EDITOR’S NOTE: This product was originally known as “Exec.” We have since renamed it “Red Canary Automate.” Where appropriate, references to the former product name have been updated accordingly.
Threats can occur at any time of the day. They don’t care if you’re sleeping, if it’s the weekend, if you’re on vacation, or if you’re short-staffed. For many security teams, it’s a struggle to meet the time sensitivity requirements of containing and remediating threats. What happens when a threat hits your network at 3 a.m.? How do you enforce consistent, dependable response workflows even when you’re away?
That was the case for Tony, an IT security analyst at a world-leading manufacturer. “We’re a small team, and worrying about something happening overnight has always been a bit of a concern. While Red Canary’s continuous monitoring gave us visibility and awareness when threats were detected, we haven’t really had an automation system in place to act upon that awareness around the clock.”
That’s why Red Canary is excited to introduce Automate.
Automate empowers security teams to define and automate threat remediation processes in a safe, easy, and meaningful way.
“Exec bridges the gap if you don’t have a 24-hour on-site SOC,” Tony explained. “If I have to leave for a vacation or a month of training, I’m not leaving behind a vacuum of capability. Exec can augment my absence so we can run a consistent set of actions.”
Creating Custom, Visual Playbooks
Automate enables you to use custom, visual playbooks to automate decision-making and actions like employee notifications and endpoint containment.
“The ease of use of the platform is incredible,” Tony commented. “You can hop in and have triggers and playbooks set up in minutes. The speed to execution is very rapid.”
Common Use Cases
To best demonstrate the value of Automate, let’s run through some common use cases:
- Bump in the night
- Full automation for lower priority threats
- Is anyone looking at this alert yet?
