As macOS and Linux systems have become more commonplace in enterprises, so has the tooling to compromise them and facilitate post-exploit hijinks. For those charged with defending macOS and Linux systems, knowing how to detect and defend against this activity is critical. Even unsophisticated attackers can use these tools to infiltrate a system, perform reconnaissance, escalate privilege, and move laterally throughout a network.
At Red Canary, we see the use of post-exploitation frameworks often. They come in all shapes and sizes, for a variety of platforms (Empire and Metasploit being quite popular), and are loaded with a salvo of tooling suited to the goals of the threat actor. EggShell is one such framework focusing on surveillance on macOS and iOS devices. In this blog we’ll provide practical methods to detect and prevent some of EggShell’s most intriguing capabilities.
EggShell Capabilities
Once you pull down the tool, you will notice that EggShell comes packed with a wide variety of capabilities, a few of which are:
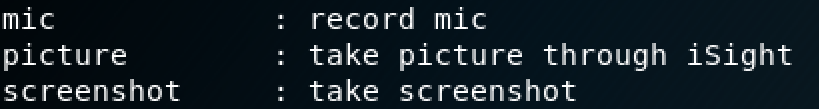
- Full camera and microphone control
- Screenshot desktop and collect clipboard data
- File manipulation (download, upload, delete, etc)
- Send iMessages and manipulate iTunes tracks
- Local Phishing via user prompt
- Facebook session cookie theft
- Much more
While some of the features make EggShell perfect for trolling your colleagues, a threat actor with this level of control over a key endpoint could do critical damage to your organization. Imagine an attacker recording a board meeting prior to a big announcement, or capturing evidence that your CIO is having an affair. Blackmailing a C-level executive can be far more efficient than poking around a network for interesting files.
Let’s dig deeper into how EggShell works and look at actionable techniques defenders can use to detect and prevent this activity.
Payload Creation
From the attacker’s perspective, getting started is as simple as walking through a few quick steps to set up the listening server and create the call-back payload. Once crafted, the attacker will need to find some delivery mechanism to execute it on the target’s system. There are countless exploitable vulnerabilities that will allow attackers to run arbitrary code on unpatched systems. What we’re interested in today is less about how the adversary is able to exploit the system, but what they do once they land in your network.
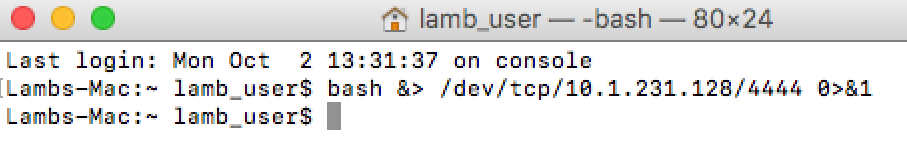
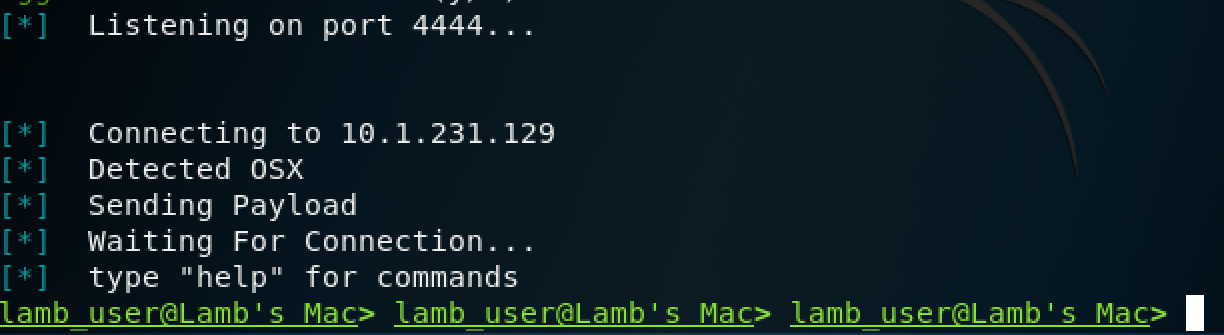
The command to establish control is a very simple one-line reverse shell that looks something like this:
This establishes the connection back to the actor’s system, allowing the use of the tools within the framework.
