Stolen credentials were the most common path to a breach in 2021, according to the Verizon Data Breach Investigations Report. Requiring multi-factor authentication (MFA) during login significantly decreases the risk that stolen credentials will result in a breach. However, adversaries can still circumvent MFA—both in sophisticated ways as Microsoft observed recently, or by just overwhelming the user with push notifications, as detailed by Recorded Future.
To help you detect and respond to credential compromises before they result in a breach, Red Canary is excited to reveal an expanded integration with Okta Workforce Identity.
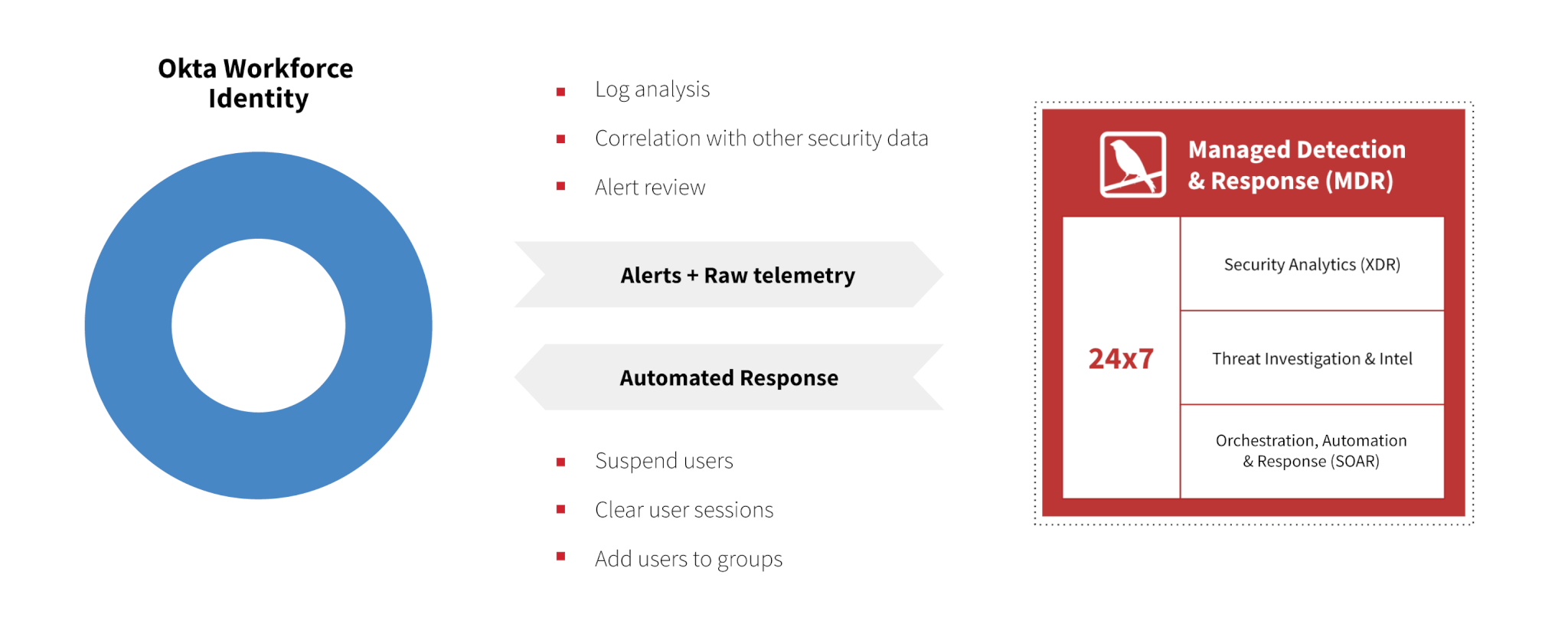
Detecting credential compromise using Okta Workforce Identity
Red Canary detects credential compromise using Okta Workforce Identity in multiple ways. First, we’ll correlate information from your Workforce Identity alerts with relevant data from your other security tools. Maybe we detect that the identity that just initiated a password reset also recently clicked a phishing email. Or maybe one of your Okta admins escalates privileges to an identity that recently tried to access banned applications per your firewall. Because our XDR platform correlates information from across your enterprise, our detection engineers can review events with the proper context to quickly determine what alerts are benign or could indicate a threat.
