The festive season is in full swing, which means the Home Alone series is likely top of mind for many of us. It got me thinking about how Kevin McCallister really is a quintessential figure head of proactive defense. As I argued in my original blog, the pint-sized defender is masterful at analyzing his environment and preparing for the inevitable. Such wisdom can also apply to the cloud. So, I’m doubling down and leveling up. Think of this as his sequel adventure.
In Home Alone 2: Lost in New York, 10-year-old Kevin thinks he’s on his way to a relaxing family vacation—one he arguably deserves since he was forgotten last time—until a small mix-up sends him to New York City alone. What follows is a whirlwind of misdirection, opportunistic villains, unprepared environments, and a kid who, yet again, learns to secure his surroundings with creativity and speed.
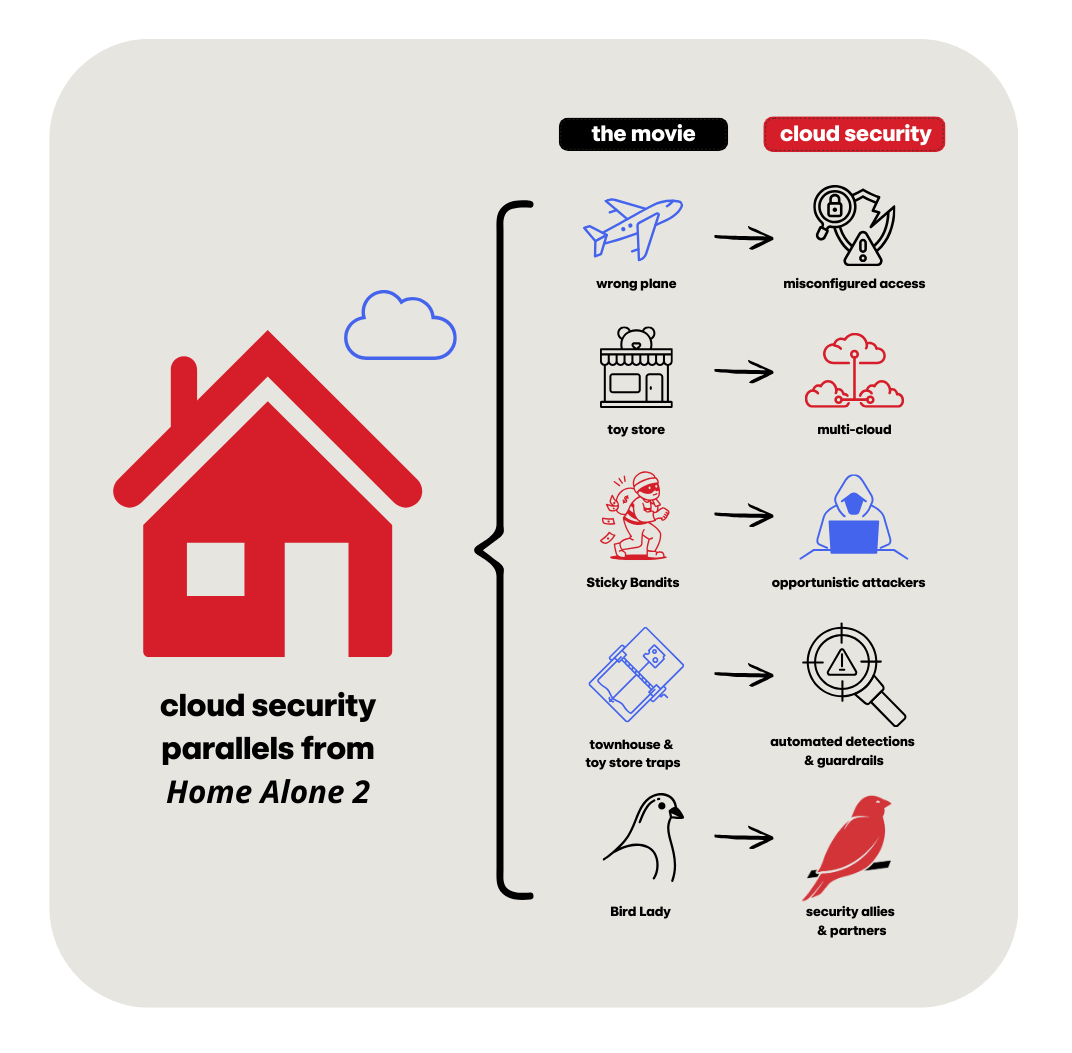
Swap planes for software platforms, burglars for threat actors, and toy stores for cloud workloads and you’ve got a surprisingly accurate depiction of cloud security today.