- What about auditing?
Use Case 1: “Bump in the night”
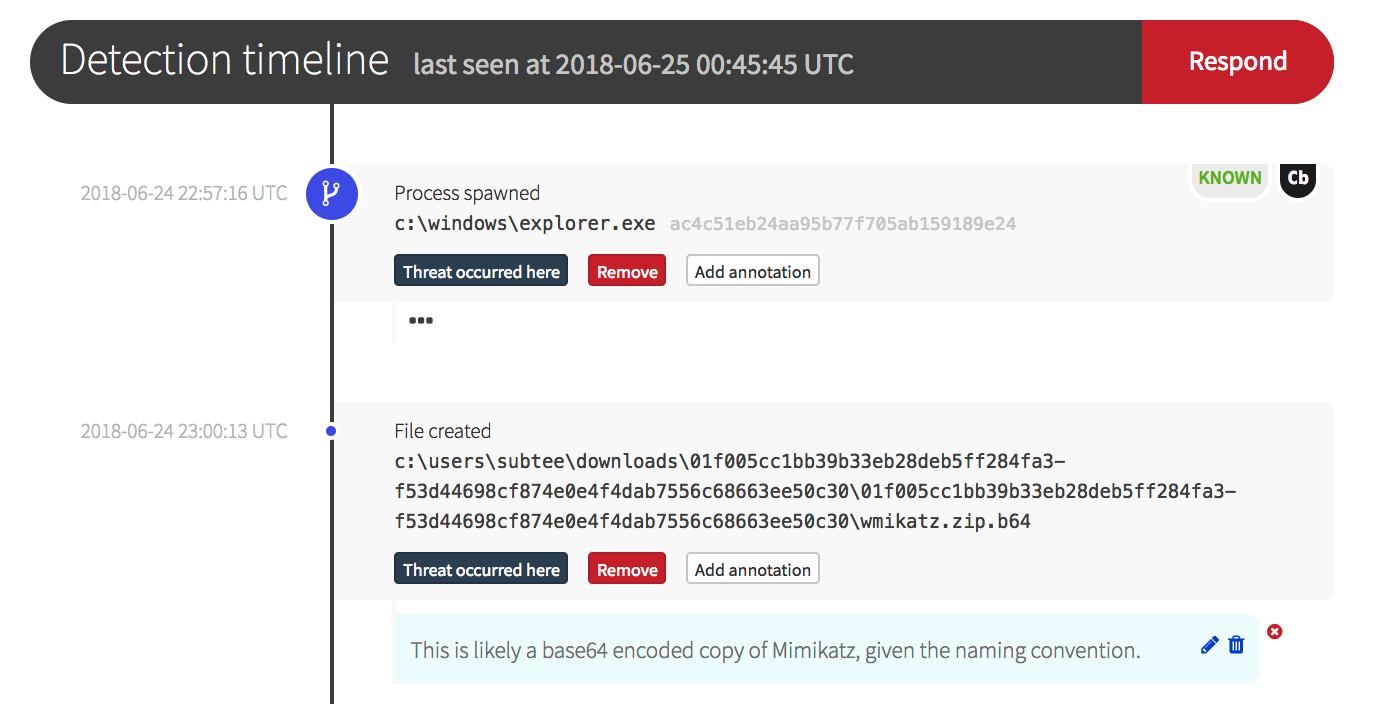
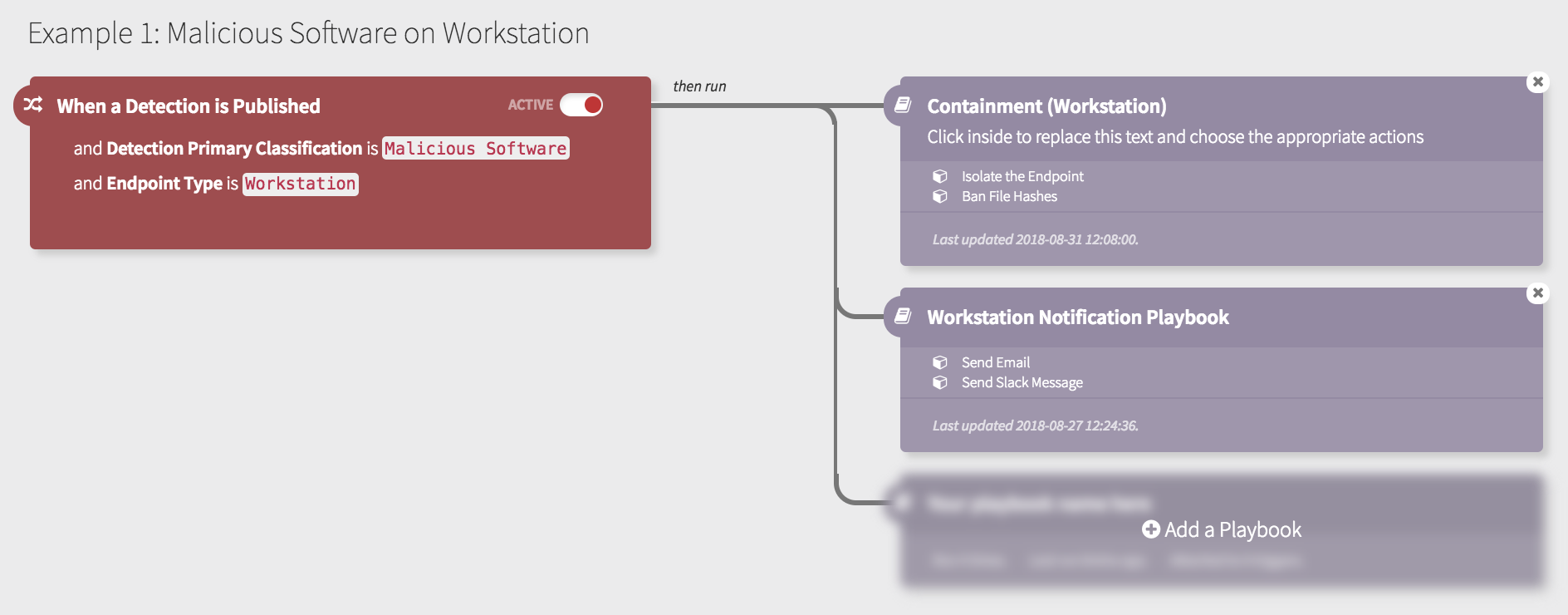
With Automate, you can automate initial containment actions to mitigate much of this risk. For this example, we can define a Trigger to listen for ‘When a Detection is Published’:
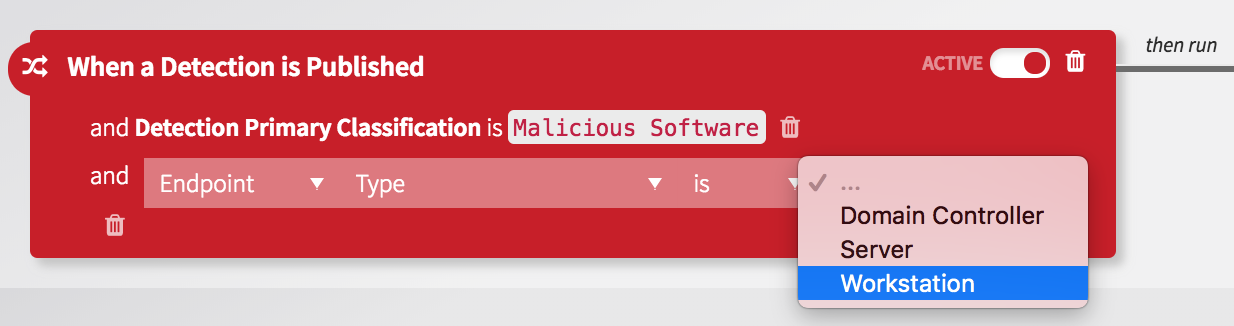
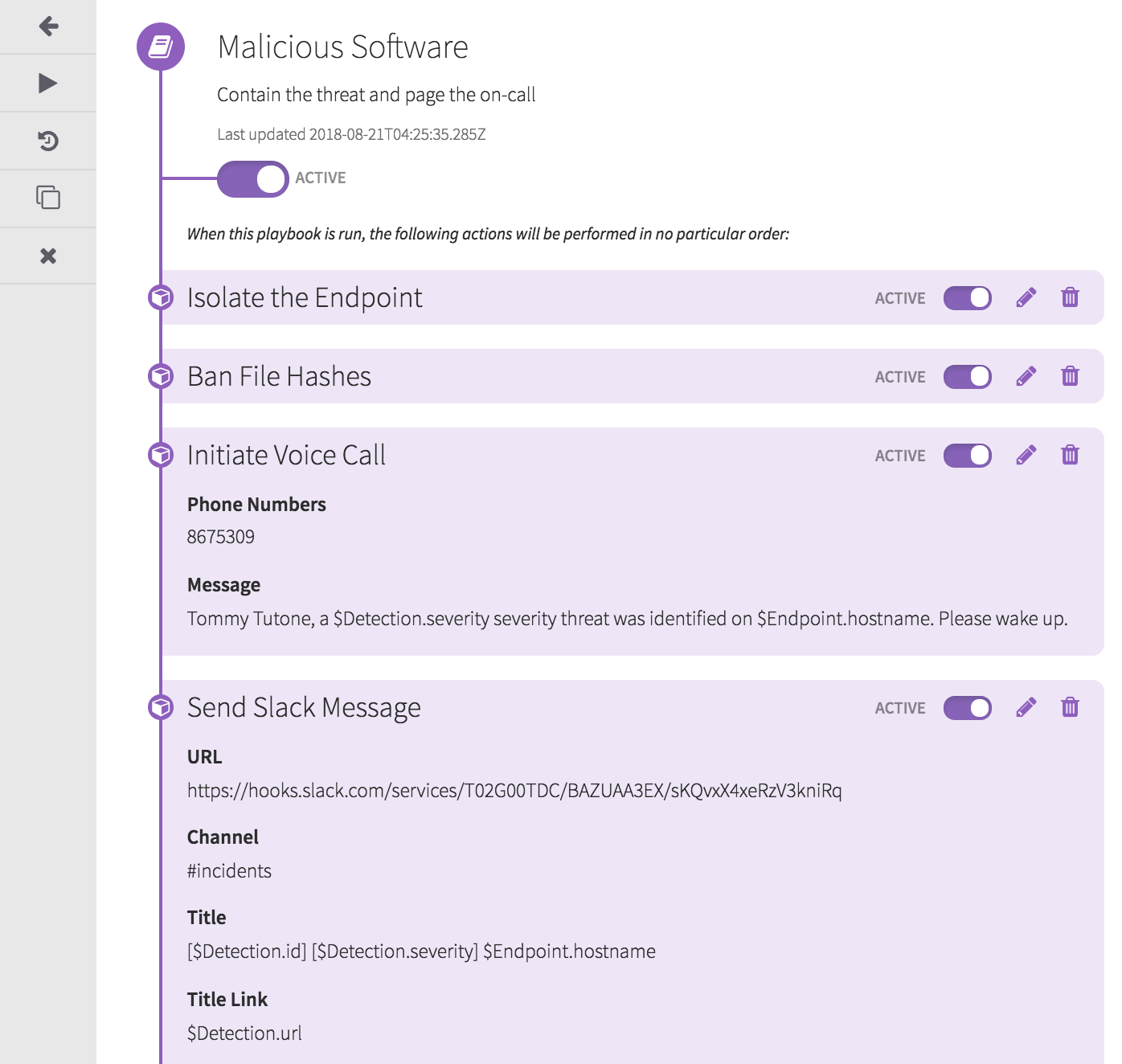
- Containment of the endpoint using network isolation
- Banning of the malicious software and associated file hashes (IOCs)
- Paging an individual via phone call
- Notifying your broader team in Slack
These automated actions ensure the workstation won’t continue to communicate with command-and-control servers and prevent the malicious software from running on other endpoints in the environment. With these important steps taken immediately, we have reduced the likelihood of lateral movement and exfiltration, and you can focus on your remaining incident response procedures.
