Everyone knows advanced threats are extremely difficult to defend against. Nothing earth-shattering there. They leverage sophisticated tactics, techniques, and procedures (TTPs) to covertly harvest sensitive data, and are characterized by their ability to avoid detection. Most organizations say they are concerned about advanced attackers, but also question if they would ever be a target. But what about the organizations that have been breached by an advanced attack and know they can expect more targeted attacks? How do they think about securing their organization, employees, and data?
This was the case for a global not-for-profit organization who is currently a Red Canary customer. The organization’s sensitive work around human rights and other issues often runs contrary to foreign government interests, making it a regular target.
This customer profile will take a closer look at:
- The organization’s primary security challenges based on their environment
- Why they selected Red Canary as a key component in their defense strategy
- A real-world attack that Red Canary detected and helped the organization defend against
Read the full case study to learn more about the not-for-profit organization and how Red Canary helps them stop advanced attacks.
Challenge: Stopping Advanced Attacks and a Second Breach
Before becoming a Red Canary customer, the organization was successfully breached by an advanced attacker looking to collect information about the organization’s work. They knew they would be targeted again, and needed to bolster their security to protect against similar attacks. The organization had a lean, security-conscious IT organization who knew they needed additional security capabilities, not just more security products. They had already invested in advanced technologies like application whitelisting but still felt they had exposure.
Key requirements included:
- Continuous collection and storage of endpoint telemetry
- Broad detection coverage that accurately identifies malicious and suspicious behaviors and abnormal endpoint/user activity
- The ability to quickly respond to a compromised endpoint regardless of its global location
- Access to knowledgeable security practitioners who could advise the organization on security best practices and provide insight on highly targeted attacks
Developing a Defense Strategy: Managed Endpoint Detection & Response
The organization began looking for a solution that delivered continuous endpoint monitoring, behavioral analysis, and rapid response. Red Canary Managed Endpoint Detection and Response quickly and accurately identifies threats on customers’ endpoints ranging from compromised credentials to lateral movement to crimeware.
Key reasons the organization selected Red Canary:
- The solution relies primarily on behavioral detection and can detect the behaviors that an attacker exhibits when they compromise an endpoint and move around the organization
- The Red Canary SOC investigates every potential threat, removing false positives and adding context to legitimate threats
- The Red Canary Technical Account Management (TAM) Team serves as an extension of the customer’s security organization, helping them tune and support the solution, answering broad security questions, and providing recommendations on incident response plans
Real-World Threat Detection: Stopping a Spear Phishing Attack
Since deployment, Red Canary has helped to stop a number of attacks that could have resulted in a serious breach. The following screenshots are taken directly from a detection notification sent to the customer when it was hit by a highly targeted spear phishing attack. They highlight how Red Canary identified the attack, investigated it, notified the organization, and helped them stop it before it could do significant damage.
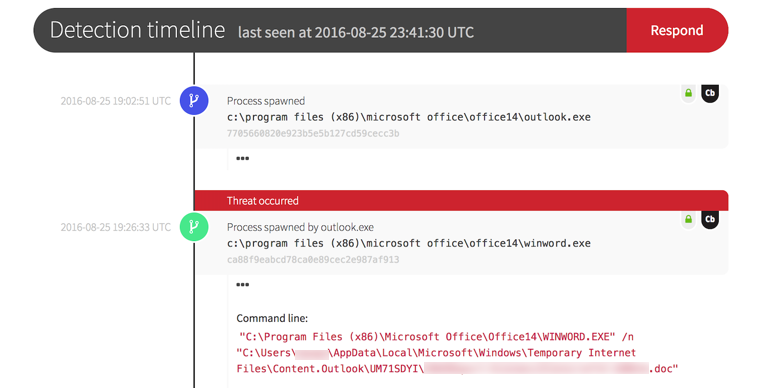
Threat Detection Timeline
It was a Thursday afternoon when an employee at the organization’s office in Asia received an email appearing to come from an individual that they were in the midst of working with. The email was actually a well-disguised spear phishing attack containing a weaponized Word document.
