Red Canary is excited to announce an expanded integration with Microsoft Sentinel. Our security experts will now triage and investigate Sentinel incidents–groups of related Sentinel alerts generated from built-in Sentinel analytics–and will pivot into our customers’ Sentinel environments to run additional queries as an investigation dictates. Our combination of security technology and human expertise will deliver detection and response results from Sentinel for our customers.
Why we built this
Security information and event management (SIEM) products are integral to many security programs. Despite widespread adoption, however, organizations struggle to harness SIEM tools for threat detection and response. Too many false positives, not enough in-house product expertise, and ambiguity around responding to identified threats are just a few of the common reasons that putting SIEM at the center of a threat detection and response program often comes up short.
At Red Canary we have the security expertise and technology platform to deliver the detection and response outcomes you’re seeking from your SIEM.
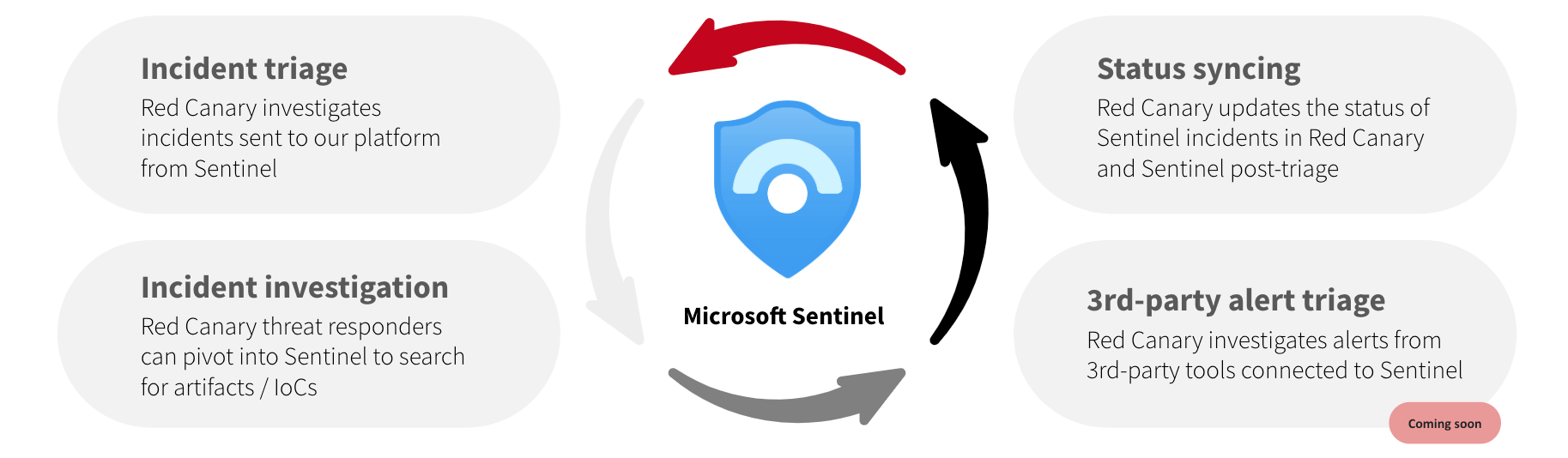
Four new capabilities underlie our expanded integration, all of which save our customers time and move their teams toward more effective security operations:
- Incident triage
Red Canary’s Cyber Incident Response Team (CIRT) will review all incidents sent to Red Canary from Sentinel, triage them, and work with you to respond and remediate threats 24×7.
- Incident investigation
When working an incident you need to know what additional evidence to look for and where to look for it. Red Canary technology correlates data from Sentinel with data from Microsoft 365 Defender, Defender for Cloud, and data from your non-Microsoft security tools, making it easy for our experts to consider relevant data and investigate quickly. If our experts have questions that require more specific log analysis, they can now pivot into your Sentinel environment to answer those questions with additional read-only investigative queries. Either way, all events relevant to a threat are published in an easy-to-understand way in your Red Canary threat timeline. - Incident status syncing
Whether you use Sentinel or Red Canary for alert triage, both should reflect the most up-to-date status of those alerts. To this end, when Red Canary triages a Sentinel-generated incident, we will now update the status of each Incident in both Red Canary and Sentinel based on Red Canary’s threat designation. Additionally, when Red Canary detects a threat from a non-Sentinel source, a corresponding Incident will be created in Sentinel that contains all the relevant information to the threat per Red Canary’s analysis. - Coming soon: 3rd-party alert triage
Many organizations want to send all of their security product alerts to Sentinel for triaging, regardless of whether those products are Microsoft ones. In the near future Red Canary will ingest all of those third-party alerts into the Red Canary platform for enrichment, correlation, and triage, and create a new Incident in Sentinel when our CIRT determines that an alert reflects a threat.
Business benefits
These features will result in several operational improvements for our customers, including:
- Faster time to value for Sentinel
Red Canary MDR already delivers excellent security outcomes–look no further than our Leader position in The Forrester Wave™: Managed Detection And Response, Q2 2023 or the MITRE Engenuity ATT&CK Evaluation for Managed Security Services. With Red Canary, Sentinel becomes more fuel for an already hyper-efficient security operations program working on your behalf, not an organizational bottleneck that requires extensive training and troubleshooting for in-house personnel. In short, we put Sentinel to work for you from the moment you connect it to Red Canary. - Time and cost savings
The time we spend triaging and investigating your Sentinel Incidents is time your team can spend doing more forward-looking, business-specific security work. The additional data from Sentinel is context that we’ll use to detect threats earlier and more quickly understand the full scope of an attack. Our ability to quickly consider Sentinel data in the context of all other security-relevant data you send us results in faster investigations, and when using our SOAR and Active Remediation capabilities, faster response and threat remediation as well. - More ROI from Microsoft licensing
E5 and other bundled Microsoft licenses are gaining traction and helping organizations find both budget and incentives to move to Microsoft Sentinel. Red Canary MDR + Microsoft Sentinel allows you to get the most value from Sentinel. And because we integrate with Microsoft 365 Defender, Defender for Cloud, and other Microsoft products, we provide assurance that all the workloads you have access to and pay for are contributing to an improved security posture for your organization.
To learn more about Red Canary MDR for Microsoft, check out our Microsoft solution page. To see Red Canary in action, sign up for a Microsoft-specific demo.