As security leaders struggle to combat an evolving threat landscape and a severe talent shortage, a growing majority are taking a fresh look at their services options. Security services made up 45% of all security spending worldwide in 2016, and nearly 60% of organizations plan on increasing their use of IT security services.
Clearly, “managed” is no longer a dirty word. However, some security leaders remain resistant in spite of the great need. Some have had bad experiences with MSSPs and are apprehensive about considering any kind of outsourced security offering. Others don’t want to outsource 100% of the control over their security functions and automatically assume managed solutions are “not a good fit.” Unfortunately, these organizations close the door on meaningful outside help based on some mistaken assumptions about the security services market.
Moving Beyond MSSP
The days of a “one-size-fits-all” outsourcing model are gone. A variety of specialized security services have emerged which address past MSSP shortcomings and provide highly focused expertise. To move the needle on risk, many organizations are looking externally for help managing security on multiple fronts to fill gaps in:
Here are some of the top reasons outsourcing security is becoming an increasingly common solution:
1: Outsourcing security can help combat the internal resource struggle.
If there’s a single word that can best describe the working conditions in cybersecurity today, it would undoubtedly be “overwhelmed.” Information security practitioners struggle to keep up with an incredible volume of sophisticated attacks against a wide range of systems. Even when armed with advanced security tools, these professionals drown in so many alerts, unpatched vulnerabilities, and insecurely configured systems that they can rarely make incremental improvements to their overall risk posture.
Most security executives are aware of these challenges and are on the lookout for ways to make across-the-board improvements. However, they must counterbalance improvements with bottom-line realities like budget. Bringing in cutting-edge technology is expensive enough, but it’s the cost of an experienced security team that can really put a dent in the bottom line. No matter how automated the technology gets, an organization will ultimately need talented analysts, incident responders, and security engineers to get the most out of their security infrastructure. These people are in short supply and high demand. It’s a classic set-up for a service-based use case.
Get more insights from Ben Johnson, Carbon Black co-founder: I Can’t Fill My Security Head Count. What Can I Do?
2: New security services break the MSSP mold.
The generalist service model offered by MSSPs left the market wanting more. Because MSSPs either wouldn’t or couldn’t accommodate customers with new, highly sophisticated product offerings meant to take on very specific risks, there’s been a shift towards specialization. Many organizations need to backfill specific weaknesses in technology, manpower, or expertise without blowing up their internal security program, and the typical MSSP has been unable to help them.
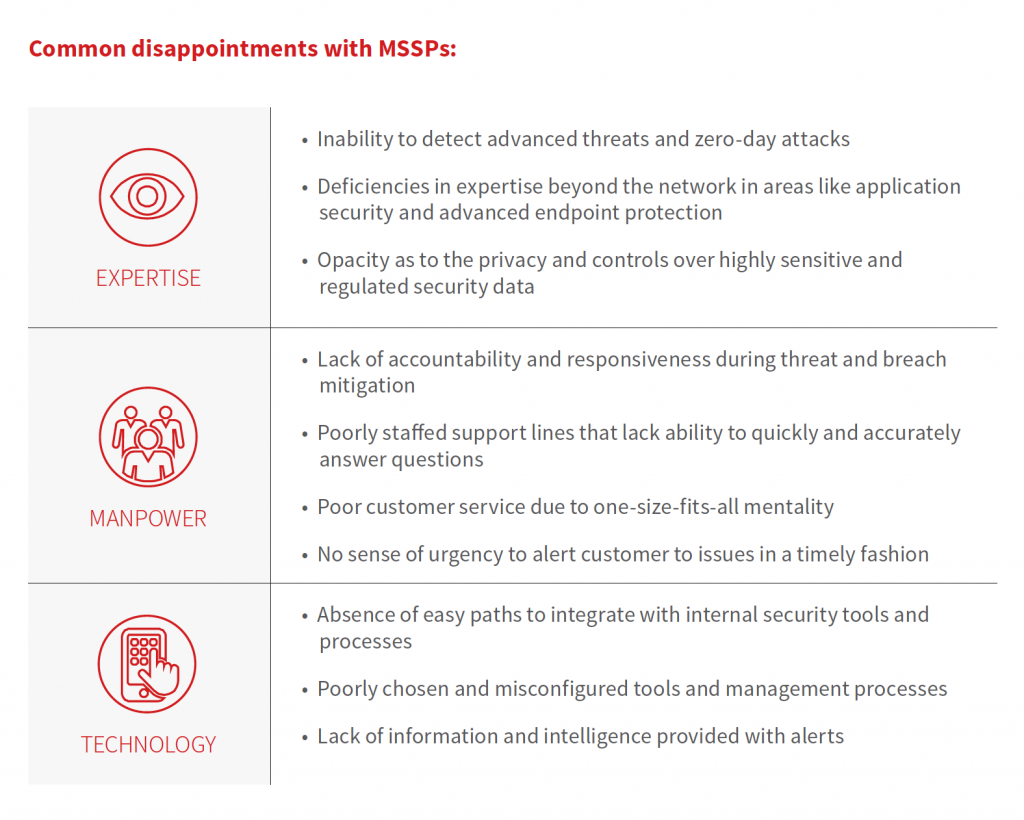
Take a closer look at the fastest growing specialty services by downloading a guide to specialized services.
