We’ve been actively exploring the potential of generative AI (GenAI) since early 2023. We are now confident that, when applied judiciously, it can significantly benefit defenders. We recently wrote about how Red Canary uses GenAI technology to take some of the toil out of security operations. In this follow-up post, we detail how we use this technology to tackle a longstanding source of drudgery in security operations: alert triage and investigation.
To ensure the effectiveness of GenAI in our security operations center (SOC), we focus on clear security goals informed by quality data and always include human experts in the investigative process. Our primary objective is to deliver accurate, complete, and timely information to our customers, enabling rapid remediation before a threat significantly impacts the business. We continuously monitor and strive to improve our threat accuracy, completeness, and timeliness through internal telemetry and customer feedback. Any new tool we introduce must enhance our performance across these metrics.
Our SOC hits the gas with GenAI
We are confident in Red Canary Copilot, our internal GenAI agent, because we feed a large volume of trustworthy historical and real-time data into the large language models (LLM) we use. Over the past decade, we’ve developed thousands of behavior-based detection analytics, mapped them to MITRE ATT&CK®, recorded their conversion rates to confirmed threat detections and their severity levels, and provided response and remediation guidance to customers. Additionally, we’ve continuously updated hundreds of adversary and threat profiles, aligning them with corresponding detection analytics.
In the more than 10 years that we’ve been doing security operations work for thousands of customers, we’ve learned a lot of lessons and applied just as many time-tested decisions that are the perfect input to supercharge Red Canary Copilot’s ability to assist with alert and detection triage and investigation. Red Canary reviewed approximately 37 million potentially malicious events last year, gleaned from 200+ petabytes of security telemetry. To ensure that we’re suppressing noisy nothing alerts, and shining the light on suspicious activity, we have to be efficient and consistent in our approach to alert triage and investigation. We use GenAI agent flows to make sure that we can get through lots of alerts, make good decisions, and explain those decisions clearly.
In areas of investigation where we have enabled Red Canary Copilot flow investigations, our mean time to publish a threat dropped 60 percent without degradation of quality (i.e., completeness and accuracy).
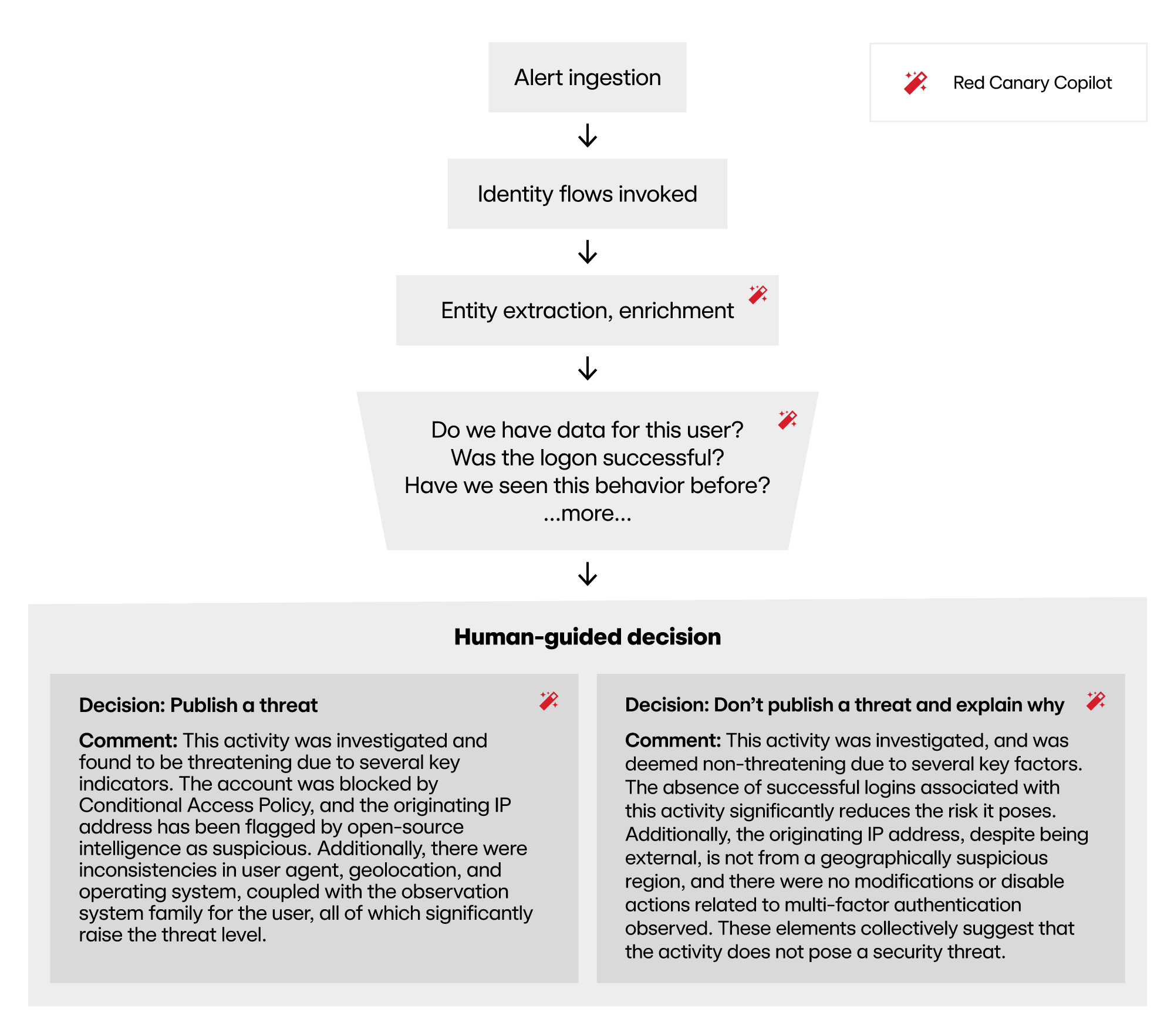
We call this technique Red Canary Copilot flow investigations. When an alert is ingested, it is directed through a pre-planned set of decision points. Developed by our security experts, this plan leverages GenAI to accelerate the process. This type of application is called flow engineering, and is on the cutting edge of GenAI applications in security.
A flow investigation, step by step
