Red Canary is excited to announce full coverage of all major cloud providers, delivering improved visibility and correlated threat activity across multicloud environments.
While migrating to the cloud has enabled organizations to innovate faster and gain numerous benefits, it also poses a number of security challenges. Many of the difficulties organizations face—having the resources and security expertise to properly monitor and secure their cloud, staying on top of threat intelligence, and accurately and quickly responding to new and unique risks and threats—becomes magnified in a multicloud environment. Hosting parts of your infrastructure on multiple platforms introduces even more operational complexity.
That’s why we’ve expanded our intelligence-led security operations platform and threat expertise to provide 24×7 monitoring, threat detection and response, and actionable visibility across your cloud estate.
Protect your multicloud environment
Red Canary now integrates directly with AWS, Microsoft Azure, and GCP alongside native alert ingestion and third-party security tools, providing deep investigations and comprehensive coverage across clouds. We analyze behavior and cloud activity and correlate that data with alerts, identified misconfiguration, and posture management issues to detect threats that others miss. If a threat is ever discovered, our team of threat hunters are there to help you respond, stopping the threat before it can cause damage to your organization.
Coverage
Secure your Azure cloud environment with deeper investigations and enhanced threat detection and response capabilities. Red Canary now ties directly into Microsoft Azure Cloud Audit logs (Azure AD Audit, Signin, Activity, Key Vault Diagnostics, and Storage logs) correlating that behavioral data alongside native Microsoft Defender for Cloud alerts to find and respond to threats others miss.
Stay ahead of adversaries’ subtle defense evasion techniques—such as attempts to remove admin accounts or modifying S3 bucket expiration dates to impair logging capabilities—through the addition of over 30 new threat detectors and improved threat intelligence to Red Canary’s AWS monitoring capabilities.
Detect and respond to unique cloud threats and get greater coverage in GCP as Red Canary enters early access for integrating directly with GCP Audit logs.
Enrich threat data with identified risks and vulnerabilities
Our integrations with Lacework and Wiz (coming soon!) enrich posture management alerts with additional context across your cloud, user identity, and endpoint activity to better operationalize these signals.
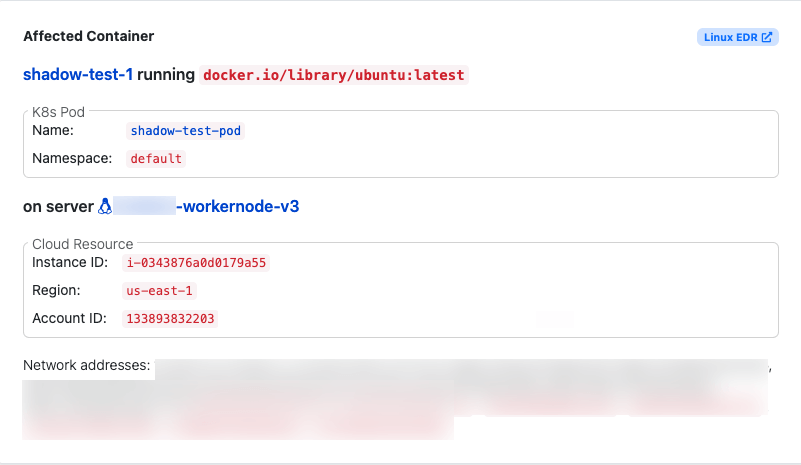
Enhance threat protection in cloud runtime environments
Red Canary’s lightweight Linux EDR agent just got better, with improved metadata collection for containers and Kubernetes. This newly added info provides greater context and insight into where threats are occurring within your containerized environments.
