Thank you once more to everyone who took the time to attend Cover Your Security Gaps with Outsourced Endpoint Detection & Response! We had fantastic attendance, and really great questions during the presentation. If you missed the webinar, or if you loved it so much that you’d like to watch it again, you can view it here.
I thought I’d take a moment to address some of the questions and themes that we discussed.
As context for those who haven’t watched it yet: Red Canary provides outsourced endpoint detection and response to businesses of any size.
We do this because for many companies building an effective EDR capability in-house is out of reach from a resource and budget perspective. For companies looking to outsource their endpoint detection and response, there are two primary options: MSSPs and Managed Detection and Response (MDR). We stressed this many times during the webinar, but MSSPs and MDR are very different. MSSPs are focused on device management, log collection, and helping you meet your compliance requirements. MDR solutions focus on monitoring your network for threatening activity, validating the threat, and assessing the severity or risk. If you take nothing else away from this webinar that that, then I feel that I succeeded.
Before Outsourcing, Know Thyself
We listed a few important questions that you should answer before embarking on the road to EDR. One thing we continue seeing organizations overlook is the full cost it will take for them to establish their EDR capability. This is often due to the fact that organizations have not dug into the details around EDR as it pertains to them:
- Why they need it
- What goals they have
- How they are envisioning the tools, process, and expertise fitting together
- What budget they can commit long-term
Attendee Question: When it comes to very specific, target attacks against very specific verticals, what expectations should companies have about outsourced providers?
Ultimately, a good outsourced provider should feel much more like a partner and a part of your team than a vendor. The more you you understand what normal looks like in your organization and are able to convey that information to the provider the better a partner they can be. In our case specifically, every piece of organizational information provided helps Red Canary learn your environment, improve detection, eliminate false positives, and identify very specific, targeted attacks with greater accuracy.
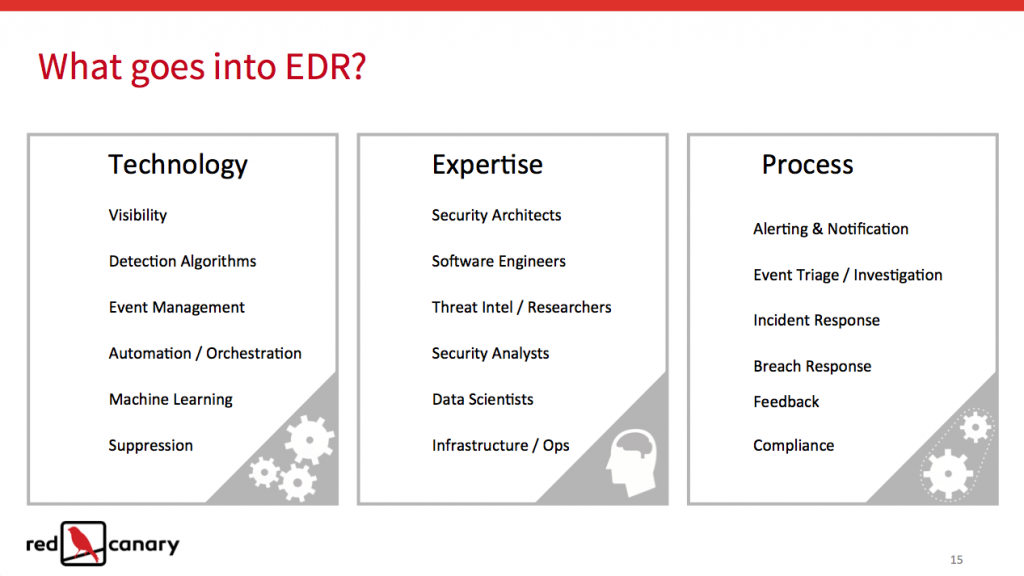
 The Core Components of EDR
The Core Components of EDR
This is where we spent most of our time during the webinar and really we didn’t even scratch the surface. One of the biggest misconceptions in the market right now is that you can purchase an EDR tool and get an EDR capability. That is just not the case and we are tired of seeing companies being taken advantage of. EDR is a capability that requires equal parts Technology, Expertise, and Process. If a vendor tells you that you can shortcut this process with their magic box or “math” be very skeptical.
Attendee Question: It’s not realistic to hire top notch talent across all of these expertise categories – are we of the mindset it is not worth trying to build an EDR capability internally unless you can get all of these disciplines?
Not necessarily. However, you do need to have a plan for how you are going to satisfy the requirements. Whether you use a combination of an MSSP and consultants or you try to find the unicorn security professional who meets several of the requirements (read expensive!) there are ways get a working EDR capability in place without hiring 8-10 people. We have just found that for 99% of organizations, it would be cheaper, quicker, and more effective to use a fully outsourced approach like MDR.
Hopefully, this webinar will be a useful piece of reference material for any organization looking to outsource their endpoint security. If you have any other questions, I check my email once a week (mild exaggeration) and I will respond as soon as possible.
 The Core Components of EDR
The Core Components of EDR