Red Canary detected the following activity:
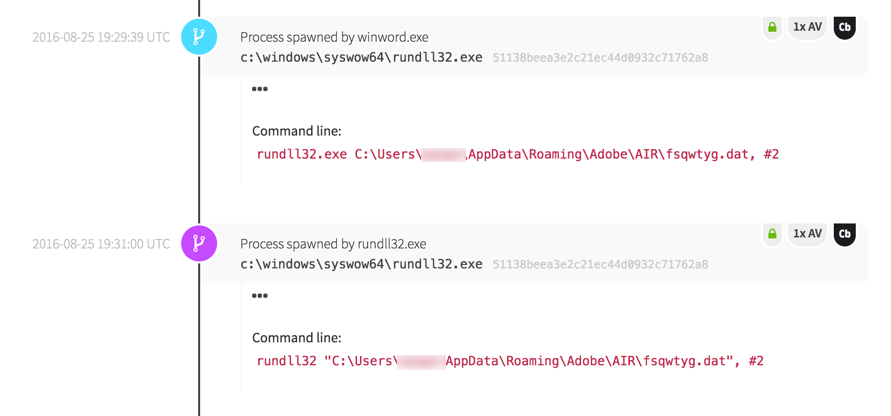
Next, Word executed a binary via rundll32.exe. While Word spawning rundll32 isn’t necessarily evil, it was suspicious because it was loading a dat file from the user’s temp directory.
RunDLL32.exe then made a network connection to a domain registered in Austria, which it should not do under normal circumstances.
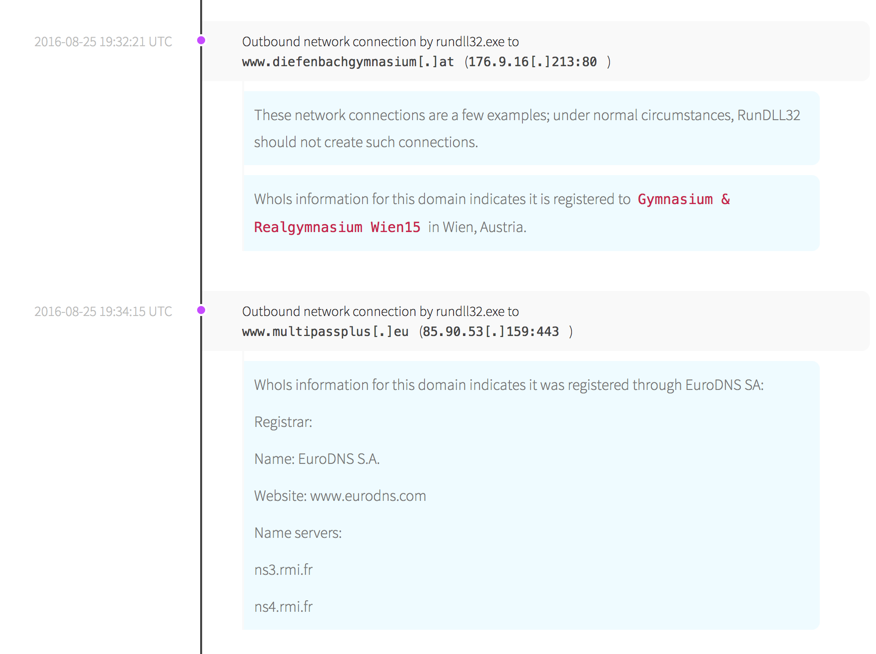
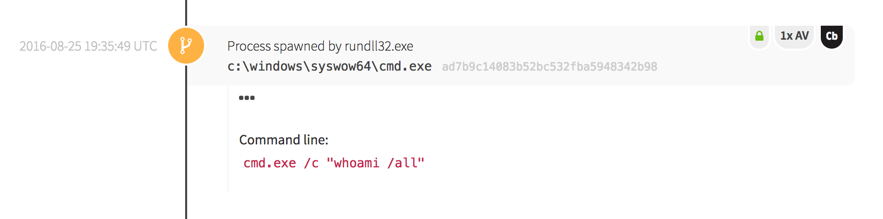
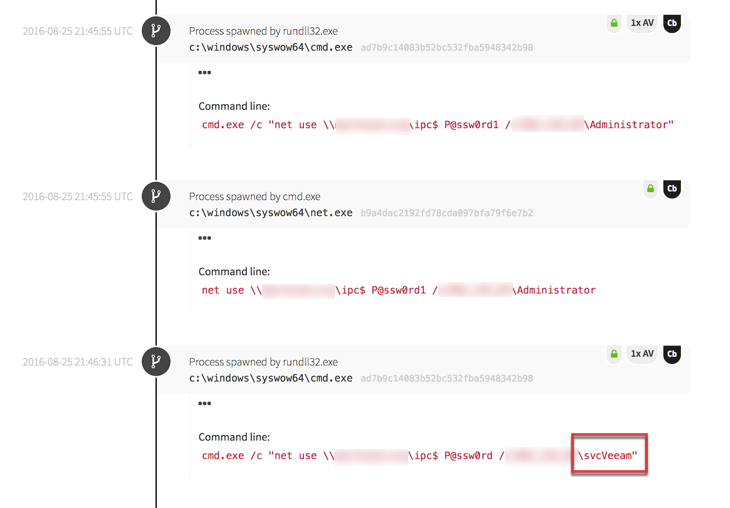
The attacker then executed a secondary script that established more network connections.
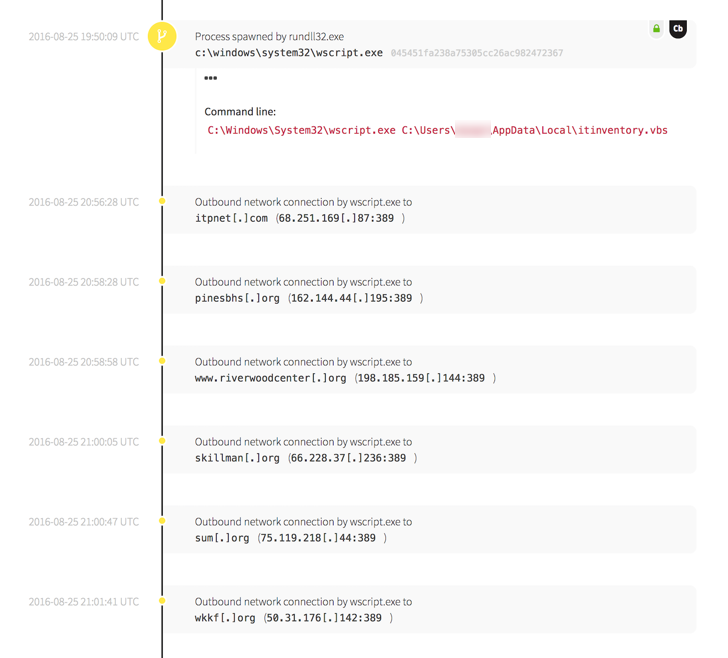
Because Red Canary was monitoring the organization’s endpoint activity, our analysts quickly detected the suspicious behavior. They jumped into action, notifying the organization’s team and working alongside them to support response efforts. Without Red Canary, the attack could have lasted for days or weeks. Instead, the attacker’s dwell time was limited and the organization was able to prevent a breach.
Want to learn more about the types of threats Red Canary detects? Download an overview of the behaviors and indicators Red Canary identifies.
Key Takeaways
While there is no silver bullet to stop APTs, a mature endpoint detection and response (EDR) capability is one of the best methods of defense. This was an advanced attack, but it still followed a very common playbook. Sadly, spear phishing continues to be a reliable vector into an organization and is frequently employed by advanced attackers. Due to attackers’ levels of sophistication and ability to gather intelligence about targets, it can be extremely difficult for users to identify these attacks. Continuous endpoint monitoring, behavior-based detection, and rapid response enablement can help security teams to detect suspicious behaviors and stop attackers before they accomplish their objectives.