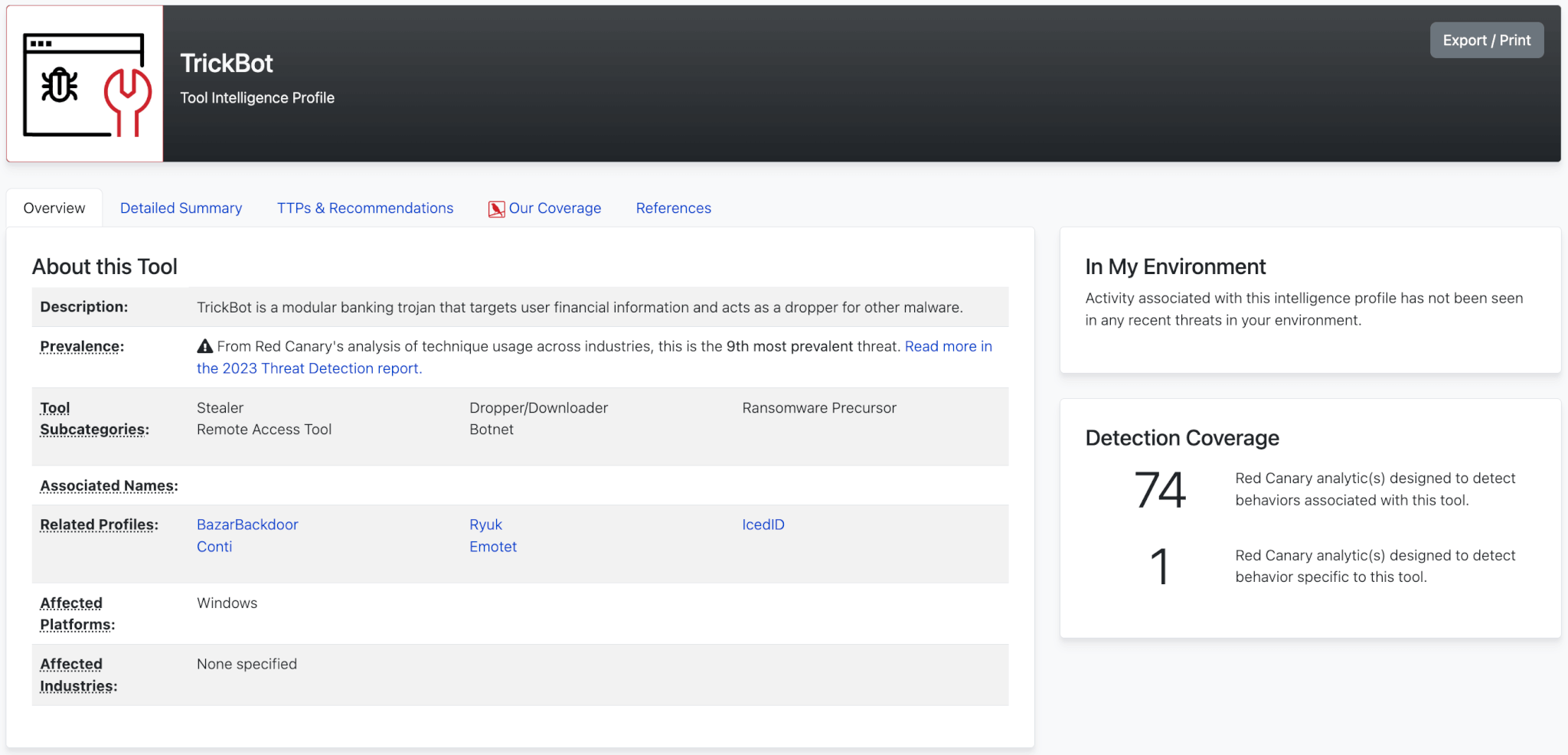
Get actionable threat intelligence
Gain herd immunity from our continuous development of detection analytics informed by the adversary behavior we observe, detect, and anticipate across customer environments. New threat intelligence specific to ransomware and cloud account compromise gives you the actionable insight you need to stay one step ahead of modern exploits and adversary tactics.