One wrong click and you’re in the wrong cloud environment
Kevin’s journey to the wrong plane is a perfect metaphor for what happens when an organization loses track of identity controls.
In the cloud, misrouting happens all the time:
- Overly-permissive identity and access management (IAM) roles send users into environments they shouldn’t access.
- Misconfigured SSO sends authentication tokens to the wrong application.
- Stale access keys end up being used where they don’t belong.
Just like Kevin accidentally boarding the wrong flight, identity drift is one the biggest drivers of accidental exposure in cloud environments, and it often flies under the radar.
What would Kevin do? Tighten identity boundaries, enforce least privilege, and verify every action. Don’t assume the “right person is on the right plane.”
The bandits are back & so are threat actors
In the movie, Harry and Marv return, evolved (going by the new moniker “sticky bandits”), but not exactly smarter. In cloud environments, adversaries operate the same way: persistently and opportunistically. Take Scattered Spider, for example, one of many modern threat groups that have pivoted to the cloud in recent years.
Modern attackers often:
- scan for publicly exposed S3 buckets or blobs
- find valid credentials in public-facing resources
- look for environment variables containing leaked secrets
- try to exploit insecure APIs
- follow misconfigurations like breadcrumbs
They may not always be sophisticated, but they don’t need to be. Weak cloud security hygiene is often all it takes.
What would Kevin do? Assume attackers will return. Automate cloud security posture checks and continuously harden configurations.
Turn an unfamiliar environment into a security playground
Dropped in NYC with nothing but a bag, Kevin gets resourceful: improvising traps, fortifying a townhouse, and using the environment itself as a defense platform. This is exactly how security teams should approach the cloud.
Cloud-native defenses you can “build on the fly”:
- automated detection rules triggered by anomalous activity
- serverless functions acting as tripwires
- granular network rules to establish a perimeter
- resource policies to lock the doors
- temporary elevated credentials controlled by workflow systems
Kevin uses bricks, paint cans, and a staple gun. We use resource configurations, IAM policies, and real-time detection logic.
What would Kevin do? Cloud security is less about static walls and more about agile, creative, environment-aware defense.
Trusting the wrong systems leads to chaos
In the sequel, multiple adults assume someone else is watching Kevin. In cloud ecosystems, this same “assumed responsibility” creates blind spots. Our Incident Response & Readiness guide covers this in detail, but establishing clear responsibilities and accountabilities now will save you significant headaches when the time comes.
Common trust failures:
- Developers assume ops secured the environment.
- Ops assumes the vendor hardened defaults.
- Vendors assume customers will enable critical security settings.
- Everyone assumes “we’re covered” because it’s a managed service.
When nobody is truly watching, even small misconfigurations turn into breaches.
What would Kevin do? Shared responsibility requires shared visibility. You can’t secure what you don’t own, or what you wrongfully assume is protected. Prioritize identifying ownership and accountability.
The best defense comes from knowing your environment
Kevin consistently outsmarts Harry and Marv because he knows the layout, choke points, and weak spots of the townhouse, Central Park, and the toy store. Cloud security teams must do the same.
Understanding your cloud environment means:
- mapping data flows
- knowing which assets are exposed
- understanding default service behaviors
- tracking shadow resources
- maintaining inventory of all identities and workloads
Adversaries are counting on you not knowing your architecture.
What would Kevin do? Cloud defense starts with cloud awareness. Make sure to test your environment against cloud attacker TTPs (e.g., emulation via tools like Atomic Red Team)
Kevin doesn’t do it alone, neither should you
The Bird Lady, the toy store owner, even the hotel staff (eventually) help Kevin succeed. Similarly, cloud defenders also need allies.
Instead of trying to handle everything manually:
- Leverage threat intelligence integrations.
- Use Managed Detection and Response (MDR).
- Employ cloud security posture management (CSPM) tools.
- Collaborate between DevSecOps, AppSec, and cloud teams.
- Automate wherever possible.
What would Kevin do? Cloud security is a team sport, not a solo survival mission. Nurture your partnerships.
Don’t get “lost in the cloud”
Kevin’s story is a reminder that chaos often starts with one small oversight, but resilience spawns from awareness, agility, and smart use of available tools. So, if I were to sum up the parallels from the sequel in a single image it would be this:
Like Kevin, you can’t prevent every mistake, but you can prepare and build a resilient cloud environment capable of withstanding the “cloud bandits.” Just think of it this way: By prioritizing cloud security, you can enjoy that Kevin-in-the-limo level of peace. Happy holidays!