 Detection and Prevention
Detection and Prevention
In some compilations of bash, the OS vendor can elect for “pseudo-files” to be created in /dev/tcp/ and /dev/udp/ when commands such as these are run. Apple’s implementation of bash doesn’t do this, and as such monitoring for the creation of these files won’t detect this particular threat. Instead, we will want to monitor command-lines referencing “/dev/tcp/”:
As an aside, building detection capabilities for all major Office and PDF applications spawning child processes such as shells (sh, bash, etc.) and scripting processes (python, powershell, osascript, etc.) can help you find this and a lot of other evil things. We see this technique used quite frequently in malware and phishing campaigns.
As for prevention, standard security hygiene applies. Limit your attack surface by disabling Office macros, keeping your systems and applications patched, and putting any preventative controls you can between your users, their emails, and the internet at large. Unfortunately you can’t stop everything at the perimeter, but by putting some basic controls in place, you can avoid being the “low-hanging fruit” victim, and all but the most determined adversaries will pass you by.
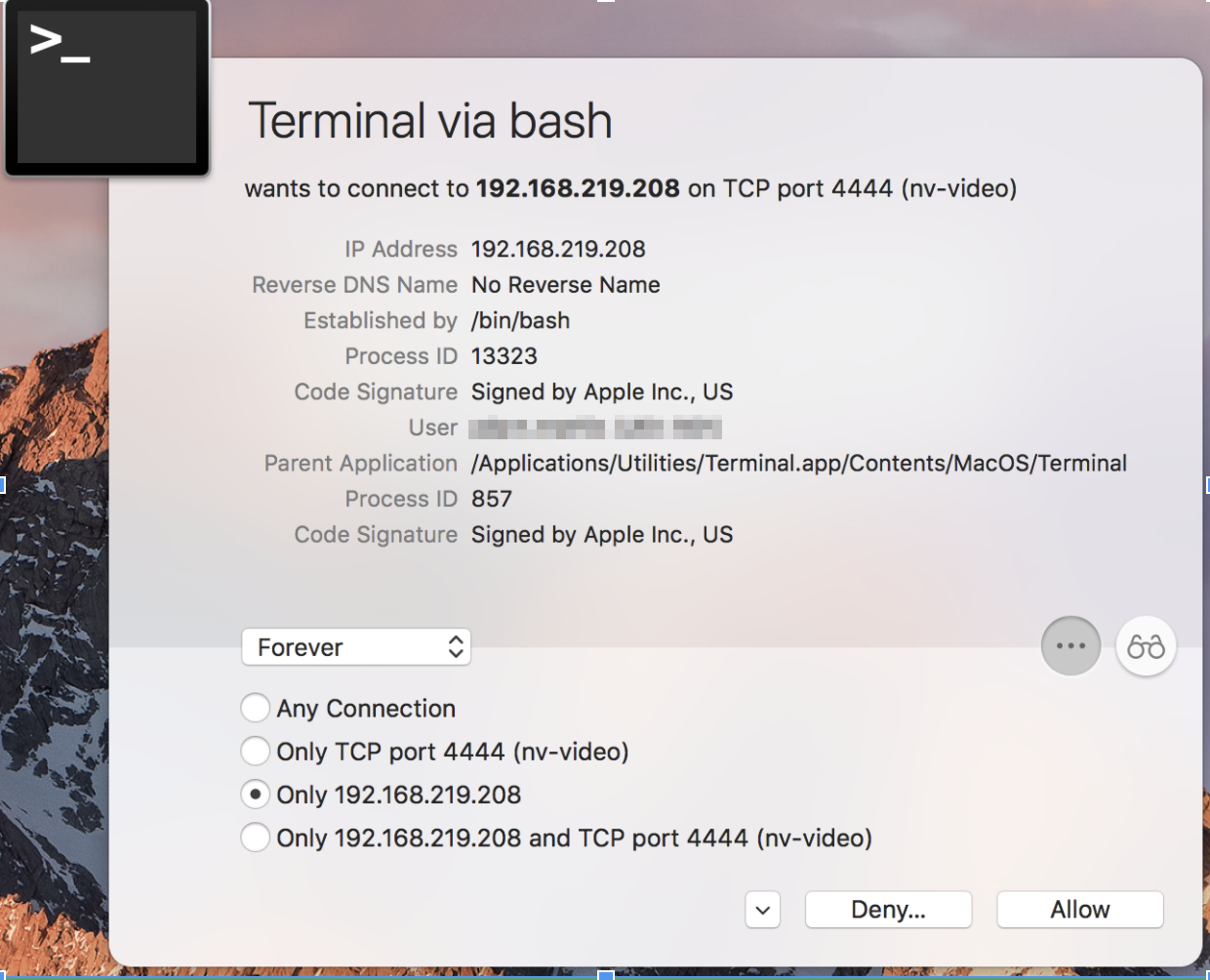
In this case, firewalling may be your best safeguard for this type of threat. Using a firewall utility such as LittleSnitch or the built-in Mac firewall with explicit allowances for required traffic stops this callback in its tracks.