Whether you are a team of one or ten or more, having the ability to quickly contain threats through automation will save you time, money, and stress.
Use Case 2: “Full auto for low-priority alerts”
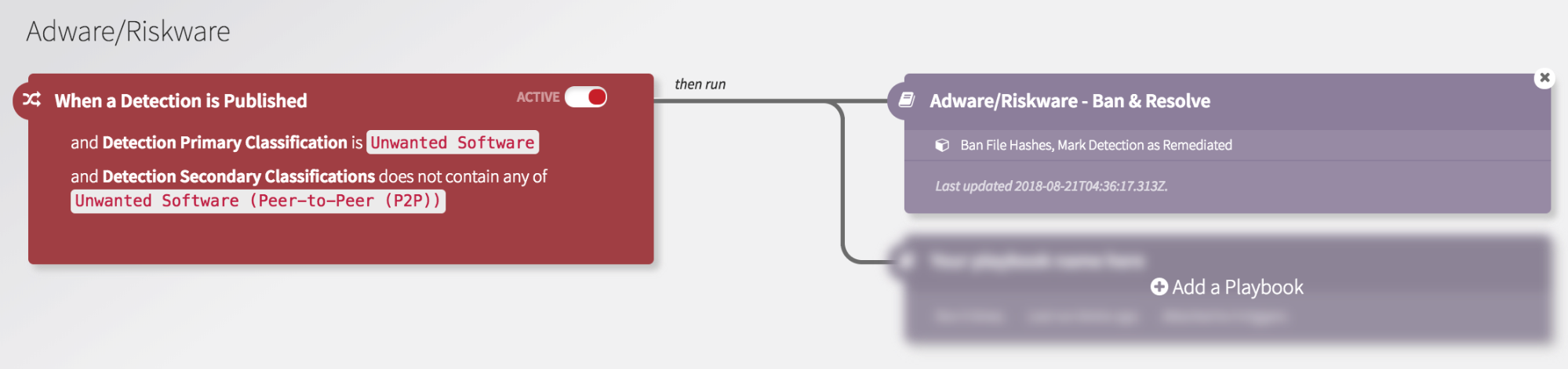
Let’s imagine your team isn’t positioned or empowered to action on adware/PUPs/PUAs. In fact, the business has “accepted the risk” when it comes to P2P software. You wish you could do something to mitigate some of the risk, but