The specific decision points that we apply to an investigation depend on the source of the alert in question, but take for example an Entra ID suspicious login alert. Once this alert hits our system, the flow begins:
As a first step, the alert is submitted to a highly optimized LLM agent to extract entities we use for correlation. Using a LLM to parse this data makes the investigation resilient to unexpected schema changes or new alert types. Once the key entities are extracted, the data is transformed, cleaned, and enriched, and the flow investigation begins.
Do we have access to more data about this user?
If no: Copilot concludes the investigation right away, since neither human nor machine can add more context and value without data to review.
If yes: We proceed.
Was the logon successful?
If no: Copilot recommends that this event by itself doesn’t represent an immediate threat. We will continue to track other logins that may represent a broader pattern of behavior (like brute forcing, for example). But on this alert, we can conclude that IAM controls successfully blocked this login and we can move on.
If yes: We proceed.
In the case of a successful suspicious login, the Red Canary flow investigation really accelerates. The agent in this step automatically pulls together contextual data that would take much longer for an analyst to put together manually. Red Canary Copilot asks the following (not comprehensive) list of questions in an order defined by our security experts:
- Is this login from an ISP that typically produces false positives for risky sign-in alerts? For example, an authorized VPN in the environment?
- Is there overlap with known customer IPs?
- Does the login have a bad reputation, based on IP, ISP, Tor connection, VPN, or previous bad behavior?
- Are the logon characteristics normal in this environment, or is this behavior new and different?
After completing the steps, one final call is made to the LLM with a custom crafted prompt, including all the context that previous steps in the flow have assembled and the final recommendation of the flow investigation. The LLM summarizes all the context that leads to the decision, and how that context justifies the final decision.
At this point, the output goes straight to a Red Canary detection engineer, who reviews the data, reviews the recommendation, and makes appropriate edits and a final determination before sending the results on to the customer. Our human-guided approach ensures that any GenAI funny business (e.g., hallucination) doesn’t misinform a customer. Since the flow has asked the questions that our detection engineers designed it to ask, they already have all the information they need to make a decision.
Go with the flow
By taking 10 years of security operations expertise, and baking that into a Red Canary flow investigation, we can deliver investigations 60 percent faster than before, without sacrificing quality or accuracy. This ultimately means that we can investigate threats and deliver high-quality information to customers faster than ever without placing undue burden on our team of security experts.