Below is an example prompt from LittleSnitch when a connection attempt is made that is not explicitly approved in your configuration. Once you have locked in the desired firewall configuration on your endpoints, a default “deny any” rule will prevent users from allowing this type of connectivity when prompted.

Establishing Persistence
Once the threat actor has established a remote connection to the victim’s system, they can establish persistence using the “persistence” function in EggShell. This function uses the built-in cron functionality to add a recurring task to the user’s crontab, allowing the attacker to resume control of the Mac after a reboot or other interrupted connectivity.
Detection and Prevention
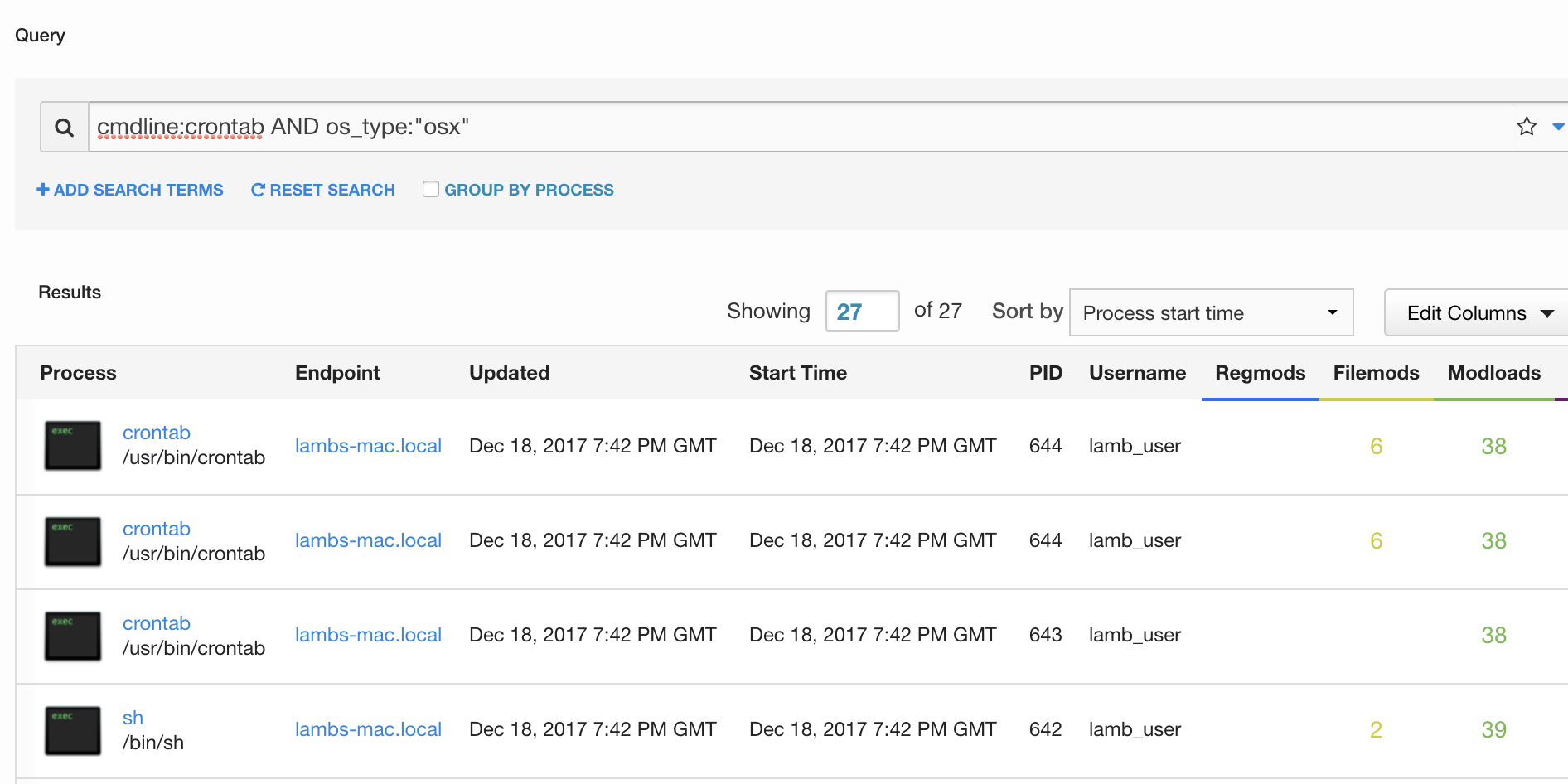
Watch for the creation of new crontab entries. This could be noisy on a production Linux server, but should result in a higher fidelity detection for end user endpoints. In Carbon Black Response, a query to detect this activity may look like this:
It is possible to prevent persistence by disabling the creation of crontab entries for all non-root users, which effectively disables users’ ability to create scheduled tasks. When planning and implementing controls, you are often balancing security with usability. Knowing your organization’s risk appetite and testing thoroughly will save you grief in the long run.
