In Part 1 of this three-part series, we walked through the top concerns that have been keeping security leaders up at night over the past year, based on findings revealed in the report. In Part 2, we’ll dig into common obstacles that hinder security improvements, even as threats are growing.
The 2021 State of Incident Response Report revealed one fact loud and clear: security leaders’ struggles are real.
Over the course of 2020, organizations shifted already overburdened staff to build capacity to support remote working, and threat actors aggressively exploited weaknesses exposed in the transition. Nearly half (49%) lack adequate tools to prevent, detect, or respond to cyber threats, while more than four in 10 say they do not have adequate staffing on their security team and that the staff they do have lacks adequate expertise.
Are organizations their own worst enemy?
While security leaders attempt to deal with heightened external risks, they are also facing substantial internal obstacles. For example, despite escalating threats, 45% of organizations surveyed said that their security spending will stay the same or decrease over the next 12 months. These organizations will be required to do more to respond to the changing threat landscape with existing—or fewer—resources.
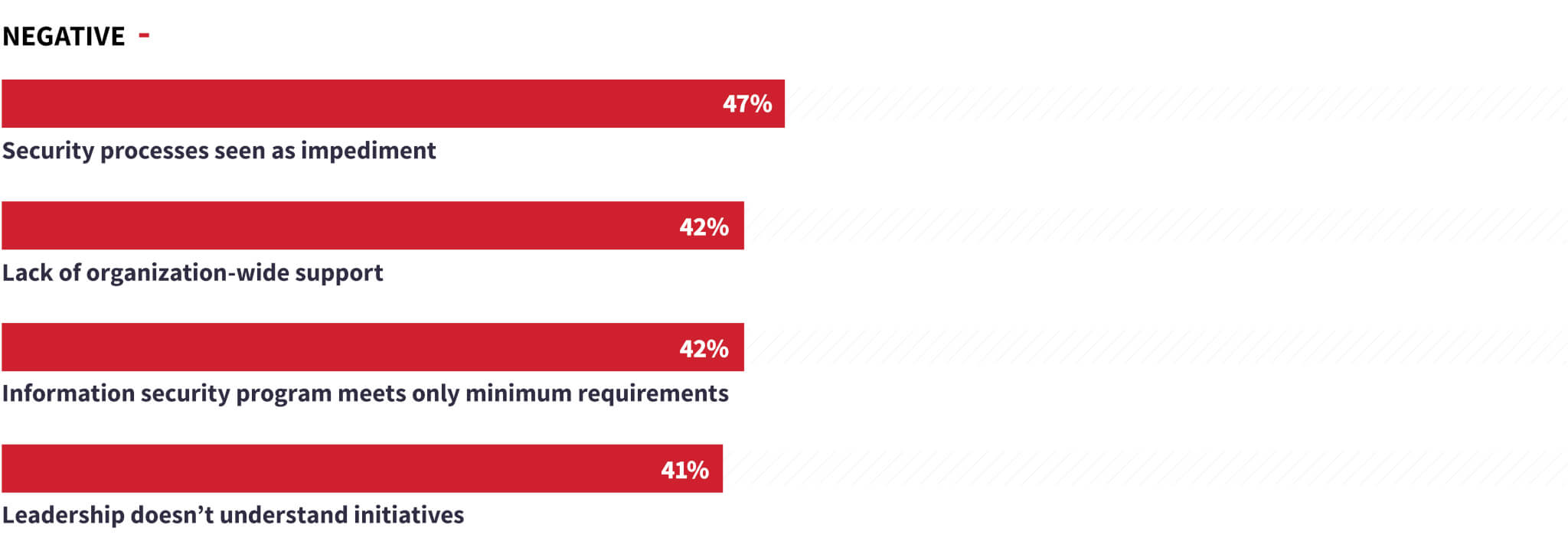
Difficulty adhering to best practices
While many security teams are following best practices, there is ample room for improvement in this area. Lack of best practices is putting defenses at risk, with as many as two in five organizations failing to perform compliance audits of partners handling sensitive data or lacking an employee security awareness program. If a large percentage of security programs are not auditing third-party vendors for compliance, they’re also likely not auditing them for security concepts such as secure development lifecycle. This could be a critical error because if an adversary pulls off a software supply chain attack on one of your third-party vendors, then you and all of their other customers are at risk—and likely the intended targets.
Many security leaders are also overlooking vital practices to test their incident response processes. Less than three in five conduct incident response exercises on a regular basis (57%), update their process based on frameworks such as NIST and MITRE ATT&CK (59%), or measure changes in performance based on the response to actual incidents (57%). Even organizations that have suffered the most are neglecting key procedures—only 51% of organizations that suffered three or more data compromises over the past 12 months regularly conduct incident response exercises.
Other notable findings from the survey: Nearly one-third (29%) don’t have a formalized information security strategy at all, and over one-third (36%) have failed to implement an employee security awareness program (37%).
Introducing best practices and formal strategies won’t automatically make an organization more secure, but it will provide a clear structure, enabling easier measurement of security processes’ effectiveness. Of course, it’s a challenge to implement these best practices when you’re always underwater, as we’ll explore in the next section.
Inefficiencies overwhelming teams
Many organizations are wasting valuable resources on inefficient processes, with the majority (54%) of security teams spending too much time investigating low-level security alerts. It’s no surprise that security teams are pressed for time when most (70%) are bombarded with 100 or more cybersecurity threat alerts every day.
Some of the most exposed organizations are also inundated with alerts: 25% of organizations that had more than three data compromises in the last 12 months are receiving more than 500 alerts a day, many of which are either innocuous or not examined at all. Most (79%) security teams at all organizations are investigating up to 20 threat events daily.
Weaknesses are evident elsewhere in the process. Only 8% of security leaders are fully confident that their organization could identify the root cause of an attack. The inability to determine the root cause can make it difficult to track threat movements and could hamper detection of what malicious activity is occuring, by whom, and in what network segments.
Lack of resources slows response time
Triaging potential threat activity requires resources to accurately sift through incoming information, an area where many security teams are lacking. After the initial compromise has occurred, nearly half (46%) of organizations are typically unable to contain a threat in less than an hour. Notably, nearly a quarter (23%) of organizations that have had more than three data compromises in the past year take at least 12 hours to contain a threat.
In the worst-case scenario, an organization will suffer an attack so debilitating that operations will go down. All organizations surveyed have a disaster recovery plan, but most plans (51%) take at least one full day to recover from downtime, costing the company precious time before operations are restored. Sustained downtime can have wide-ranging negative impacts on an organization, including wasted resources, loss of business, and damage to reputation—all the things security leaders ranked highest amongst their top concerns.
Turning the tide
So what can security leaders do to turn the tide? In the final part of this 3-part series, we’ll talk to cybersecurity experts from Red Canary, Kroll, and VMware for insights, analysis, and practical recommendations.
This is the second installment of a three-part series. Subscribe to the Red Canary blog to receive the last part in the series, as well as a weekly email with our latest articles and research.