these adversaries before the bell rings.
Thank you to Zach Diehl, Jason Killam, and Tony Lambert for their assistance with this research.