To restrict cron to root only, perform the following:
`chmod 700 /usr/bin/crontab`
Even though EggShell uses cron jobs for persistence, there are many other persistence mechanisms that a determined threat actor can leverage to maintain their foothold on your systems. So why bring this up? Another interesting feature EggShell gives you is the ability to pass your keystrokes through to the victim machine. While the attacker has access to your system, they may opt to protect their foothold by running additional commands directly on the host. Familiarize yourself with the various macOS-specific persistence mechanisms that MITRE has curated here: https://attack.mitre.org/wiki/Mac_Technique_Matrix
Audio/Visual Surveillance
Once the threat actor has access to the system and has established persistence, the real fun begins. At this stage, they can take numerous screenshots of the desktop, activate the camera, and record the user’s conversations with the microphone.
 Detection and Prevention
Detection and Prevention
While it is technically possible to track applications accessing the library files associated with camera use, this would be quite cumbersome in practice. Calling each user to confirm they attended a web conference is not ideal, so thankfully defenders have other options here. MicroSnitch is a lightweight “surveillance firewall” utility that notifies the user when the camera or microphone are activated on their Mac. Deploying a utility such as this and educating your users can be a solid indicator that something is amiss.
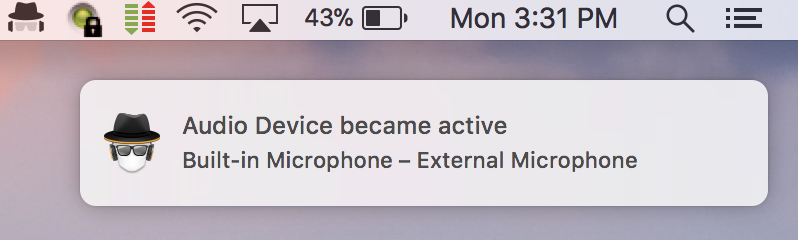
Recon and Privilege Escalation
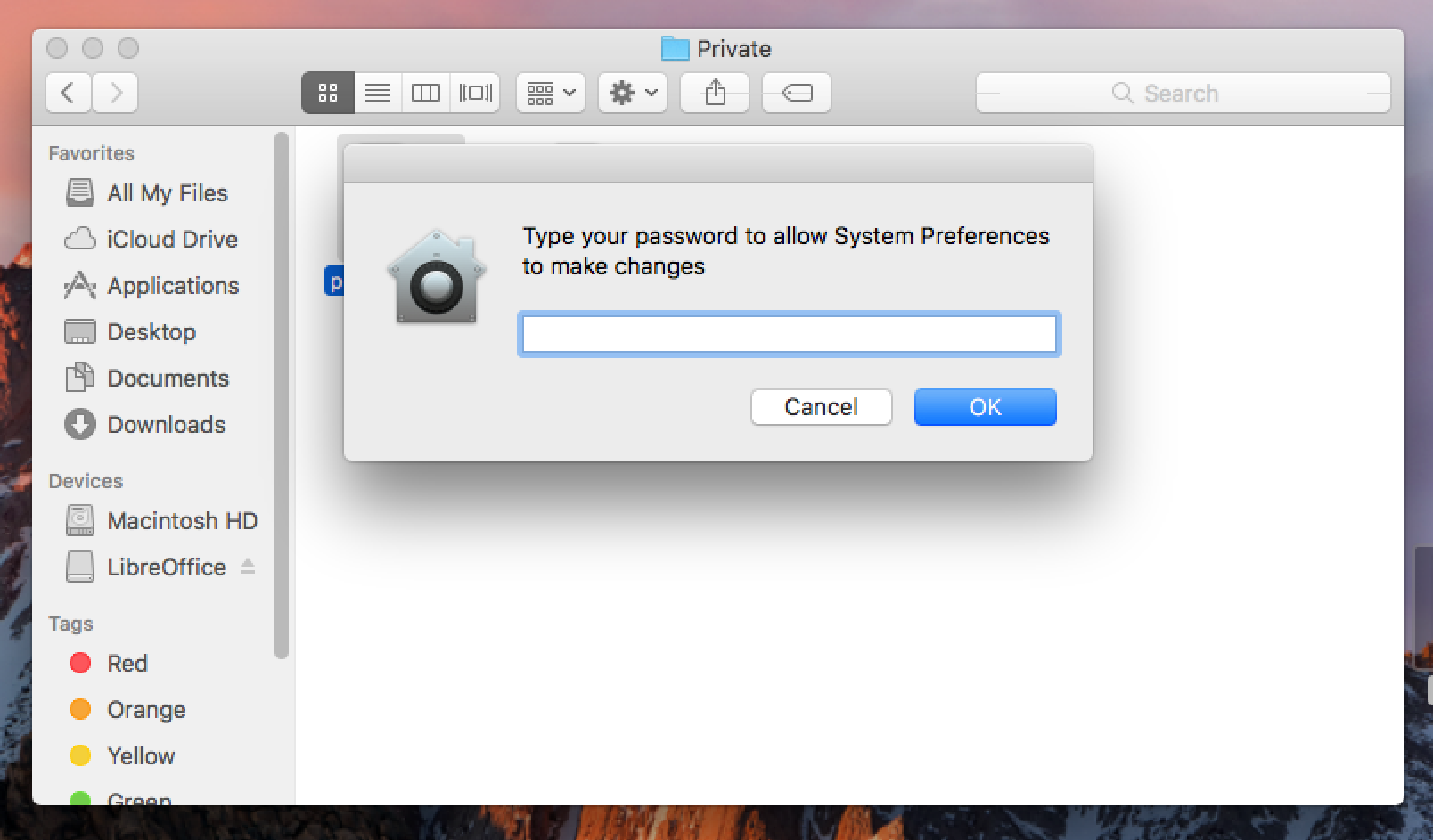
A common adversarial tactic upon gaining access to a system is performing reconnaissance and escalating privileges. EggShell provides a very convincing escalation method that uses AppleScript to simply prompt the user for their password:
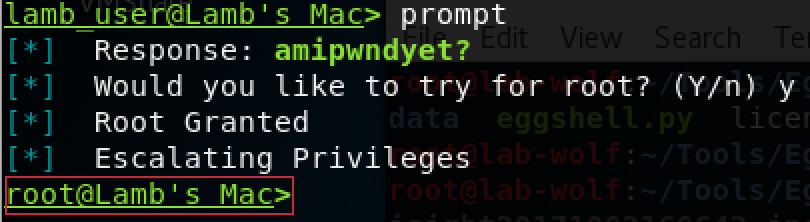
Because AppleScript can generate user prompts that appear identical to system prompts, it is highly likely that a non-paranoid end user will provide their credentials when prompted. As soon as EggShell receives the user’s password, it will prompt the attacker to escalate privilege to root:
Once the actor has root privileges, they effectively control the entire system and can go about accessing otherwise protected processes and files outside of the user’s control (such as disabling security settings and agents). Also, by using the “persistence” function with root privileges, the entry is added to the root crontab, making it invisible to normal users and defenders not looking in this location.
