At Red Canary, we believe that a cohesive ecosystem of integrations and tech partnerships is key to providing comprehensive protection. By leveraging our ever-growing list of integrations, organizations can:
- Improve their security posture by adding 24×7 detection across IT domains
- Accelerate incident resolution through automated communication and containment
- Reduce alert fatigue and gain visibility across disparate tools
In this blog post, we’ll explore some of Red Canary’s recent releases that enhance our integration ecosystem. By expanding our partnerships and capabilities, we’re empowering our customers to better defend their organizations against cyber threats.
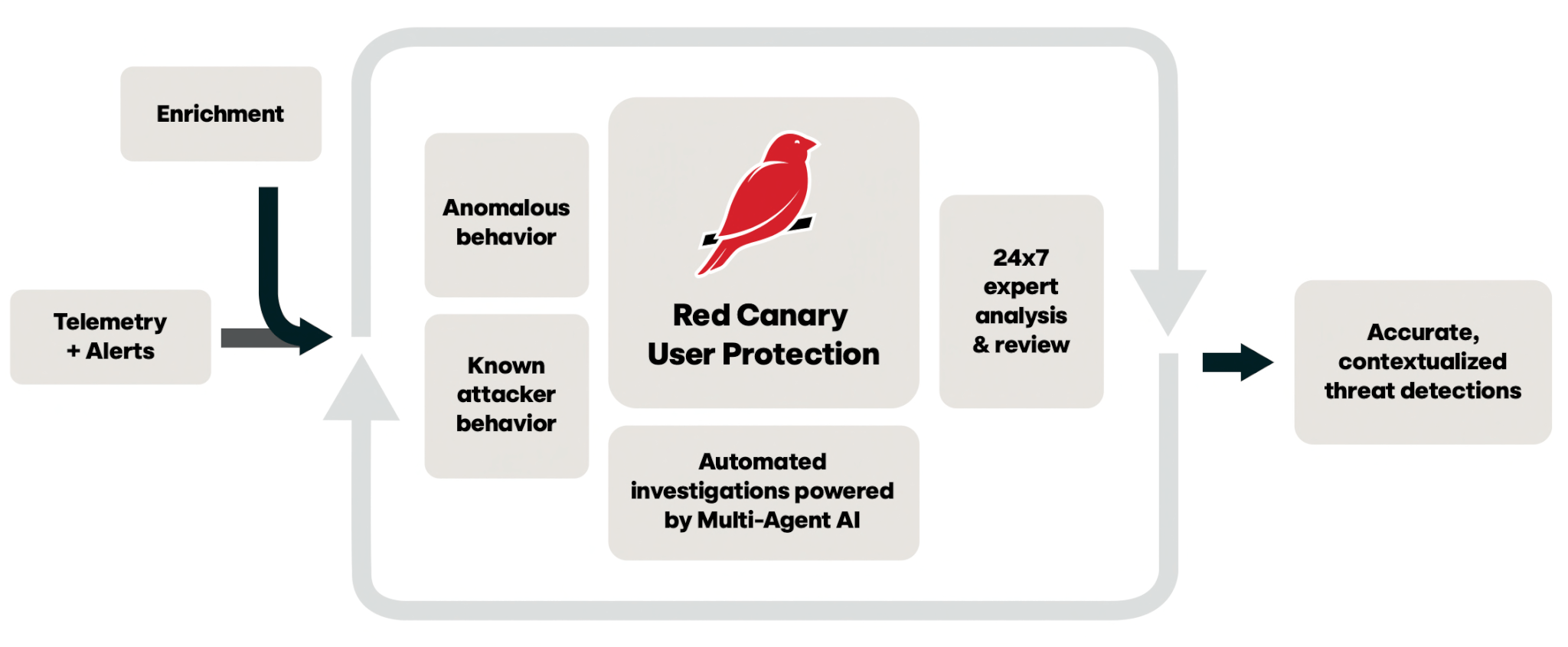
Better secure your identities
Compromised identities are a prime target for adversaries, granting unauthorized access to sensitive systems and data. Unlike endpoint threats, identity-based threats are harder to detect and move much more rapidly, as adversaries can leverage compromised credentials to quietly escalate privileges or access sensitive data across multiple systems and applications. To stay ahead, organizations need a new approach to identity security.