with competing priorities and multiple fires, it’s often difficult to do so.
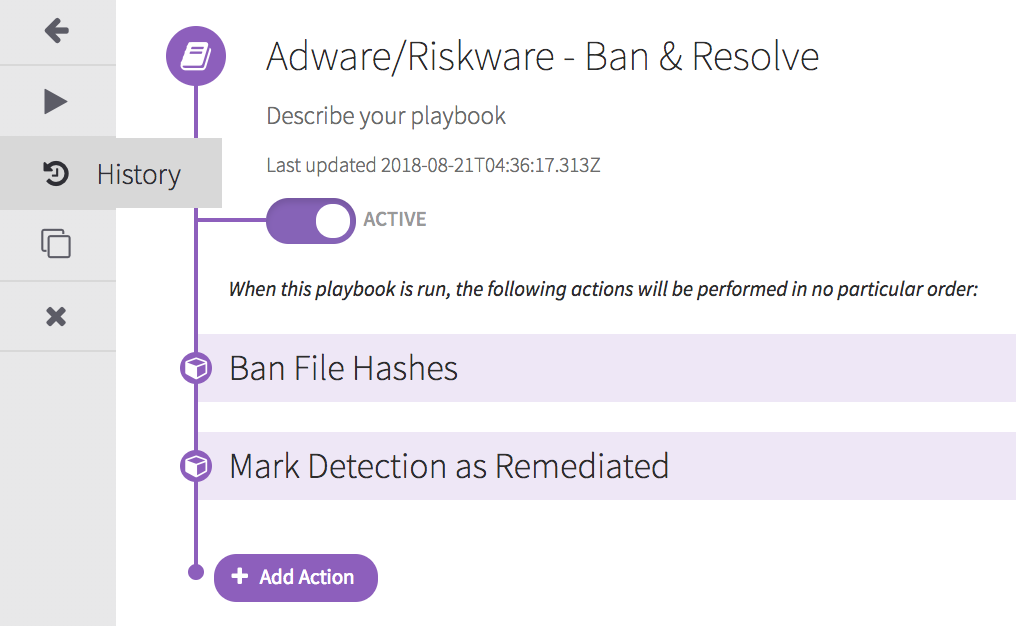
With Automate, you can define a Trigger that looks for Detections classified as Unwanted Software, while excluding P2P. If this criteria is met, the associated playbook runs, which bans the unwanted software from running and marks the detection as remediated:
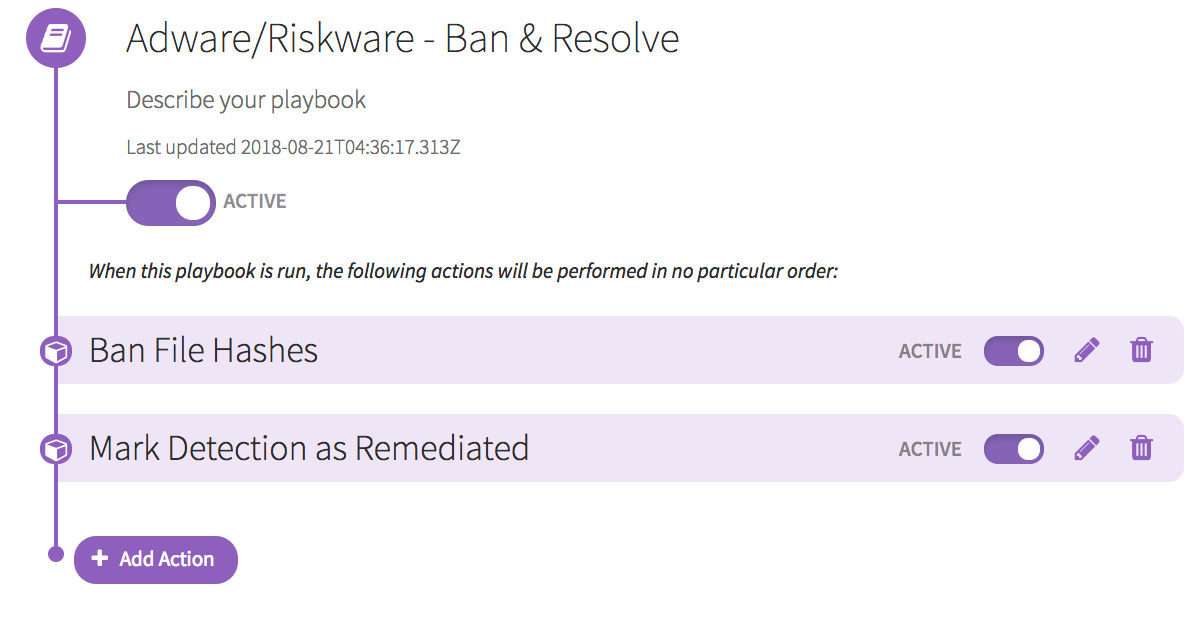
Use Case 3: “Is anyone looking at this alert yet?”