Detection and Prevention
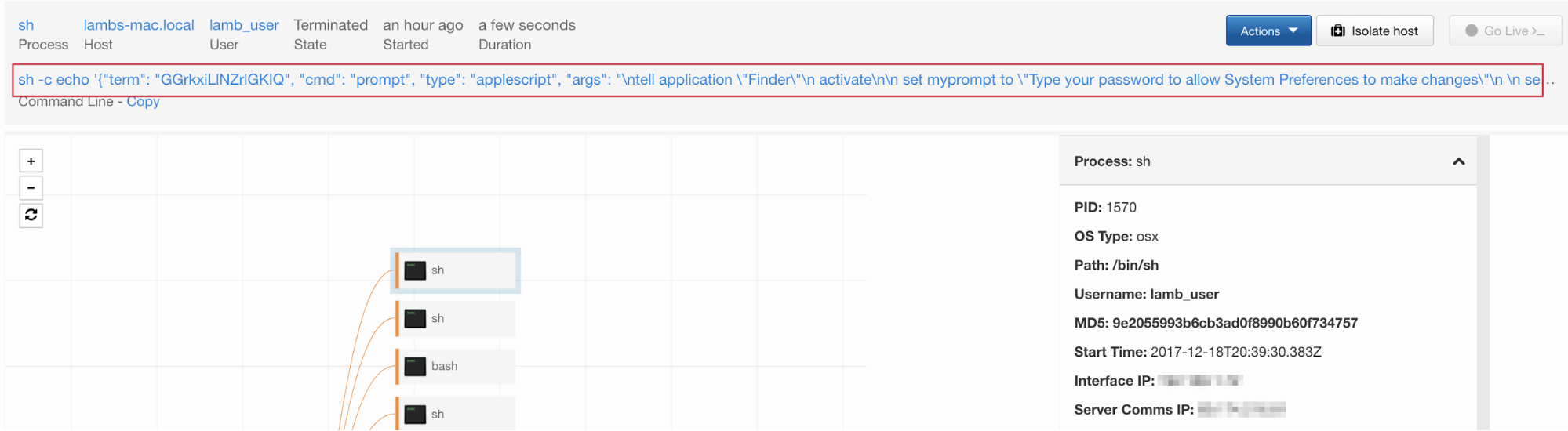
Because there is no way to elegantly prevent a user from executing AppleScript, good detection is key. Look for executions of AppleScript (either from osascript or called by the shell process) with a command-line that includes “System Preferences” and “password”. You will likely find a few third-party applications that do this, but not at such frequency that it becomes unmanageable. Here I’ve created a sample query in Cb Response to find this type of prompt:
