Most security leaders (82%) believe their organization is vulnerable to a cyber attack…and unfortunately, they’re right. A staggering 93% of organizations suffered a data compromise over the past 12 months, and nearly half (49%) of these had at least four such incidents.
The data was uncovered in a 2021 State of Incident Response Report based on a survey of 500 security and risk leaders conducted by Wakefield Research on behalf of Red Canary, Kroll, and VMware.
These jarring statistics come on the heels of one of the most challenging years the security industry—and the world—has ever seen. The COVID-19 crisis forced organizations to quickly adjust, with many security teams scrambling to establish secure connections to support a work-from-home (WFH) model. Meanwhile, threat actors worked just as quickly, seizing the opportunity to target remote workers and aggressively exploit weaknesses. It’s no wonder the majority of security leaders are left feeling vulnerable.
But there’s a bright side to the findings: uncovering challenges can pave the way toward new solutions. In this three-part blog series, we’ll take a closer look at the research revealed in the 2021 State of Incident Response Report and explore:
- Top concerns keeping security leaders up at night over the past year
- Common obstacles standing in the way of effective incident response
- What organizations can do to turn the tide and improve security
What keeps security leaders up at night?
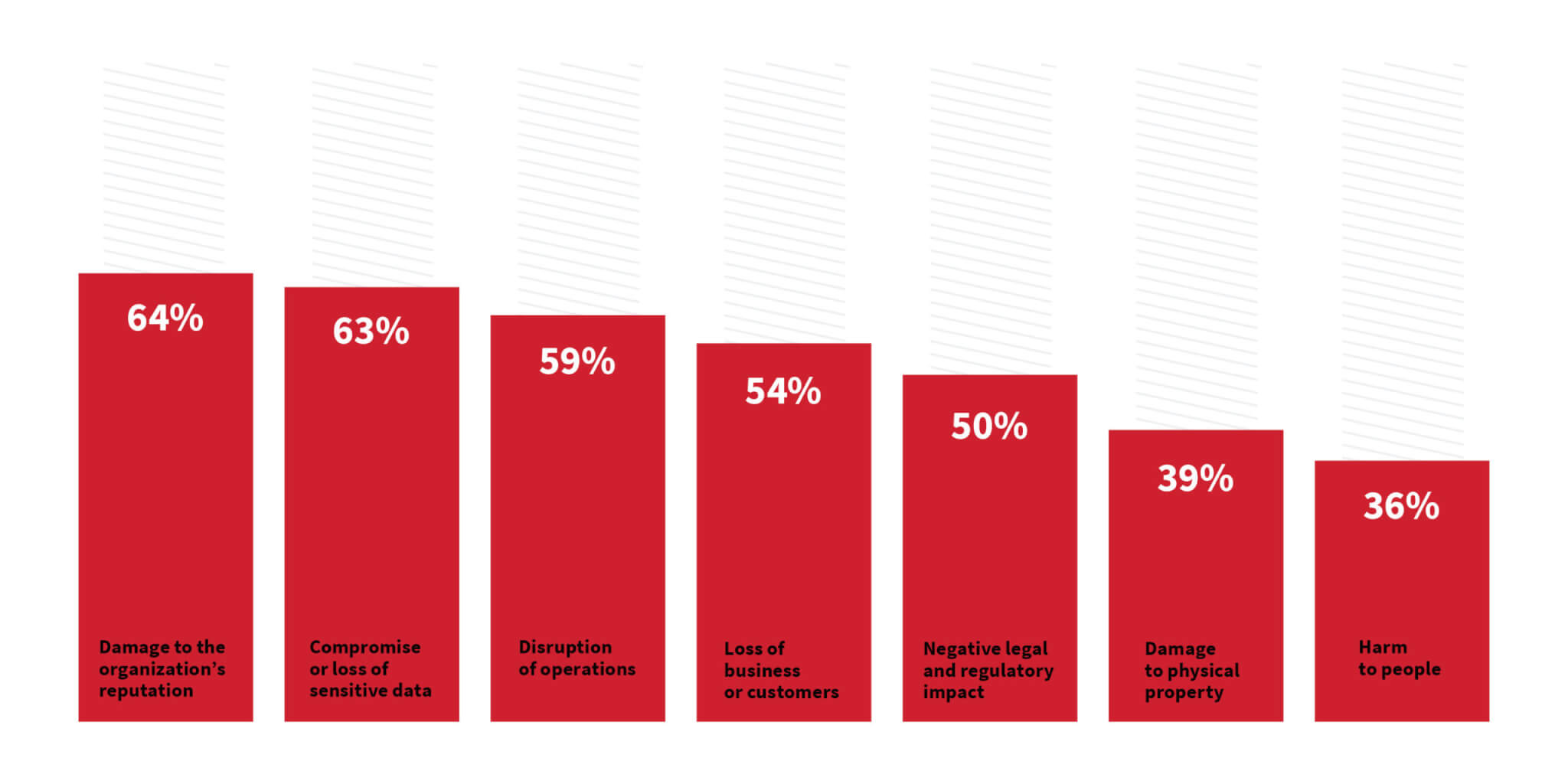
Security leaders know that a cyber attack can impact every aspect of their organization. Their concerns over the negative consequences of an attack range from immediate impacts like data loss to immeasurable, long-term effects like reputational damage.
