Until recently, organizations that have lacked the resources to build an internal detection and response capability have had few options. They could either (a) purchase an advanced product without properly staffing it; (b) attempt to hire; or (c) use the traditional outsourcing option of a Managed Security Service Provider (MSSP).
Last year, Gartner identified Managed Detection and Response (MDR) as a new, rapidly growing service category. MDR services emerged to fill a gap left by the traditional MSSP model. While MSSPs support many different parts of a security program, detecting and responding to advanced threats is not where they specialize. Meanwhile, MDR services deliver specific expertise to support organizations seeking to improve their threat detection and incident response capabilities.
8 Common Questions & Answers: MSSP vs MDR
Key Differences Between MSSP and MDR
If you are considering outsourcing detection and response, make sure you understand the key differences between an MSSP and MDR. To help you make an educated decision, we’ve compiled an at-a-glance comparison, a deeper dive into several key differences, and red flags to watch out for. We also encourage you to download our full guide for 8 common questions and answers on MSSP vs MDR.
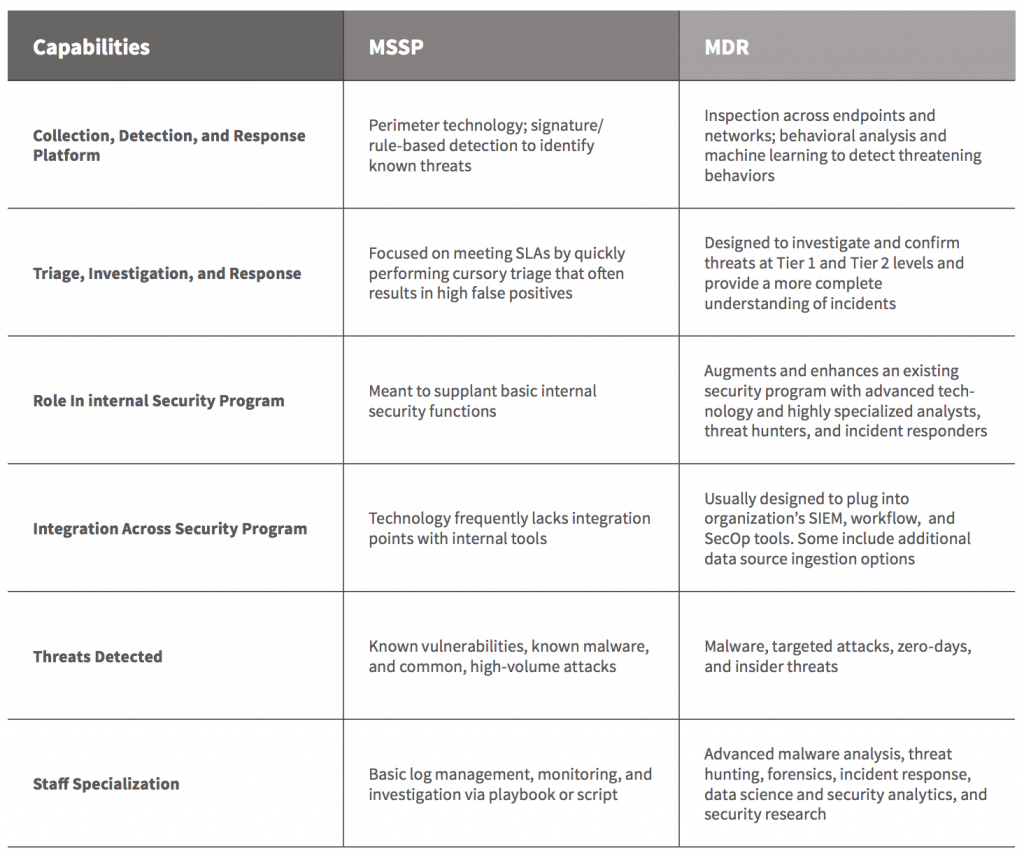
MSSP vs MDR: At-a-Glance Comparison
Here’s a deeper dive into several key differences:
1: High-level security coverage vs focused expertise
MSSPs typically focus on basic security tasks like monitoring standard ingress-egress traffic on perimeter products and vulnerability management. They are meant to provide high-level security coverage for basic and repetitive tasks across an organization’s entire security stack. It is not uncommon to find an MSSP advertising that they use hundreds of security tools. A detailed look will often show that they employ inexperienced staffers trained to capably operate only a small fraction of those.
Meanwhile, MDR augments and enhances an existing security program with advanced technology and highly specialized practitioners. Their staff delivers focused expertise in advanced malware analysis, threat hunting, forensics, incident response, data science, security analytics, and security research.