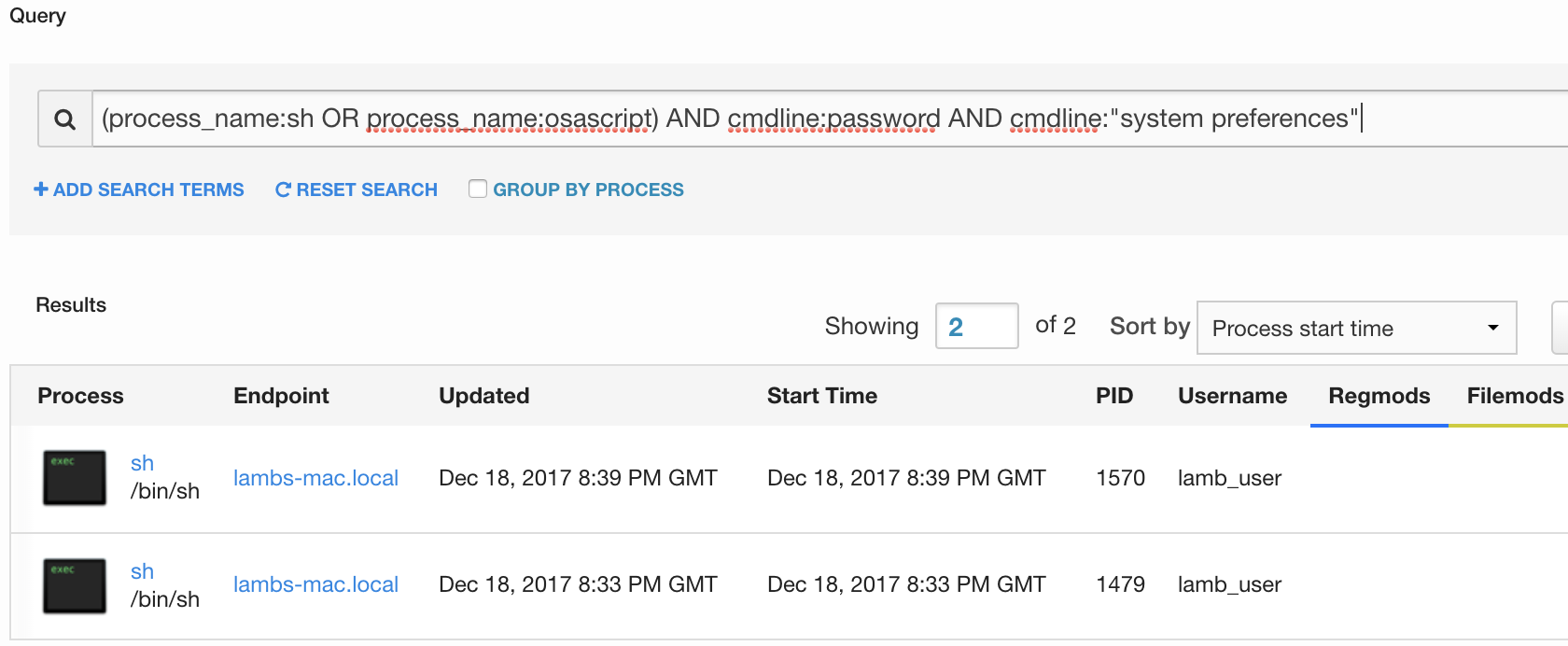

File Manipulation and Exfiltration
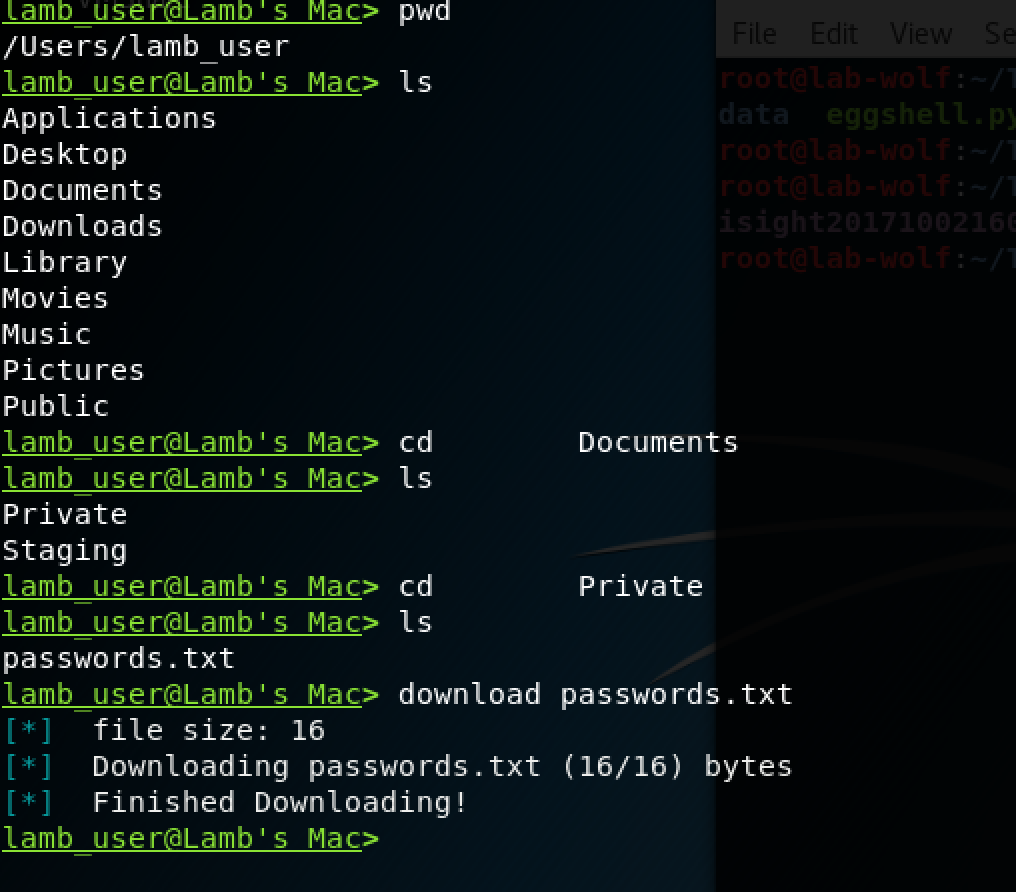
Actors with a foothold on your system also have basic file system capabilities, including capturing files, deleting files, and placing files and binaries of their own. This is not only a way for the attacker to deploy additional tooling, but also an easy way to exfiltrate sensitive data out of your network.