These concerns are not unfounded. The COVID-19 pandemic has brought to light inefficiencies or a lack of preparedness within security teams. All at once, security teams found themselves dealing with an influx of personal devices on the corporate network, greatly reducing endpoint visibility and expanding the potential attack surface, at the same time that attack vectors were, and continue to be, on the rise.
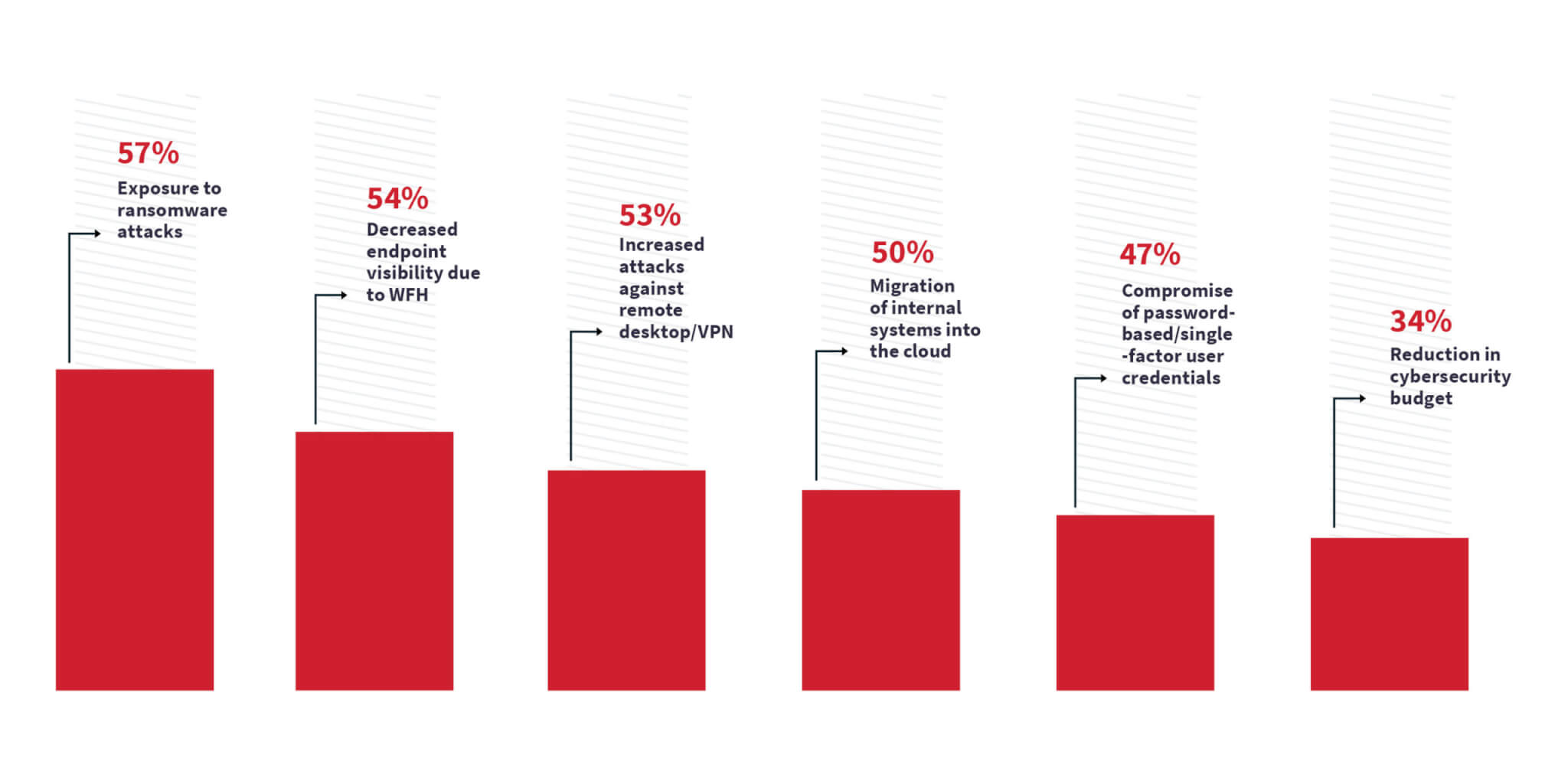
The new risks are diverse and substantial. Here’s a closer look at security leaders’ top areas of increased concern:
- Ransomware attacks: Ransomware has been a high-profile threat for some time and continues to grow in prominence. Its frequent success and continually evolving tactics makes it a regrettably profitable business model that has left organizations struggling to adapt their approach to incident response.
- WFH, remote attacks, and cloud migration: Prior to the remote work surge, tools like network-based threat detection and web proxy filters were traditionally implemented on premises at a corporate location. Now, security teams are staring down a proliferation of employee-owned endpoints that are accessing the corporate network and causing visibility challenges. The reduction in endpoint visibility due to working from home has become an increased concern for more than half of security leaders (54%). Increased attacks against remote desktop services (53%) and the migration of internal systems to the cloud have also become greater threats (50%).
- Credential compromise: Nearly half (47%) of security leaders pointed to identity compromise through password-based/single-factor user credentials as a growing area of concern for their organization. However, this has long been a commonly used attack vector, made attractive to adversaries simply because gaining access to a system as an authorized user is much more efficient than attempting to target the built-in security of operating systems. It’s also common to see a remote desktop or other service exposed to the internet with single-factor authentication serving as the initial entry point for an adversary, then leading to lateral movement and ultimately, ransomware.
- Reduced budget: Despite so many suffering a data compromise over the past year, security budgets remain insufficient. Security leaders know all too well that security is a cost center, not a revenue source for most organizations. Many expect their stakeholders to minimize spend.
What stands in the way of security improvements?
The threats are real and have been felt by nearly all organizations. But closing the gaps isn’t easy, and organizations are facing headwinds to meet cybersecurity challenges. In the next installment of this three-part series, we’ll explore the real-world obstacles that are hindering security improvements. Then, we’ll turn to cybersecurity leaders at Red Canary, Kroll, and VMware for practical advice on how to turn the tide.
This is the first installment of a three-part series. Subscribe to the Red Canary blog to receive the next two parts in the series, as well as a weekly email with our latest articles and research.