We know the limitations of out-of-the-box alerts, which is why we now write our own detections specifically applied to Okta logs. We’ve already written detections to detect MFA fatigue intrusion attempts, and we will continue writing Okta-specific detections to catch threats that Workforce Identity alone would miss.
Responding to credential compromise using Okta Workforce Identity
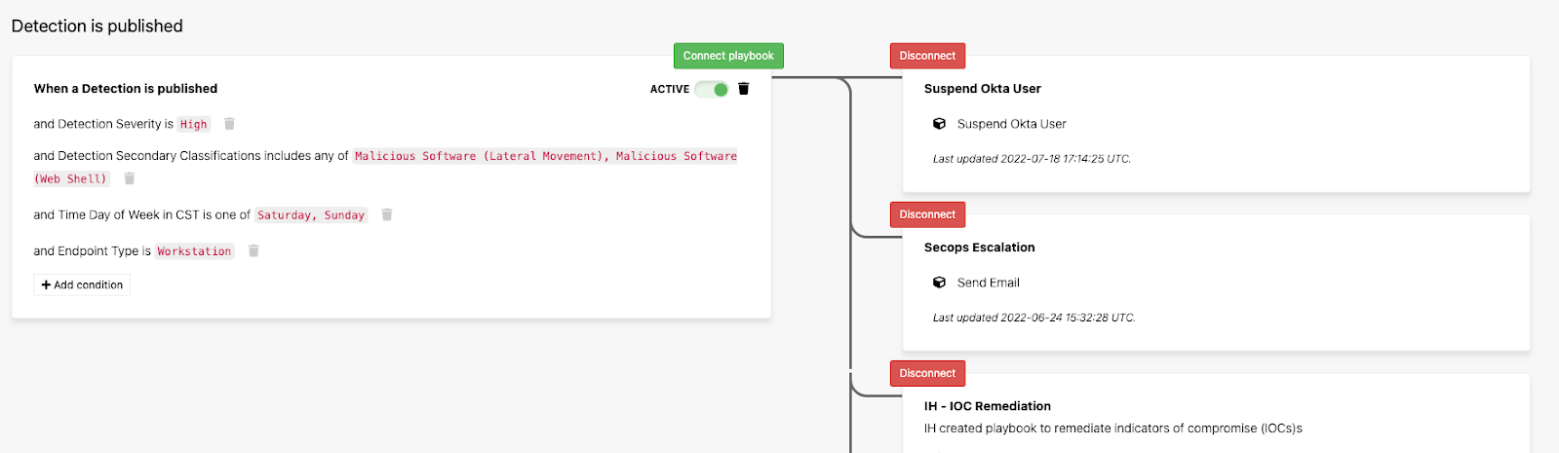
When we determine that a user’s credentials are stolen our built-in SOAR platform allows you to easily configure automated responses in Okta. No coding is needed: you can set up the responses entirely with Boolean logic and visual playbooks. We enable you to configure automated responses in Okta Workforce Identity for any Red Canary detection in which an Okta identity is implicated, not just detections we confirm via Workforce Identity alerts or logs. For example, you could set up a playbook such that anytime Red Canary detects malicious software on a device, the associated Okta user is suspended and added to an Okta group with access restrictions. It’s also easy to set up a playbook that clears a user’s sessions, forcing them to authenticate on their next operation anytime Red Canary associates an Okta user with a threat of any severity level.
Red Canary MDR ensures that you’re staying ahead of credential abuse in your environment by detecting account takeover threats early and helping you respond automatically in Okta. To learn more about Red Canary and how we work with Okta and other identity technology providers, feel free to schedule a demo or talk to one of our experts.