Red Canary’s integrations with leading identity protection solutions provide continuous monitoring and early detection, ensuring that your identities and sensitive data stay secure. With enhanced support for platforms like CrowdStrike Falcon® Identity Protection, Microsoft Entra ID, and Okta Workforce Identity Cloud, we ensure timely detection of identity threats and fast response, keeping your business-critical data secure.
MDR for CrowdStrike Falcon Identity Protection
Red Canary extends the value of Falcon Identity Protection with 24×7 monitoring and advanced analytics to detect anomalies and real-time threats. Our integration gathers and analyzes events like login attempts and group changes.
Key benefits:
- Early detection of unauthorized login attempts, password changes, and other suspicious activity
- Improved visibility into domain controller activity and user behavior
- Reduced burden on your security team with 24×7 monitoring and response by security experts
MDR for Microsoft Entra ID
Red Canary’s integration with Microsoft Entra ID has been significantly enhanced to deliver even more granular and timely insights. With near real-time access to Entra ID sign-in, audit, and user event logs, Red Canary can rapidly detect and investigate suspicious activity in your Microsoft ecosystem.
Key benefits:
- Real-time monitoring for anomalies and suspicious behavior such as MFA exhaustion and legacy authentication attacks like brute forcing
- Enhanced threat timelines and contextualized alerts, enabling faster, more effective incident response
- Automated playbooks to respond automatically to compromised credentials in your Entra ID environment
MDR for Okta Workforce Identity Cloud
Red Canary’s expanded integration with Okta Workforce Identity empowers organizations to proactively detect and respond to advanced identity threats. By ingesting a wider range of telemetry, we can identify threats such as MFA fatigue, unauthorized proxy access, policy-driven app access denials, and malicious MFA resets. Additionally, we can detect anomalous behaviors such as high-risk logins from unusual devices, IP addresses, or proxies, and uncover suspicious admin actions like MFA disabling and admin console access attempts.
Key benefits:
- New detectors identify a wider range of identity threats like unauthorized proxy access, malicious admin actions, and suspicious TOR logins
- Enhanced visibility into your Okta environment and correlation with other security tools streamline investigations, enabling faster detection and resolution of incidents
Protect your endpoints
Adversaries are constantly evolving their tactics to bypass traditional defenses and compromise sensitive corporate data. Red Canary’s integrations with leading endpoint protection solutions ensure advanced threats are detected and stopped before they impact your business.
MDR for Trend Micro Vision One™
Our new integration with Trend Micro Vision One empowers us to proactively identify and respond to advanced threats 24/7, safeguarding your endpoints from malicious executables like ransomware and malware.
Key benefits:
- Real-time visibility into your endpoint environment to proactively identify and mitigate threats
- Accelerated incident response and minimized business disruption with automated workflows and expert guidance
- Advanced threat detection and response against a wide range of threats to strengthen your endpoint security posture
Take the stress out of SIEM and SIEM alternative management
Today’s SOCs are often built on siloed tools and data. At the same time, they’re inundated with an overwhelming number of threats, resulting in the inability to keep pace, remediate incidents quickly, and stop threats at scale. Red Canary is proud to announce expanded SIEM and SIEM alternative offerings, designed to help organizations break down silos and boost efficiency.
Co-managed Microsoft Sentinel Subscription
Building on the success of our Microsoft Sentinel Security Jumpstart, we now offer a yearly subscription for ongoing support and optimization. Our Co-managed Microsoft Sentinel Subscription extends support beyond initial deployment, ensuring your Sentinel environment remains optimized, secure, and delivers maximum value year-round.
Whether deployed independently or through our Security Jumpstart engagement, this subscription provides proactive health checks, analytics, and support, enabling your team to prioritize business-critical objectives over routine maintenance.
“Our Microsoft Sentinel instance was deployed in partnership with Red Canary, taking our needs and objectives into account while leveraging their Microsoft expertise. We’re now able to identify threats in Sentinel that we couldn’t with our previous SOC and SIEM. We now have a much clearer understanding of our ruleset and can easily export logs for expert forensic analysis if the need arises. Working with Red Canary has been a tremendously positive experience.”
DIRECTOR OF IT
LEADING PRIVATE EQUITY FIRM
Your ecosystem, our expertise
By integrating seamlessly with the security tools you already trust, Red Canary empowers you to effectively detect and respond to cyber threats. Our commitment to innovation and strategic partnerships ensures you have the data and expertise needed to secure your organization now and in the future.