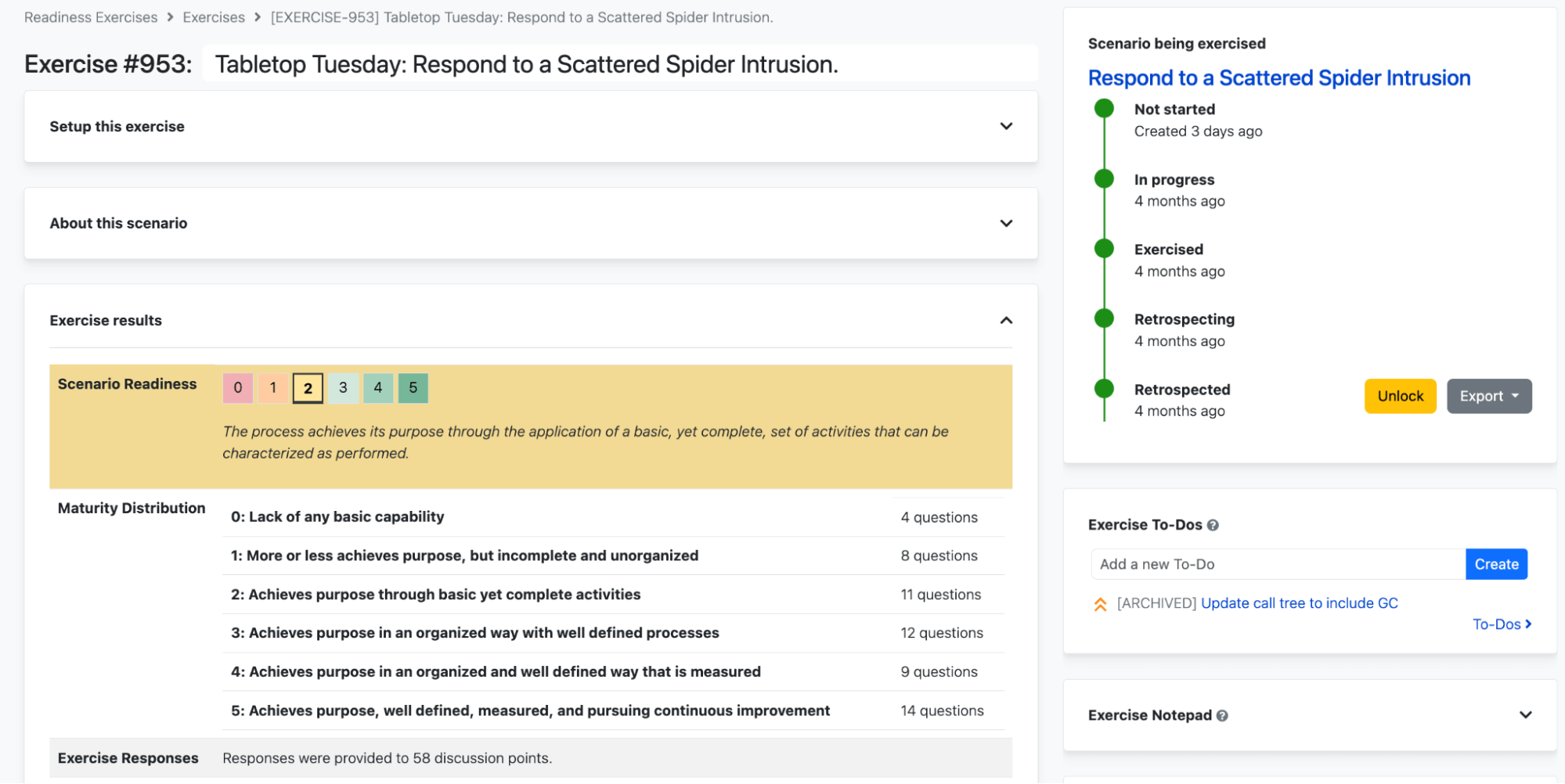
Run more effective tabletops
Prepare your team for today’s most challenging adversaries like Scattered Spider. Readiness Exercises, our learning experience platform, now features even more on-demand scenarios, enabling your team to practice, learn, and strengthen their response to real-world threats affecting endpoints, cloud, and identities. With constantly updated and fresh scenarios, your team can improve their skills to more effectively defend against highly sophisticated threat actors while tracking their ongoing improvement over time.
Operationalize cloud-native SIEM investments
Red Canary streamlines your journey from Microsoft Sentinel purchase to operational excellence. Red Canary now helps you deploy Microsoft Sentinel and optimize it according to your budget, IT landscape, and security goals. Beyond deployment and optimization, our experts lead your team through a security goals exercise to help you clarify your priorities, and we provide you with 130+ analytic rulesets, 100+ threat hunting queries, custom dashboards, automation playbooks, and more. We are at your side and deliver you a return on your SIEM investment in weeks, not months.