3: Outsourcing security is now highly flexible.
The idea of completely outsourced managed security is a non-starter for many organizations. Most have risk concerns that make it imperative to maintain in-house control over certain portions of the security function. The market has clearly moved to address this reality, and rather than a “build vs. buy” debate, CISOs and security decision-makers can now consider a portfolio-based approach to security services. Once they move beyond the fully outsourced mentality, it becomes clear that there are a lot of different ways an organization can pull together services to minimize risk.
For organizations with strong in-house security programs and a mature technology stack, choosing a few selected services can help augment existing security staff with targeted expertise in emerging technologies. Similarly, departments with underutilized existing technology can choose co-managed services to bolster their manpower without taking on a heavy investment in recruiting and salaries for in-house teams. Meanwhile, under staffed and lower maturity organizations can often utilize specialty services as a replacement for dedicated headcount.
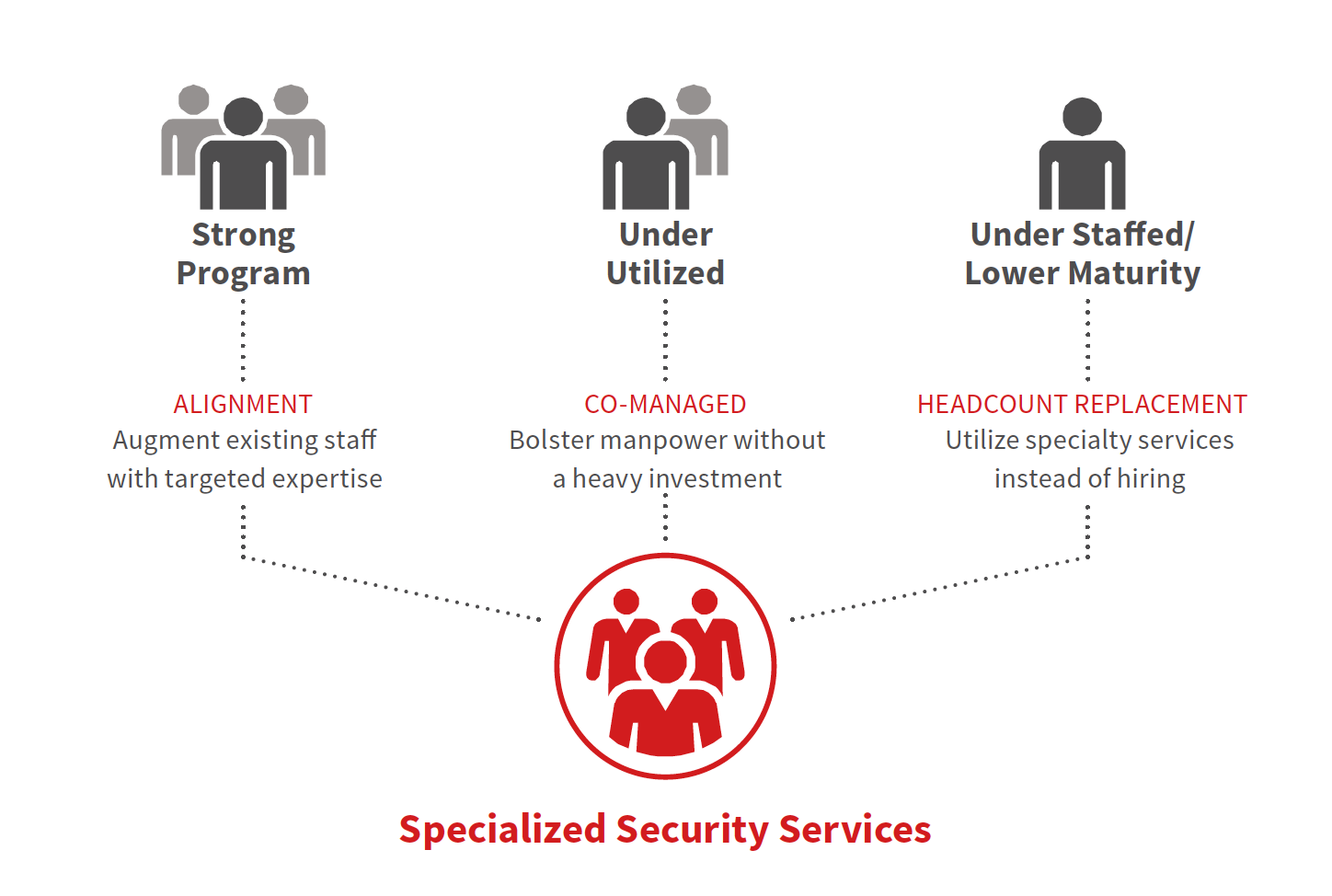
Next steps in building a security services portfolio
Developing a balanced portfolio of services that complements in-house capabilities is an effective way for many organizations to improve their security operations. At the same time, the variety of services now available can also put potential buyers into analysis paralysis. The market can be confusing, and ambitious marketing from certain providers can further muddy the waters. Buyers should come to the table understanding the models used to deliver services, the type of specialties that different market niches cater to, and how that aligns with their internal strengths and weaknesses.
