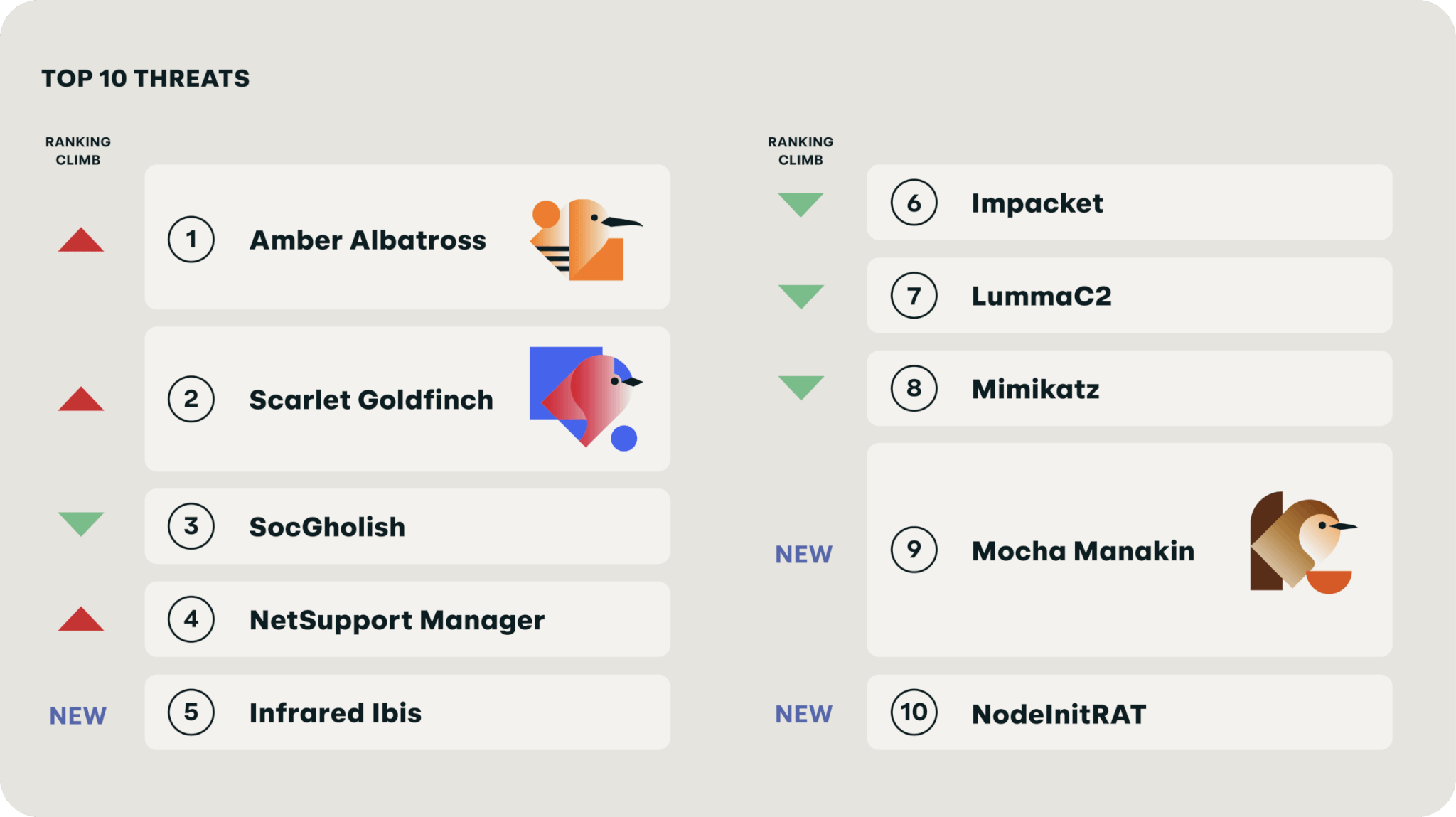
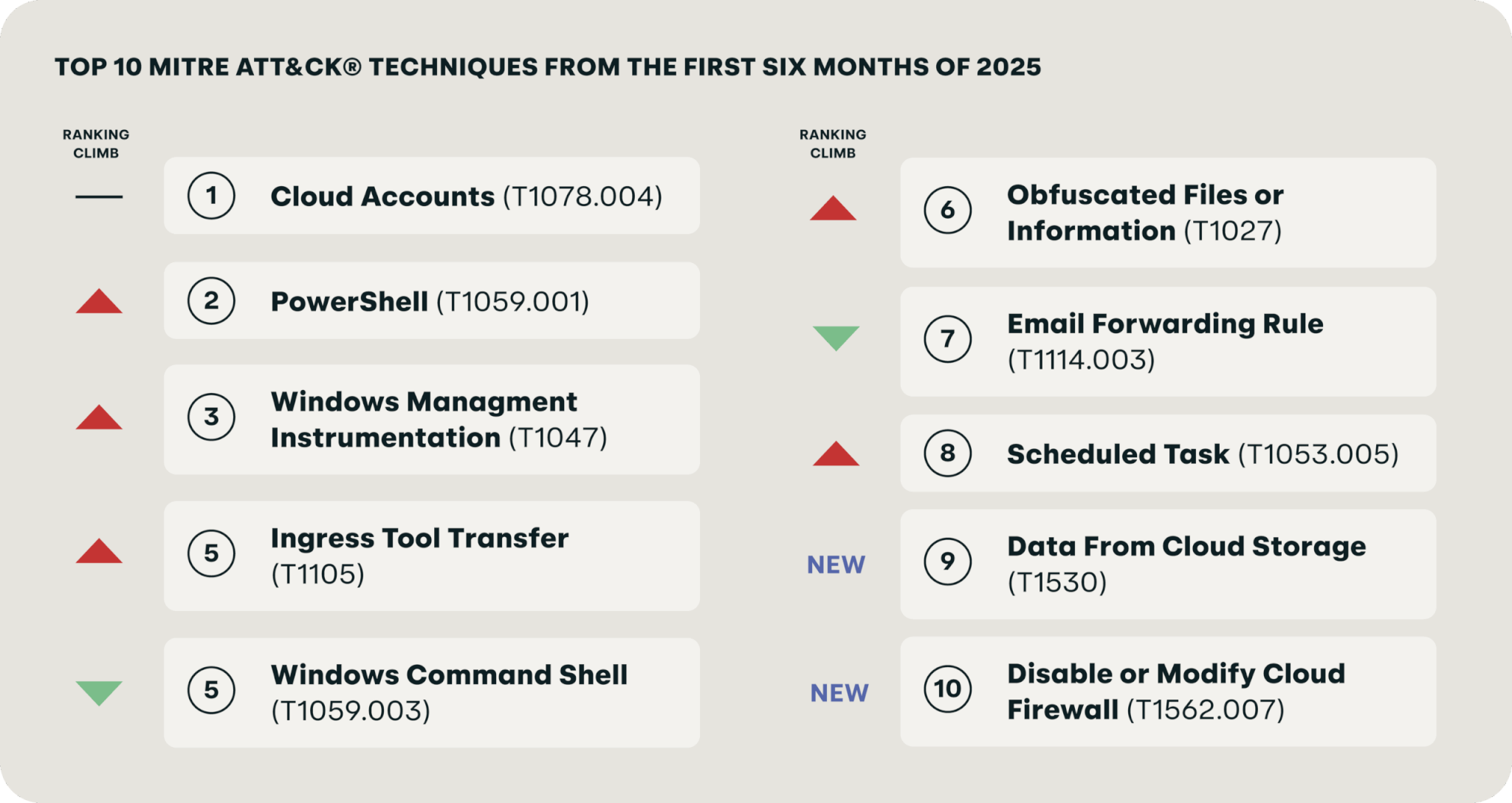
We detected a rash of color bird threats in the first half of 2025, led by stealer-like Amber Albatross and dropper Scarlet Goldfinch. Cloud Accounts (T1078.004) continues to dominate our MITRE ATT&CK® technique rankings due increased adoption of identity security products and improvements in detection coverage, and Data from Cloud Storage (T1530) and Disable or Modify Cloud Firewall (T1562.007) also cracked our top 10 list for the first time ever. Further, paste-and-run initial access schemes (aka ClickFix, fakeCAPTCHA) spurred MITRE to create Malicious Copy Paste (T1204.004)
Additionally, we analyzed thousands of user-submitted phishing emails so far this year, identifying novel phishing tradecraft and learning about the phishing landscape generally. We dive into all this and more in the 2025 Midyear Threat Detection Report.