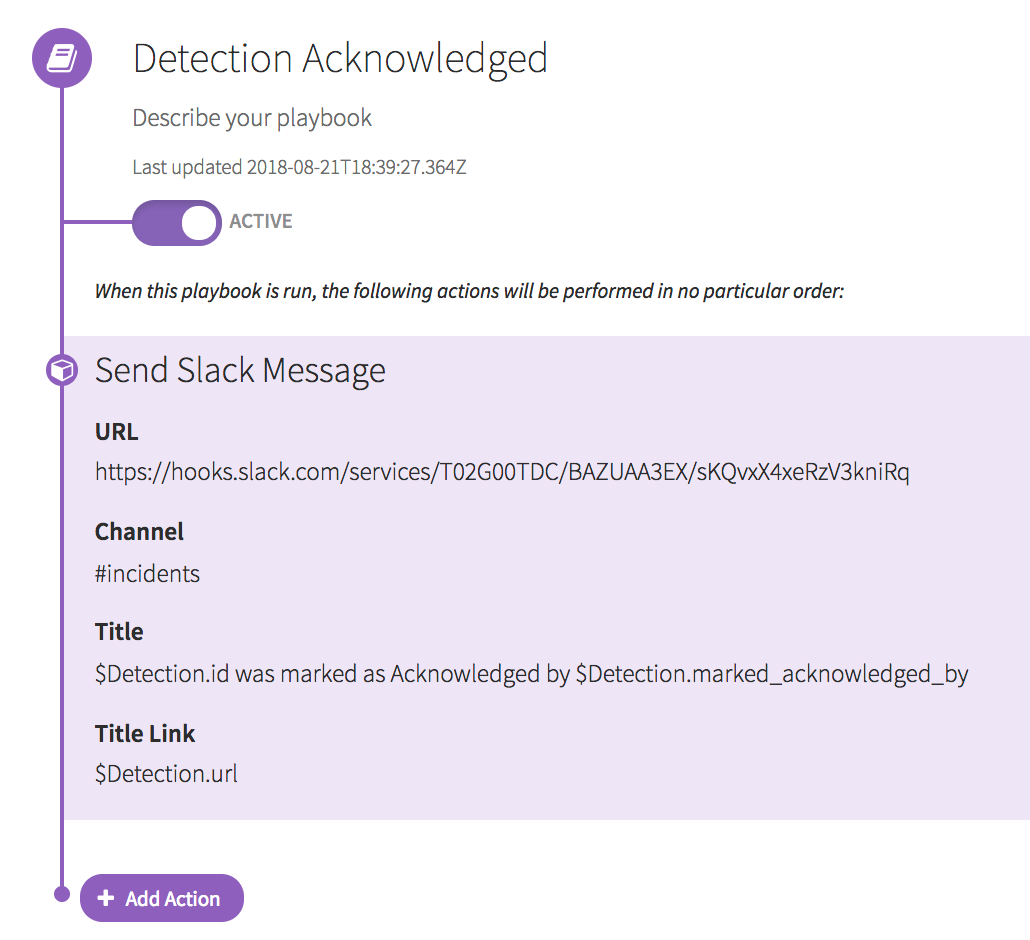
If your team has more than one analyst or incident responder, you likely want a steady stream of updates to your chat channel that covers the entire detection lifecycle—when new detections are identified and when a team member is acknowledging or resolving a threat.
With Automate, you can define triggers for when a detection is published, when a detection is acknowledged, and when a detection is marked as remediated. These triggers then can be associated with a playbook that sends custom messages to a defined Slack channel.
Use Case 4: “What about auditing?”
In this scenario, you want auditing and alerting around access and use of privileged security tools, which is being driven by security, privacy, and compliance requirements.
With Automate, you can define triggers for Red Canary actions like:
- Login events (success/failure)
- User events (invite/add/remove)
- Authentication events (MFA enabled/disabled, token resets…)
- Action events (remote access or commands run, hashes banned…)
You can also view an audit log for all actions performed via Automate, in addition to a change-log that captures all changes made to Automate playbooks.
How It All Works Together
For those who are unfamiliar with the intricacies of the core Red Canary product, here’s how it works:
- Red Canary continuously collects endpoint telemetry, standardizes it, and makes it available to your team.
- We continuously monitor endpoint activity, analyzing application, user, and device behavior to identify threats and anomalies. This is achieved through hundreds of automated detection techniques that are continually updated through research and development, many of which are mapped to MITRE’s ATT&CK™ framework.
- Alerts are reviewed around the clock by the Red Canary Cyber Incident Response Team (CIRT), ensuring customers only receive high quality, actionable, timely threat detections with less than a 0.5% false positive rate.
While this has already delivered a lot of value to our customers, many have asked if we could handle basic remediation responsibilities for detections, in the event of an emergency, unresponsiveness, or just to ensure timeliness due to customer staffing constraints. As a result, we set out to find a way to support timely remediation in a way that’s flexible enough to meet each of our customers’ needs and unique requirements.
The result of this exploration: Automate. By developing an automation framework that customers can easily use, we can ensure that remediation actions properly reason about internal context, business criticality and edge-cases. It provides automation you can trust, as actions are only being performed against high quality, reviewed alerts, and those actions are accounting for business context and internal processes that only you know.
After a few weeks of using Automate, Tony concluded: “This is a hard-hitting, rapid integration automation platform. My biggest advice would be to check out the platform and see how easy it is.”
Getting Started
Already using Red Canary and want to dig right in?
Review documentation on help.redcanary.com to get started.
New to Red Canary and want to learn more?
Schedule a demo to see how Automate fits into our end-to-end solution for threat detection and response.