Detection and Prevention
Once the actor has this level of control over your system, it is difficult to differentiate the actor’s actions from your end user’s. Defining a policy of keeping sensitive data off of endpoints is a solid best practice to prevent the attacker from accessing your critical data, but this can be hard to enforce. File integrity monitoring on critical files is another excellent tool to ensure integrity is maintained for your critical files and folders, and can indicate when someone is attempting to collect or destroy these assets.
Conclusion
The threat of post-exploit frameworks isn’t going away any time soon, and with the ever-growing list of delivery mechanisms it can begin to feel like a game of “whack-a-mole” to defenders. As with most security strategies, a defense-in-depth approach that combines many layers of detection and prevention capabilities will yield the best results. And once you feel like you have a good handle on this threat, test your process! Tools like EggShell are available to Blue teams as well as the enemy, so spin up an instance and make sure you’re using every advantage in your arsenal to keep your click-happy users safe.
To walk through an example of post-exploitation on a Mac, read: Attacking a Mac: Threat Detection #392
 Detection and Prevention
Detection and Prevention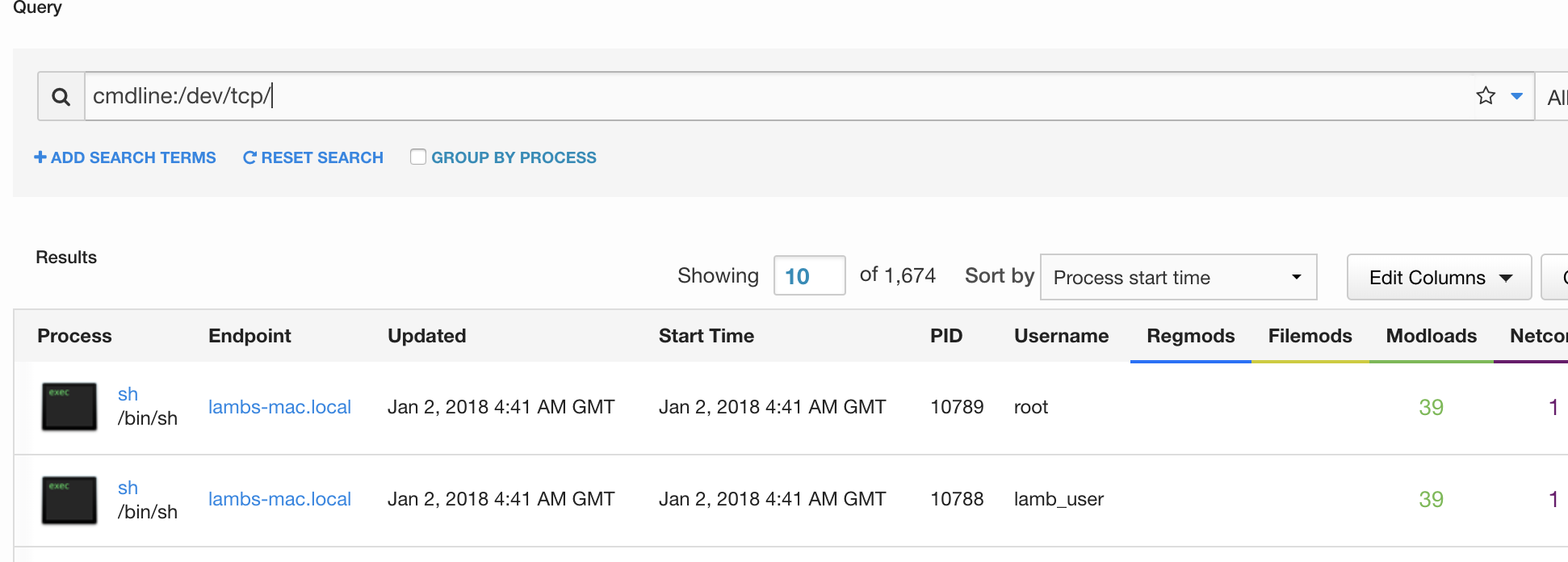
 Detection and Prevention
Detection and Prevention