A precipitous rise in identity detections
We detected roughly 5 times as many identity-related detections in the first half of this year as we did in all of 2024. While this may sound alarming at face value, this increase is not a direct reflection on changes in the threat landscape. Rather, it’s a reflection of increased adoption of identity security tools and improvements in detection coverage enabled by the implementation of a custom AI tooling across Red Canary.
Cloud Accounts (T1078.004) detections
Securing an organization’s identity infrastructure requires the ability to detect suspicious or risky logins as well as overtly malicious ones. For many months now, we’ve been leveraging agentic AI to build user baselines for the identities we protect, which, in turn, is allowing us to better identify anomalous logins and prevent identity compromise by comparing the characteristics of a given login to that identity’s baseline activity. As such, we’re able to detect when a user logs in from an unusual IP range, unexpected device or browser, or via an unsanctioned VPN.
While these sorts of logins aren’t necessarily malicious, they represent a potential risk to organizations, and they are frequently the means of initial access that lead to costly breaches.
Color birds dominate threat rankings
For the first time ever, Red Canary-named activity clusters (aka “color birds”) accounted for a full half of the top threats over the first six months of the year. While that’s an interesting novelty, it’s important to understand the risk these and other threats pose collectively.
Our top 10 included stealers, loaders, remote monitoring and management (RMM) tools, and ransomware precursors. Adversaries delivered these threats via potentially unwanted programs (PUP), compromised browser extensions, fake browser updates, malvertising, SEO poisoning, and, increasingly, paste-and-run schemes.
The prevalence of these threats across our visibility suggest that most organizations are likely to face them at some point. Further, since they represent a risk that can materialize in a variety of ways (e.g., data theft, ransomware, financial loss, etc.), it’s critical that organizations have a defensive strategy in place to detect and prevent these threats and mitigate the initial access and other techniques they leverage.
Two new cloud techniques and a look at paste and run
As is the case with identity detection, it’s important to detect risks when you’re securing a cloud environment. And the two new techniques in our top 10, Data from Cloud Storage and Disable or Modify Cloud Firewall, are two great (and related) examples of the importance of risk detection in the cloud. Over the last decade, countless breaches have occurred due to overly permissive access policies for cloud resources. Exposed AWS S3 buckets in particular have been a major problem.
Organizations might intentionally make an S3 bucket publicly accessible or otherwise enable external access to cloud resources. However, doing so inadvertently is a common misconfiguration issue that’s caused a lot of heartache for organizations. As such, it’s important to understand when broad access is being allowed for cloud resources and why.
Finally, Malicious Copy Paste didn’t make our top 10 technique list due to the art and science of ATT&CK mapping, but it’s probably the technique of the year given just how widely threats leverage it. It’s important that organizations understand this technique, how it’s being leveraged on Windows and macOS alike, and strategies to diminish its efficacy.
What we’re learning from investigating phishing messages
We investigated thousands of user-reported phishing emails this year. Just 16 percent of the emails we investigated were confirmed malicious, suggesting that users are definitely suspicious about phishing emails (good!) but also that regular emails often look quite a lot like phishing emails (not so good!).
The phishing emails we detected involved credential phishing, malicious attachments, and all variety of social engineering. We also investigated some fairly novel phishing tradecraft wherein adversaries leveraged Google Translate services to evade detection, used built-in tooling to conceal payloads, and more.
Phishing remains a major problem, but user education efforts over the years are clearly paying off as skeptical users are reporting suspect emails in droves. Nevertheless, it remains important to understand the ways that adversaries are leveraging phishing so we can develop strategies to counteract the risk that phishing schemes pose to organizations.