Read why Gartner thinks MDR may pose a threat to MSSPs
TIP: To identify an MSSP overselling its services, ask specifically about the staff’s experience in the following areas:
2: Signatures and rule-based detection vs advanced detection technologies
MSSPs mostly rely on signatures and rule-based detection and frequently miss advanced threats (and increasingly even basic attack tactics). Conversely, MDR services focus specifically on improving an organization’s advanced threat detection and response efforts. MDR services are used to augment and enhance internal capabilities. They frequently examine similar data sets as MSSPs such as network logs or endpoint telemetry, but at a much greater depth.
MDR services are specifically tailored to use advanced technologies such as Endpoint Detection and Response (EDR), behavioral analytics, specialized forensics tools, and custom security event management platforms. The most sophisticated MDR providers focus heavily on detecting behaviors like lateral movement, credential theft and escalation, and C2 activity, all behaviors of today’s advanced attacks. Some even operate large software and security engineering teams to design their own detection and response technology to keep pace with attackers.
3: Incident Response (or lack thereof)
When incidents are discovered, many MSSP customers are still responsible for managing containment and mitigation unless they pay the provider’s Incident Response team extra for help. Even then, the MSSP’s staff may not be specifically trained to effectively respond to an incident. MDR, on the other hand, is designed to investigate and confirm threats and provide a more complete understanding of incidents.
Can MSSPs Provide MDR Services?
In theory: yes, MSSPs could provide MDR services. But the majority of MSSPs are not offering true MDR capabilities at this time—even when they advertise that they do. The current business model used by traditional MSSPs cannot support a specialty service like MDR.
MSSP infrastructure is typically designed around signature-based detection and perimeter defense. And generally MSSPs employ Tier 1 SOC analysts who are there to monitor rather than investigate. To add MDR services, most MSSPs would need to completely retrofit their SOC architecture and hire veteran security engineers with experience in threat hunting, malware analysis, incident response, and data science. Complicating the matter, the most mature MDR providers are technology companies that run full software development, PM, QA, and DevOps teams.
These changes require a massive investment and culture shift that most MSSPs cannot make. In fact, these service providers’ inability to deliver MDR services is partially what drove the rise of MDR in the first place.
Red Flags That an MSSP May Not Be Able to Provide True MDR
As the MDR market grows, buyers must be careful when considering a detection and response solution from an MSSP. Many MSSPs may try to dress up existing offerings without making the necessary investments.
It’s important to ask the right questions and request technical substantiation in order to identify if an MSSP is overselling its detection and response offering. Your questions should help you gain an understanding of the provider’s team, technology, philosophy about detection and response, and standard operating procedures. Below is a list to help during your evaluation.
For a printable checklist, download the full MDR vs MSSP Guide
16 Questions to Ask MSSPs (NOTE: These are also great questions to ask MDR providers!)
- What is your team’s expertise across the following disciplines: security research, advanced detection methodologies, threat hunting, security analysis, incident response, forensics, security operations, security engineering, data science, and IT operations?
TIP: To really do due diligence, ask to interview specific individuals on the security team. Learn about what they do every day and their areas of expertise. - How do you ensure you always have enough analysts and incident responders in your SOC? How do you maintain a pipeline of recruits?
- What is your process for detection, investigation, and response?
- What technologies are core to your MDR offering? How do you train your SOC to ensure proficiency?
- Can you automatically orchestrate data and suppress events to limit investigation of false positives?
- Are you able to provide metrics showing continuous improvements in analysis time?
- Can you detect XYZ activity?
For each scenario: Ask which artifacts will be collected to enable detection and what aspects of the attack will be detected. - What is the false positive rate on some of your detectors? Not the false positive rate customers report, rather the false positive rate the provider’s internal SOC reports from its own detection technology. (The key here is that internal false positives are okay. You want your MDR provider examining a lot of different activity, even if it doesn’t convert to a threat.)
- What are three new types of threatening behavior you can now identify due to improvements you’ve made in the last 3 months? (The key here is you don’t want the MSSP driving their detection with threat intelligence and you want a provider who is continually improving their detection.)
- What types of threats are you unable to detect?
- What is your customer reported false positive rate? False negative rate?
- What is your average time to detection? Response?
- Have you ever had a customer get breached? Walk through through how that event happened and what your response was. Can a conversation with that customer be arranged?
- Who do customers typically interact with when they have questions on detections, response best practices, implementation of the MDR service, etc.?
- Explain your detection and response roadmap. What new techniques and technologies will you incorporate into your offering?
- How do customers hold you accountable? (You do not want an MDR provider focused on traditional SLAs. They should be focused on breadth and timeliness of detection and response)
MSSP vs MDR: You Decide
As security teams evaluate what partners will make the biggest positive impact on their security program, it’s important to understand these differences. Many organizations that have had bad experiences with MSSPs in the past will find that MDR can help them fill gaps within their internal capabilities. Not all security services are created equal. In fact, Red Canary was created to be different.
Have questions? Contact us to talk about your security objectives and how we might partner together to make your security better.